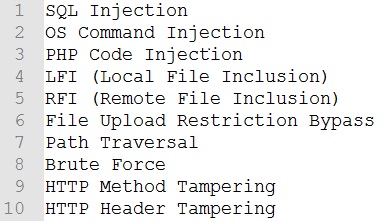
If you have solved enough machines of Vulnhub and HackTheBox, You don't have to worry about anything.
Just Go for It.
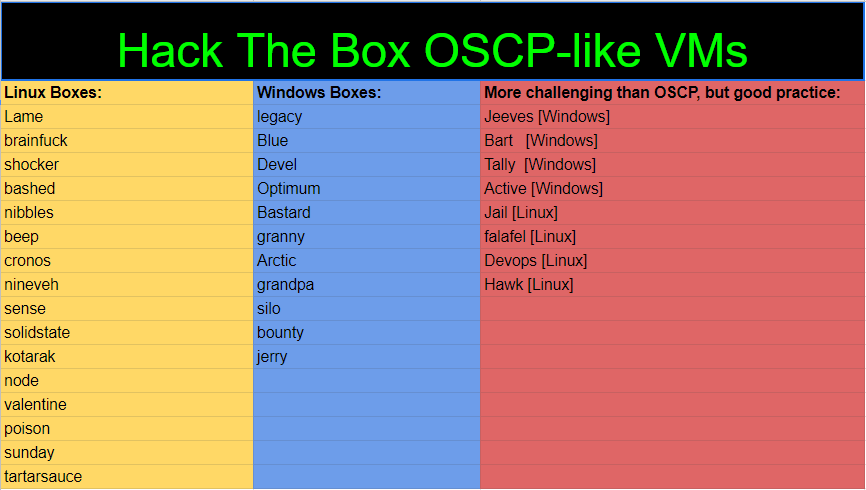
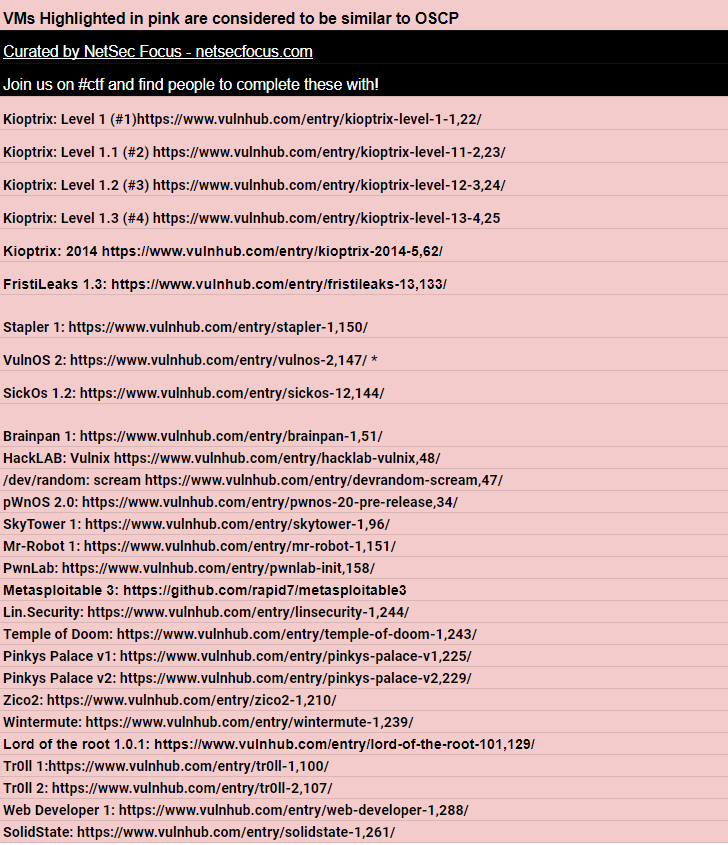
OSCP related Vulnhub and HackTheBox Machines share by @TJ_Null in his blog:
Book I preferred when I started solving machines and building pentest methodology:
"Penetration Testing: A Hands-On Introduction to Hacking by @georgiaweidman "
amazon.com/Penetration-Te…
Below are the top blogs I followed for Priv Esc during OSCP Journey :-
Linux/Windows Enumeration blog by @GuifreRuiz :
guif.re/linuxeop
guif.re/windowseop
Linux Privilege Escalation blog by @payatulabs :
payatu.com/guide-linux-pr…
Now come to Python for scripting/automation😍:
Videos: "Complete Python Bootcamp: Go from zero to hero in Python 3"
udemy.com/course/complet…
Book: "Think Python - How to Think Like a Computer Scientist"
greenteapress.com/wp/think-pytho…
Pivoting/Port Tunneling
"PWK Notes: Tunneling and Pivoting" by @0xdf_
0xdf.gitlab.io/2019/01/28/pwk…
"Explore Hidden Networks With Double Pivoting" by @m3karadag
pentest.blog/explore-hidden…
And the last but not least, To whom most of people feared, but trust me its so much easy. Its like @offsectraining is giving you 25 points free😉 - Win32 BUFFER OVERFLOW😐 :-
I have followed Chapter No. 16 & 17 of "Penetration Testing - A hands-on introduction to Hacking" to better understand Buffer Overflow concepts.
But in above book of @georgiaweidman , Finding Bad Characters is not covered,
Now you can go through her blog for "Finding Bad Characters with Immunity Debugger and Mona.py"
bulbsecurity.com/finding-bad-ch…
Although I have also written blog on Win32 Buffer Overflow i.e "10 Easy Steps to Exploit Basic Stack-Based Buffer Overflow"
medium.com/@loopspell/10-…
Daily read at least 2-3 vulnerable machines walkthrough.
You can go through blog of @0xdf_ :
0xdf.gitlab.io
And for video, i would suggest Youtube channel of @ippsec :
youtube.com/channel/UCa6eh…
Tips
1) Its an Always easy, if you solved enough machines of Lab then focus on what you already know. Don't make things over-complicated.
2) Try to solve Lab machines more than one way.
3) Use mona.py for Finding Bad Characters, it will save lot of time.
4) Start enumeration with top 5 services first.
5) Read and watch OSCP Course Material carefully.
6) Take break every 2 hour during exam and drink lots of water (I got sick during exam😬)
7) Enumerate well if stuck, start again from basics.
And below is the blog that I have followed to set every day target during Lab time:
arvandy.com/category/oscp/
That All from my side.
Reply to this thread if you want to add something.
If you face any problem relates to Resources😉 then DM me.