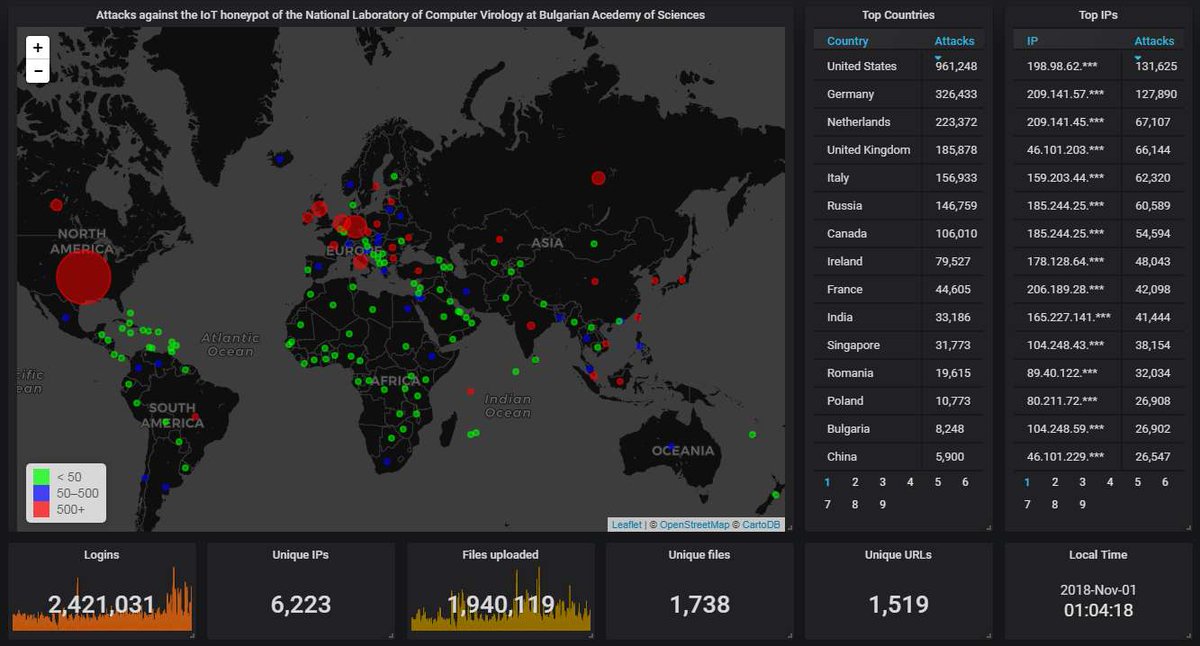
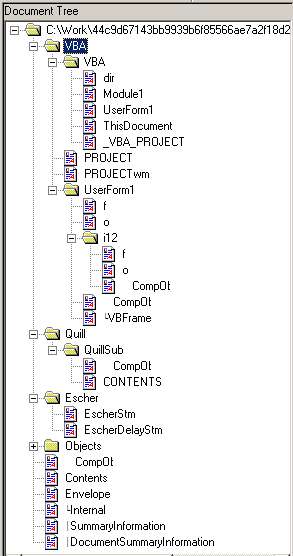
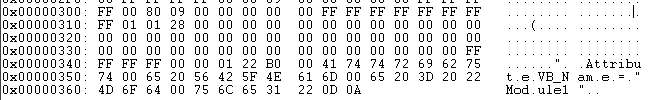
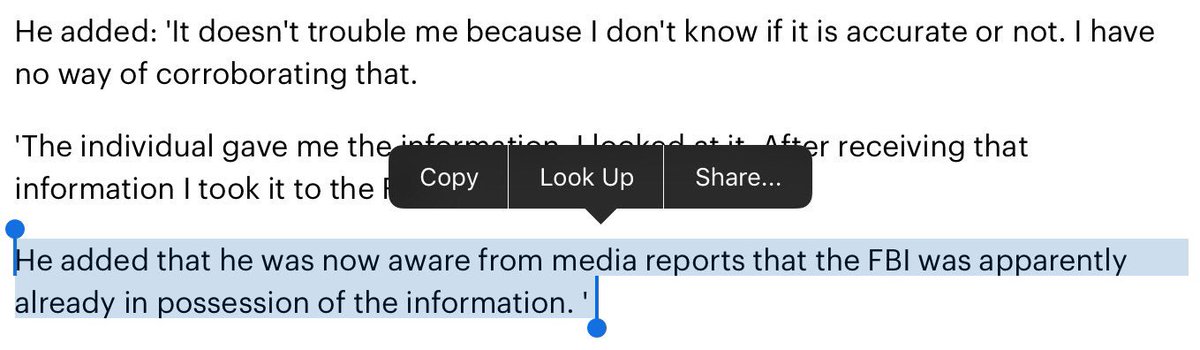
Gather 'round the fire, kids, for a short story, because I was around at the time.
I first heard of McAfee Associates and the anti-virus program SCAN in 1989.
So, what did McAfee invent? A couple of things.
But what if a bad guy took a copy of the software and modified it to do something bad? Clearly, some form of ensuring its integrity was needed.
Do you see a problem with this approach yet? Hold my beer, we're far from finished.
End of story.