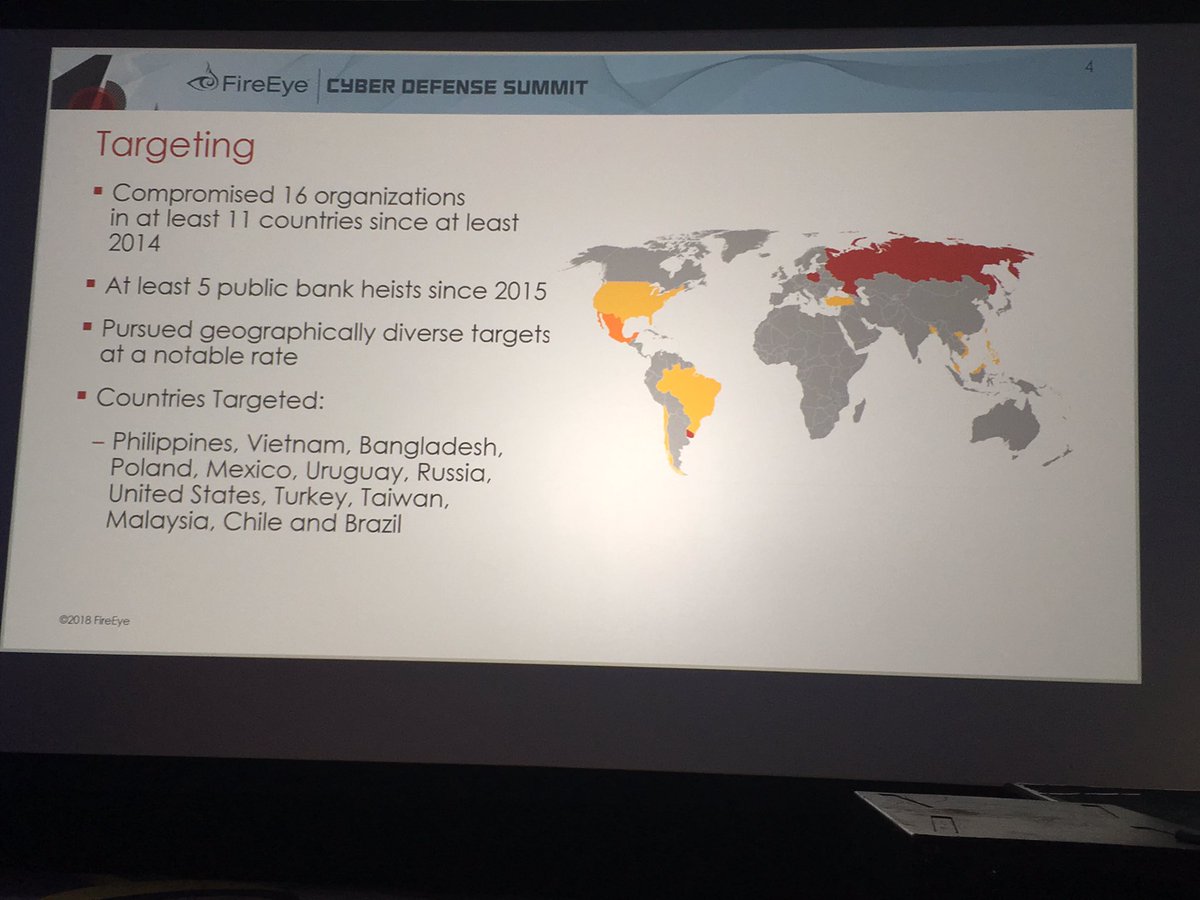
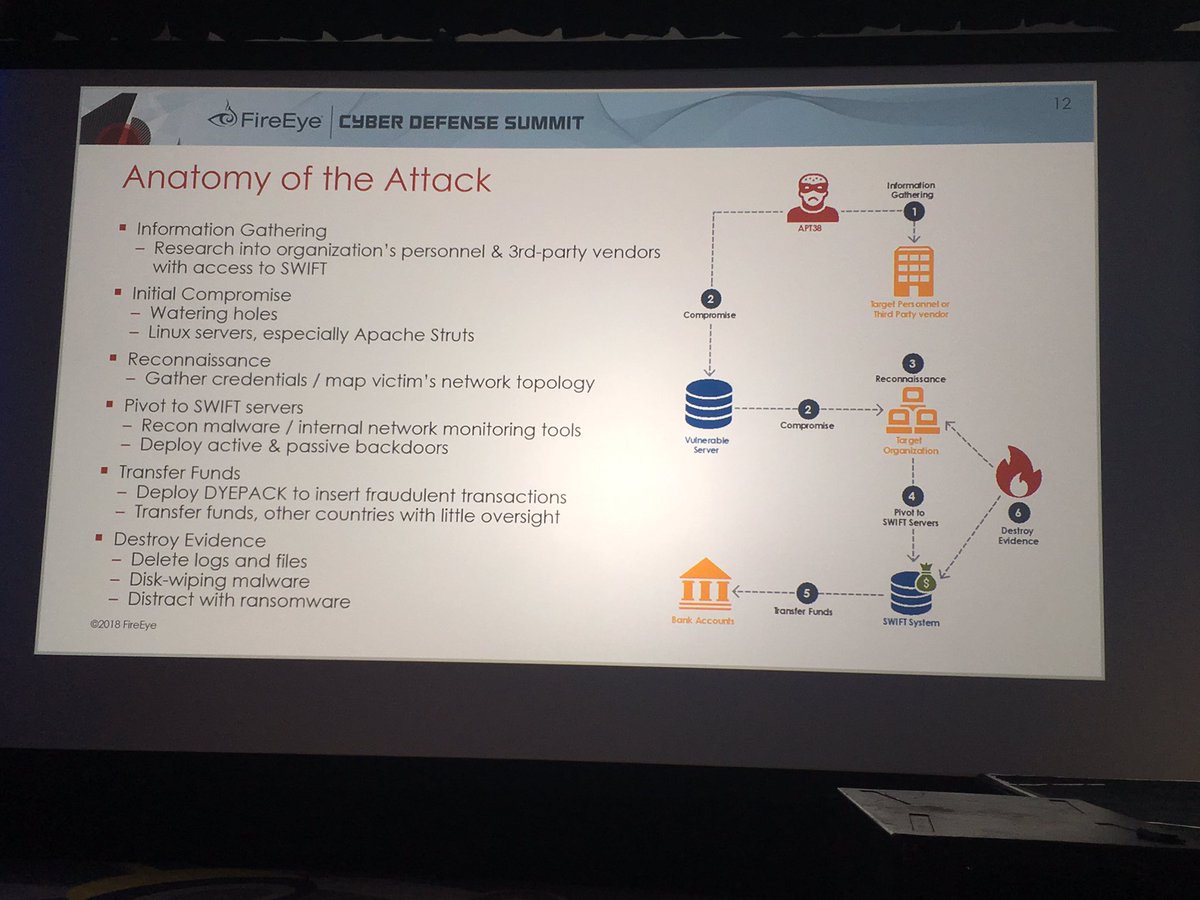
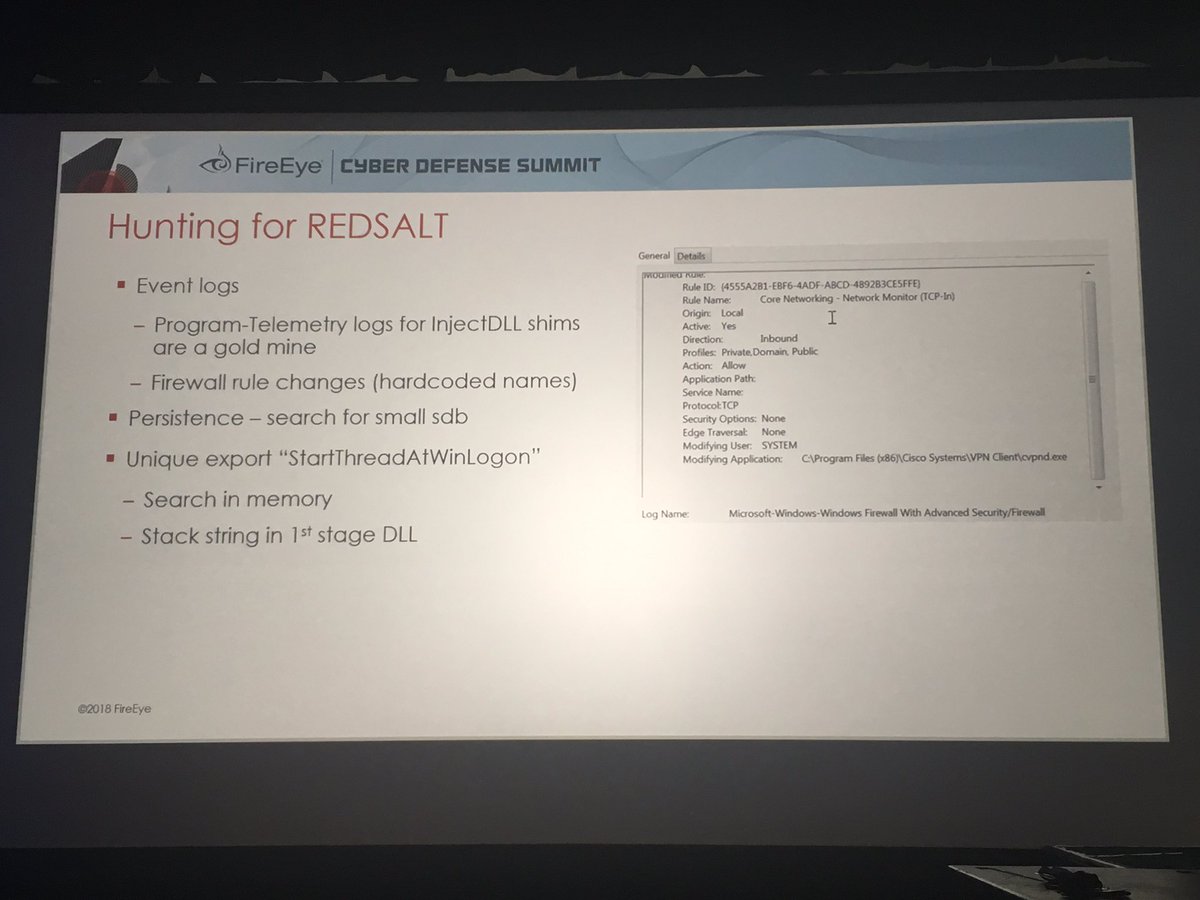
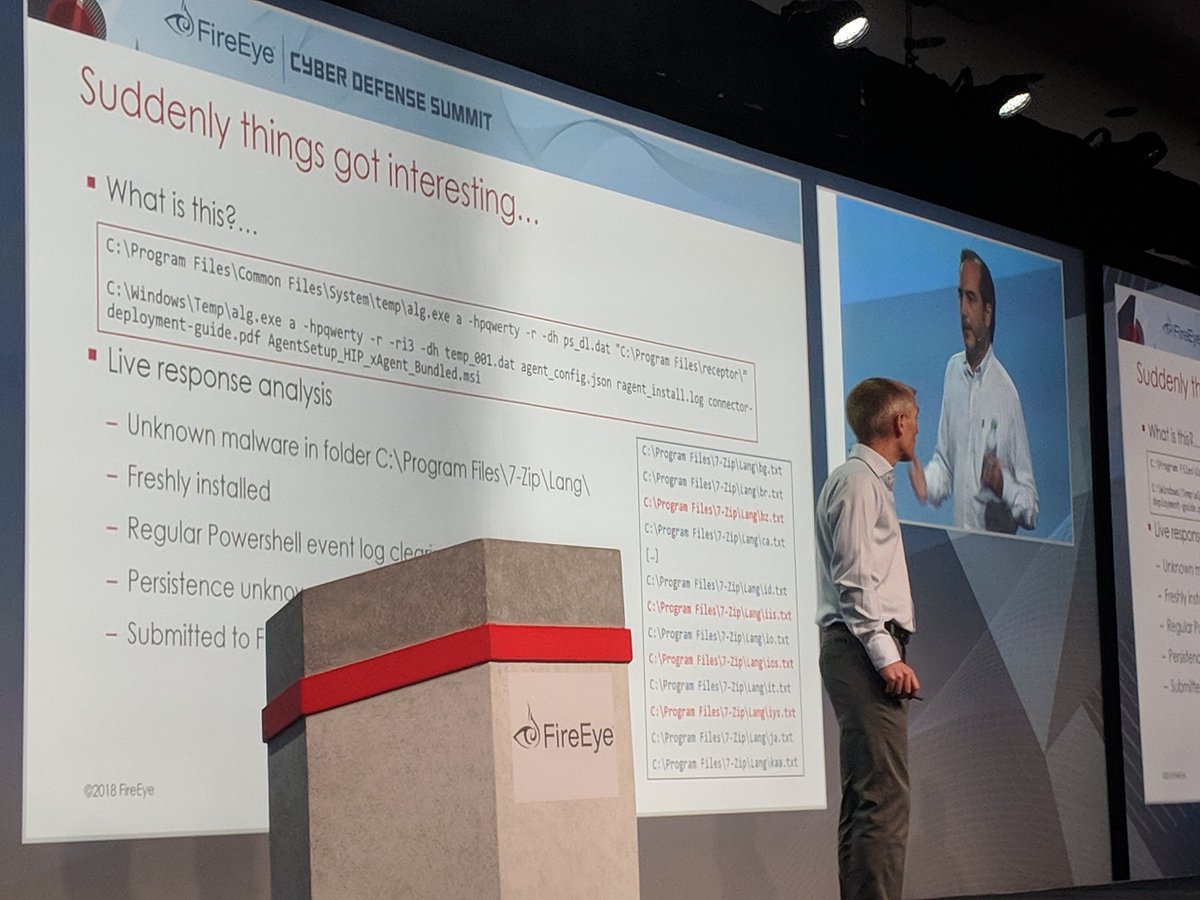
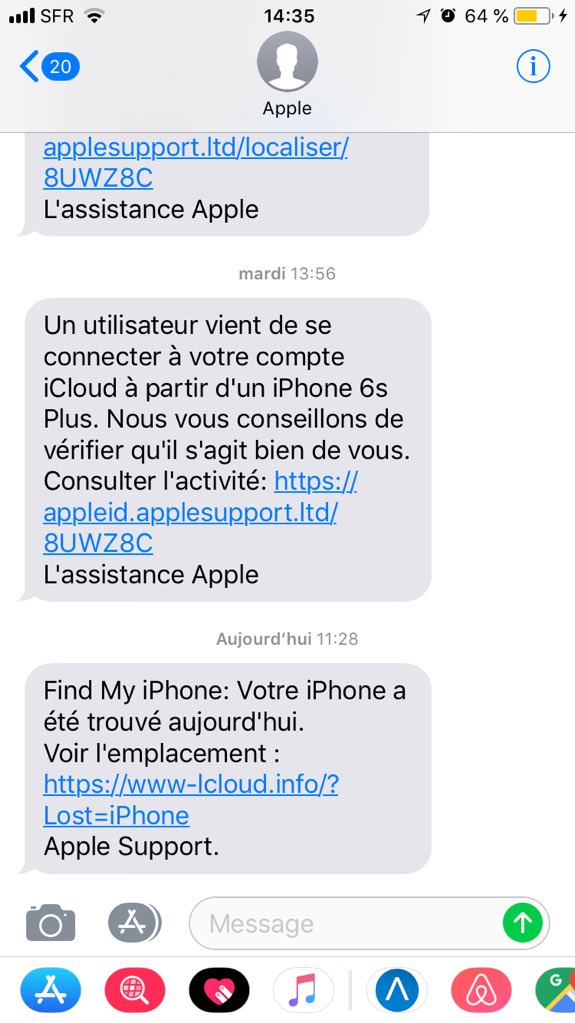
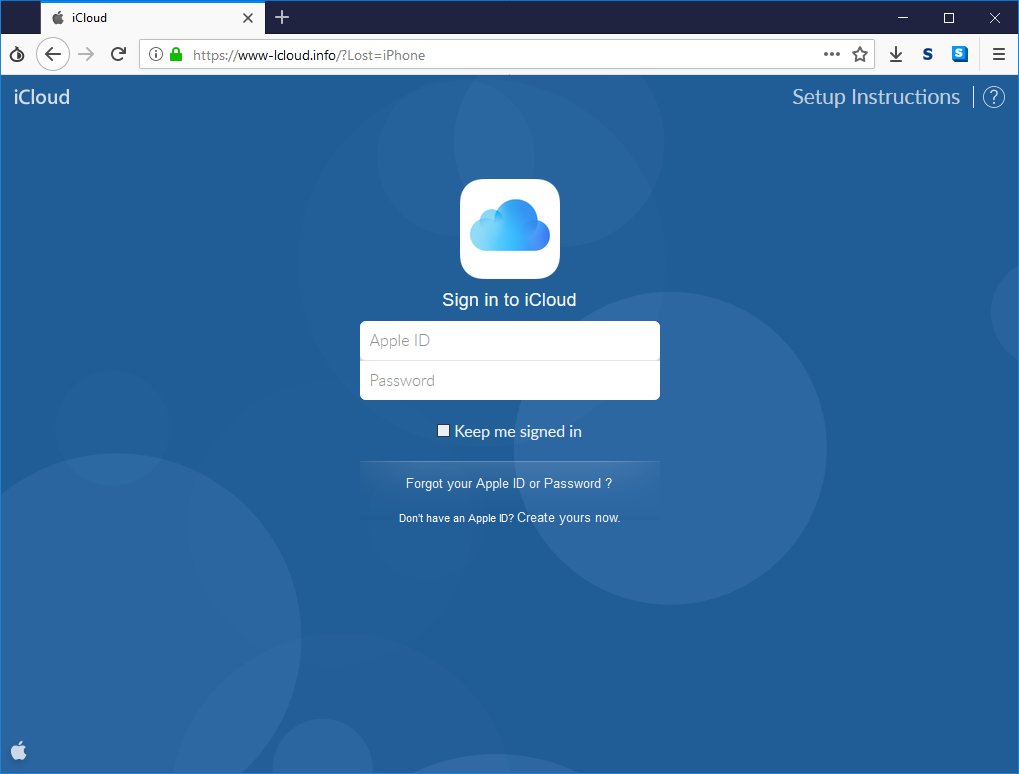
@danielcabaniel @CyberAmyntas discussing email phishing and mail server attack trends
#FireEyeSummit
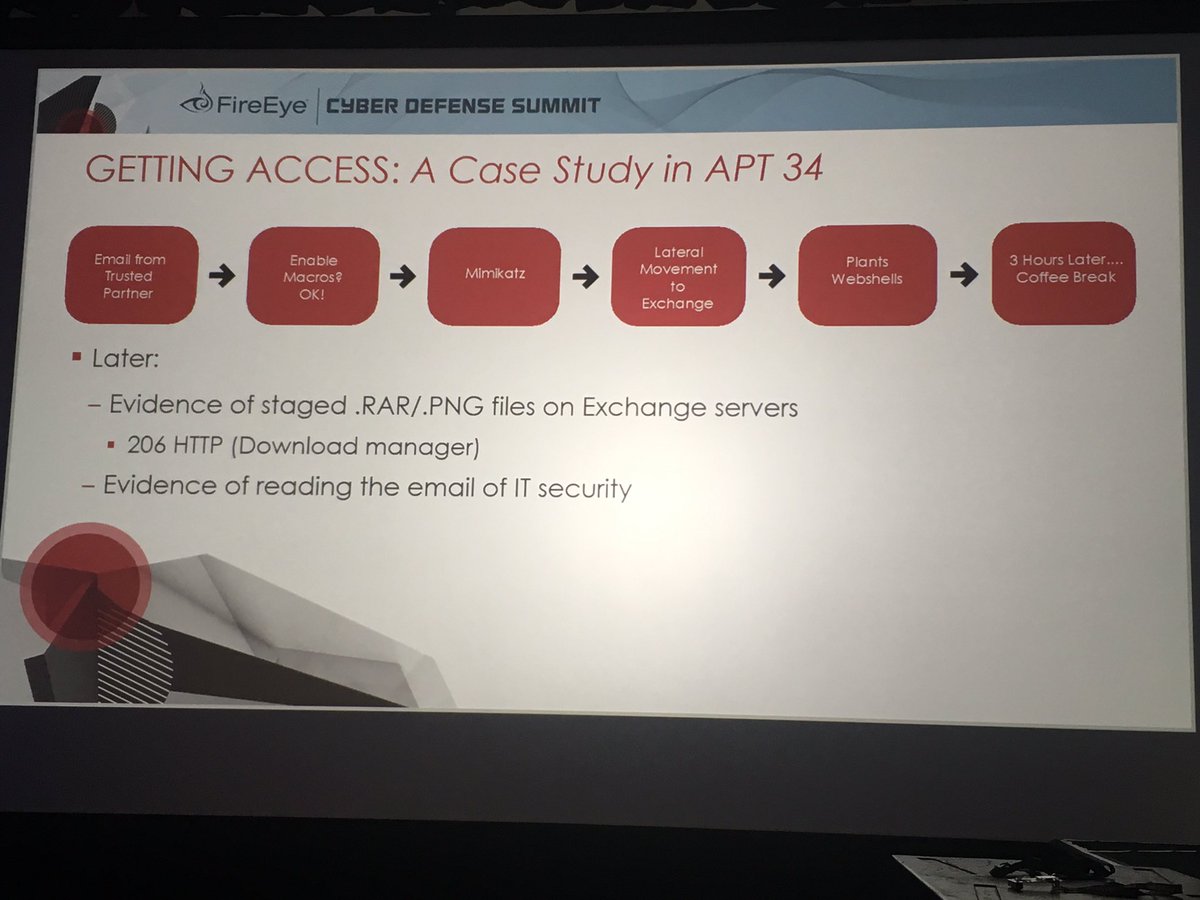
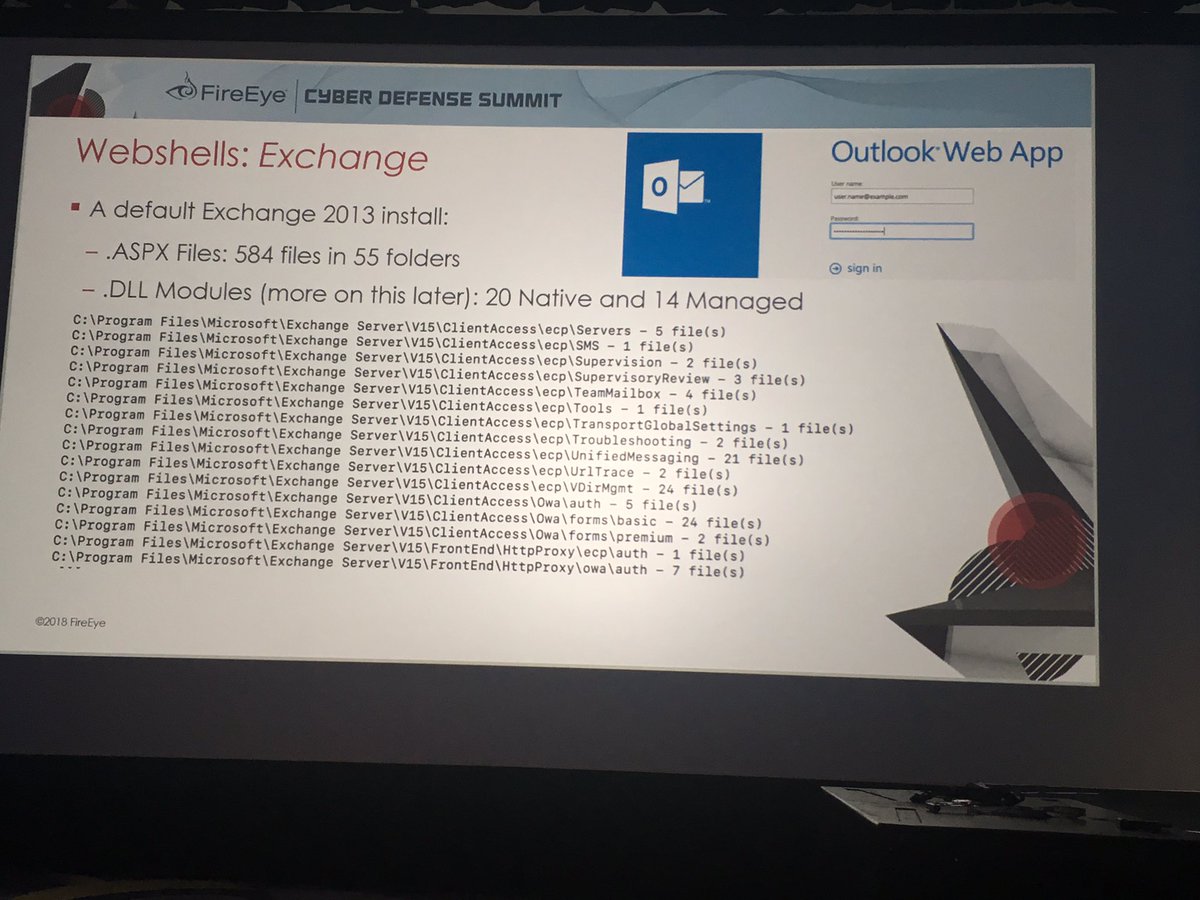
Subsequently staged data theft files on the Exchange server as .png files and downloaded from the server.
#FireEyeSummit
#FireEyeSummit
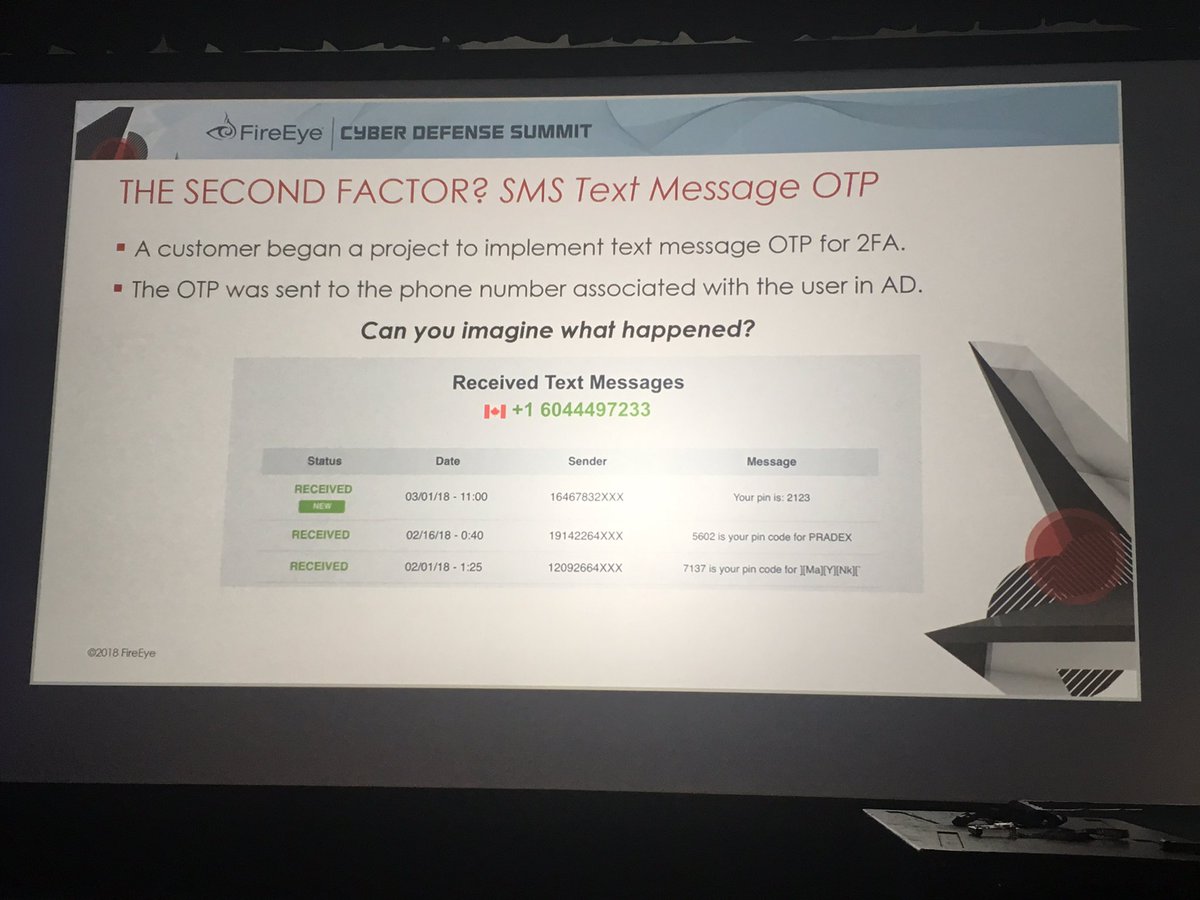
Screenshot is of a Canadian phone number accessing 2FA. Organization didn't have any presence in Canada.
#FireEyeSummit
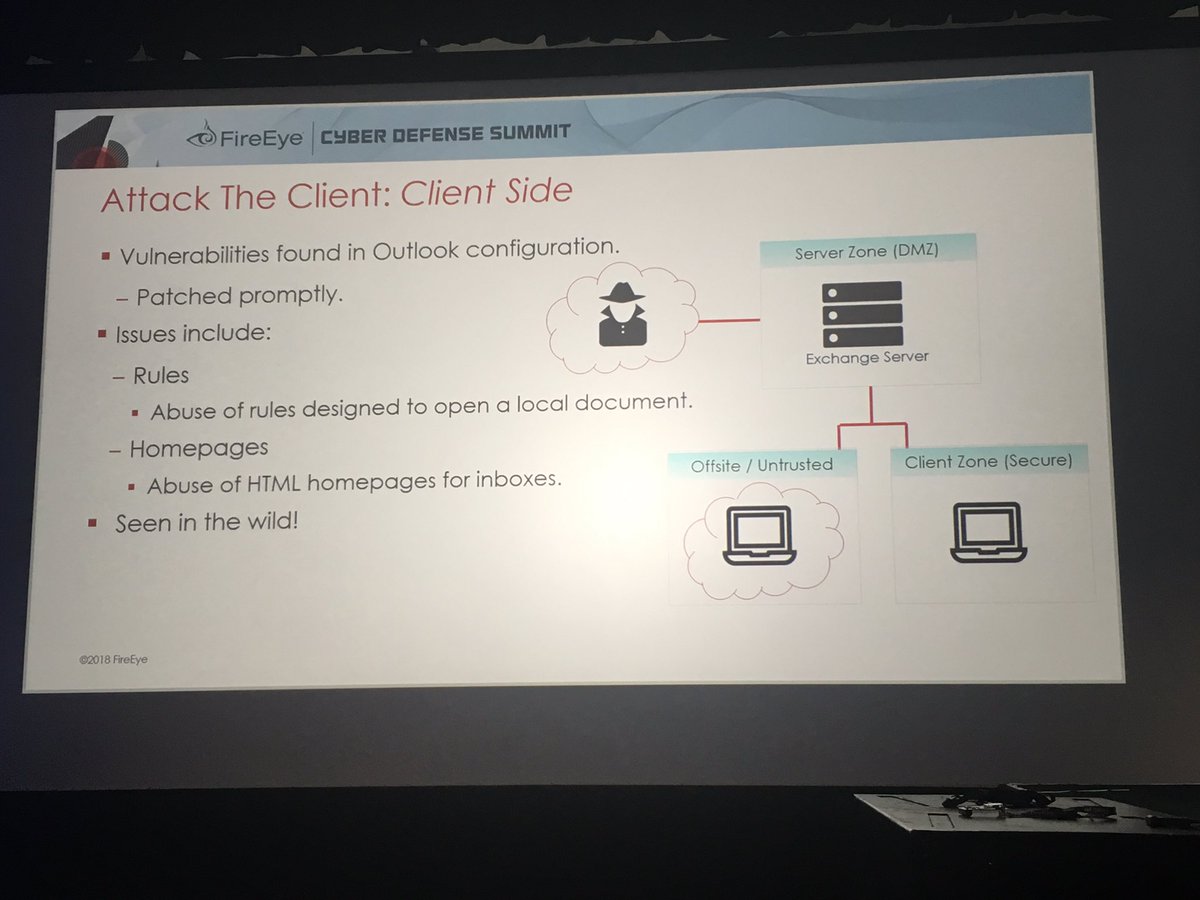
"This has been patched but we still see it leveraged b/c most orgs haven't applied patch"
Just by obtaining user email creds you can get code execution on victim machine using something like a COM scriptlet #DailyScriptlet
#FireEyeSummit
#FireEyeSummit
#FireEyeSummit
#FireEyeSummit