If you've read the report (below),
what QUESTIONS do you still have?
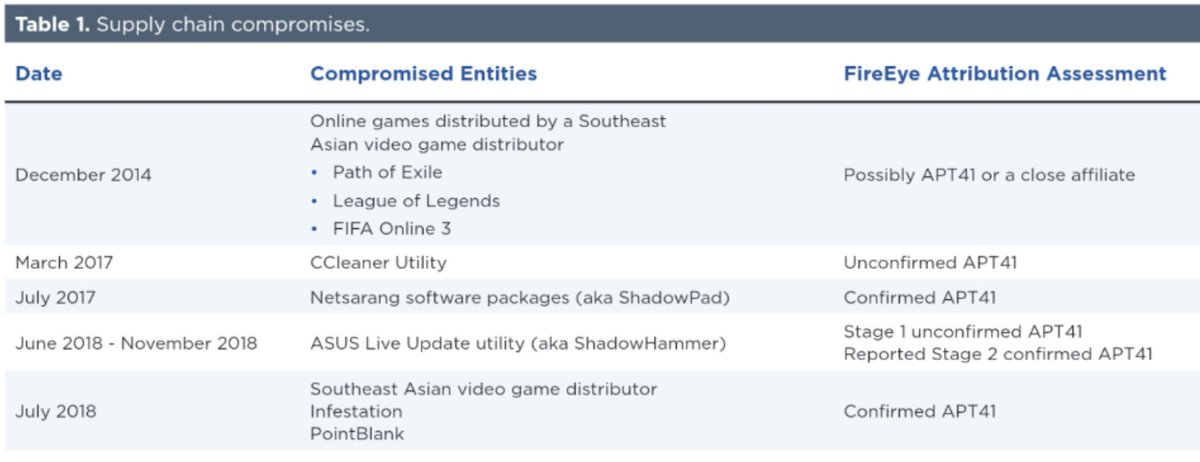
1️⃣ Supply chain compromises (and nuanced attrib)
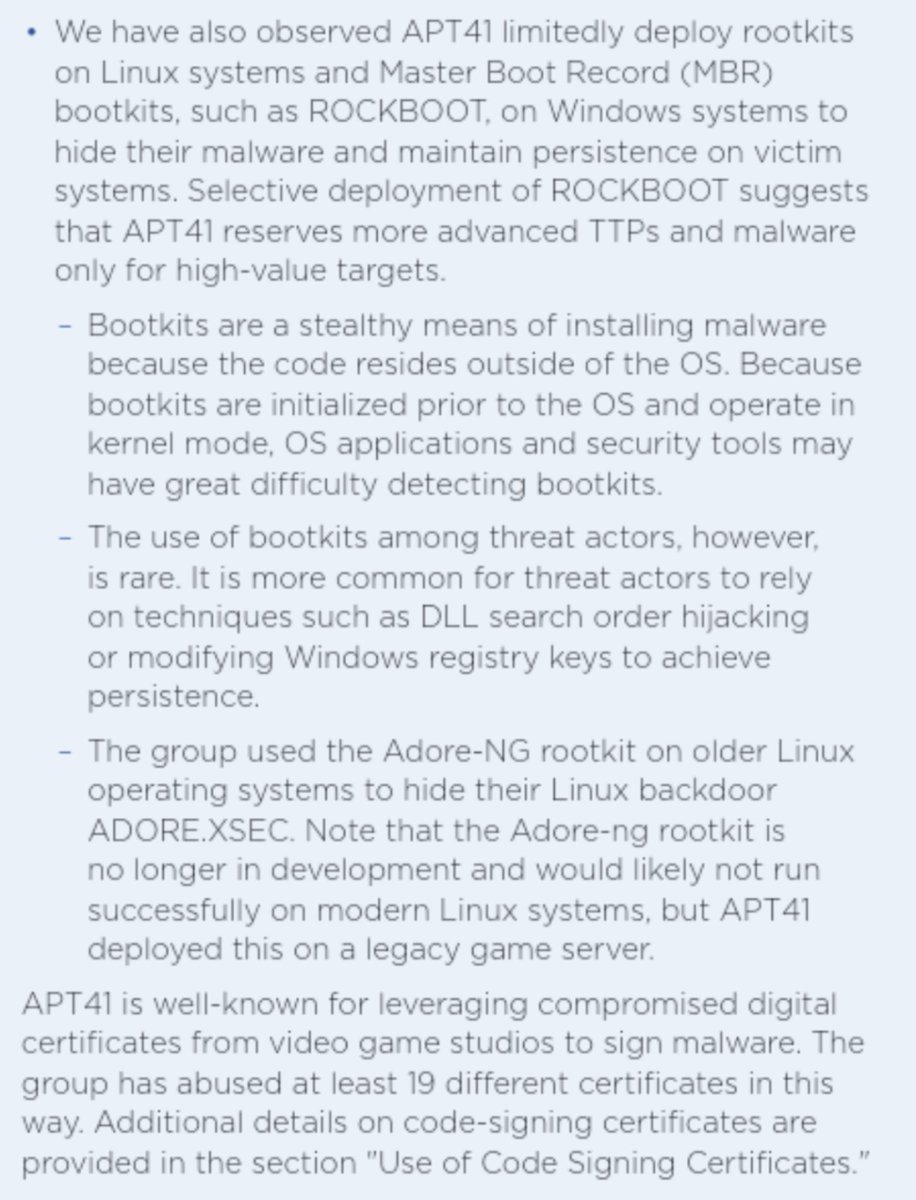
2️⃣ Linux & Windows MBR bootkits and how they were found 😉
3️⃣ Third party access 🌶️
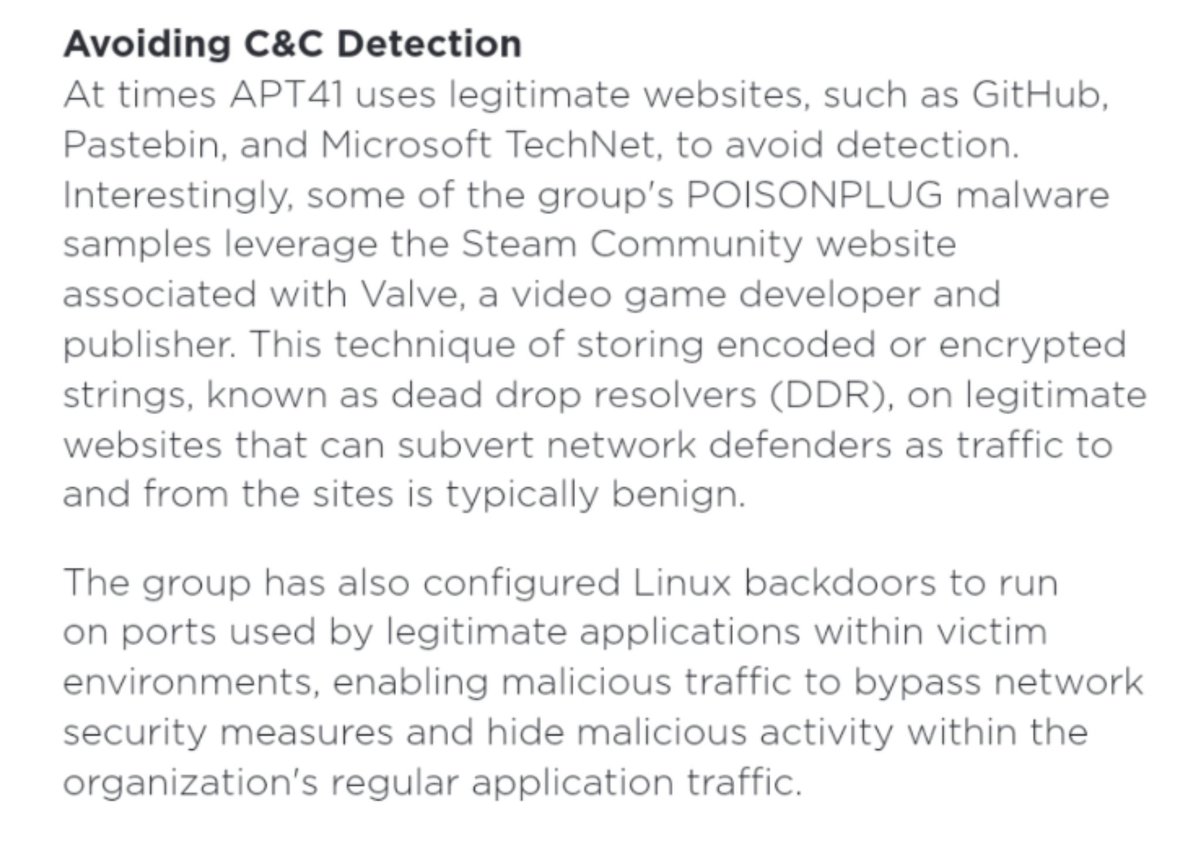
4️⃣ Legitimate web services use (and their obsession with Steam)
+concurrent ops, overlaps!
content.fireeye.com/apt-41/rpt-apt…

"Double Dragon: The Spy Who Fragged Me" 🎮
#APT41 with Jackie, Ray, and @cglyer
pscp.tv/FireEye/1vAGRW…
We name dropped the hell out of the #FLARE team (incl. @williballenthin, @jay_smif)
Spice zone: we shared that APT41 might do #flareon6, previewed a #ManagedDefense blog, + SMS backdoor:
Here are some blogs we mentioned:
1️⃣ 2015 blog on bootkits (examples from FIN1 #BOOTRASH + APT41 #ROCKBOOT): fireeye.com/blog/threat-re…
2️⃣ 2018 #BOOTWHAT blog on how we find them at scale: fireeye.com/blog/threat-re…
3️⃣ 2013 blog on #CHINACHOPPER (by @TekDefense): fireeye.com/blog/threat-re… (part 1 of 2)
I'm including this one since @cglyer gave a quick mention of the web shell, but if it's *somehow* new for you, go read this blog and play with the caidao client.
That's it for my mini "The Spy Who Fragged Me" recap thread. 😎
@threadreaderapp unroll show notes!
I took @stonepwn3000's advice