Discover multinational #InfluenceOperations at work. See how #Iran and #Venezuela can use state-sponsored media outlets, social media influencers, proxies, surrogates, and political activists in the #AlexSaab influence campaign. Read full report: bit.ly/3EPYPhv 1/8 

Insikt Group® identifies four phases of a multiyear influence campaign centered around indicted Alex Saab, the alleged financier and special agent to Iran for the Nicolás #Maduro regime. The Alex Saab timeline shows significant events from indictment to postponed trial. 2/8 

Saab, an alleged conduit of Hezbollah operations extending into Latin America, is a Colombian and Venezuelan businessman wanted by Colombian law enforcement since 2018. Maduro appointed him a special envoy to Iran after a corruption designation (by OFAC). 3/8
Initial misinformation campaigns likely began in Nigeria and amplified with #astroturfing by a firm in Ghana. Venezuela then hosted a concert to support Saab that provided psychological action by social media users and traditional media, pushing the disinformation narrative. 4/8 
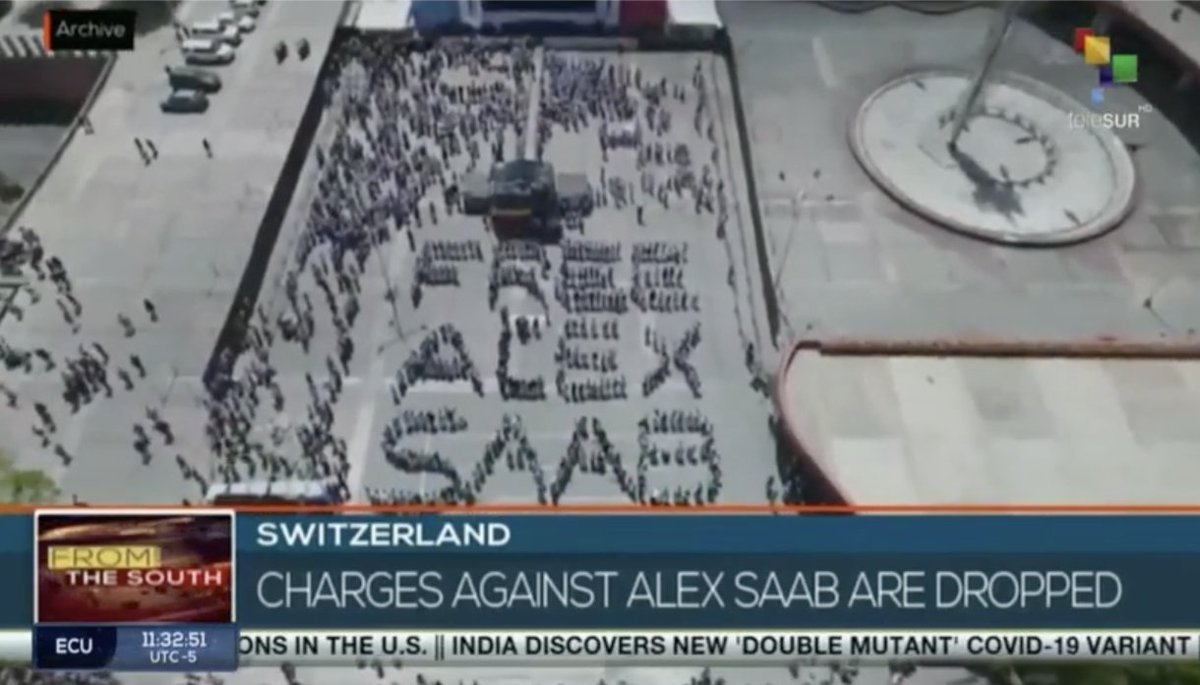
On August 16, 2021, Iranian Foreign Ministry Spokesman Saeed Khatibzadeh denounced the US extradition of Saab. The following day, Venezuela’s teleSUR published a disinformation article titled “Venezuelan Diplomat Alex Saab Is a Prisoner of War, Iran Says” 5/8 

The misinformation narrative propagated through proxies, surrogates, and political activists with the central nodes for analyses pictured in this map of Iranian and Venezuelan media organizations involved in the Saab #disinformation narrative. 6/8 

Influence efforts expand beyond the Saab influence campaign. We identified 4 identical disinformation articles authored by Pablo Jofre Leal, published by Al Mayadeen, SANA, hispanTV, and SegundoPaso on “Washington and its destructive obsession with Venezuela”. 7/8 

The Saab disinformation campaign will likely continue with the purpose to pressure the US to negotiate an exchange for Saab, as well as amplify anti-US messaging to Latin American audiences. Read the report that details the four phases: bit.ly/3EPYPhv 8/8 

• • •
Missing some Tweet in this thread? You can try to
force a refresh