In these words, we can find: Chairman, Vice President, Deputy Director, Associate Professor, Deputy Heads, General, Private Message, shipping, Address, email, ...
pastebin.com/kfvJWKJB
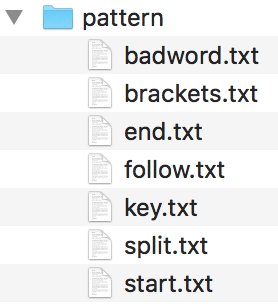
- badword.txt
- brackets.txt
- end.txt
- follow.txt
- key.txt
- start.txt
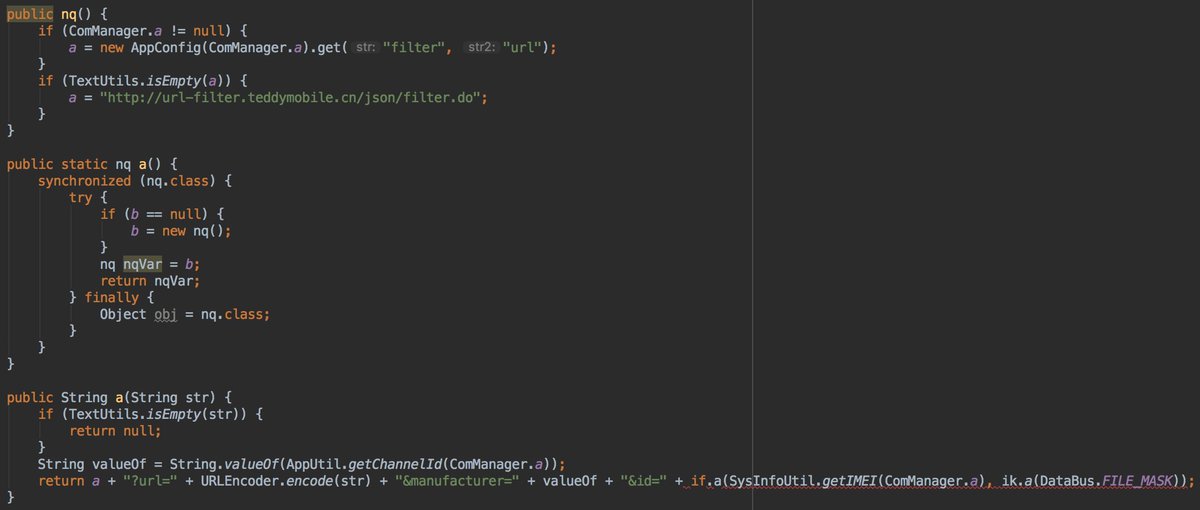
teddymobile.cn

The picture below can be translated like this:
- Total number of SMS 20M+
- SMS identification accuracy 100%
- Identification number recognition rate of 70%
- recognition accuracy of 95%

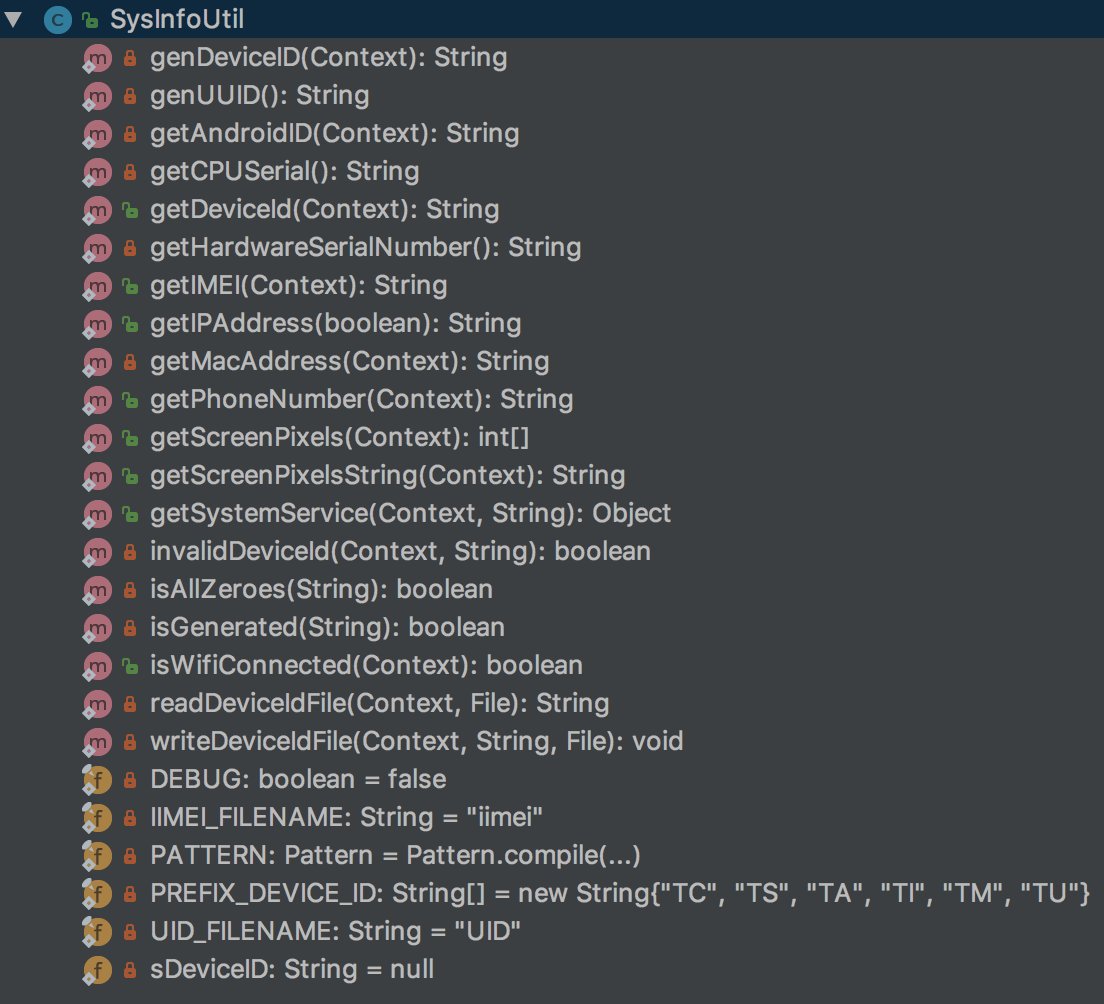
- getAndroidID
- getCPUSerial
- getDeviceId
- getHardwareSerialNumber
- getIMEI
- getIPAddress
- getMacAddress
- getPhoneNumbe
- getScreenPixels
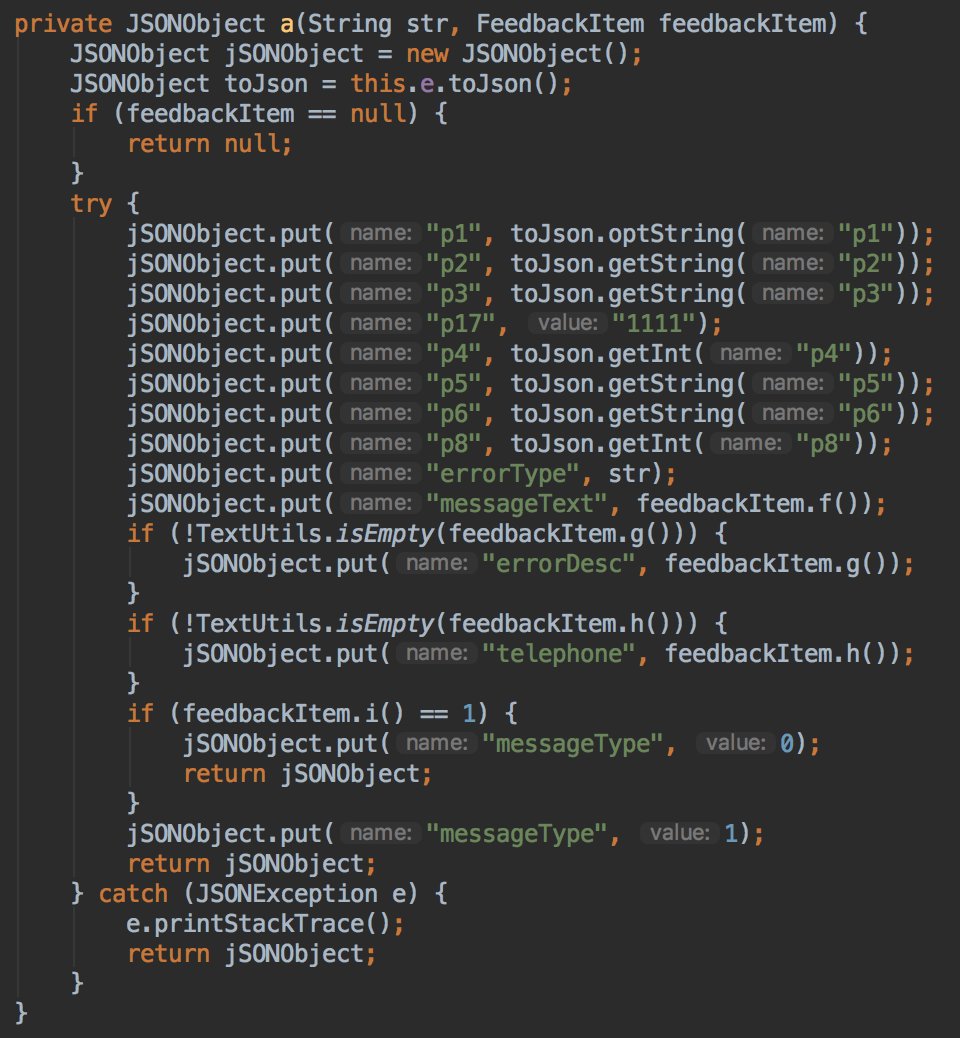
They also send JSON messages to their servers with a "telephone" and "messageText" fields...😡
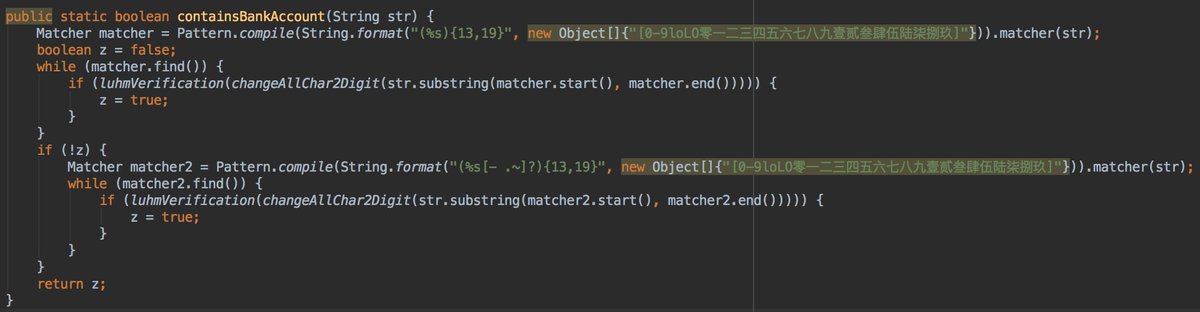
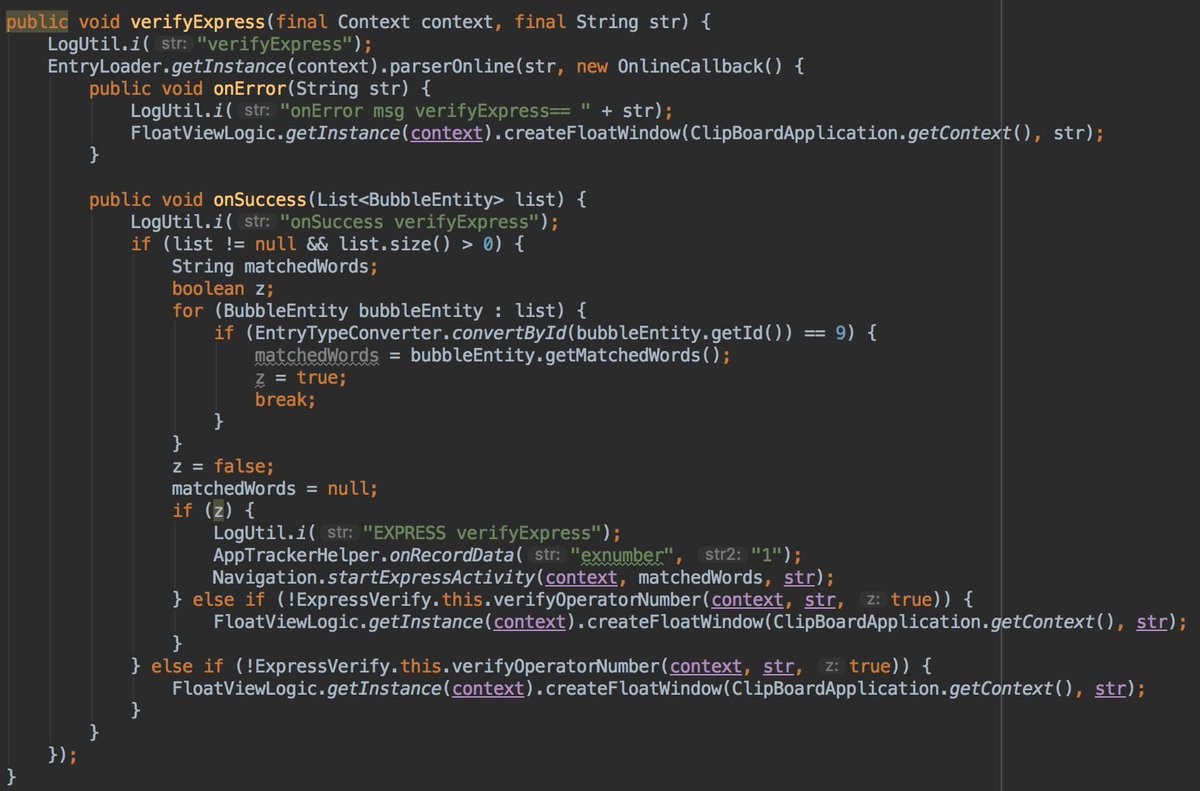
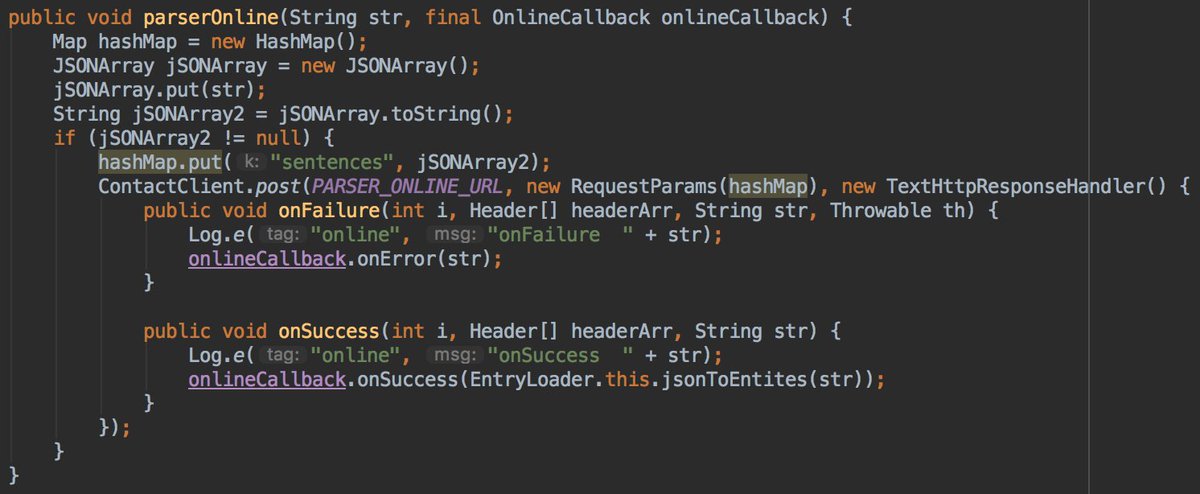
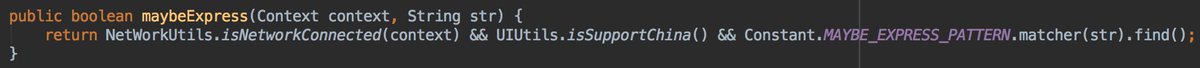
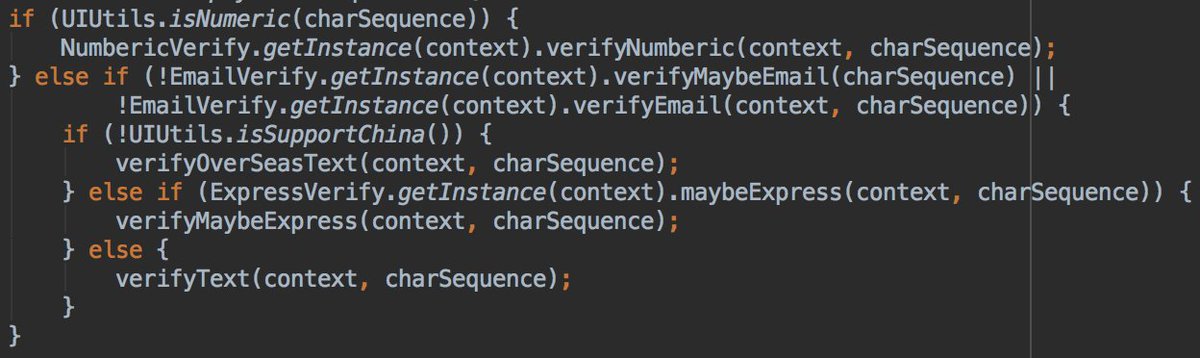
- clip data is not numeric
- not an email
- Chinese @OnePlus phone
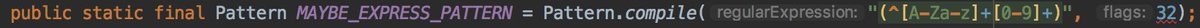
- clipboard data matched the express pattern.
It good to say that parserOnline method is used 3 times in the code, so this is only 1 of the 3 usecases