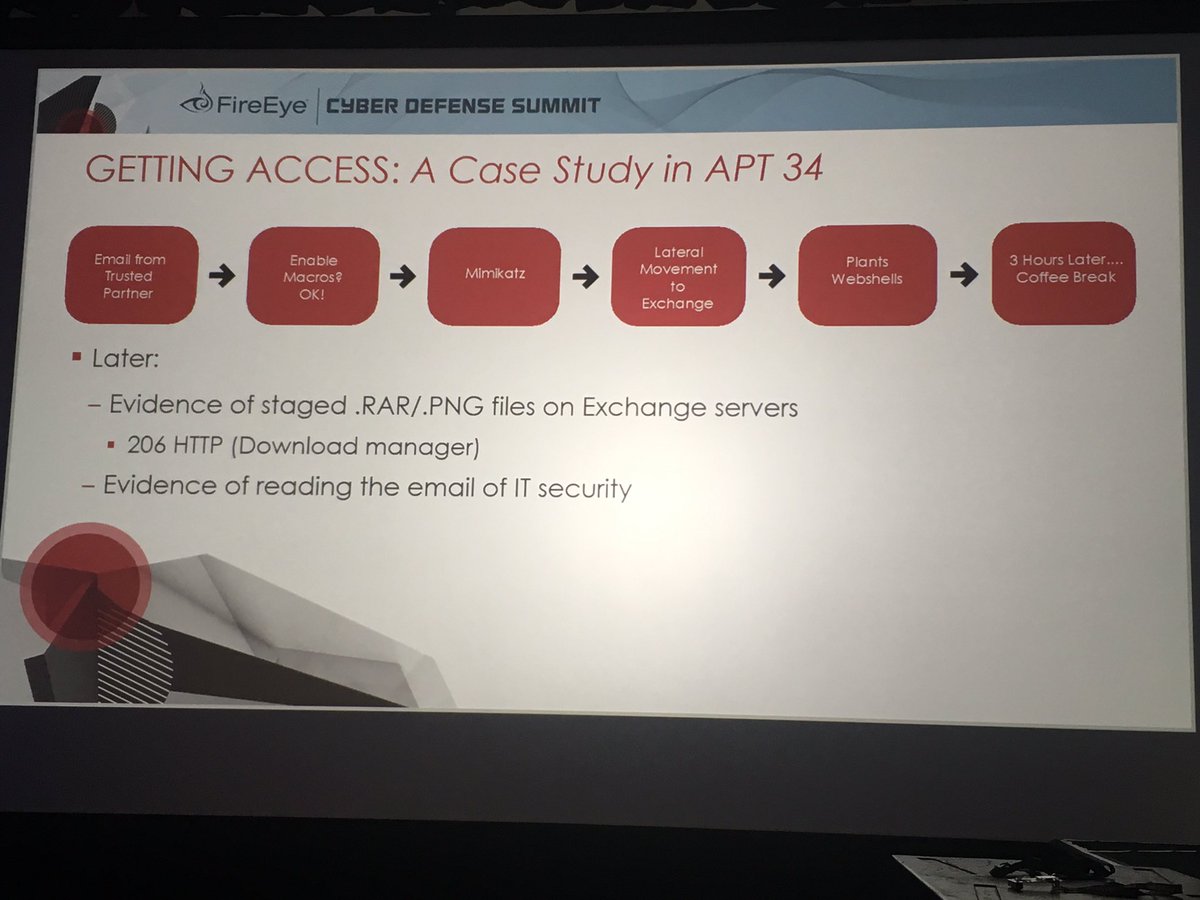
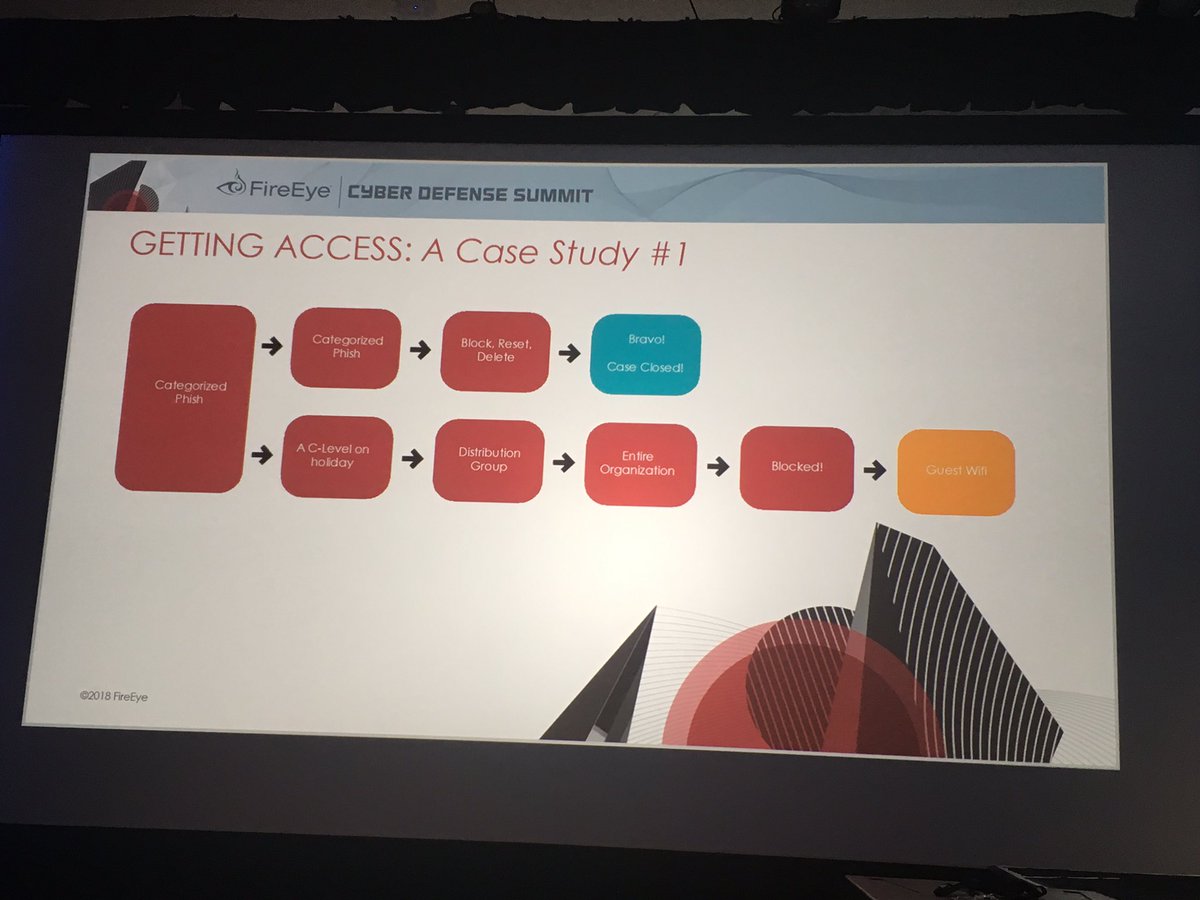
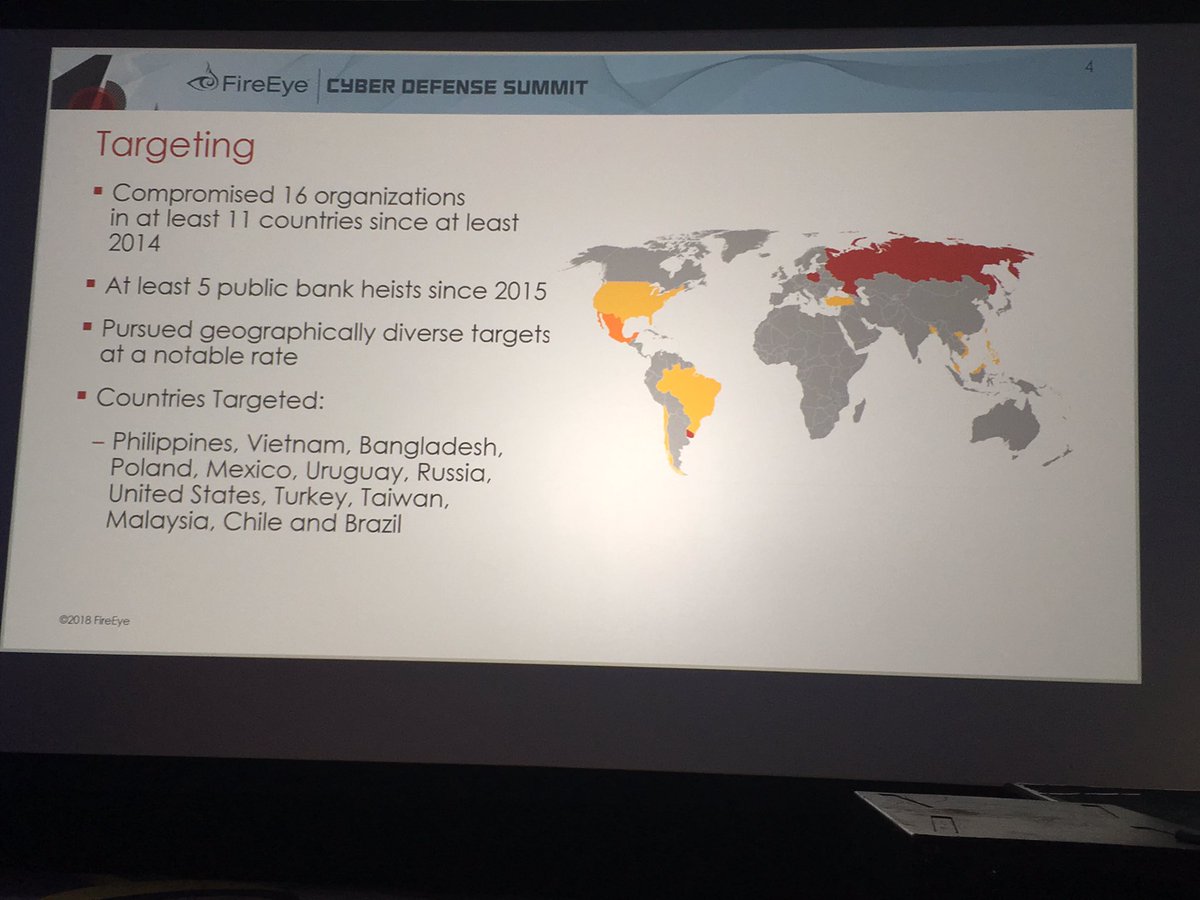
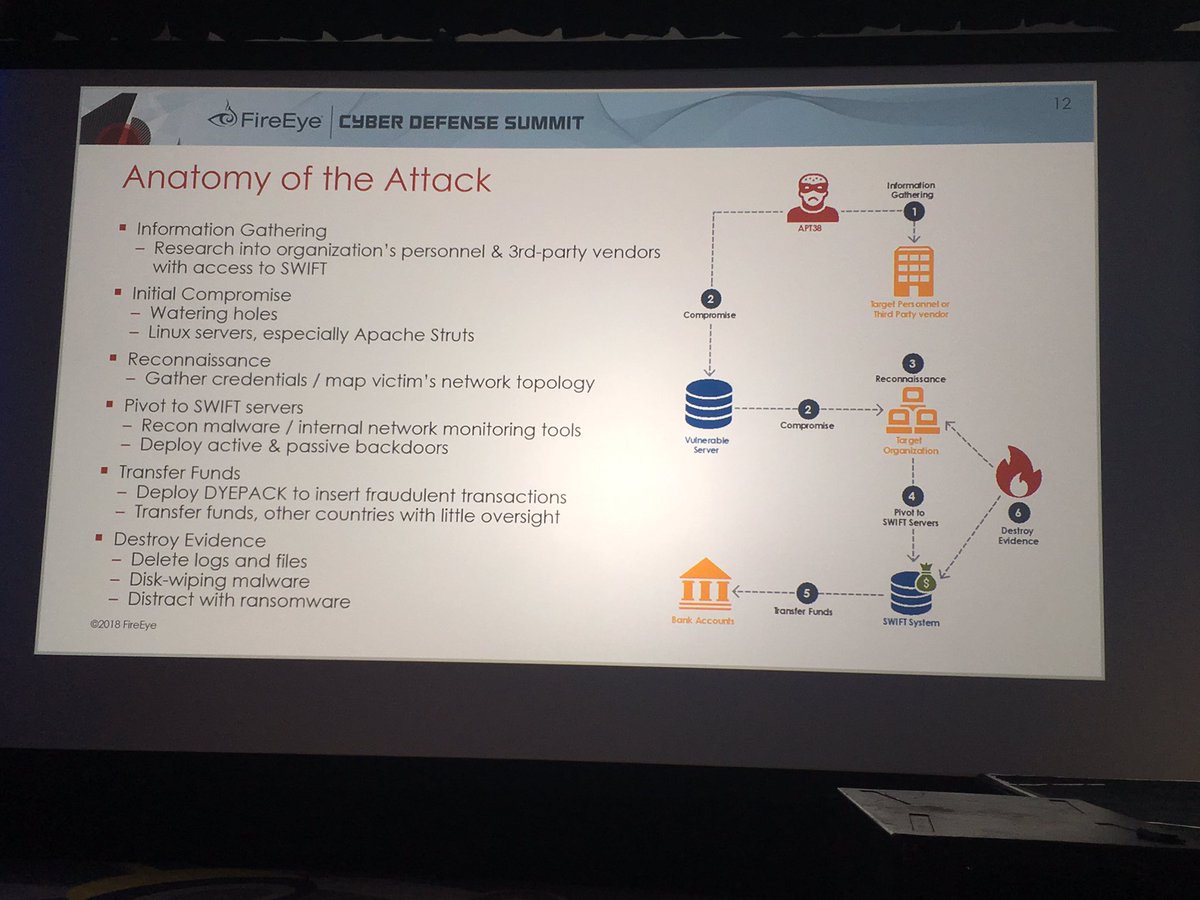
-the indictment indicates #APT10 operations started in 2006 and went through 2018. The 2006 activity was likely focused on US Government, Military, and defense contractors
1/n
@NASAGoddard, @NASAJPL, @LLNL, and the @USNavy
2/n

5/n
en.wikipedia.org/wiki/Operation…
6/n
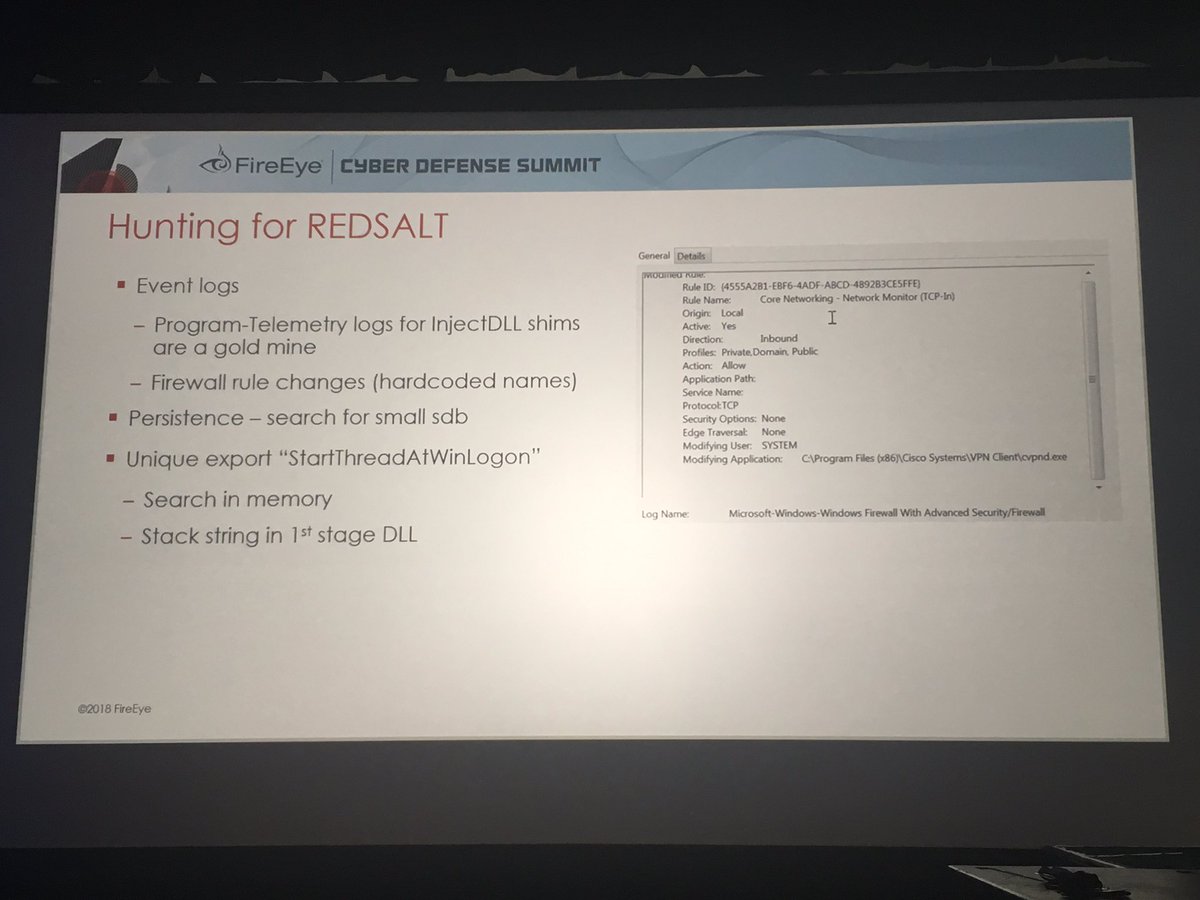
8/n
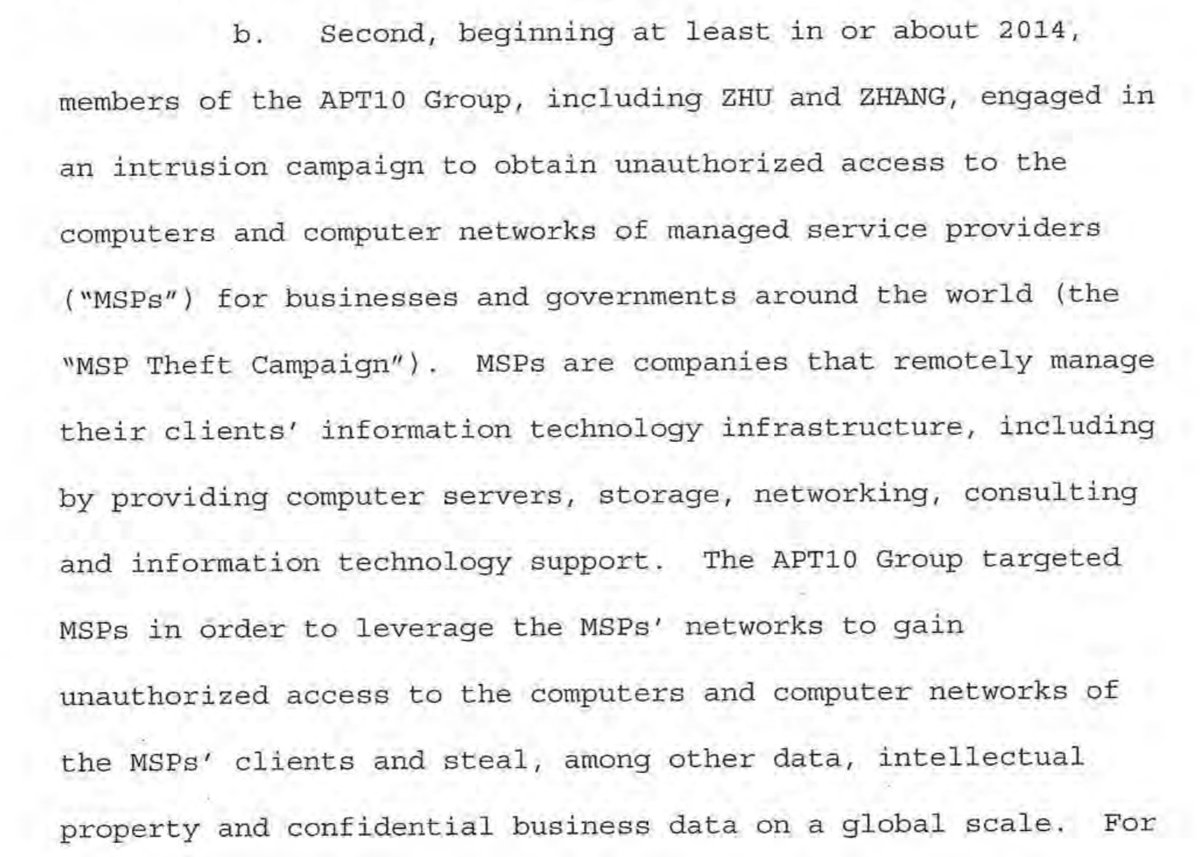
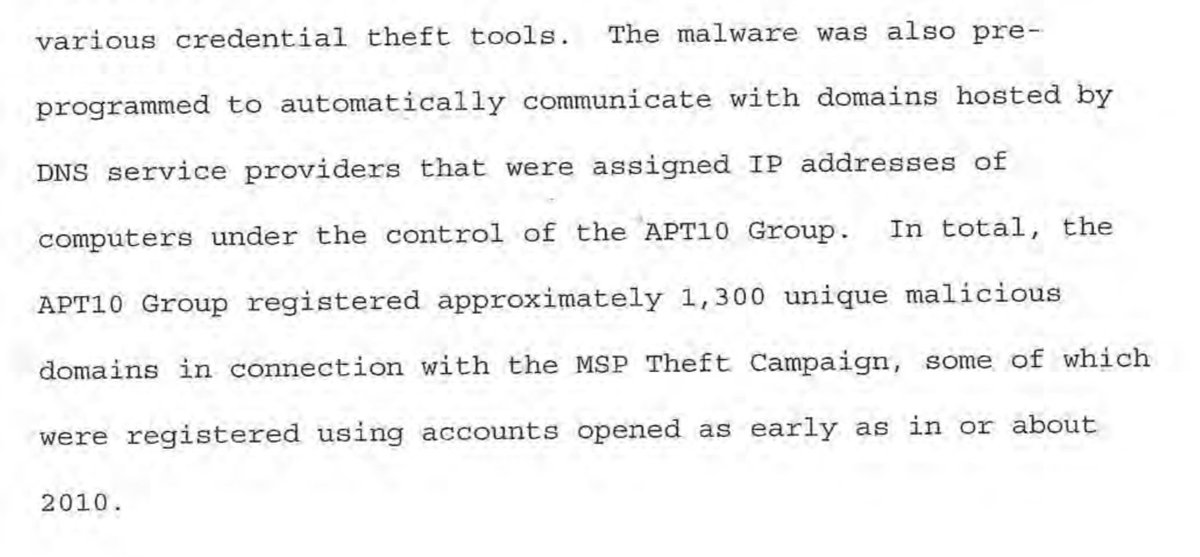
9/n
10/n
"We also discuss two trends that we see year after year, as part of our “Trends Turned Constants” section. One involves leveraging third-party service providers to gain access to victim organizations."
fireeye.com/blog/executive…
baesystemsai.blogspot.com/2017/04/apt10-…
pwc.co.uk/issues/cyber-s…
If your network accessed by #APT10 through your MSP:
2) how would you detect it?
3) is your MSP legally obligated to notify you?
4) what contractual remedies do you have if it happens or if they don't notify you?
13/n
14/n
In contrast the Russian cyber indictment called out the GRU directly
16/n
intrusiontruth.wordpress.com/2018/08/09/was…
17/n
"APT10 spear phishes...leverag[ed] .lnk files within archives"
.lnk files in archives...where have I seen that recently (*cough* APT29)?
fireeye.com/blog/threat-re…
17/n
fireeye.com/blog/threat-re…
fireeye.com/content/dam/fi…
18/n
19/n
fireeye.com/blog/threat-re…
Great Tweet by @RidT demonstrating impact of CN APT against German orgs
20/n
@smoothimpact brought up a good point. Although #APT10 is prolific at targeting MSPs. Many other CN APT groups (e.g. APT22) & other nations target MSPs regularly
22/n
fireeye.com/content/dam/fi…