⚠️URGENT⚠️
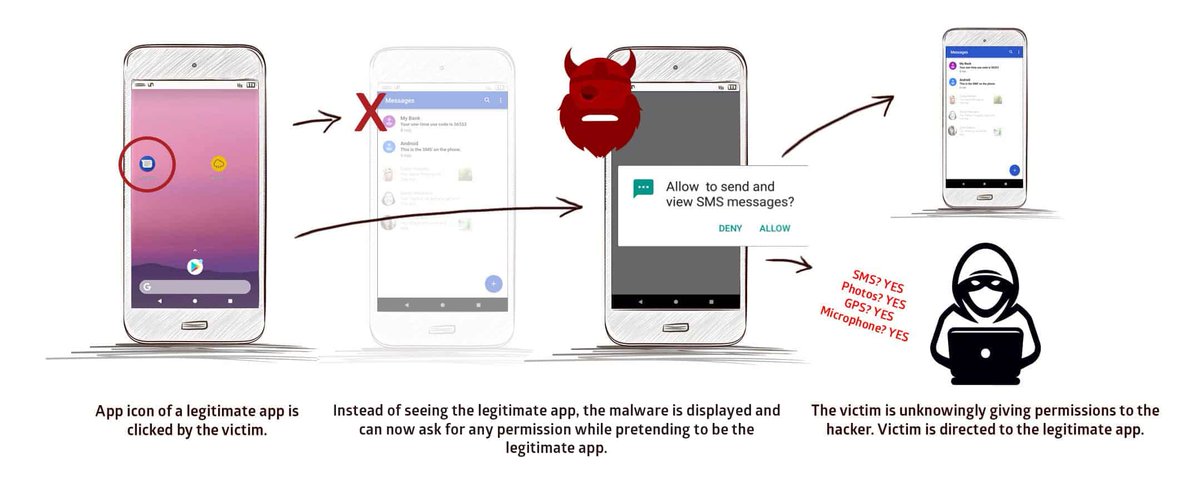
Hackers exploit #Solorigate supply-chain backdoor in #SolarWinds enterprise monitoring software to breach US Treasury, Commerce Department, other government agencies, and cybersecurity firm #FireEye.
Details: thehackernews.com/2020/12/us-age…
#infosec #cybersecurity #sysadmin
Hackers exploit #Solorigate supply-chain backdoor in #SolarWinds enterprise monitoring software to breach US Treasury, Commerce Department, other government agencies, and cybersecurity firm #FireEye.
Details: thehackernews.com/2020/12/us-age…
#infosec #cybersecurity #sysadmin
Citing unnamed sources, media said the latest cyberattacks against #FireEye and U.S. government agencies were the work of Russian state-sponsored #APT29 or Cozy Bear #hacking group.
According to FireEye, attackers tampered with a #software update released by #SolarWinds, which eventually led to the compromise of numerous public and private organizations around the world with #SUNBURST backdoor.
thehackernews.com/2020/12/us-age…
#infosecurity
thehackernews.com/2020/12/us-age…
#infosecurity

The affected versions (2019.4 through 2020.2.1) of SolarWinds Orion Platform software were released between March and June 2020, and sysadmins are recommended to upgrade it to release 2020.2.1 HF 1 immediately.
thehackernews.com/2020/12/us-age…
thehackernews.com/2020/12/us-age…
• • •
Missing some Tweet in this thread? You can try to
force a refresh