
#WAGSI🛡️
Exploiters minted over 1 Billion in $GALA tokens on BSC & fears caused a 20% drop in GALA.
The problem is caused by a misconfiguration of the @pNetworkDeFi bridge.
#GALA #galatoken #breach
🧵👇
Exploiters minted over 1 Billion in $GALA tokens on BSC & fears caused a 20% drop in GALA.
The problem is caused by a misconfiguration of the @pNetworkDeFi bridge.
#GALA #galatoken #breach
🧵👇
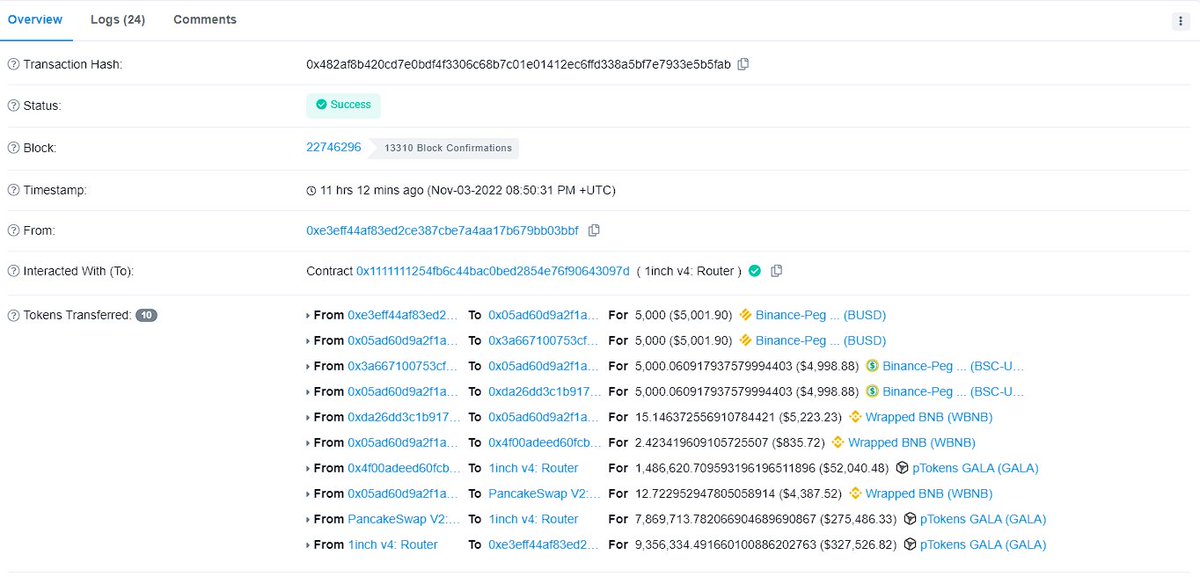
➡️ Hackers immediately sent the freshly minted GALA to #PancakeSwap.
➡️ The attacker dumped a total of 10.72 billion $GALA and earned a total of 12,977 billion $BNB ($4.4 million) by draining the PancakeSwap pool to zero.
#news #Hack
➡️ The attacker dumped a total of 10.72 billion $GALA and earned a total of 12,977 billion $BNB ($4.4 million) by draining the PancakeSwap pool to zero.
#news #Hack
@pNetworkDeFi stated that a new pGALA token will be created to replace the old compromised one and will be airdropped to those who had pGALA before the pool was drained in the coming days.
#DeFi #cryptocurrecy
#DeFi #cryptocurrecy
Follow @QuillAudits on Twitter and telegram to stay updated
Protect your Web3 Project with us -
audits.quillhash.com/smart-contract…
#cybersecurity #blockchain #quillaudits #smartcontract #security #smartcontractaudit
Protect your Web3 Project with us -
audits.quillhash.com/smart-contract…
#cybersecurity #blockchain #quillaudits #smartcontract #security #smartcontractaudit
• • •
Missing some Tweet in this thread? You can try to
force a refresh










