In this thread we will find ways to hunt and attribute phishing admin panels.
This is a continuation from my #phishing hunting thread released earlier this year. ()
Please retweet to knowledge share among others.

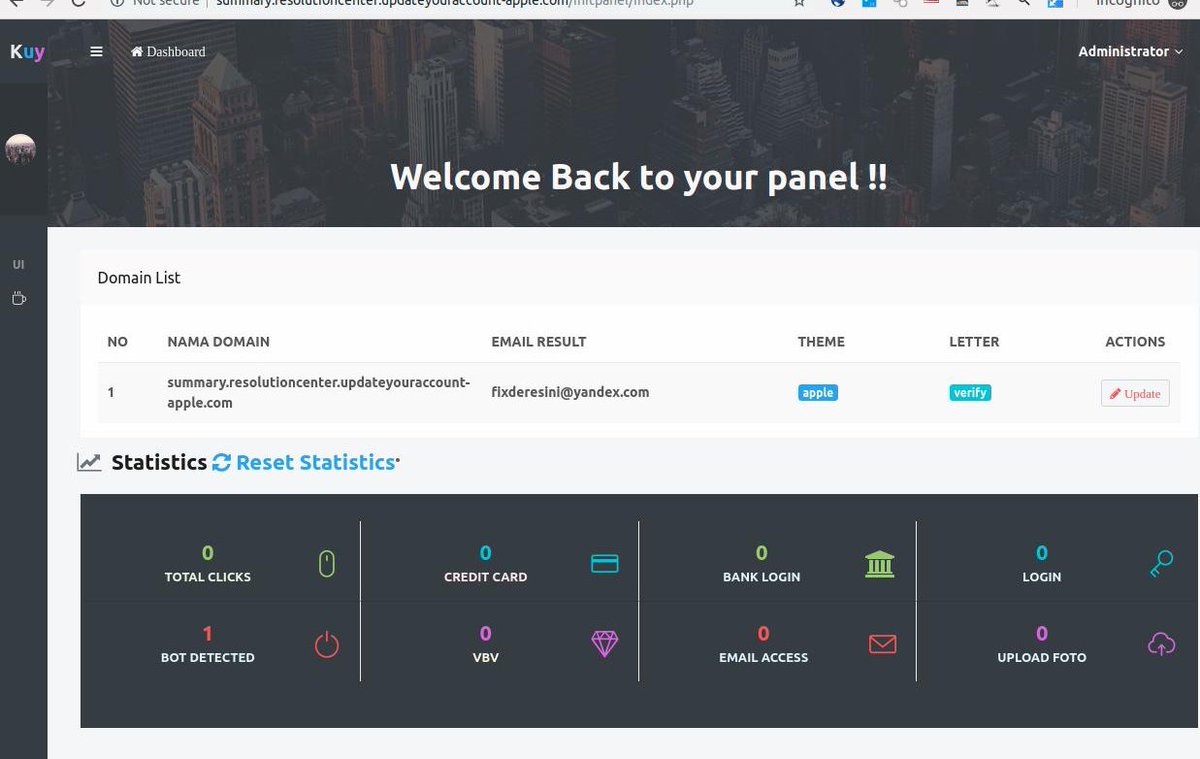
To check if a site is uses 16Shop navigate to "/admin" or "/server.ini"
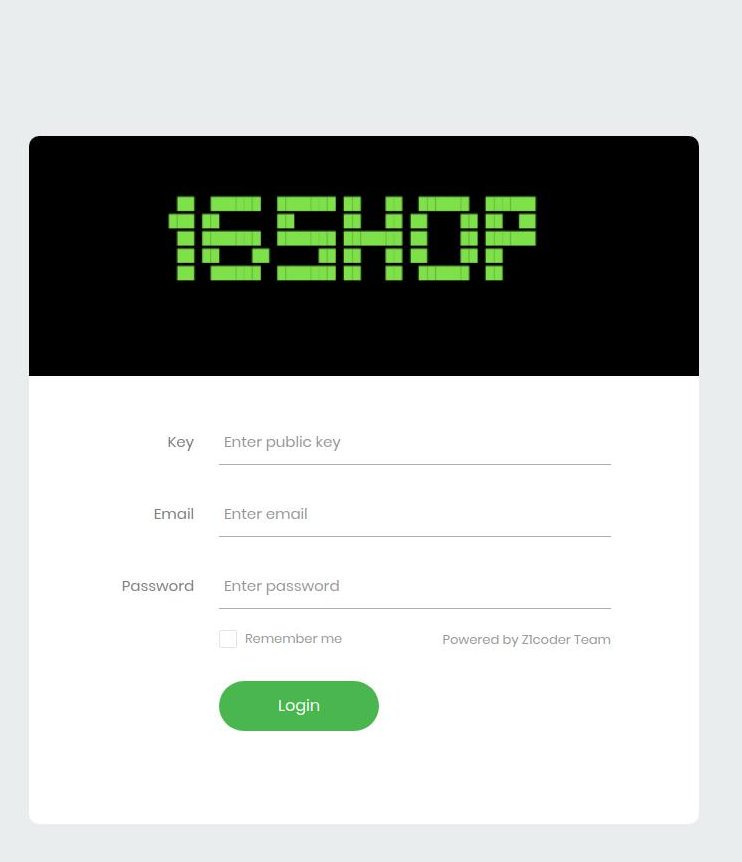
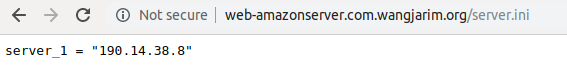
I have a thread on AppleKit here ::

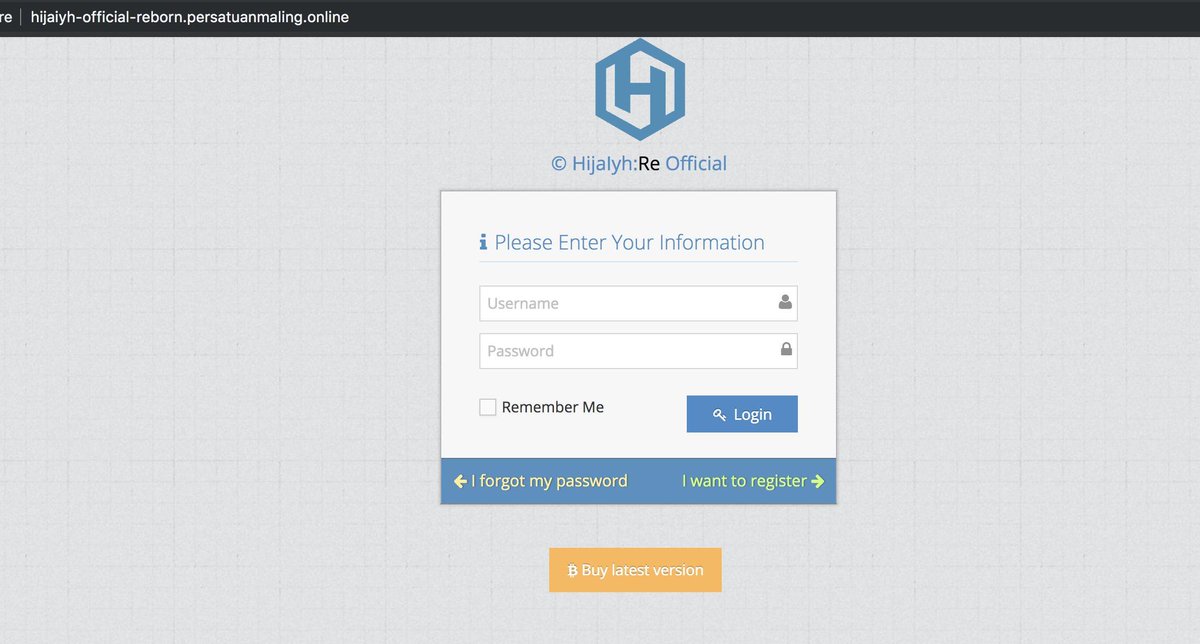
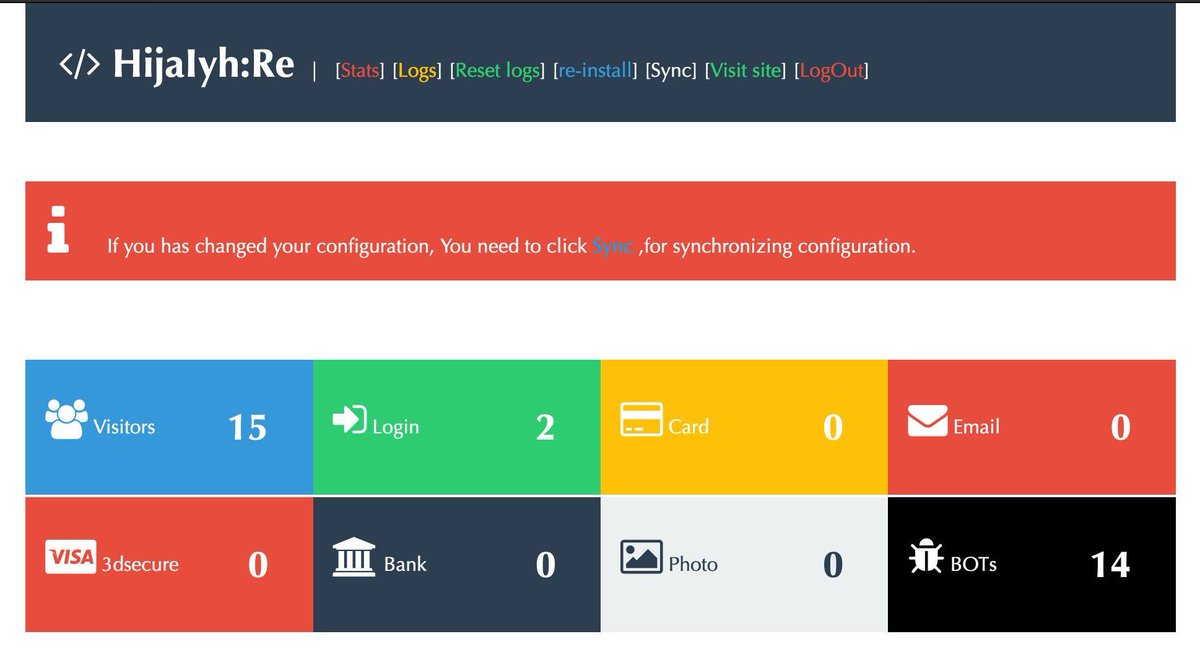
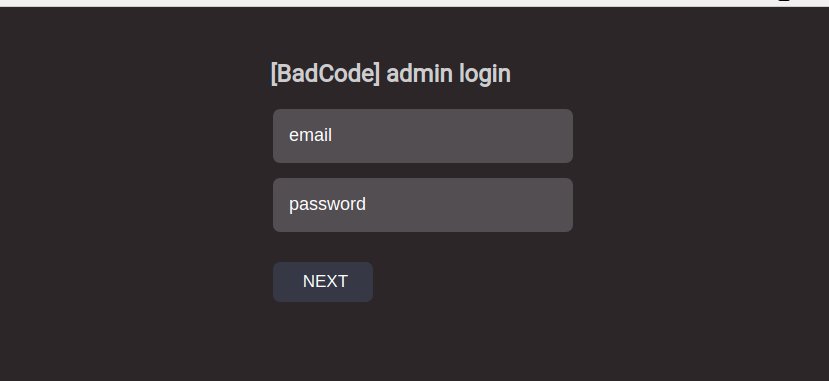
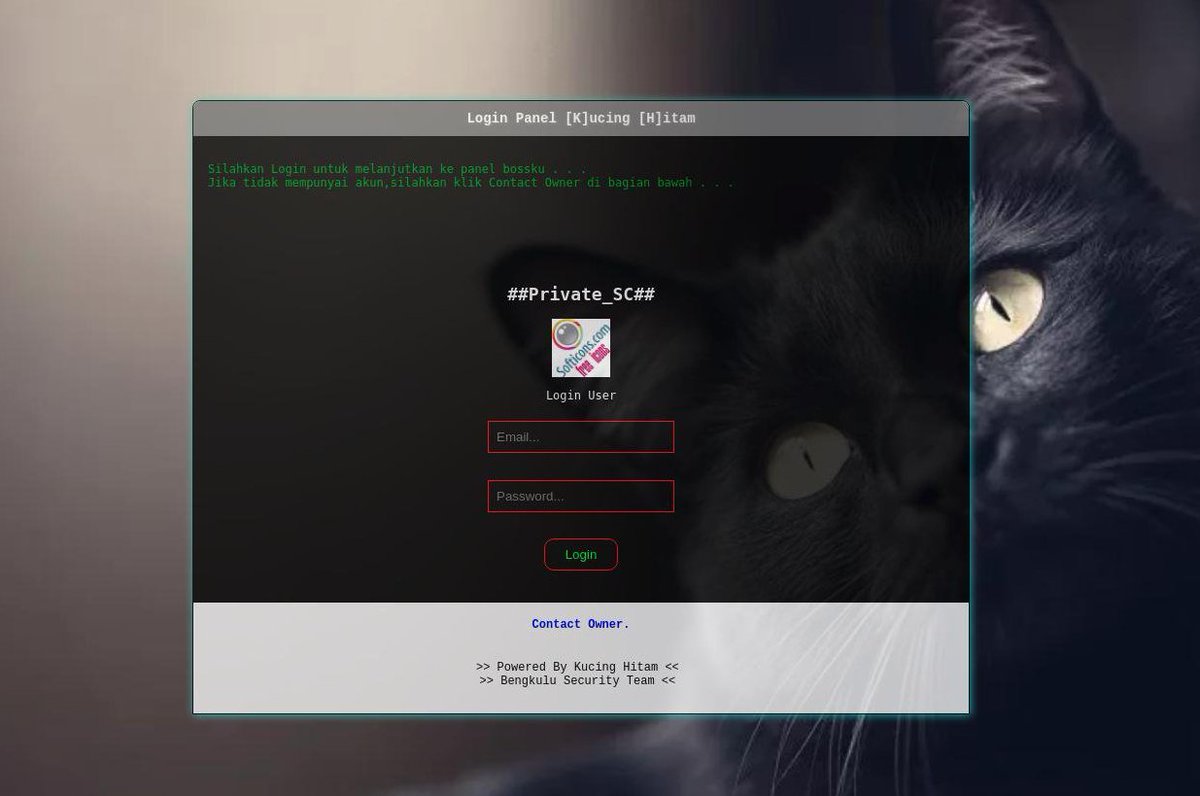

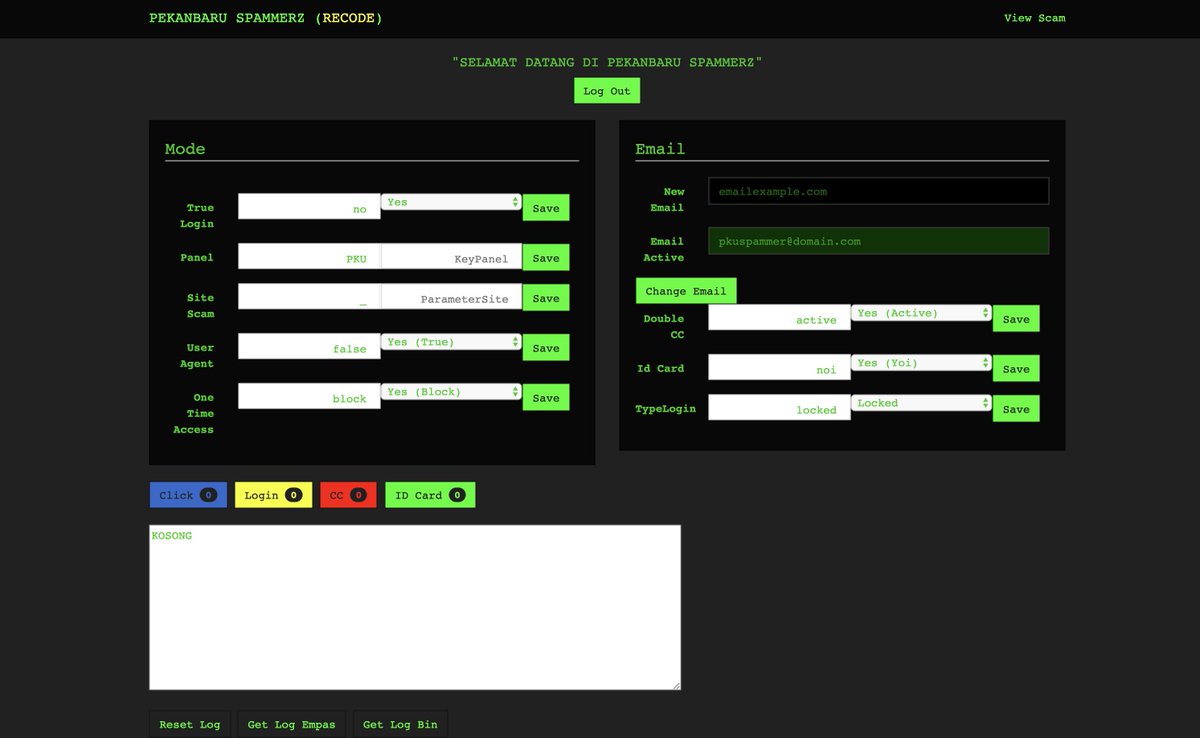
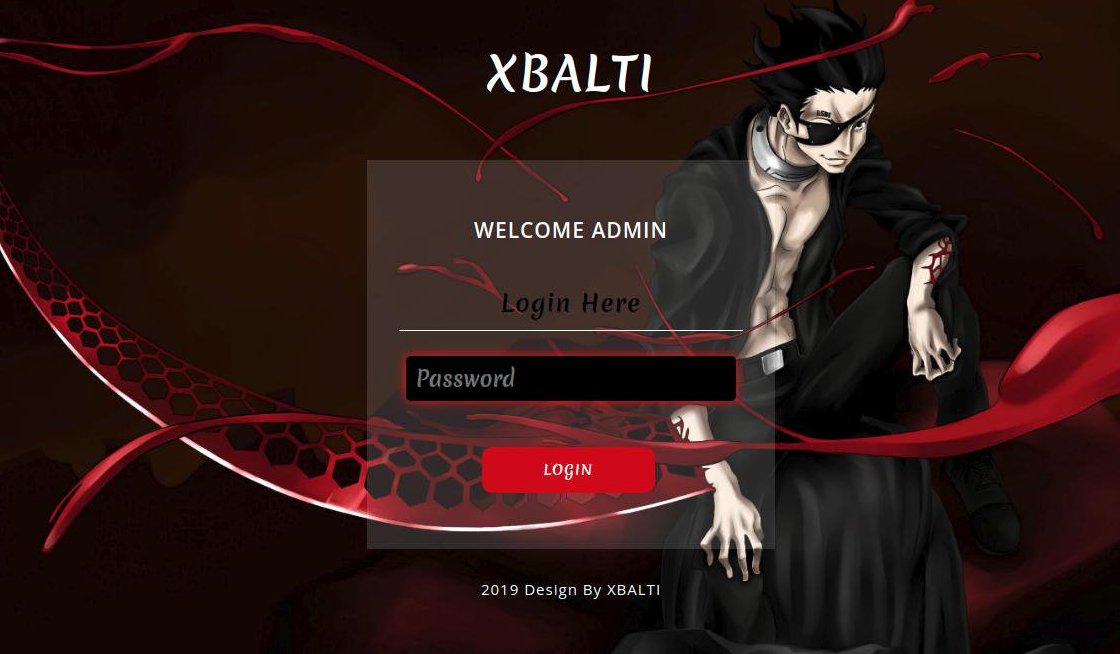
Also a big thanks to @dave_daves @ninoseki and @friedphishes for their contributions to the community.
Credit to @ANeilan for finding this panel.
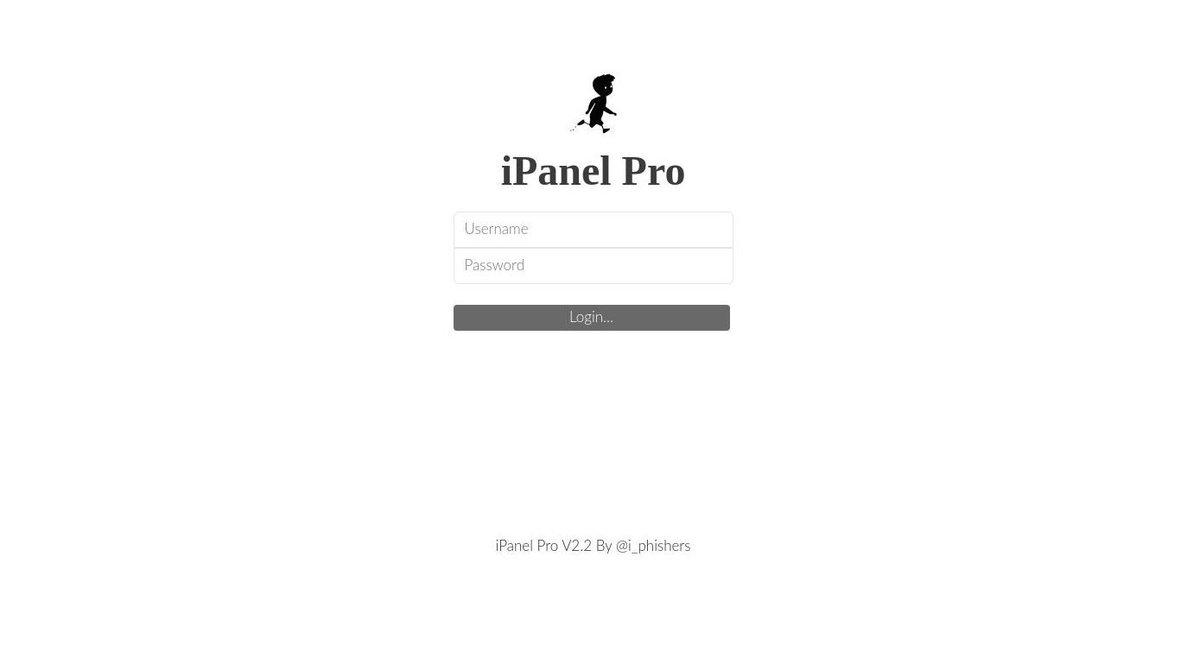
#adrenaline kit built by cazanova haxor admin login can be found under the /admin directory
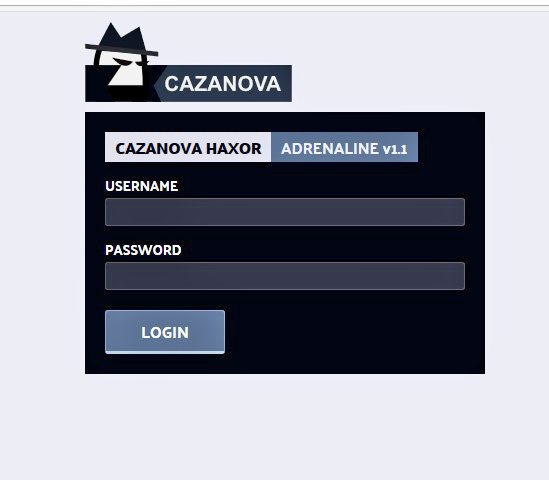
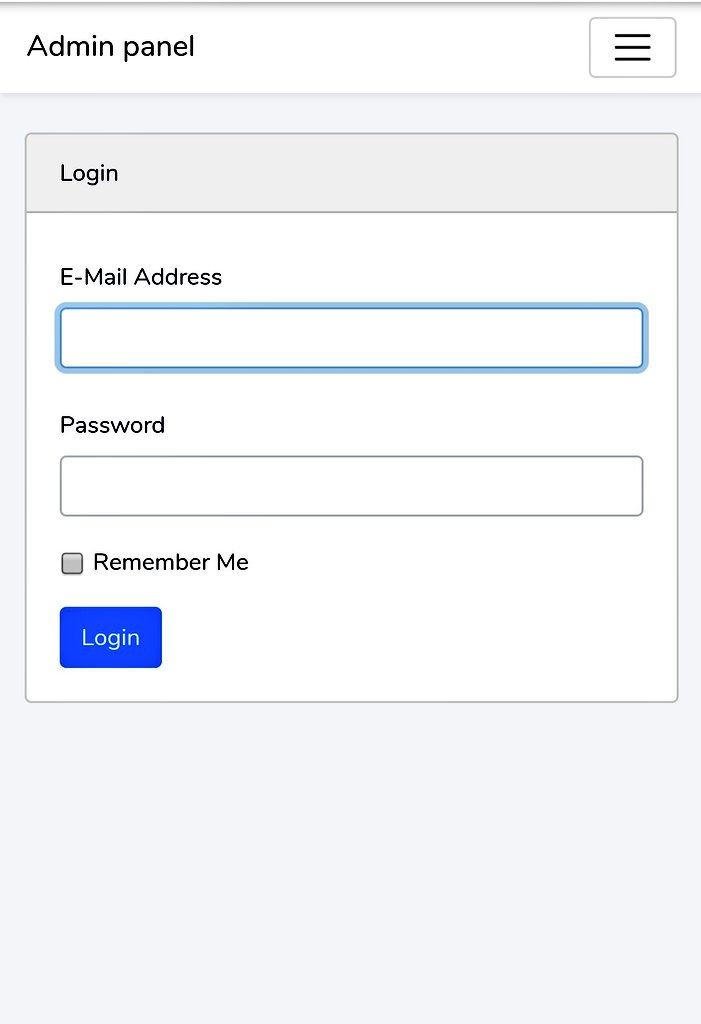
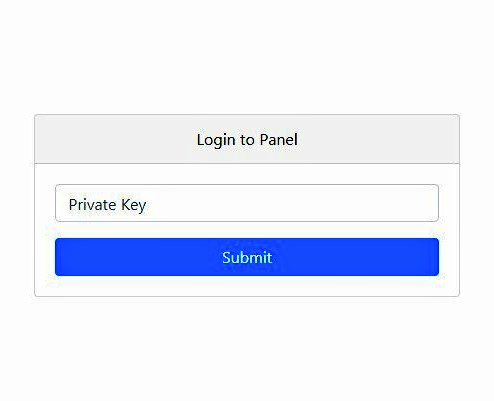
Private key (password) panel location is here /admin/login.php
Default private key on panel is "CLOUDS"
Thanks to @ActorExpose for finding
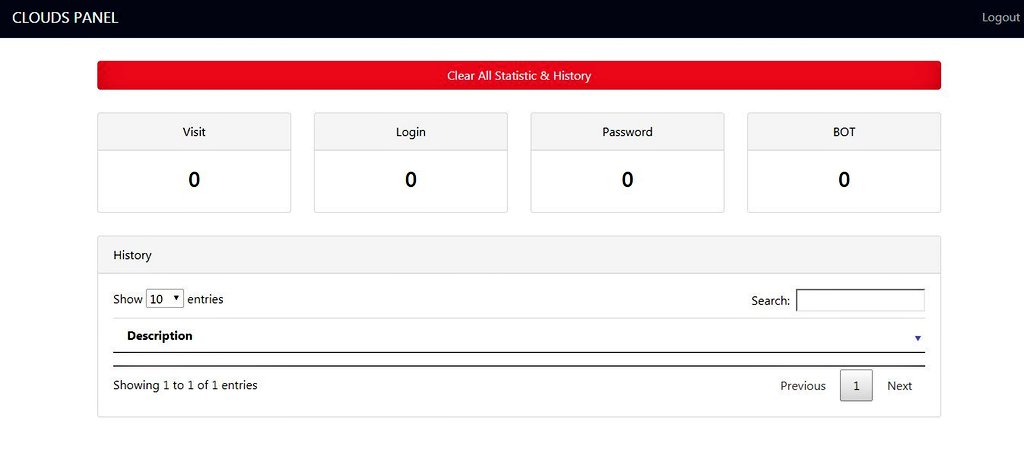
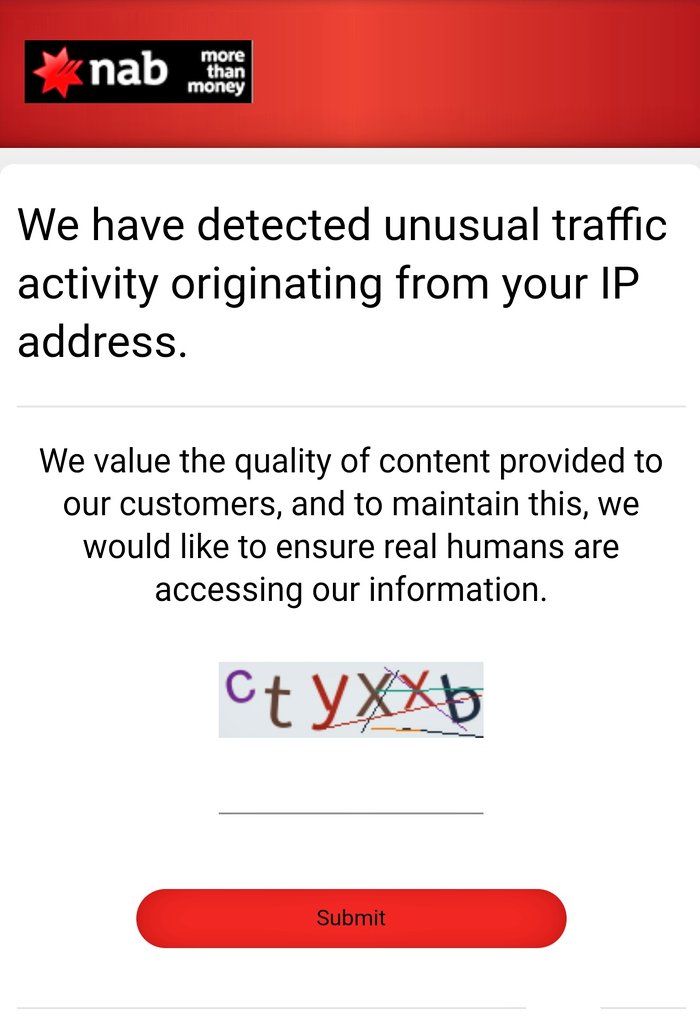
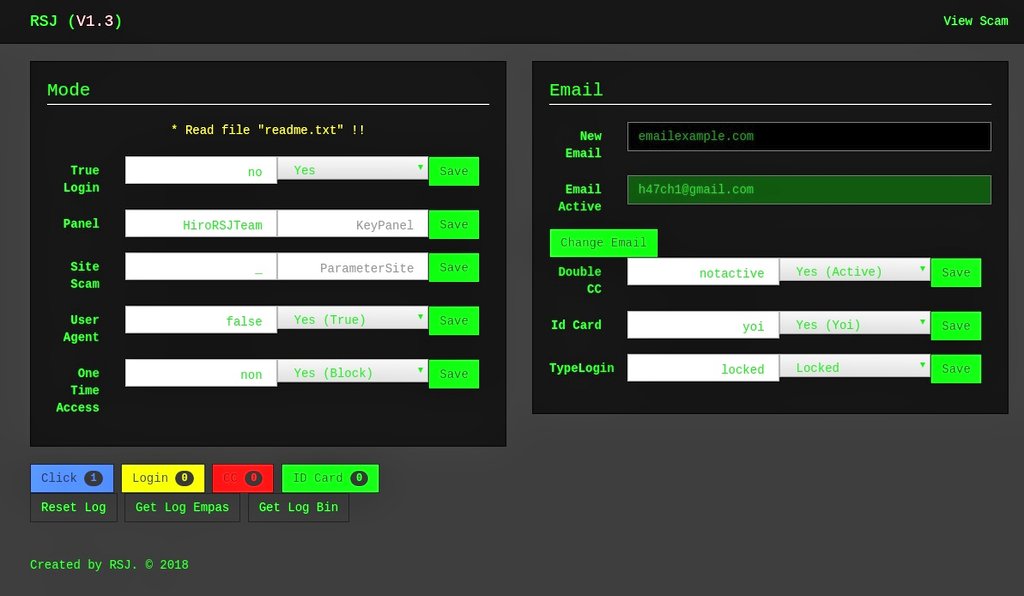
Can be accessed with the following PHP parameters: /panel.php?panel=HiroRSJTeam
If you access the panel without the parameters the alert pictured is displayed. Thanks to @sagar_ruta for alerting me to it.
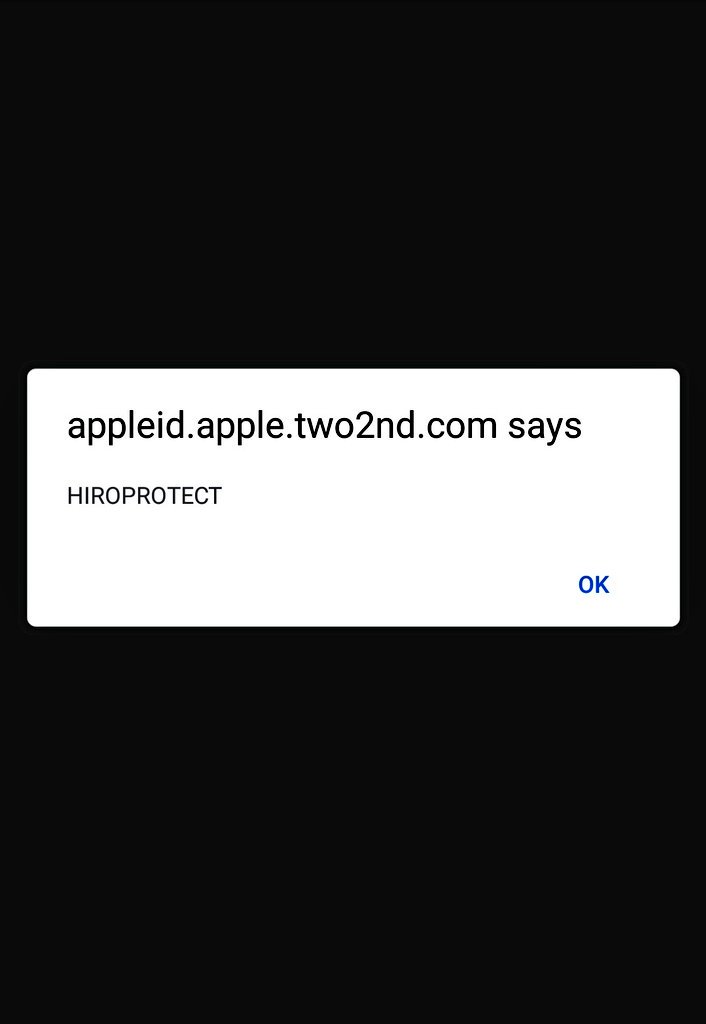
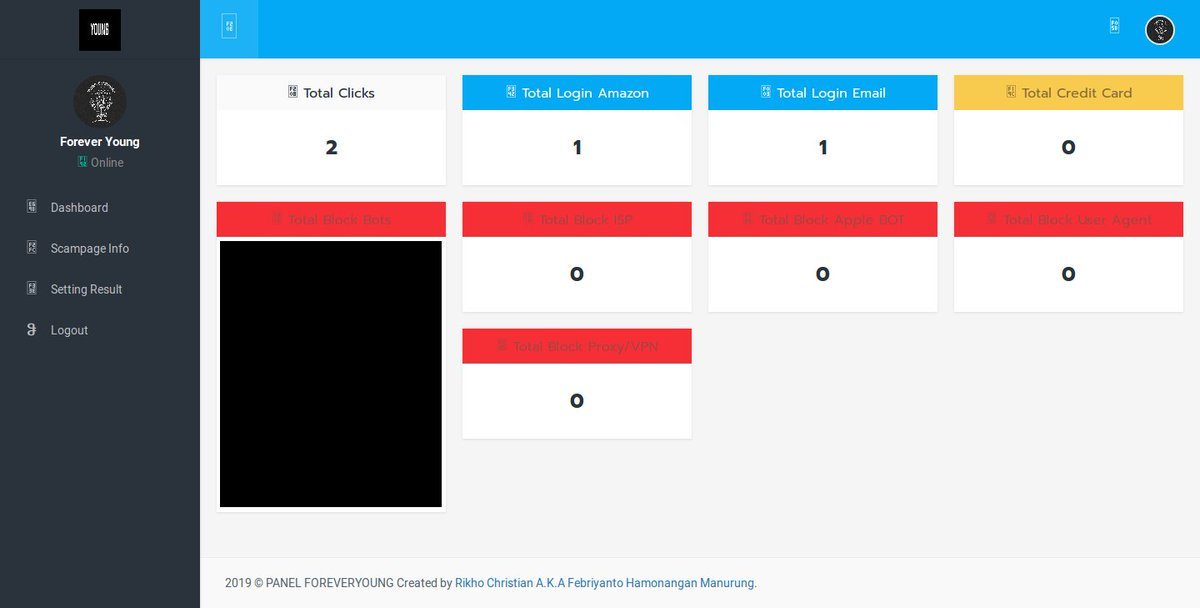
Seems to target Amazon creds as well and email and card details. Also fingerprinting can be done via the Facebook link to the threat actor author.
Thanks to @malwrhunterteam for alerting me.

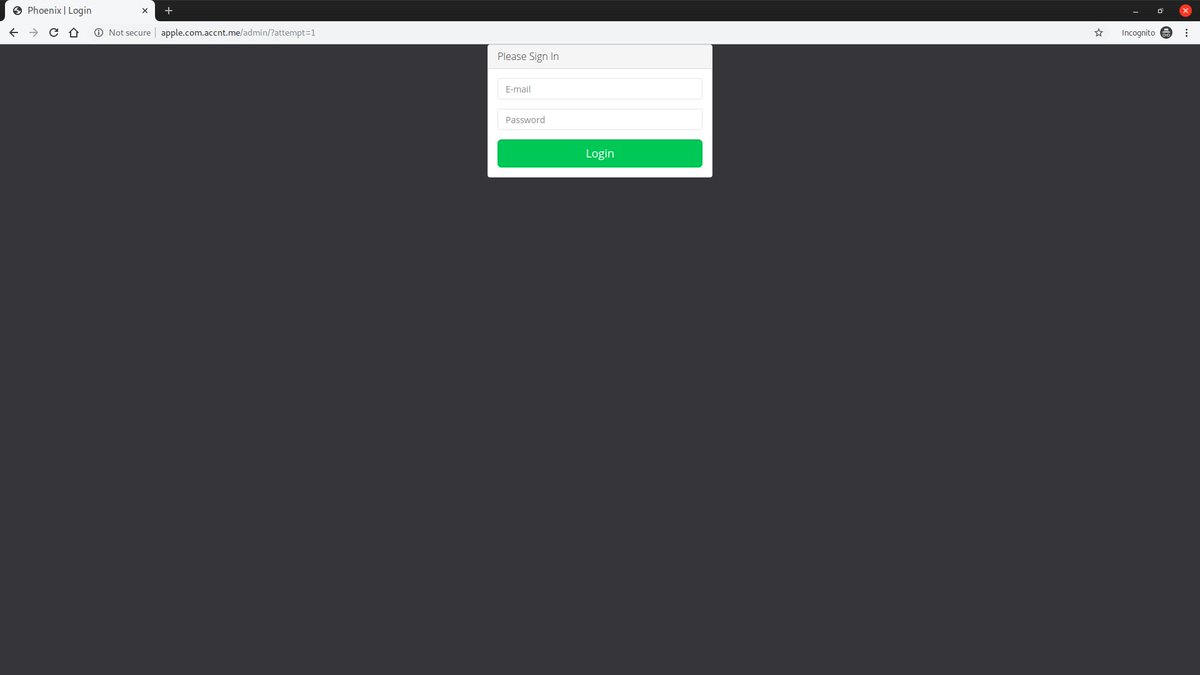
#Phoenix panel. Used Apple as a lure on #Phishing pages.
The admin panel is located /admin/?attempt=1
Thanks to @ANeilan for the tag.
created by facebook.com/founder.agility
Thanks to @420spiritz for finding it!