This is a thread about how to hunt and find #Phishing sites.
Retweets would be great to help spread the knowledge and please add your own techniques, ideas and suggestions.
Let's go hunting!

hxxp://www.new.froid-guyader.fr/libraries/sharepointcontract/
This is a #Phishing site against Microsoft Office
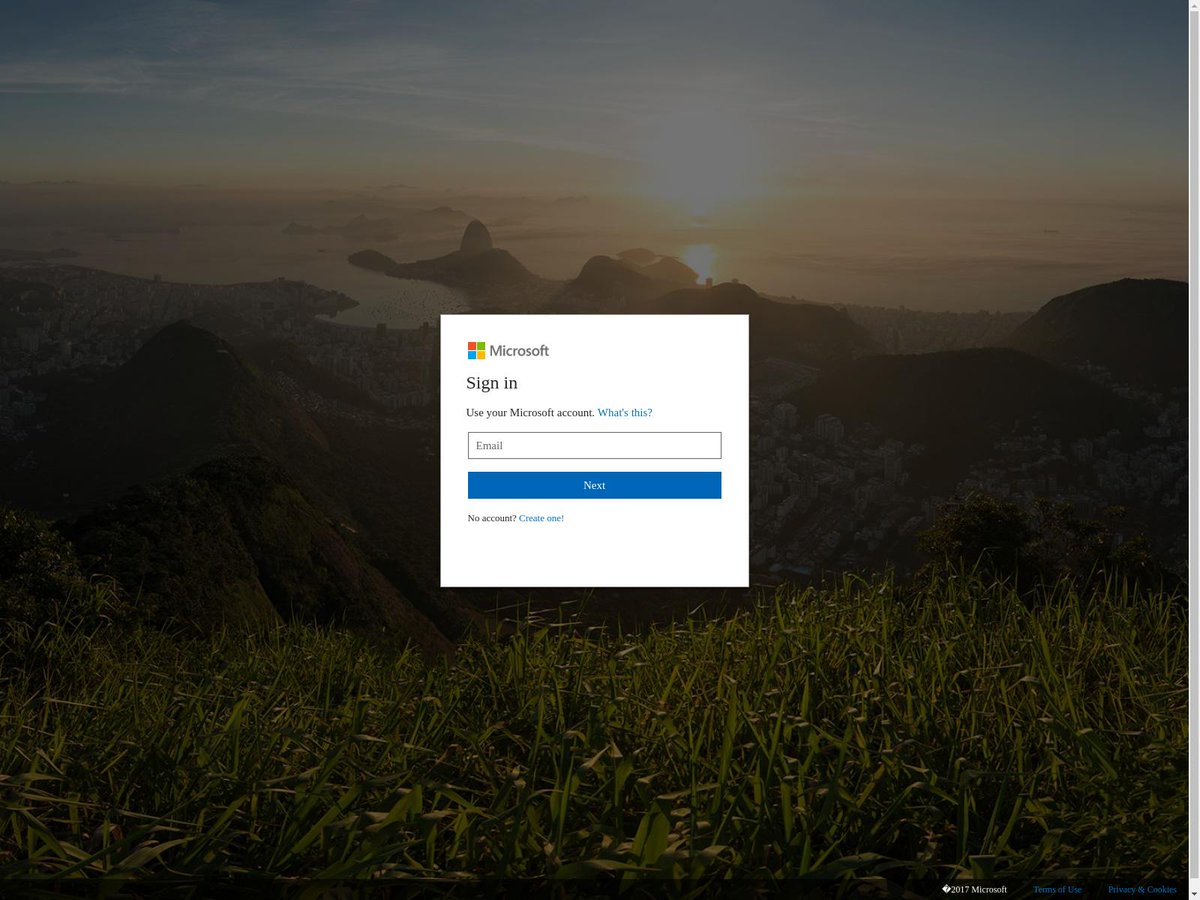
- hxxp://www.new.froid-guyader.fr/libraries/
- hxxp://www.new.froid-guyader.fr/
- hxxp://www.froid-guyader.fr/
- hxxp://www.new.froid-guyader.fr/libraries.zip
Again sadly no hits. There are some great tools to automate this. I suggest checking out this tool made by @cybercdh :: github.com/cybercdh/phish…
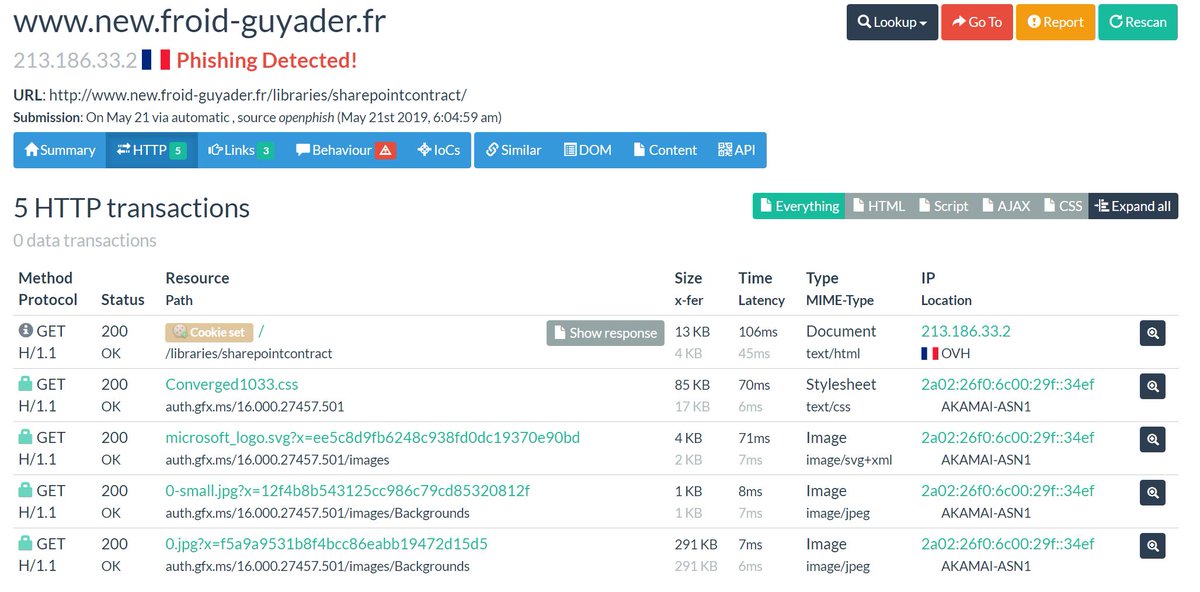
This is a big #phishing campaign. There is a huge number of sites.
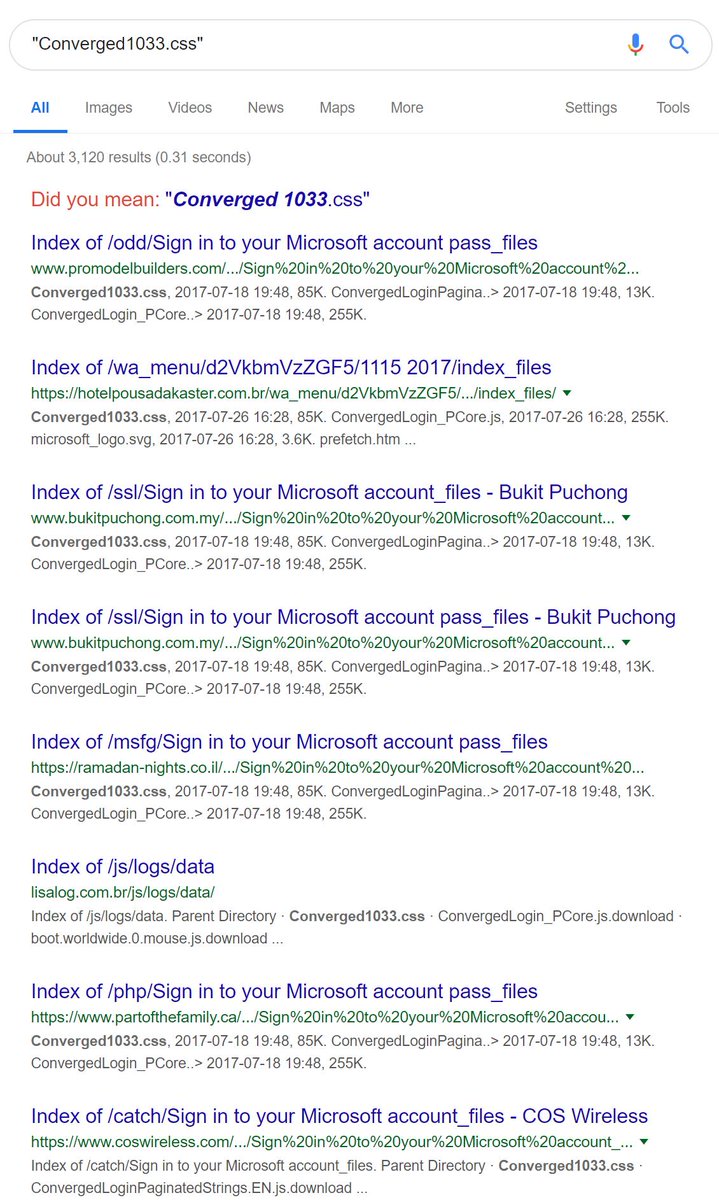
chasecardonlinerestore[.]com picked up the same campaign. Both URLs used the
same name server steelstory[.]org
- @JCyberSec_
- @IpNigh
- @PhishingAi
- @packet_Wire
- @ActorExpose
- @PhishStats
- @FeedPhish
- @JayTHL
- @Cyberfishio
- @dave_daves
- @ozuma5119
- @smica83

- @PhishStats - phishstats.info/phish_score.txt
- @open_phish - openphish.com/feed.txt
- @PhishTank_Bot - data.phishtank.com/data/online-va…
- @urlscanio - urlscan.io/live/
:: Phishing Admin Panel Hunting Thread ::
In this thread we will find ways to hunt and attribute phishing admin panels.
This is a continuation from my #phishing hunting thread released earlier this year










