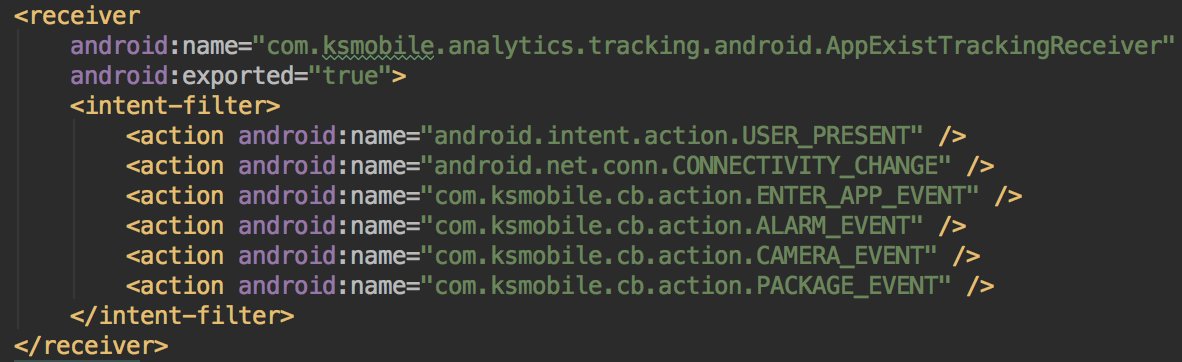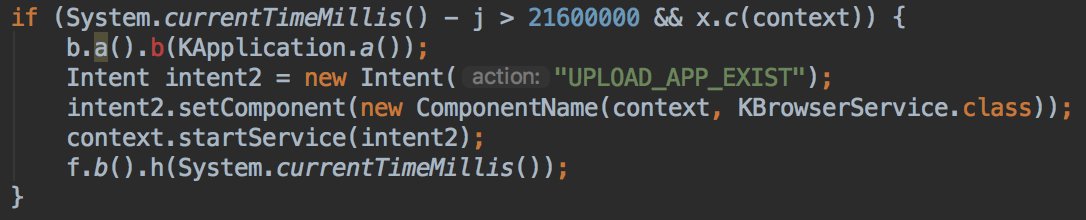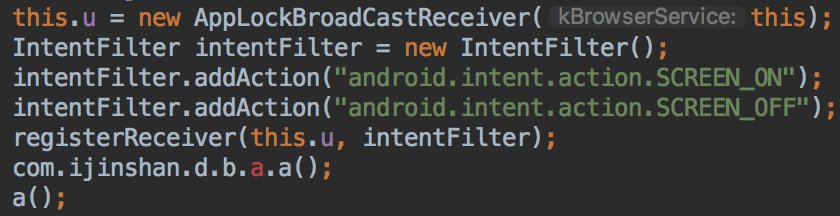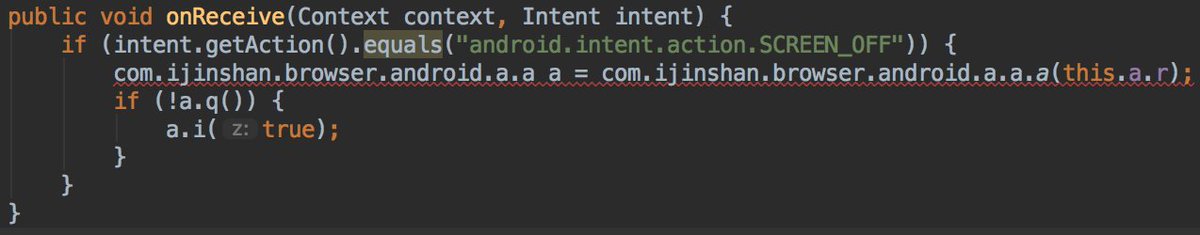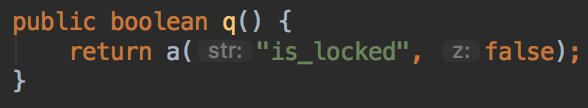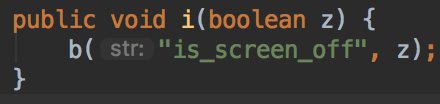

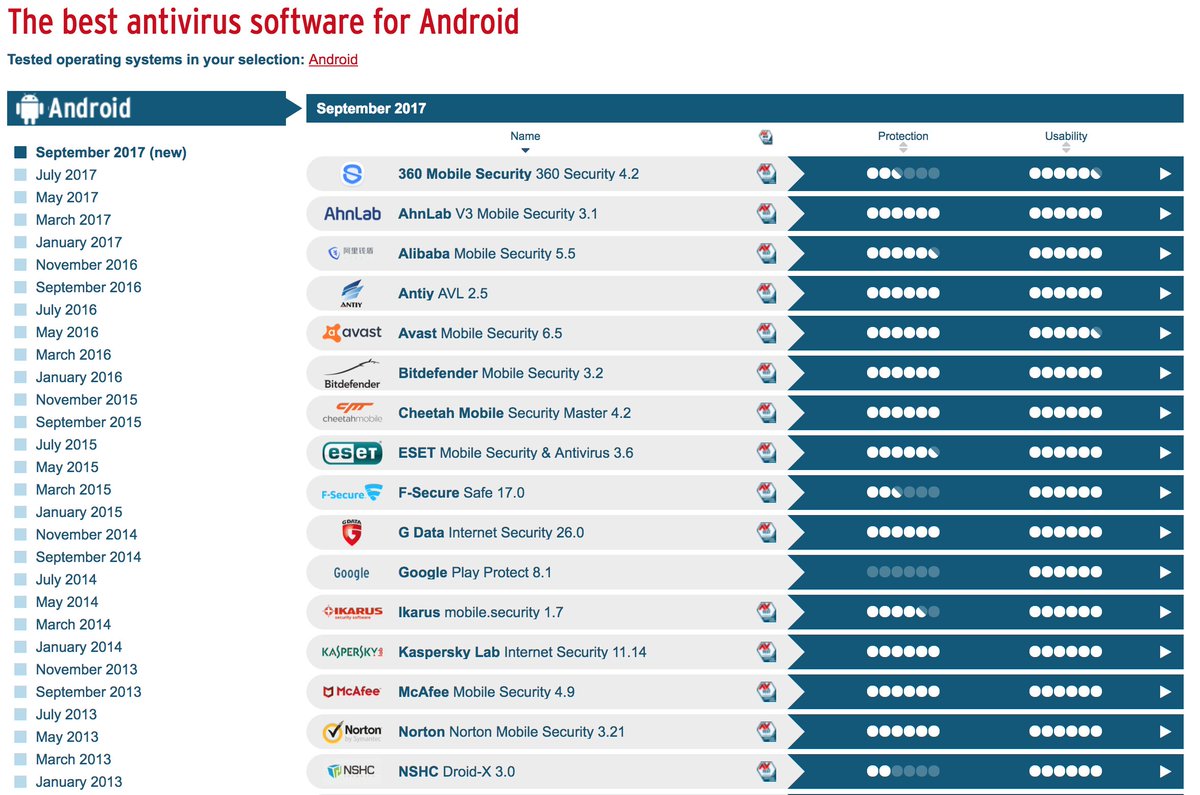
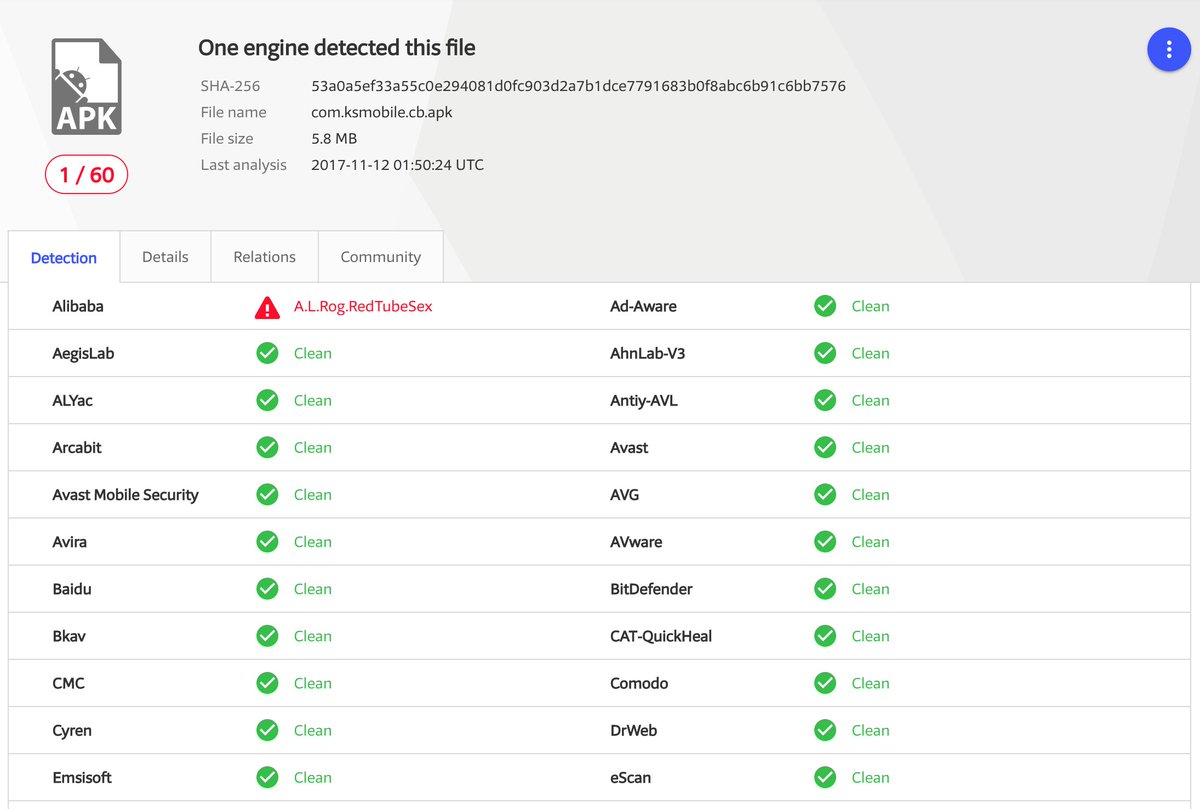

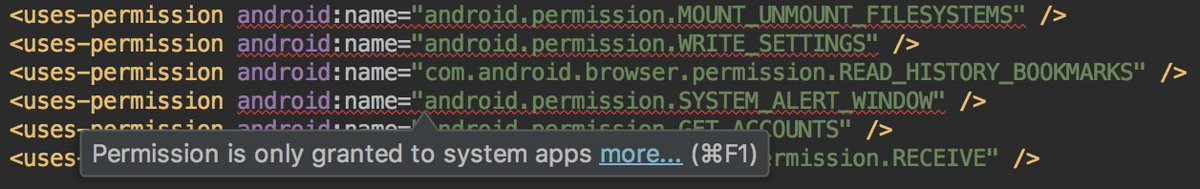
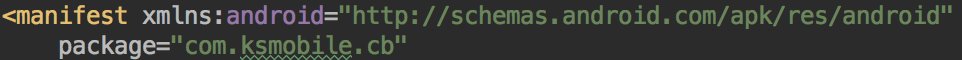

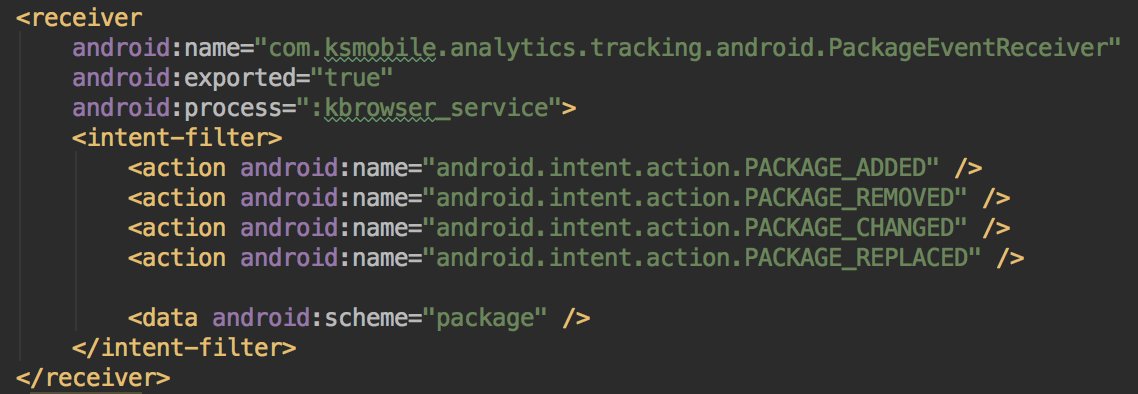
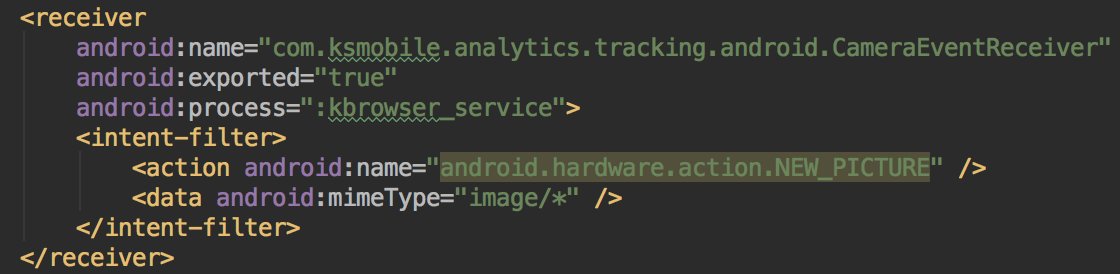
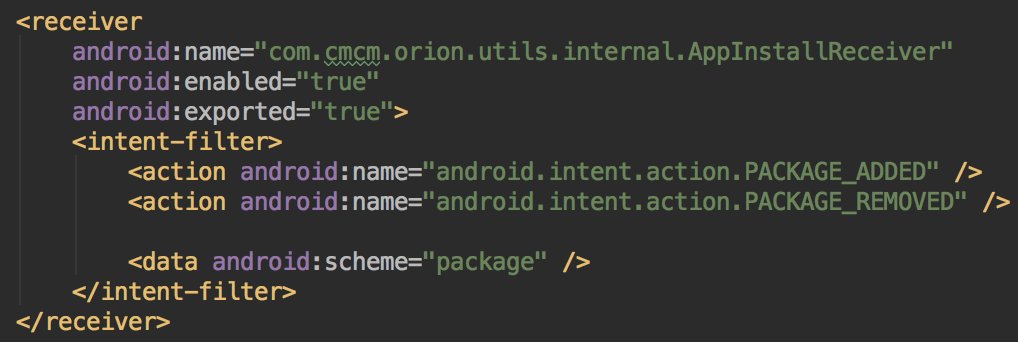
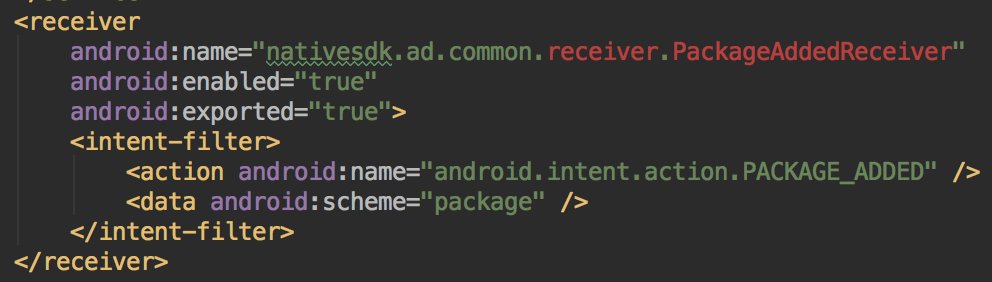
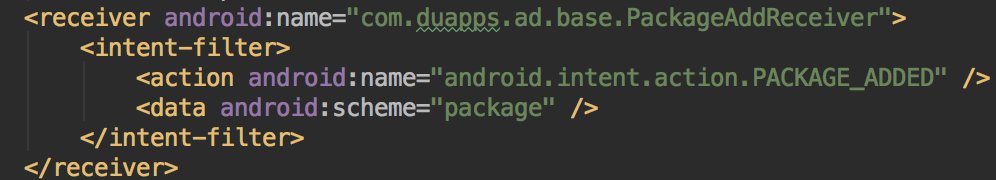
* They lie in the description
* VT detected it as a Rog.RedtubeSex
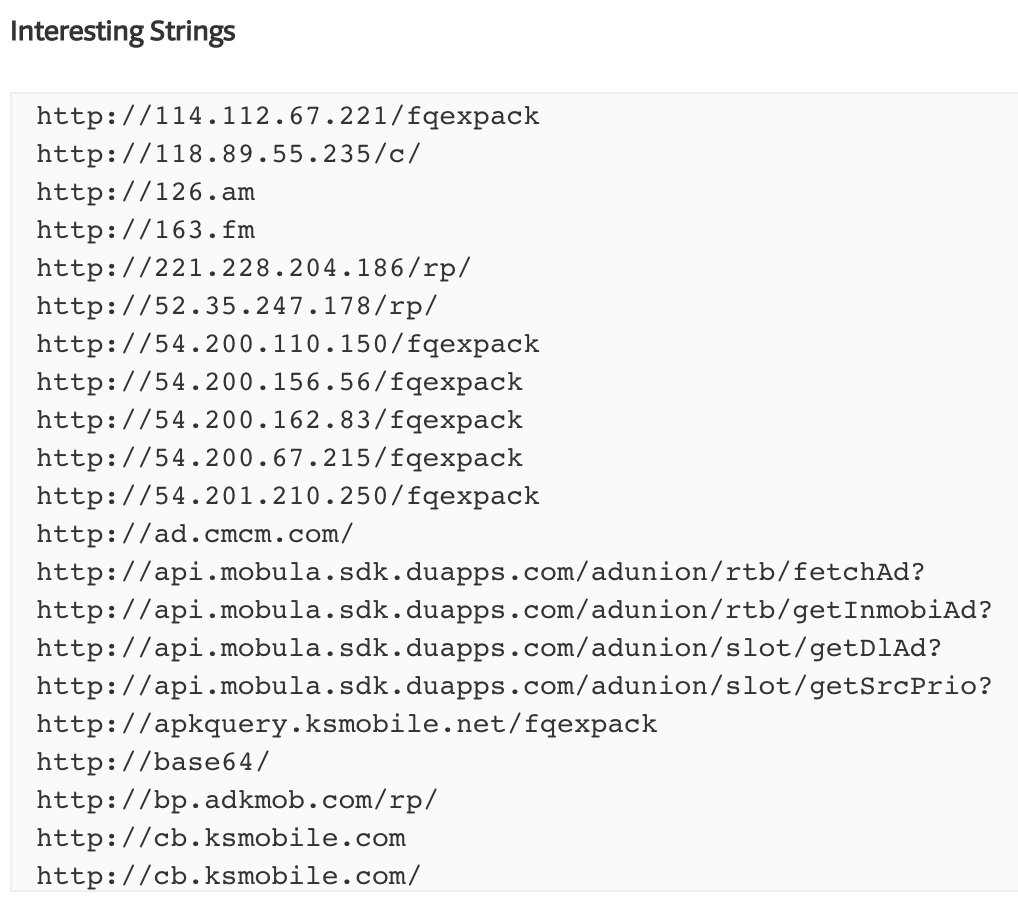
* This Adblock browser load their own ad
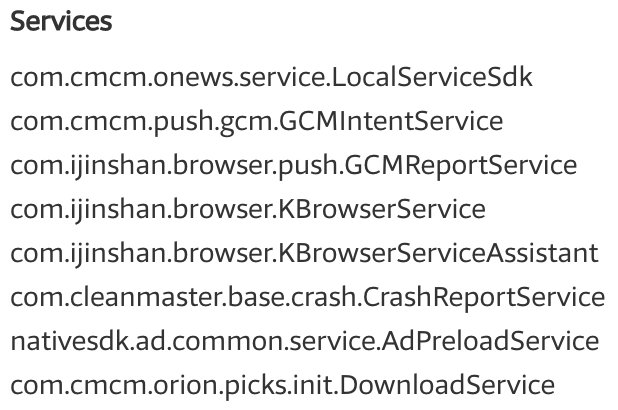
* They used multiple SDKs
* They listen to the apps movement (install,...)
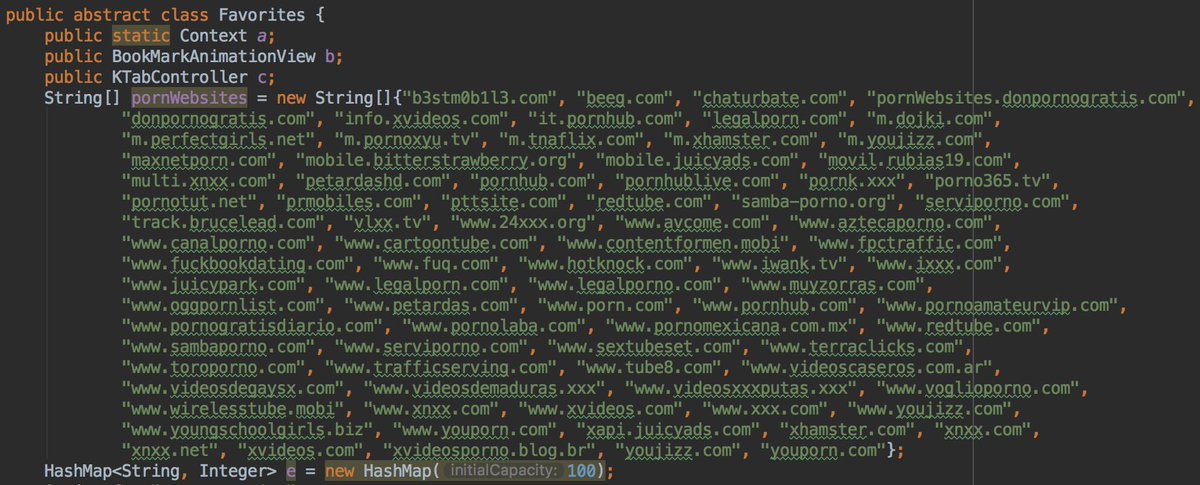
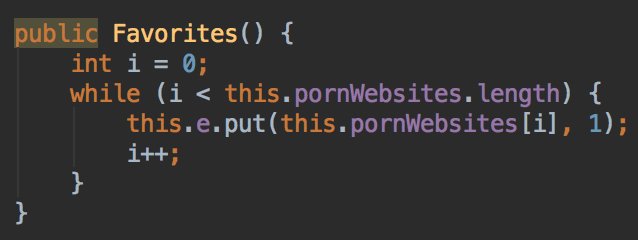
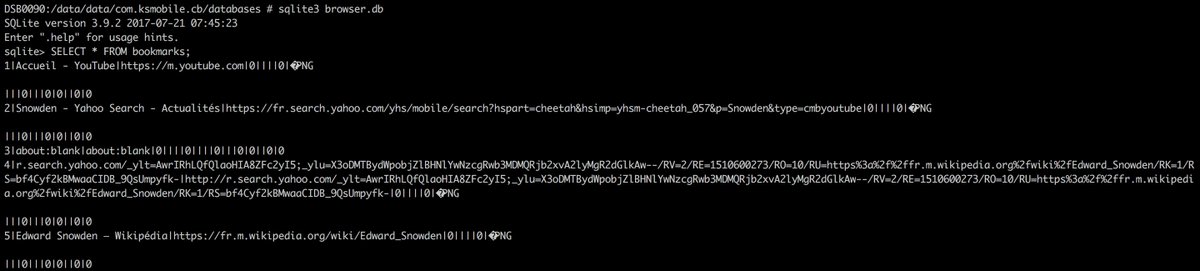
On the onReceive method it will start the KBrowserService if the device is connected to the network and the last upload is older than 6 hours