
- github.com/MetaMask/metam…
- github.com/MetaMask/metam…
- github.com/MetaMask/metam…
- github.com/MetaMask/metam…
I think the Metamask team is looking into doing this long term: github.com/MetaMask/metam…
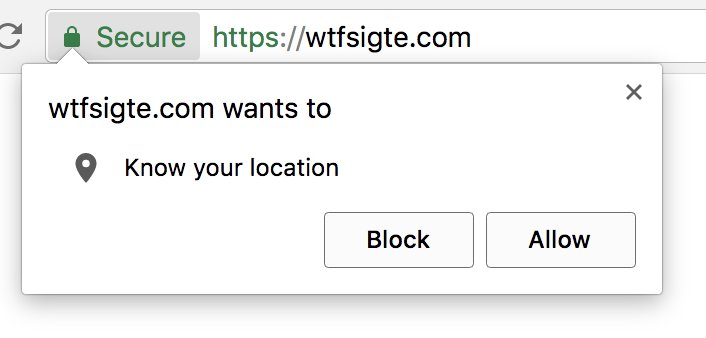
1. Hardcode that only metamask.io/whitelist can call invoke some whitelist functionality in extension
2. dApps opens popup for metamask.io/whitelist?url=…
3. Extension asks if you want to give example.com access to your wallet