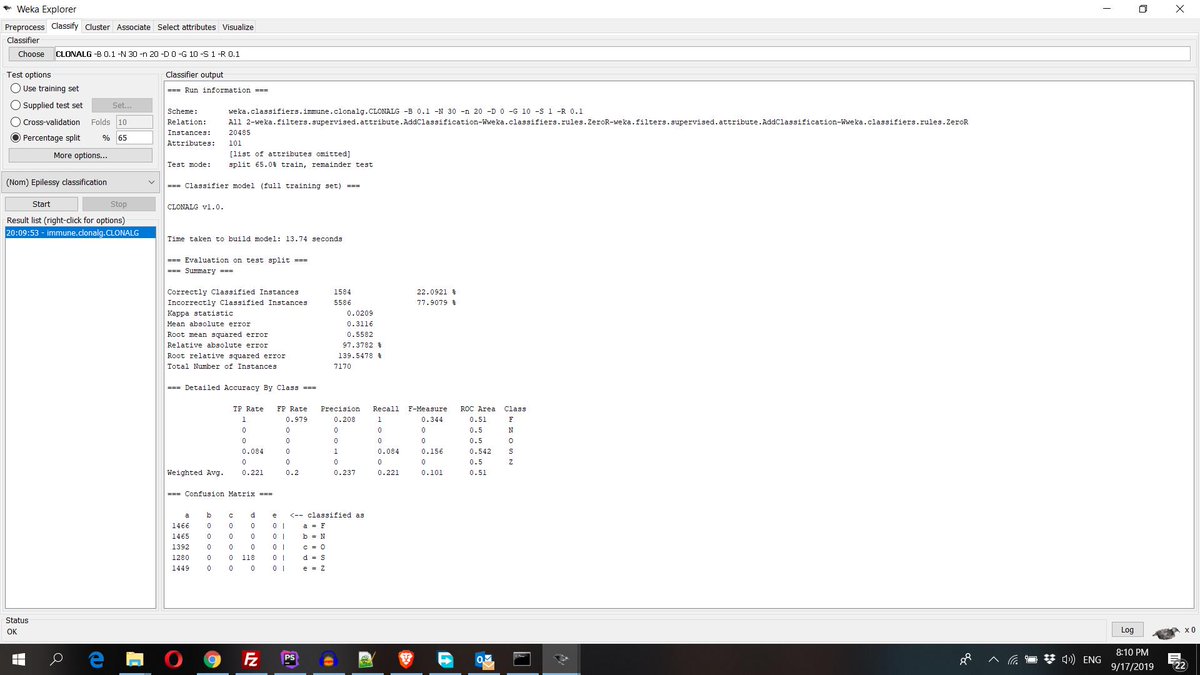
I have a hunt running looking for a known Magecart hash.
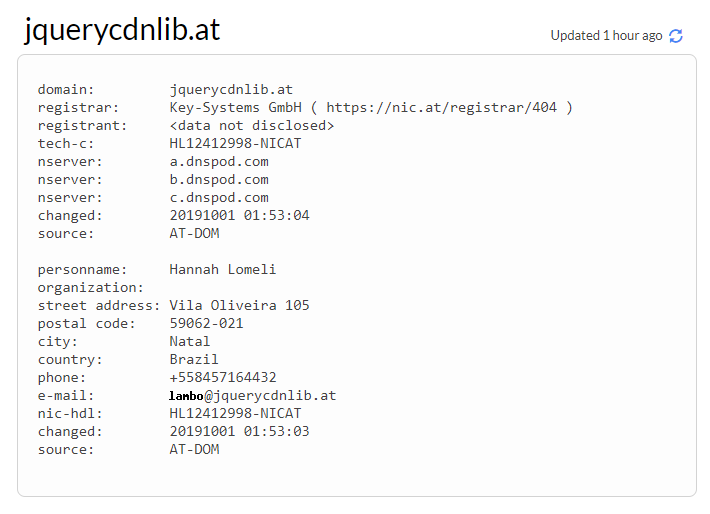
This morning a new site hit the search, looking at the site I then used the filename as a pivot. The filename which is infected with Magecart is "jquery_noconflict.js"
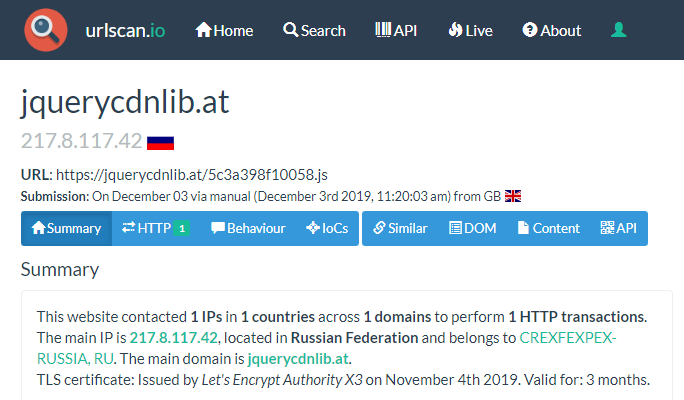
URL🌐- hxxps://jquerycdnlib.at
IP - 217.8.117.42
TLS🔐- @letsencrypt
If you enjoyed this thread then why not check out my other threat hunting threads:
-
-
@malwrhunterteam @jknsCo @dave_daves @nullcookies @dvk01uk @cybsecbot @JackRhysider @SecurityNewsbot @RiskIQ @Ring0x0 @ydklijnsma @Aamog @BleepinComputer @proofpoint @SteveD3 @ANeilan
♻️Retweets would be appreciated to help knowledge share!
Thanks.
@SINON_REBORN @echobit @three_cube @ThisIsNuse @pry0cc @malware_traffic @NarimanGharib @darienhuss @kfalconspb @RH_Poseidon @JAMESWT_MHT @kfalconspb