(ordered by cost-benefit ratio / volume > detectable threats)
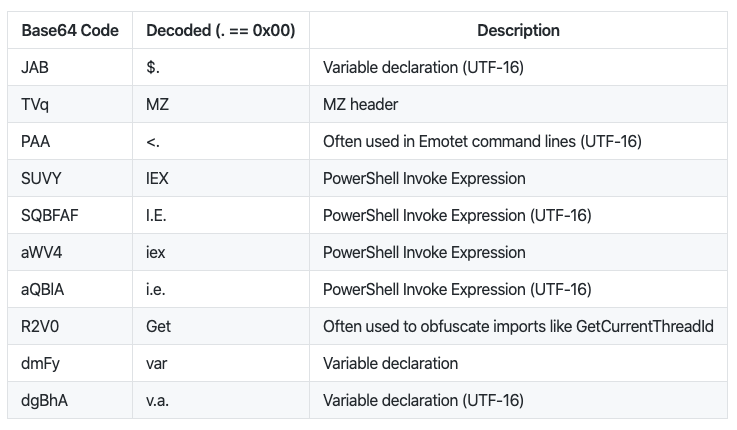
1. Antivirus
2. Windows Eventlog (+Sysmon)
3. Proxy
4. Firewall
5. DNS
In general: I included only those logs that can already be collected in most organizations, when you start a SecMon project.
Bro/Zeek, Suricata, Netflow, etc. would be somewhere between 2 and 4 if available. ..
e.g. Antivirus logs can often be collected from a single console, while NSM requires high speed network Taps on mirroring ports in central locations (💵). If you have the budget and time, NSM is worth the effort.
1. Antivirus logs often contain indicators for threat groups‘ activity that aren’t noticed b/c no one pays attention to events with status „successfully removed“.
(see my cheat sheet as guide to improve visibility)
2. All main Windows Eventlogs matter:
‚System‘ contains service installs,
‚Application‘ App Crashes & AV events,
‘Security’ logins, group mgmt & proc starts
Sysmon adds: Parent>Child rel, Hashes, Registry, Nwrk cons, WMI, NamedPipes, Image/Driver loads => a goldmine
With the right Windows audit policy and Sysmon config the log volume can be reduced to a reasonable size.
Firewall logs are much less useful than people believe. We split them into:
1. Out blocked <- most relevant
2. Out allowed
3. In allowed
4. In blocked <- least relevant
They contain C2 IPs & help in reconstruction of an incident.
Volume is very high.
5. The volume of DNS logs is also pretty high. And in many orgs you have problems to get access to them. 🤷♂️
They contain C2 domain lookups, indicators for DNS tunnels, and can also be used to reconstruct events of an incident / malware outbreak.
Some of you recommended email logs.
I admit that I’ve never worked with them. Colleagues had, but only in DFIR. Maybe that is caused by the strict data protection & strong works councils here in Germany (Europe) that wouldn’t allow tapping into email logs for daily monitoring
I hope that these comments gave you more insight into the reasons for the order of my Top5.
Each one has been shortened and there are always other aspects to consider.
Please excuse the brevity, after all, this is Twitter 🐥