Watch live: justice.gov/live
"The evidence suggests that China may not intend to abide by its promises."
“In some cases, we know exactly who is sitting at the keyboard perpetrating these crimes in association with the Chinese government.”
justice.gov/opa/press-rele…
APT10 hackers allegedly engaged in two parallel IP theft campaigns.
One, beginning in 2006, targeted companies directly.
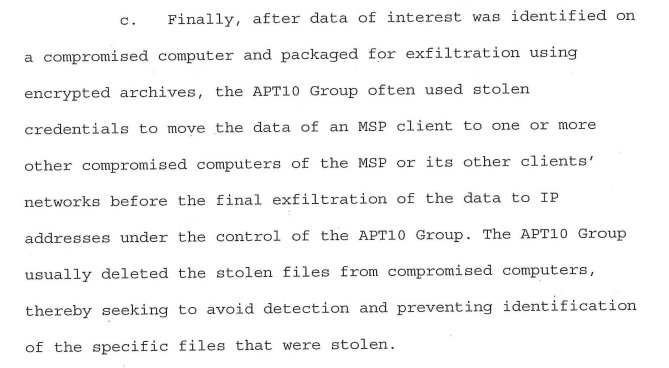
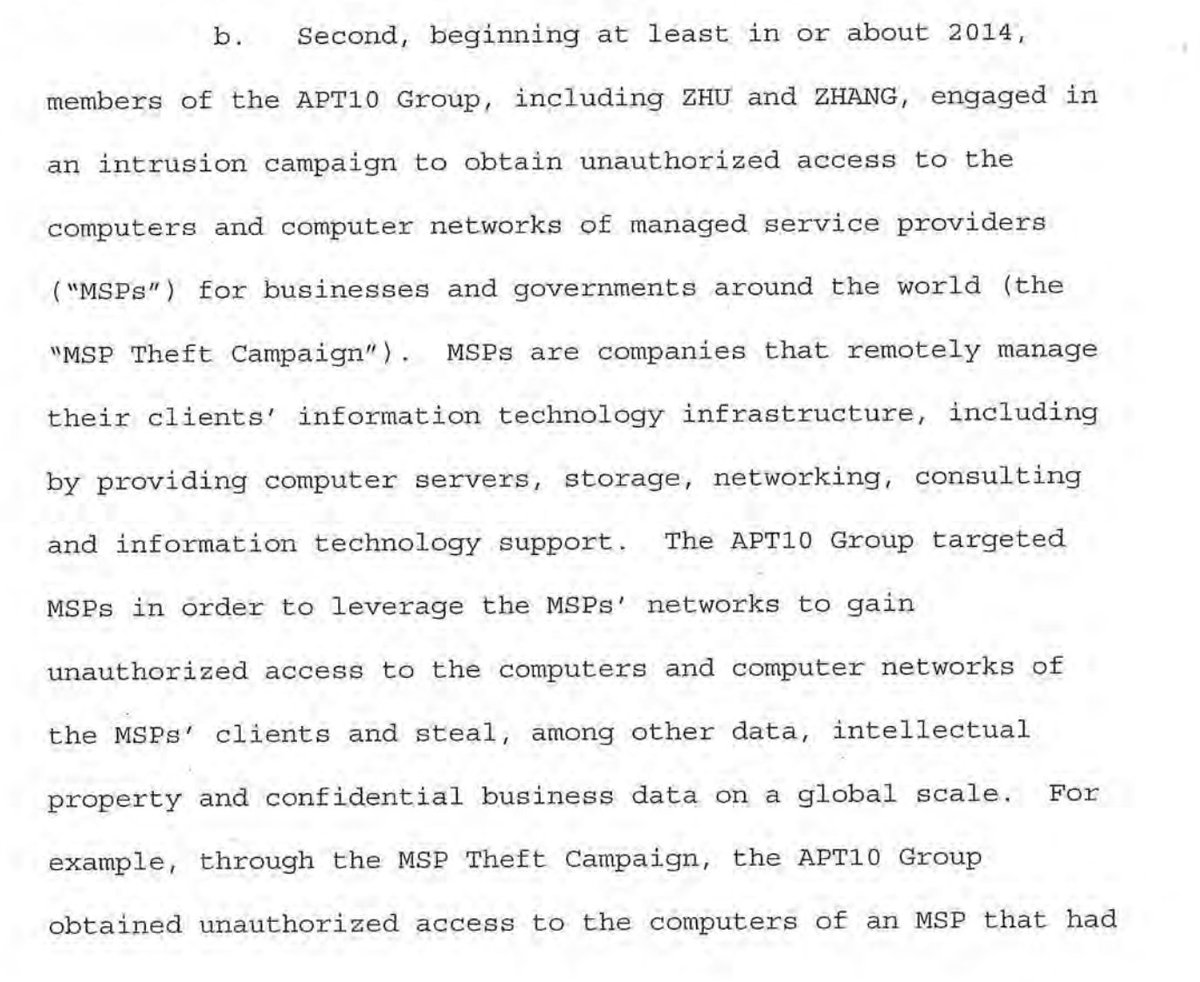
The other, beginning in 2014, targeted companies through their MSPs.




2014 campaign led to theft of data from MSP clients in 12 countries.
1. Spearphish targets
2. They unwittingly download malware, including Remote Access Trojans and keyloggers
3. Malware gives the hackers access to their victims' machines
4. They install more malware
5. They exfiltrate data
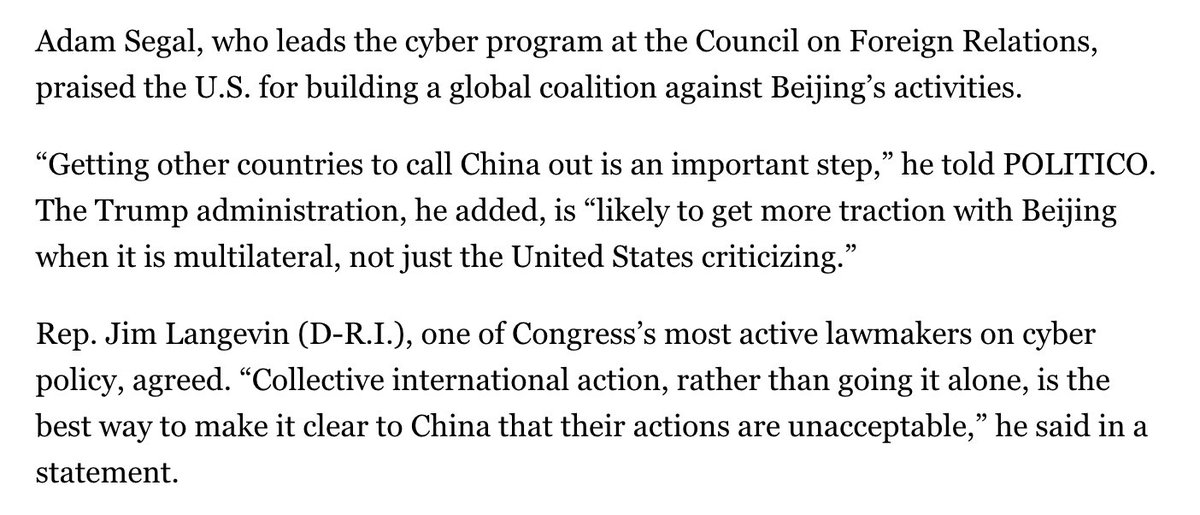
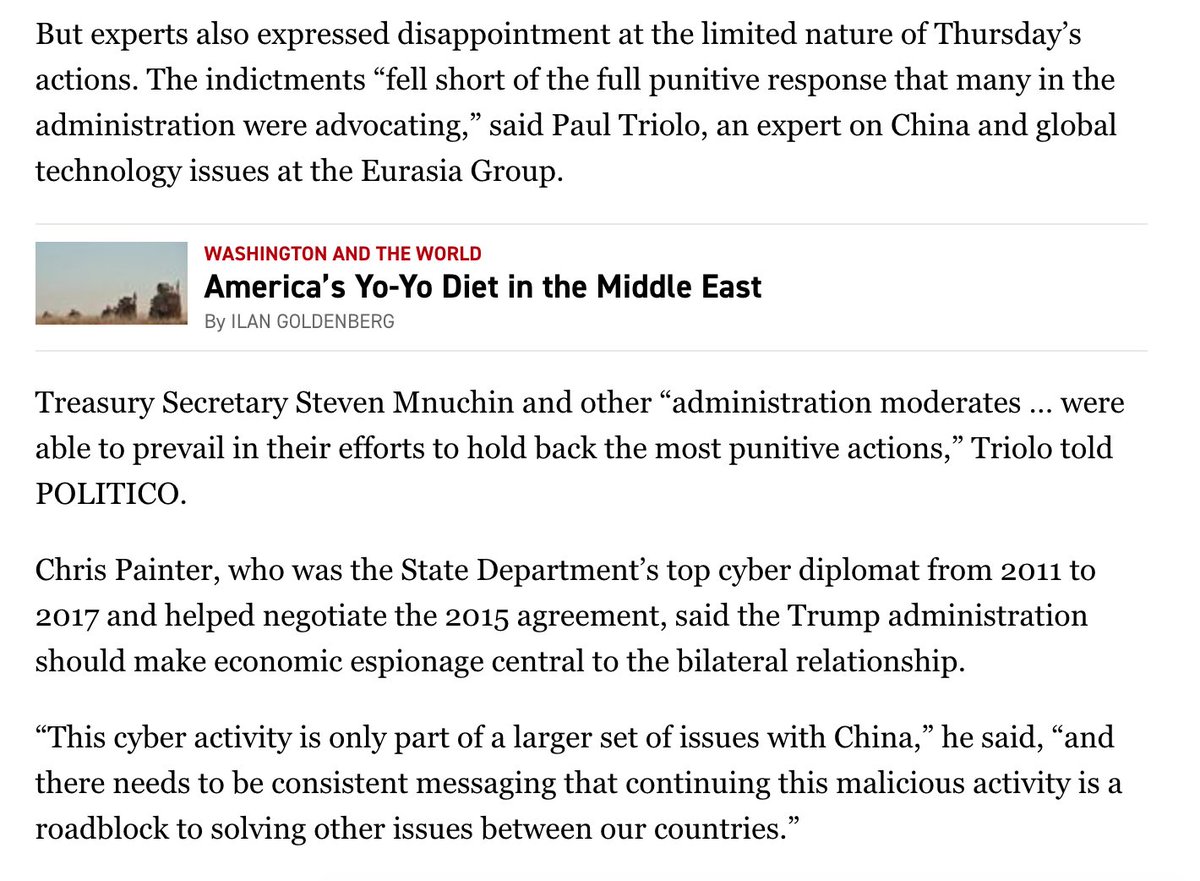
Other possibilities today: Declassified intelligence showing the links to China, and sanctions on the Chinese companies that benefited.
Stay tuned.

Folks are impressed by the charges and the international condemnation, but describe this as — so far — a missed opportunity.