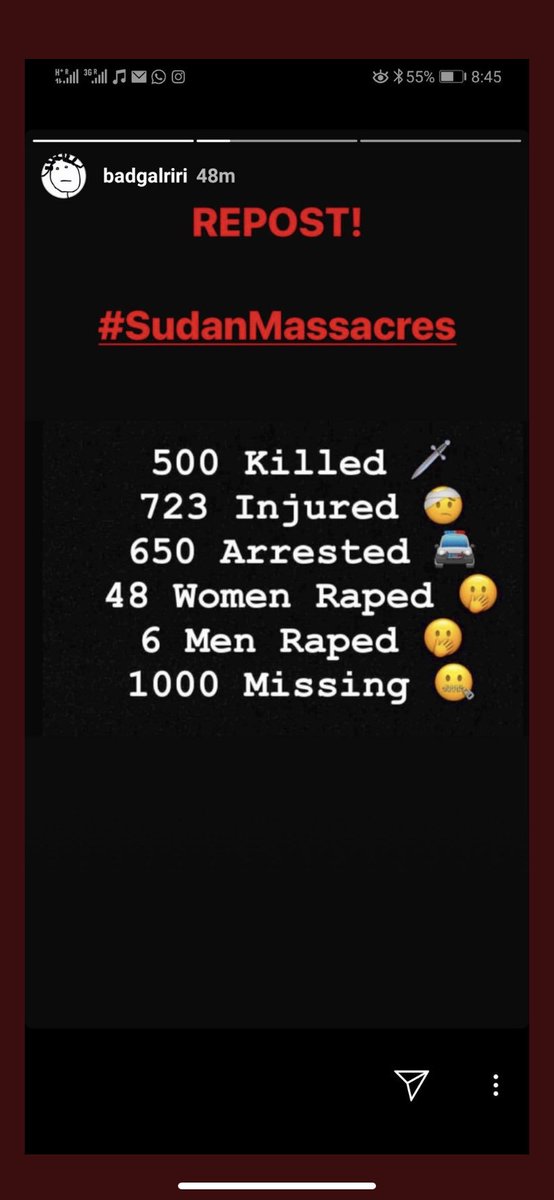
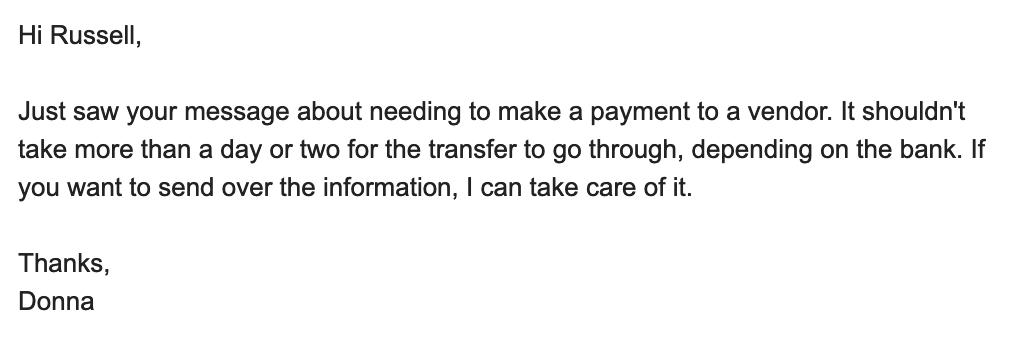
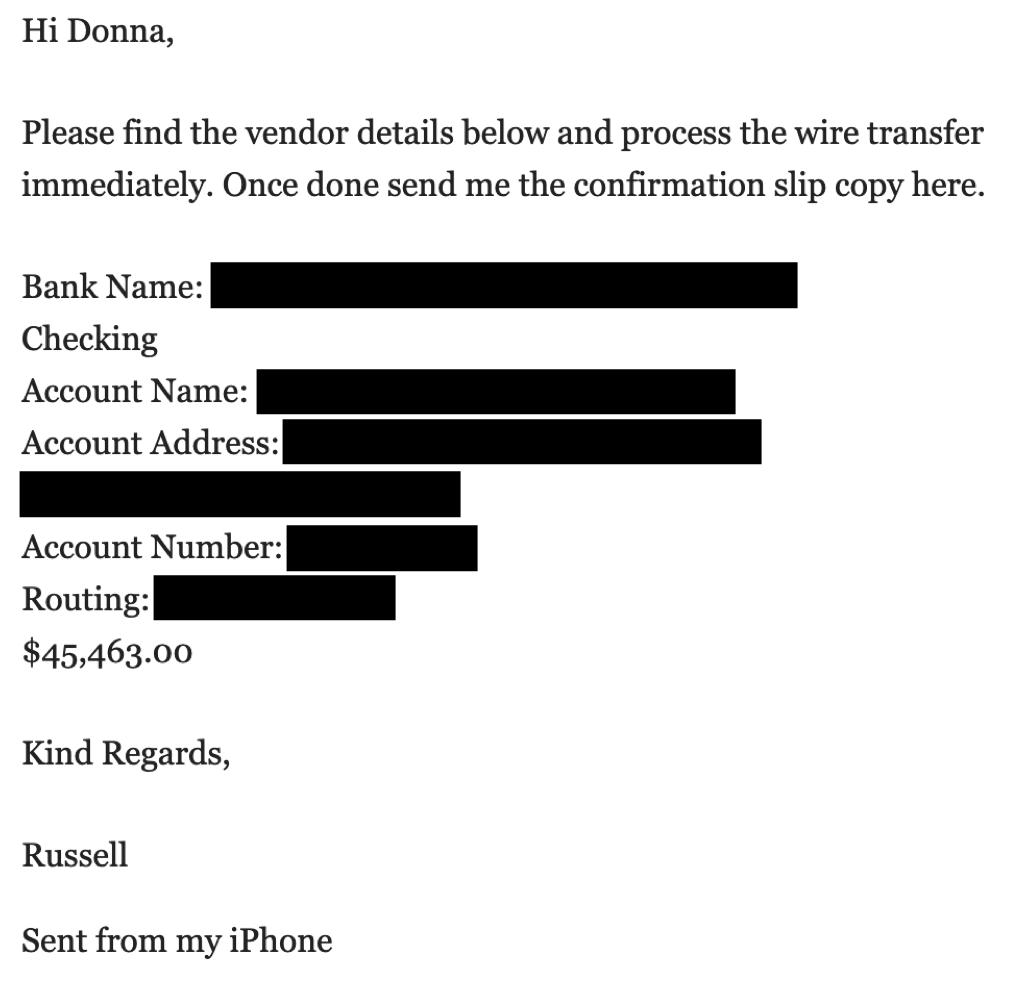
Have you ever been literally kidnapped and held at ransom by a client? I have!
We arrived, the app wasn't ready.
BC finds out that testing hasn't started and starts yelling, mostly at our contact, then turns to us and talks like the guy isn't there and derides him. Asshole.