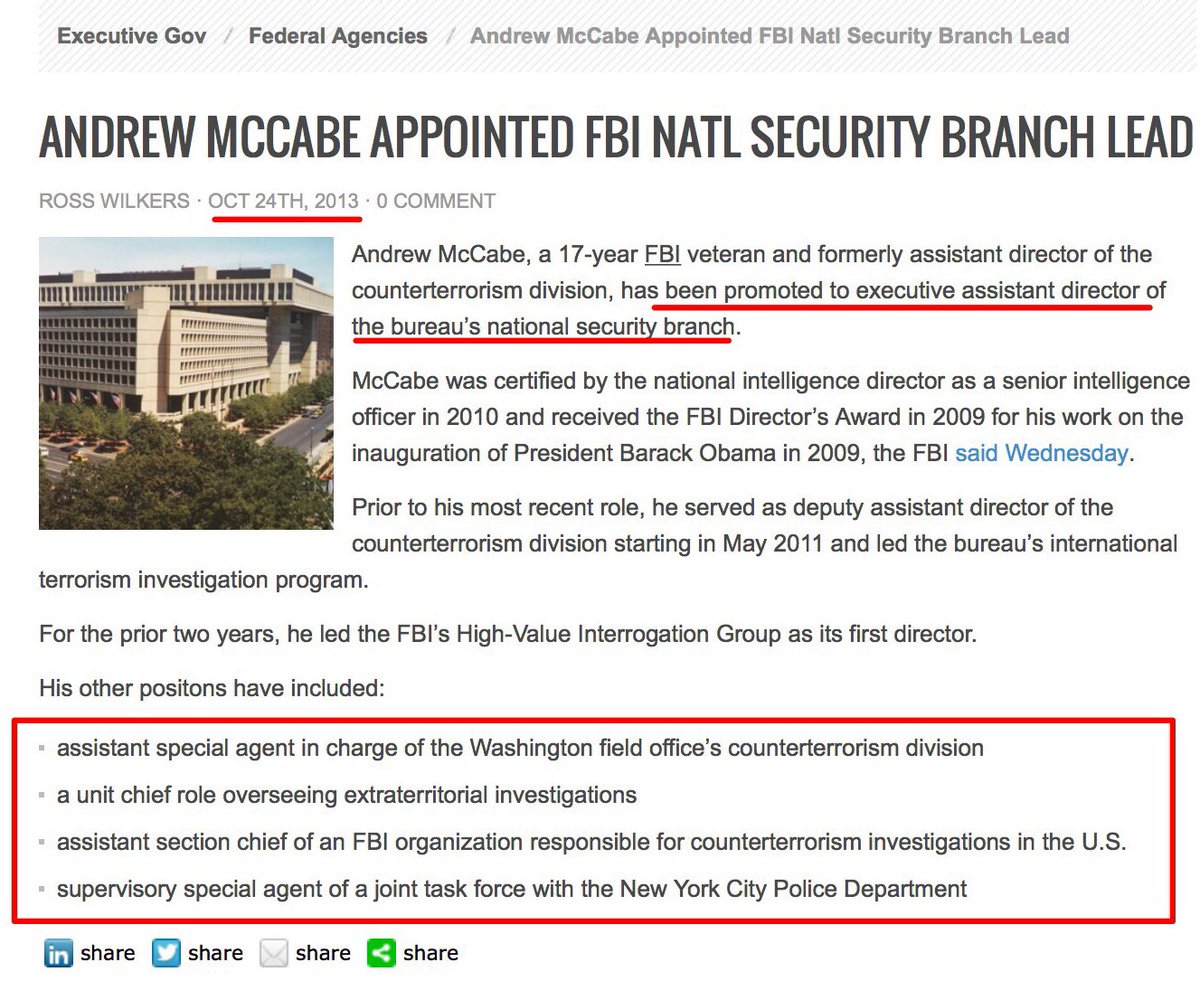
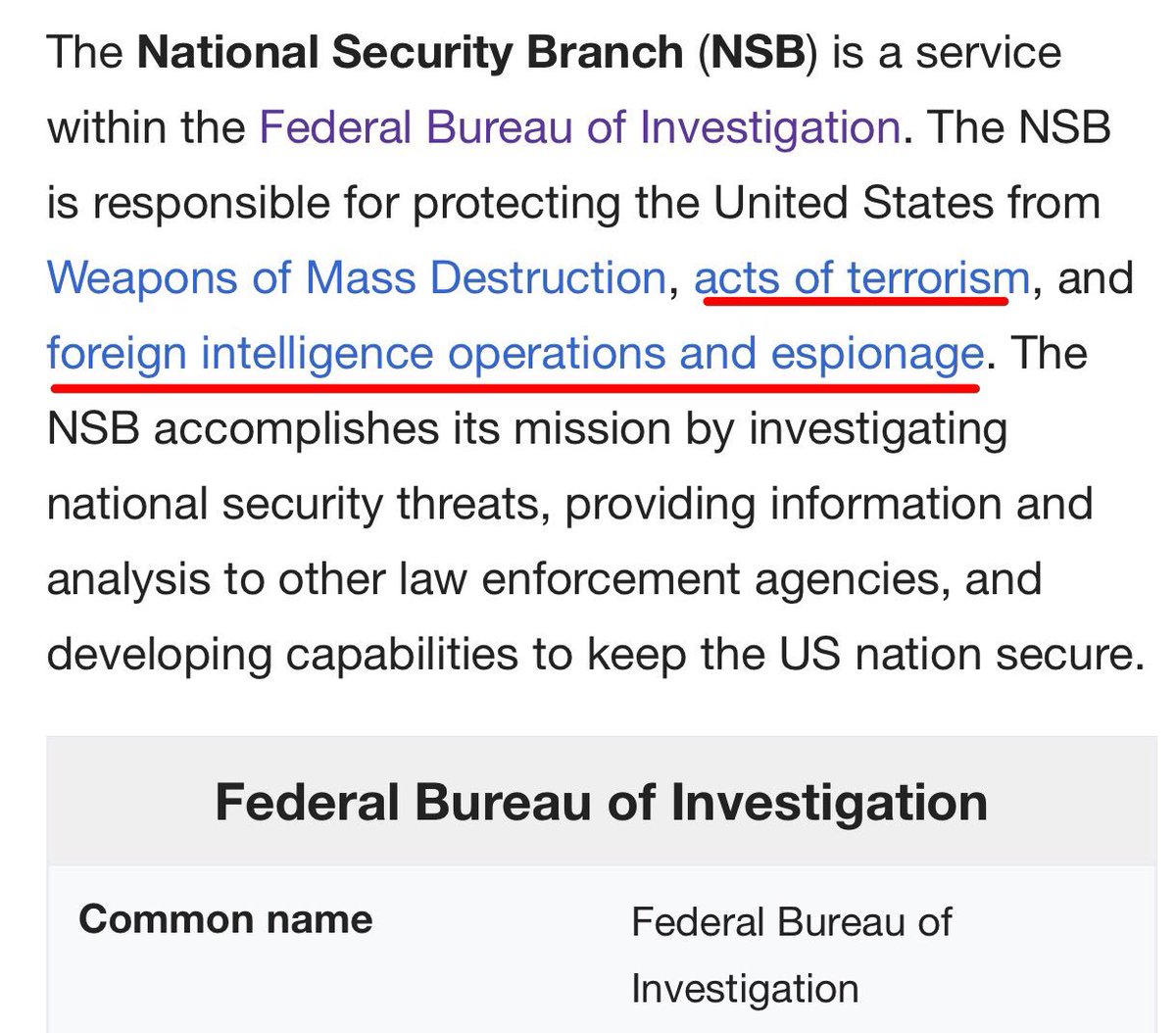
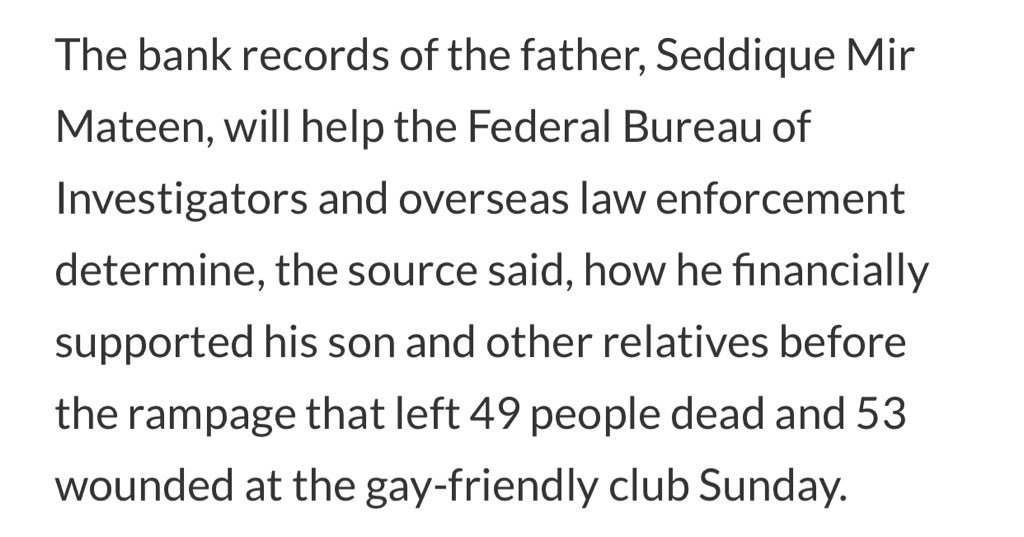
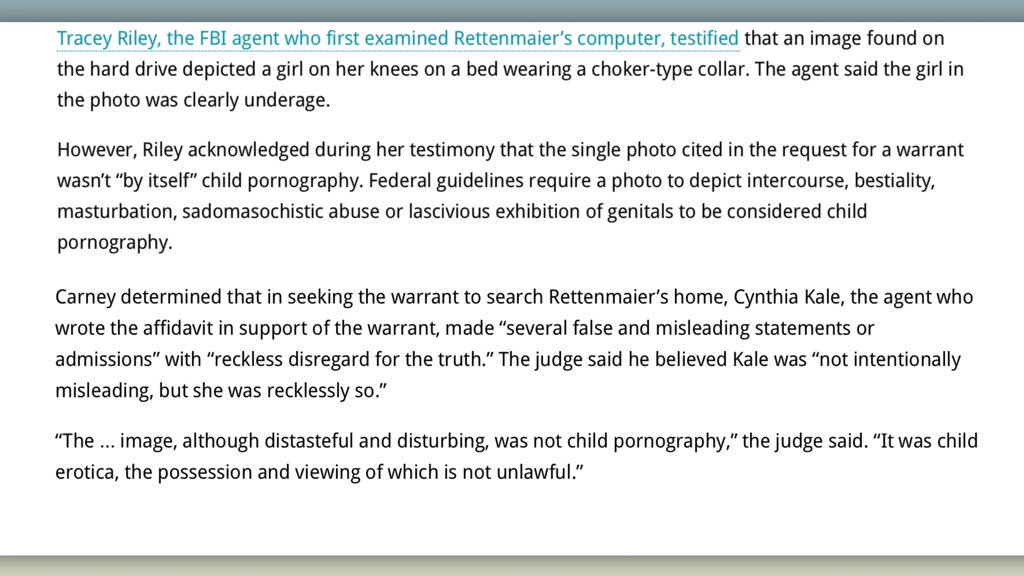
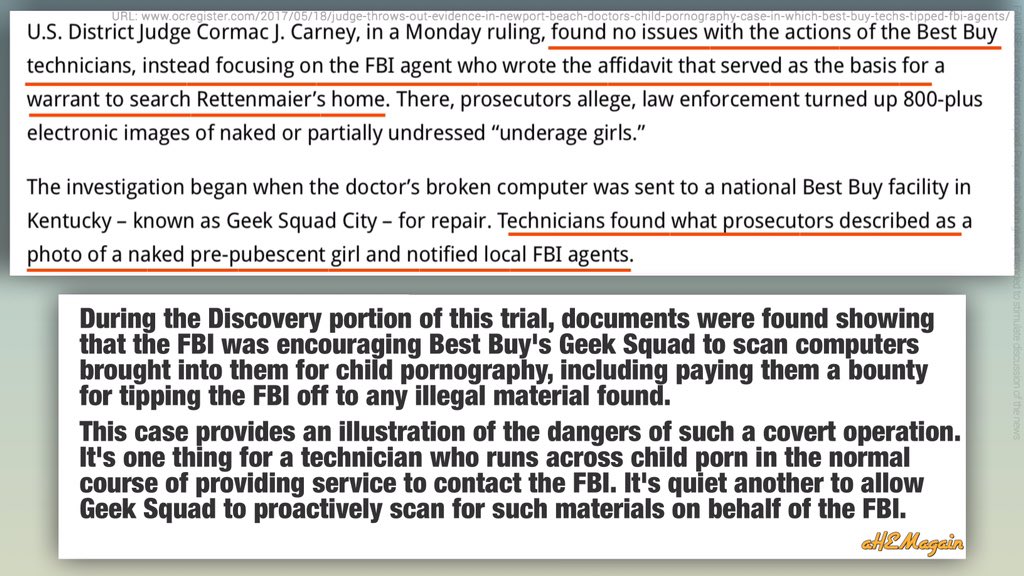
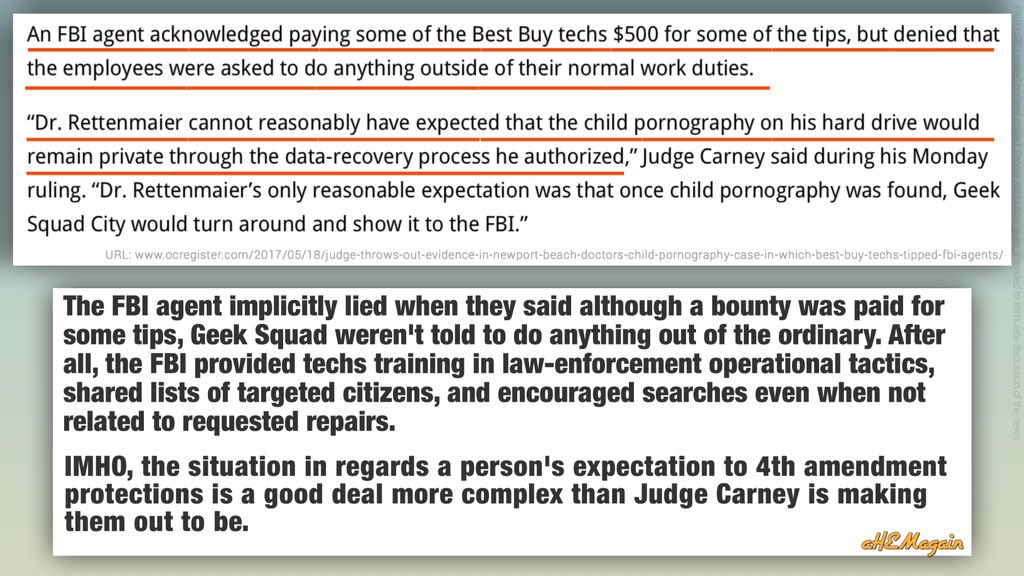
Allegedly the FBI had techniques that could have opened the San Bernardino iPhone, and withheld them — even while FBI leadership was testifying differently in front of Congress!?

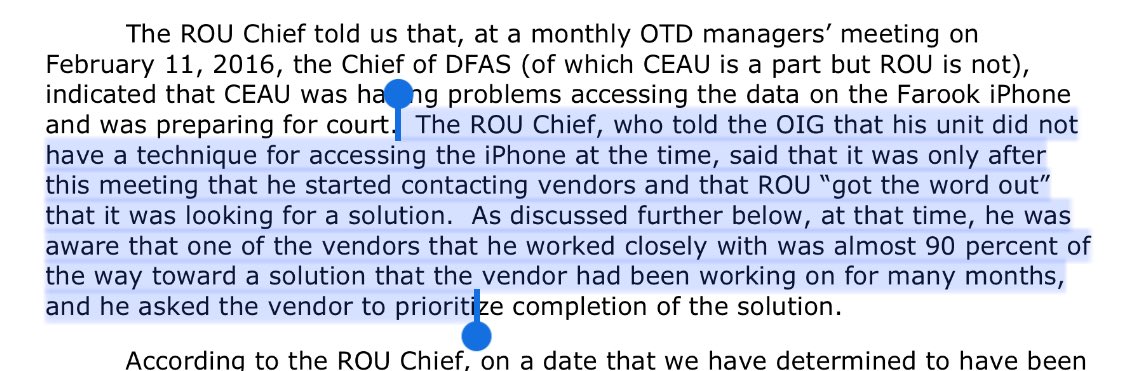
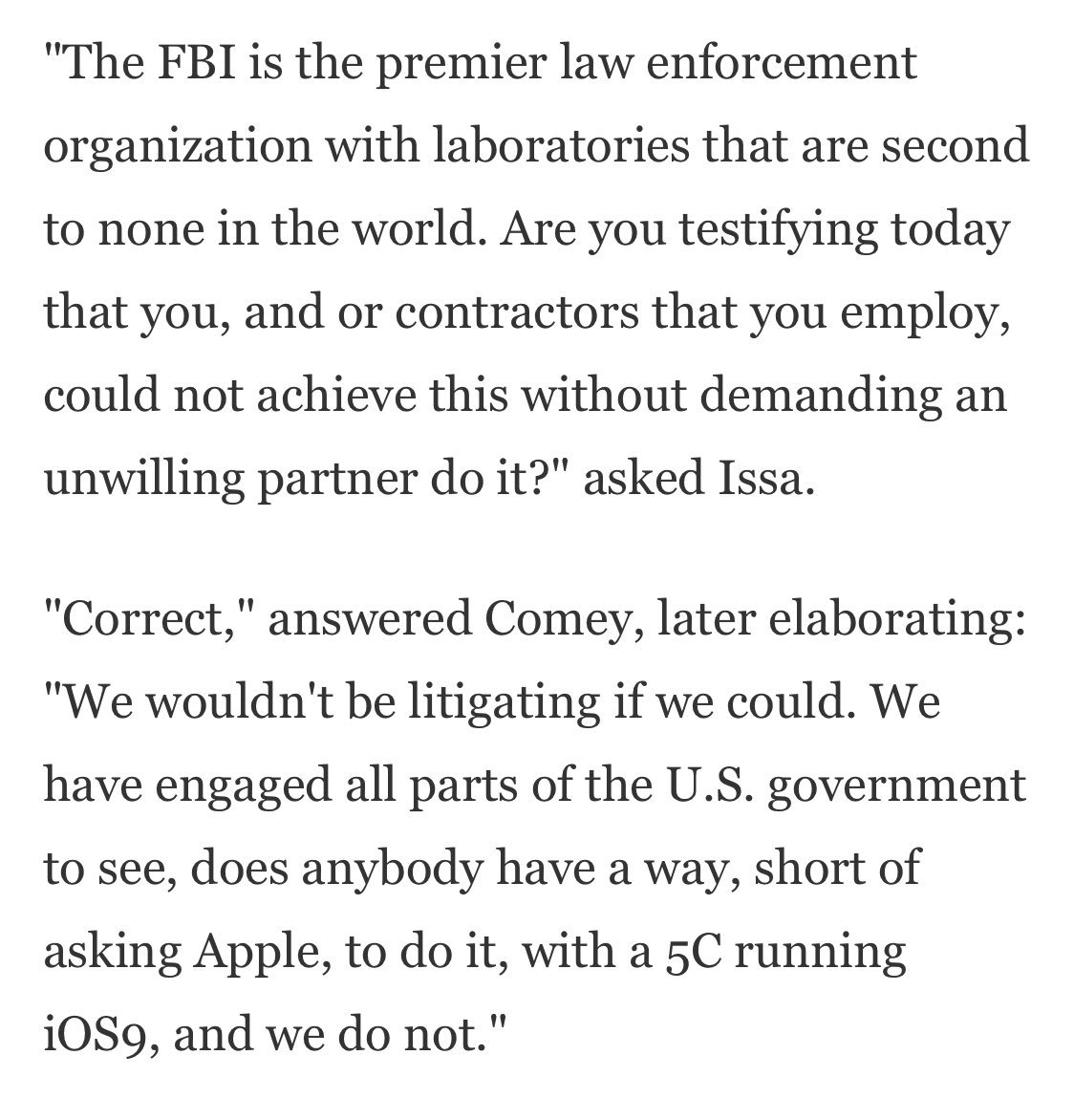
The solution was found March 16 and a working demo of the tech was given on March 20.

Hopefully they’ll keep this in mind next time. oig.justice.gov/reports/2018/o…
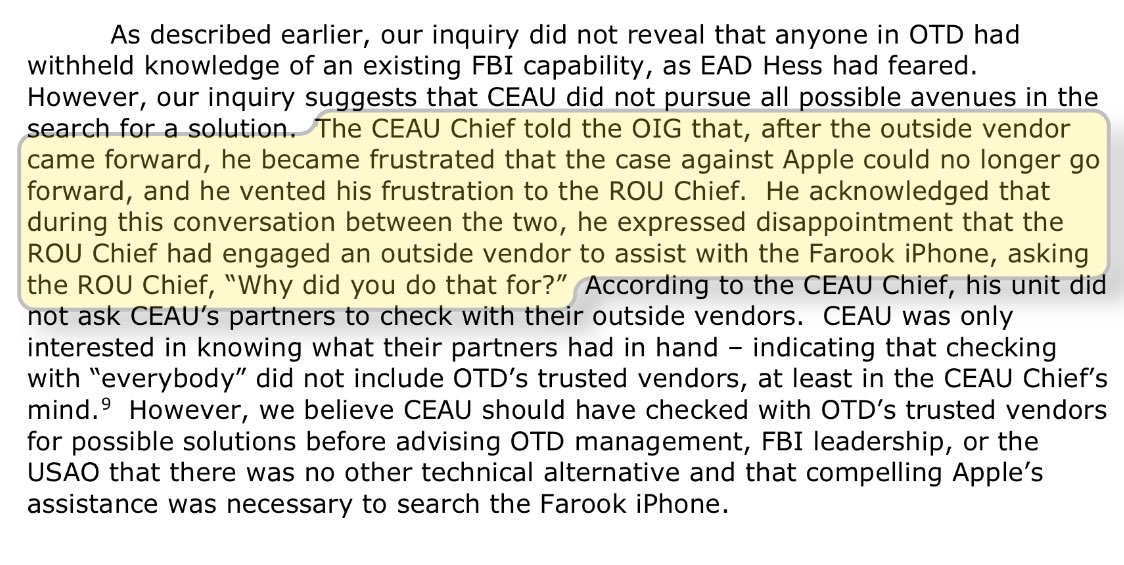
Also, mysterious outside vendors: let’s get a drink sometime. You’re buying, though.