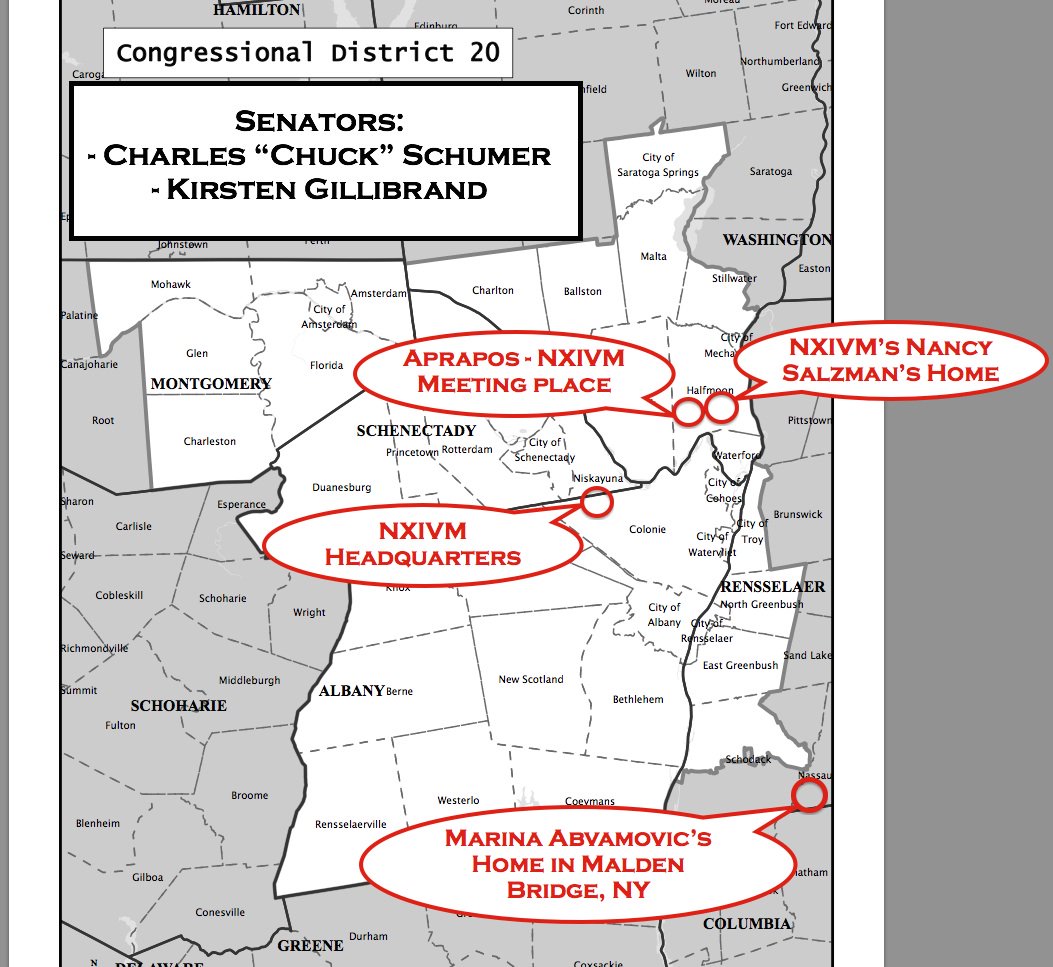
1/n
documentcloud.org/documents/4834…
Compared to the GRU indictment from a few weeks earlier, this one contains less details about the individuals and their organization. E.g. it is not really clear how many "co-conspirators" are covered and how close their cooperation is.
2/n
Mostly, the methods are comparable to what security companies do: malware similarities, identifying shared encryption keys and shared email accounts.
3/n
4/n
5/n
The main suspect supposedly worked for "Chosun Expo Joint Venture", which is called a front for the "Lab 110" of the North Korean government.
6/n
7/n
8/n
9/n
10/n