Investigating the issue. All my contracts on EOS mainnet has stopped because of network congestion.
These are attacker's accounts:
eosflare.io/account/mumach…
eosflare.io/account/gotowo…
eosflare.io/account/mumach…
eosflare.io/account/mumach…
eosflare.io/account/mumach…
eosflare.io/account/mumach…
eosflare.io/account/mumach…
eosflare.io/account/dswinn…
eosflare.io/account/eospla…
probably even more...
1. Rented a huge amount of CPU and NET at #EOSREX resource exchange.
2. Staked CPU&NET for (1) himself and (2) attacked contract.
3. Congested the network.
4. Initiated some transactions to the attacked contract. Won a lot of $EOS in gambling DApps.
1. By congesting the network the attacker disallowed anyone to send transactions because transaction cost is too high for most of the users.
Probably the RNG of attacked gambling DApps could use some transactions or data from earlier blocks as a source of entropy.
It's easier to manipulate "previous blocks" when the network is congested and you are the only one having resources to send transactions.
I.e. if you are the only one who sends transactions and RNG relies on transactions(or blocks) as a source of entropy, you can manipulate RNG and set winning conditions, and then receive all winnings. Devs could not redeploy the contract due to lack of resources.
@binance @bitfinex @Poloniex @HuobiGlobal @OKEx @OKCoin @kucoincom @C2CXExchange @BittrexExchange
Network congestion makes (1) hacker and (2) attacked DApp the only users of the network who had enough CPU to operate. This prevents contract developers from redeploying the contract and stopping the attack when they recognized the issue.
The attacker did not use the previous blocks as I thought initially. He fills future blocks with the transaction he needs instead.
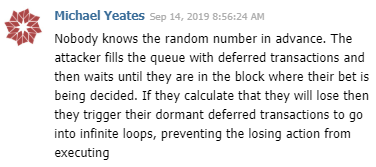
To smart-contract devs:
1. Follow best security practices.
2. Do not rely on on-chain source of entropy in EOS.