Short thread ahead.
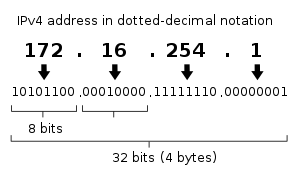
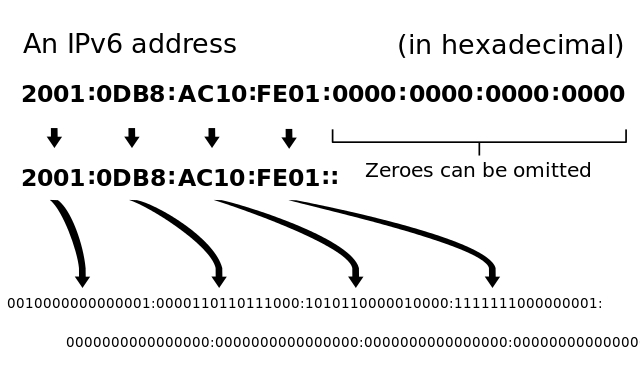
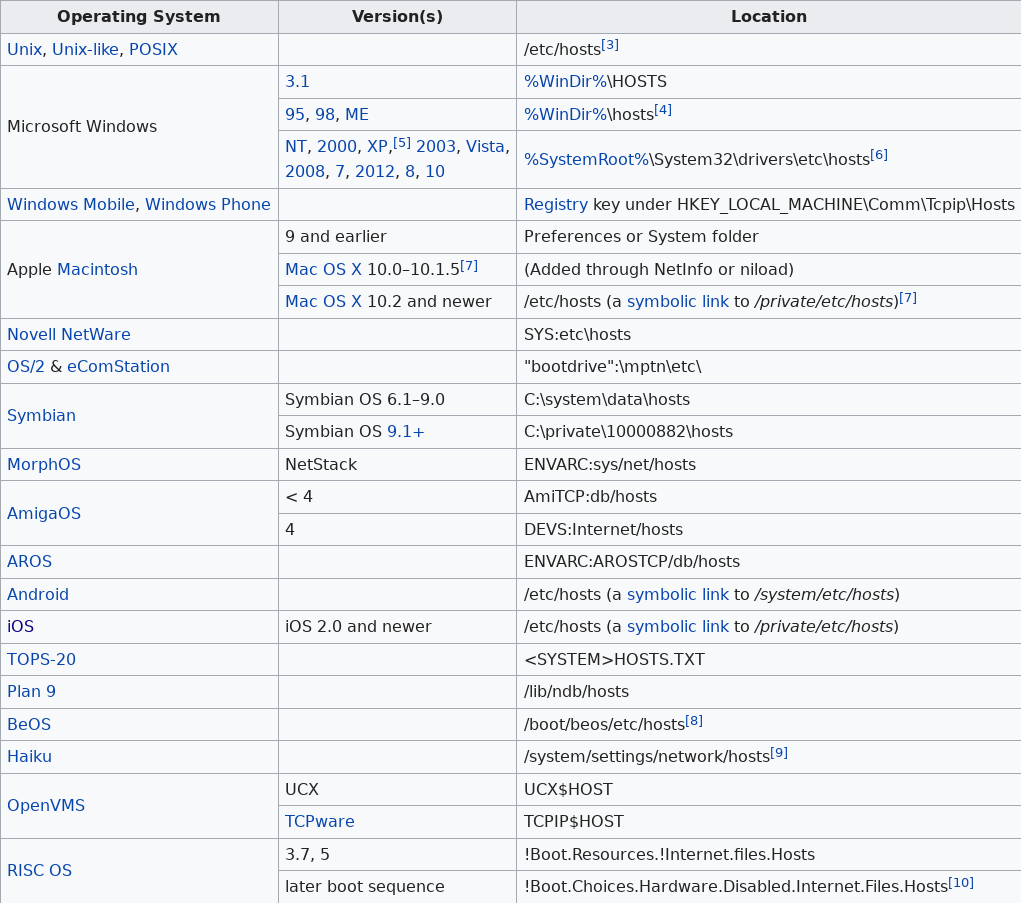
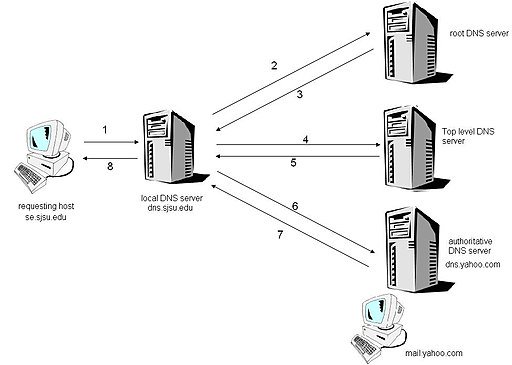
Because it is each application (not the operating system) who queries DNS.
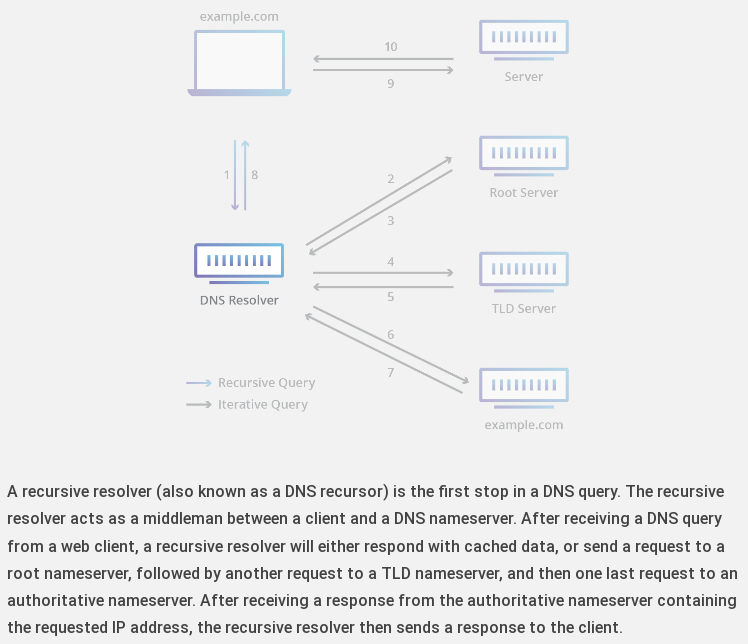
Stay with me in this, because it will be important later.
- dns.google/dns-query – RFC 8484 (GET and POST)
- dns.google/resolve? – JSON API (GET)
Details in developers.google.com/speed/public-d…
dns.google/resolve?name=w…
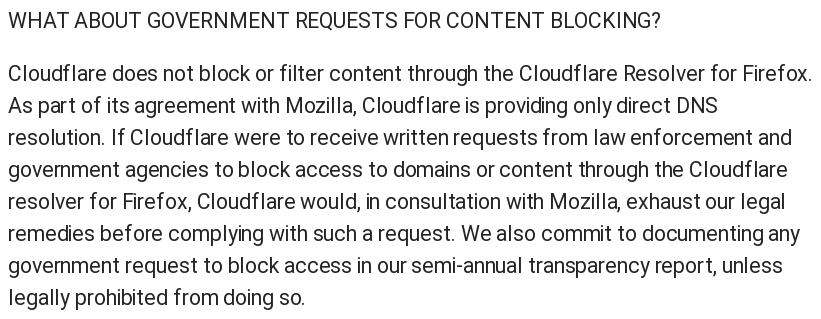

- to get DNS information about wikipedia.org: dnsquery.org/dnsquery/wikip…
- to get only the IP address: dnsquery.org/dnsquery/wikip…
Many other queries: dnsquery.org
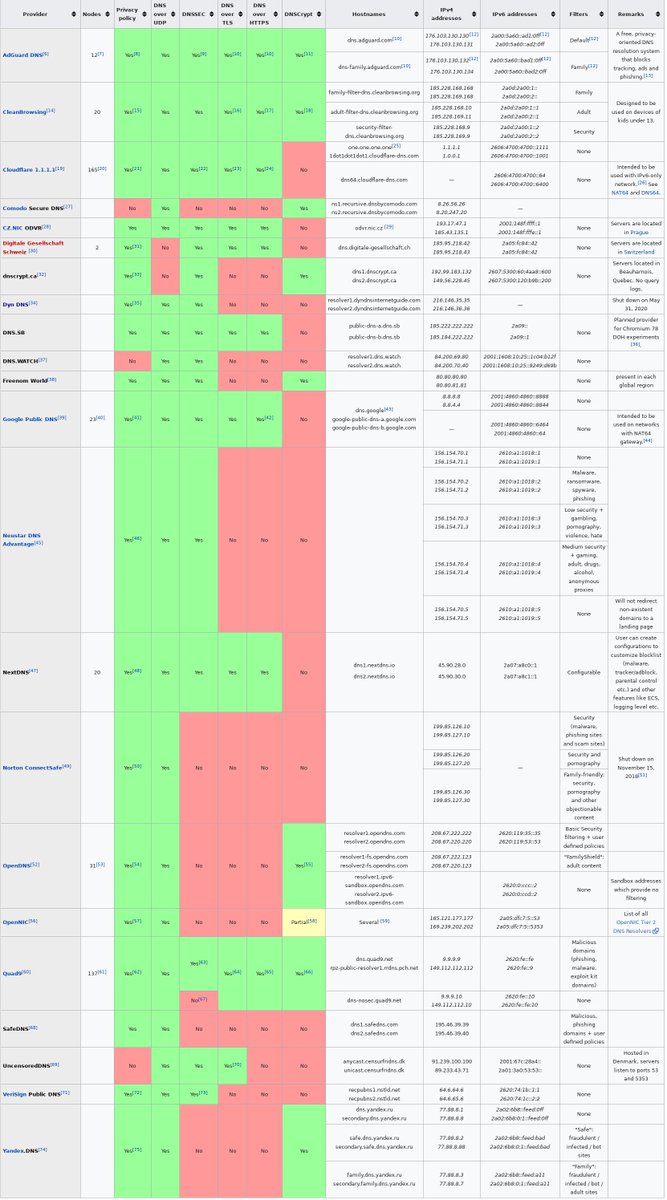
- securitytrails.com/blog/most-popu…
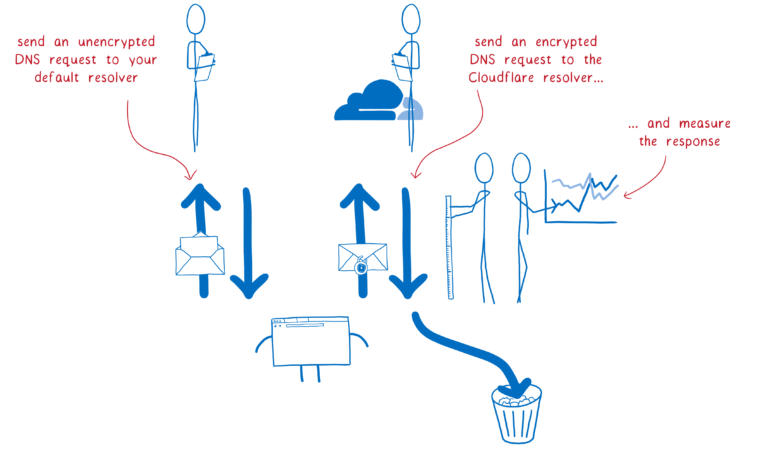
- cloudflare.com/learning/dns/d…
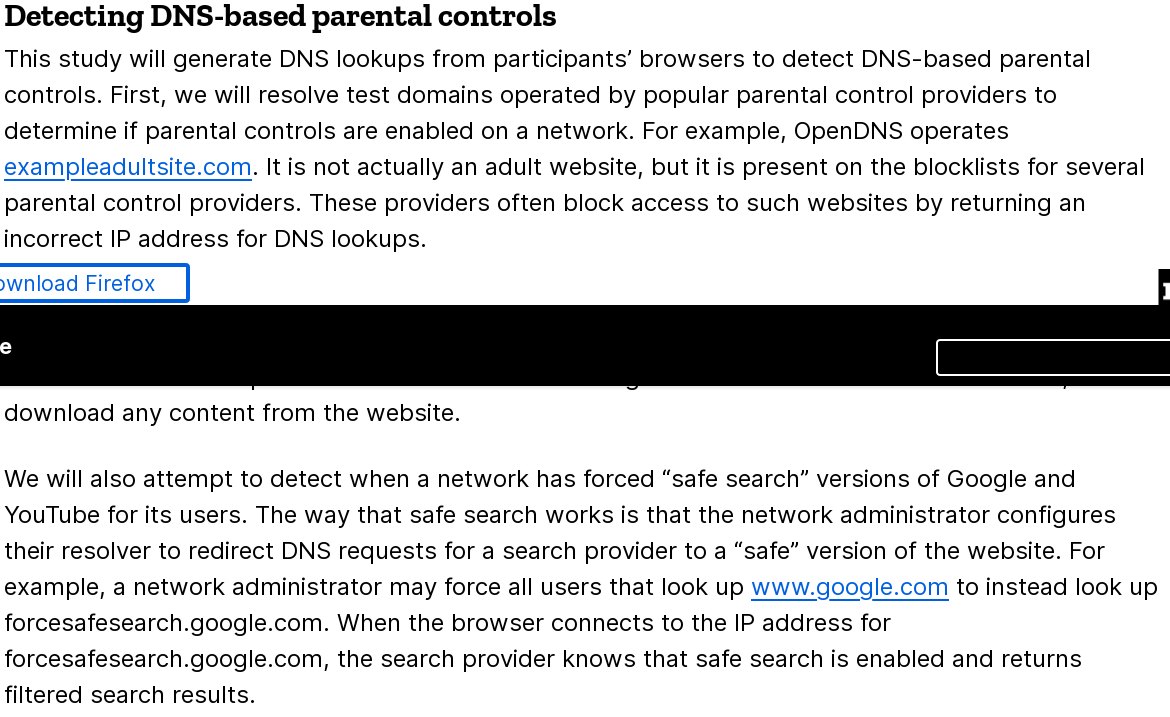
- krebsonsecurity.com/2019/02/a-deep…
- How to configure DoH in Firefox: support.mozilla.org/en-US/kb/firef…
- How to enable DoH in Chrome: zdnet.com/article/how-to…
- Check if your browser is using Cloudfare's DoH: https://1.1.1.1/help









