
Take a look at how #China #Russia #Iran and #DomesticExtremist conduct influence operations – #disinformation and #misinformation campaigns – to disrupt and influence US #Midterms2022 elections. Read the full report here: bit.ly/3ew3zhN 

The #Russophobia theme emerged on a #RussiaTimes interview with #DmitryBabich and in June 2022 with FSB-directed #Southfront. This appeal to ethnic Russians could drive tension between them and US govt, possibly motivating a hack-and-leak or hack-and-fake #OctoberSurprise. 2/7 

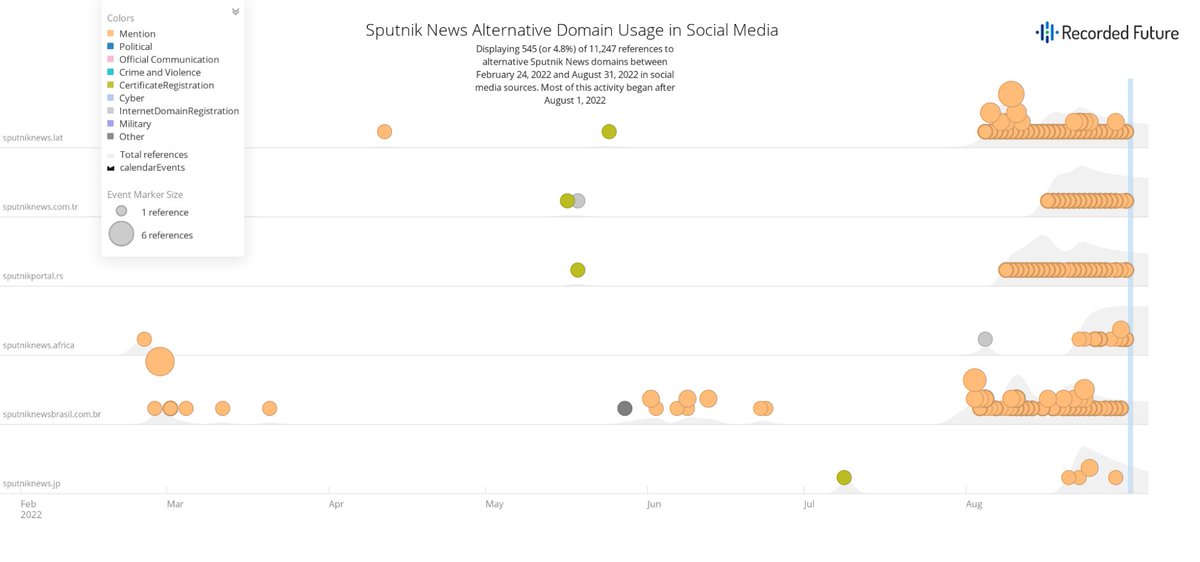
Russian state-controlled media are diversifying existing infrastructure through registration of alternative website domains – website “mirrors” – and are increasingly using country code Top Level Domains within existing infrastructure. Chart shows mirror mentions for #Sputnik 3/7 
A recent #China sponsored political influence campaign criticized both #GOP and #Democrat while promoting extreme views on both sides. For example, the Pacific Dialogue account on #Douyin hosts 600+ #propaganda videos featuring Westerners criticizing the US. 4/7 

Throughout 2022, #RecordedFuture has observed low level chatter from Chinese overt influence accounts mentioning US Congress members, such as Andre Carson for his criticism of #CCP policies and Tammy Duckworth for her official visit to #Taiwan. 5/7 

When US House Speaker Nancy Pelosi took an official delegation to Taiwan in early August 2022, China’s overt influence accounts spiked in mentions of “Nancy Pelosi” with increased criticism and threats: “unncessary” “provocative” “wreckless” 6/7 

Malign foreign influence operations on US domestic affairs are not a new phenomenon and they do not start/stop with an election cycle – rather they persist in hopes to influence US policy and undermine US global standing. 7/7 Read the full report: bit.ly/3ew3zhN 

• • •
Missing some Tweet in this thread? You can try to
force a refresh






