- Bots tend towards an equilibria (w.r.t. gas price)
- There are Wall St.-like latency wars! (Bots have started to do more raises over time.)
cc @phildaian
#CESSummit2019
A great reminder that DEX arbitrage is just the tip of the iceberg—only .1% of total volume. See @BitwiseInvest report for example of CEX. (95% of reported volume is fake!)
#CESSummit2019
- Creating GasToken (used by bots)
- Publishing blog post (which brought more attention!)
Check out the paper w/ @phildaian! arxiv.org/abs/1904.05234
#CESSummit2019
- Right compliance balance with AML/CFT/KYC vs. anonymity
- Incentivize CBDC by allowing folks to use it to pay interest
- Tech comes after use case
#CESSummit2019

i.e. It's not just CBDC vs. Bitcoin but rather dimensions of programmability, collateralization, etc.
#CESSummit2019
Main scary thing that "hit" me: zero-day vulnerability disclosures for CBDCs. (!)
#CESSummit2019
First, starting with three contexts:
- Impetus for this (crypto catalyzed innovation; payment fees are 1% of GDP)
- Other CBDC and Corporate Cryptos (Telegram)
- FB's previous 3 attempts
#CESSummit2019

- Monitoring illicit activity (KYC, AML). FinCEN and FATF.
- Macro financial stability. The Fed.
- Consumer/investor protections. Securities law. SEC and CFTC.
#CESSummit2019
Facebook will try to dodge "looking like a PIV" (see 1940 Act) by keeping 60% in cash, 40% in short-term govt. bonds.
If they do this, Gary recommends they change the *law* itself.
#CESSummit2019
#CESSummit2019
1. Use the terms "exogenous" and "endogenous".
2. Mechanism design analysis doesn't replace classical distributed systems analysis. But important to add.
(I had a funny seat.)
#CESSummit2019

In a paper they look at *one* aspect very well. Every paper has something unrealistic about the model. By design. To understand a certain mechanism super well.
#CESSummit2019
- 2 fab providers (TSMC, Samsung)
- <5 chip manufacturers (Bitmain, Bitfury, Genesis)
And rules:
- Zero-sum
- So ethical behavior is difficult
#CESSummit2019

- *Assume* we will have centralized mining. Then what should we do?
--> Minimize powers that miners have.
Stop:
- SPV
- Their ability to change consensus rules
- Their ability to signal soft forks
#CESSummit2019
But the issue is that these penalties need to be off-chain!
Off-chain penalties are generally of the form: Threaten future revenue given how expensive mining and hardware is.
#CESSummit2019
- Quit all together. (Sell coins. Full exit.)
- Change hashing alg. (When Sia did this, miners lost $100M. And they were more respectful of devs afterwards!)
- Counterattack! (Lots of sub-game theory here.)
#CESSummit2019
#CESSummit2019
Instead of assuming (like @DavidVorick's talk did) that mining *will* be centralized...take miner centralization as an *open question* and find ways to defend against it.
#CESSummit2019

"The future of decentralization in proof-of-stake is bleak. But w/ proof-of-work it's even bleaker."
"...Actually though, the jury is still out. Lots of research questions to tackle here."
#CESSummit2019
-Watch out for "timing correlation attacks"
-"Balance discovery attacks" may allow attackers to deduce payment source/destination
-Is "probing protection" possible?
#CESSummit2019
Is the cost to secure the network ~= the market cap?
@TheBlueMatt's smart response: it's correlated with that, but more a function of "untrusted" volume. (e.g. If KYC'ed exchanges double spend, then state steps in.)
#CESSummit2019
He predicts a future with 10s of trillions of blockchains (not 1, e.g. BTC). More than one per human being / IoT device. 😂
#CESSummit2019
Permissioned chains have (mostly) been absent from this event (depending on your POV on Libra validators :), but def important for this field.
#CESSummit2019
- Can't accept probabilistic settlement
- Don't need the currency
- Don't want costly validation (pay w/ rep or permission not CPU/kWh)
- Don't want come-and-leave validators
- Don't want transaction transparency
#CESSummit2019
Transparency is often portrayed as "great for customers". But in fact it may *hurt* consumers by making punishing collusion easier, which makes collusion easier (counterintuitively), which is bad for antitrust.
#CESSummit2019
She says: And maybe we shouldn't "count" that? Or maybe we should? That's an open definitional q for this community.
#CESSummit2019
#CESSummit2019
bford.info/2019/09/23/rat…
- @mZargham leading a session on Complex Systems
- @socrates1024 leading a session on how our community should do research and peer review
#CESSummit2019
#CESSummit2019
metascience2019.org
#CESSummit2019

The underlying thesis is that journals should be economically modeled as a *club good* (as opposed to a public good or private good).
#CESSummit2019

- Journals (clubs) have the same producers/consumers
- This is different than journalism, where those are separate
- The internet was good for journalism (broadcasting/narrowcasting).
- Blockchain may map well onto journals.
#CESSummit2019
#CESSummit2019
papers.ssrn.com/sol3/papers.cf…
@profjasonpotts with an interesting point: "Far away events are a costly signal." (As a way to signal/filter clubs.)
#CESSummit2019
It was *hard*. But it's here!
docs.google.com/document/d/1a1…
#CESSummit2019

#CESSummit2019
#CESSummit2019

- Assign reps from 2+ different fields to each reviewed paper
- Reviews are asked to collaborate on a summary, a "foreword from the reviewers" to be published alongside each paper.
- Explain standards ("validation" form).
#CESSummit2019
(Quick small idea: using @KialoHQ-style UX. kialo.com)
#CESSummit2019
To some extent, this is against @socrates1024 ideas for CES (to have reviewers write a forward).
#CESSummit2019
Where have we aggregated open research questions for BTC, ETH, etc.?
cc @kanzure @drakefjustin @zmanian
#CESSummit2019
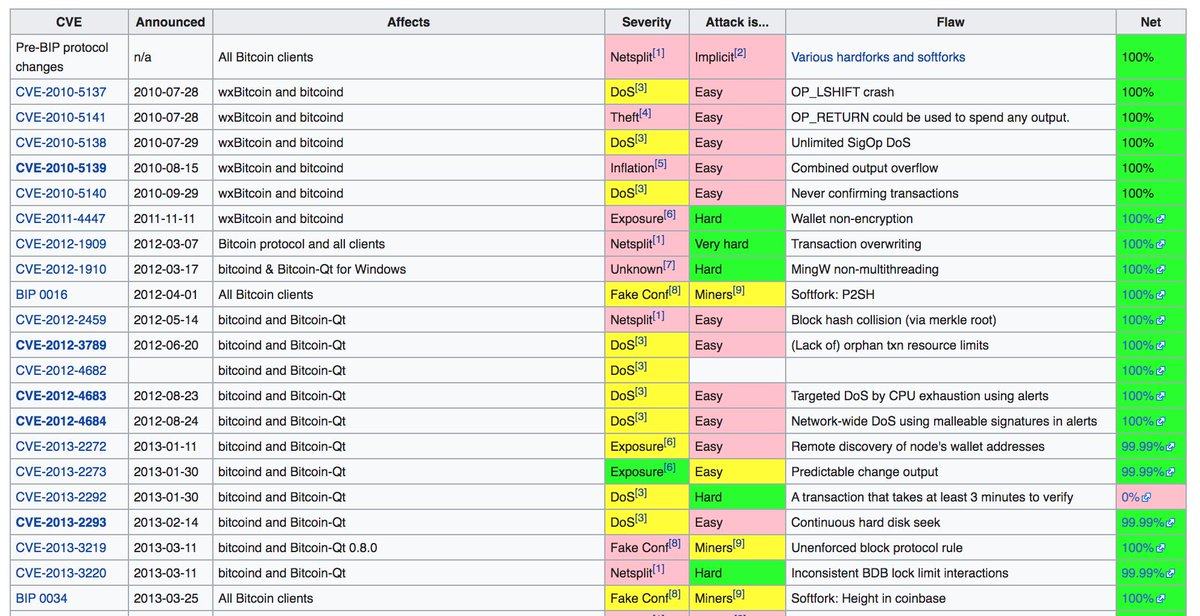
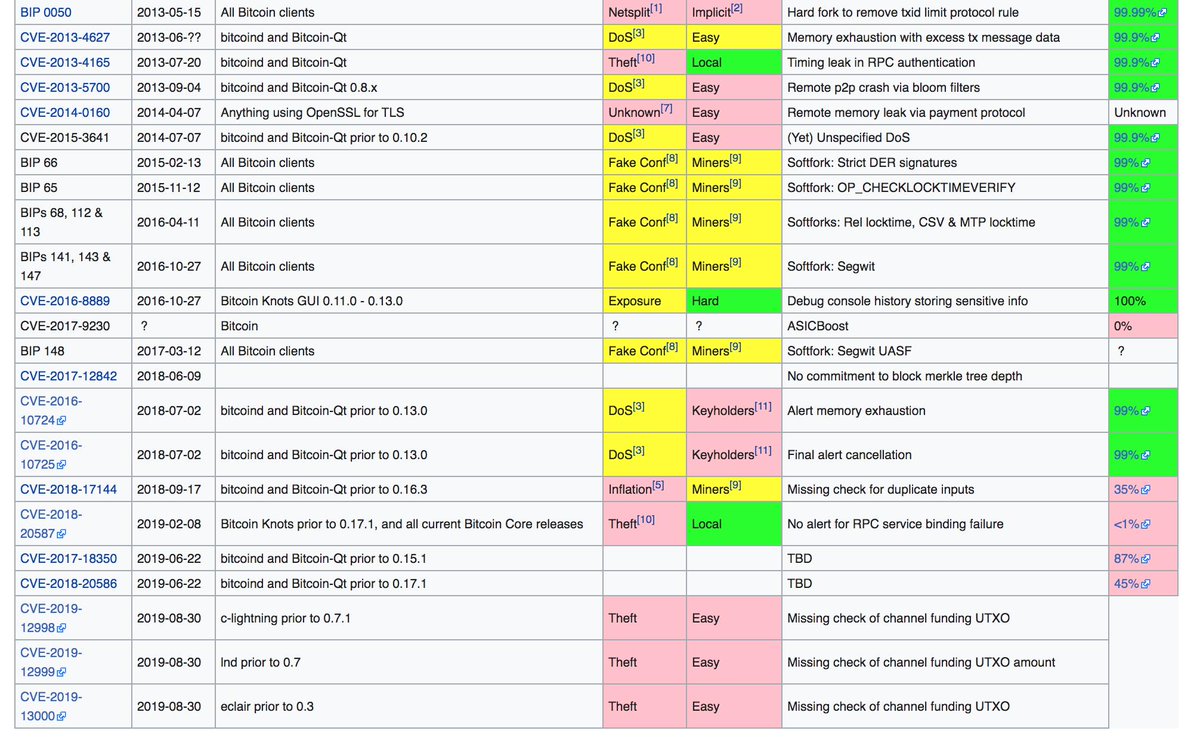
en.bitcoin.it/wiki/Common_Vu…
#CESSummit2019
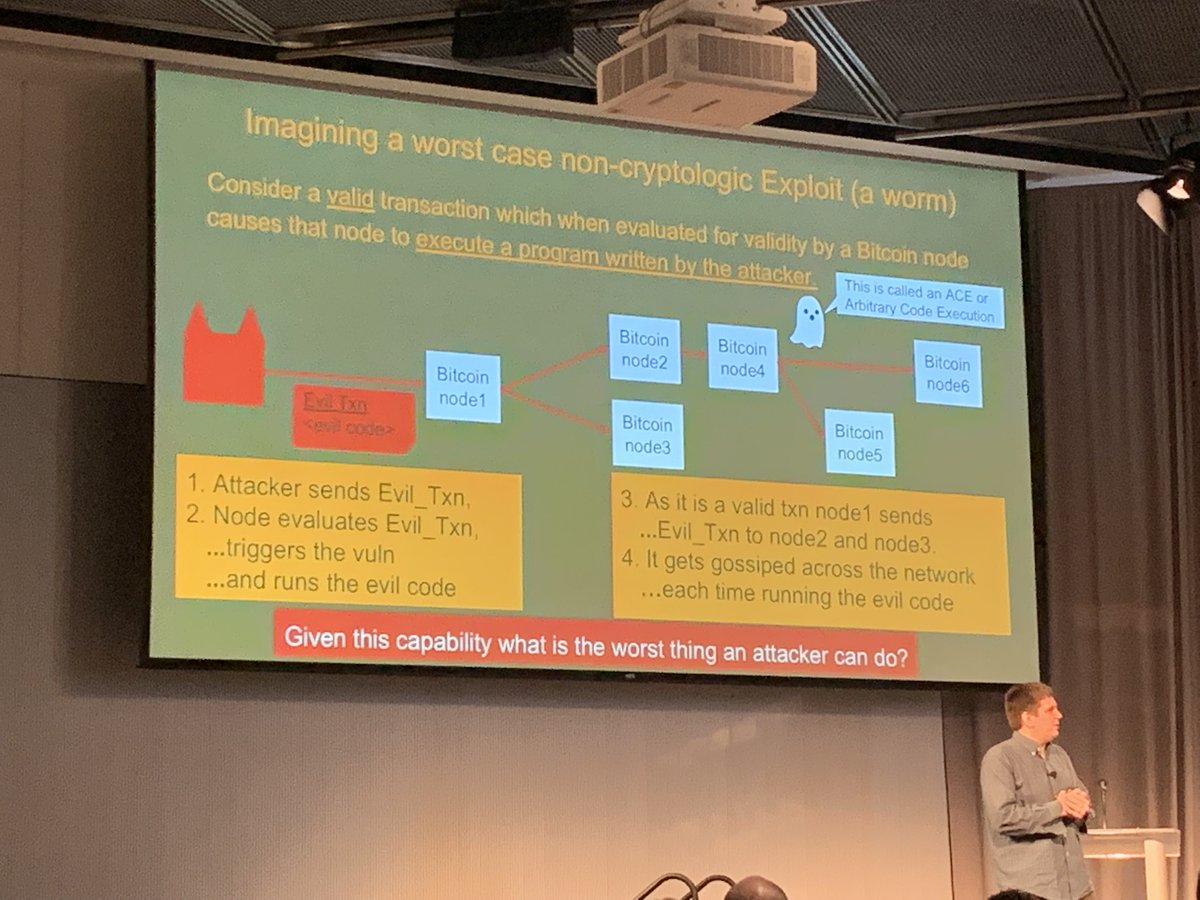
A *valid transaction* that causes a node to *execute a program* written by the attack.
#CESSummit2019
"My name is Carl, and I'm here to haunt your dreams." :)
#CESSummit2019

First, how to protect against runtime dependencies?
Minimize the # and audit them. At runtime, Bitcoin Core only allows a subset of these dependencies to run.
#CESSummit2019
How to protect against *build-time* vulnerabilities? Gitian Reproducible Builds!
This is a super cool thing that allows folks to run the same build "from scratch" and to check those builds against each other.
#CESSummit2019
But reproducible builds aren't enough! A warning about "trusting trust". How do we trust our toolchain?
It's like yogurt: you create the yogurt/toolchains with previous yogurt/toolchains. 😂 (It's turtles all the way down.)
#CESSummit2019
Solution: use GUIX to audit the toolchain. See dependency graph below.
Eventually the hope is to decrease the size of the binary seed bootstrap.
Right now: 232MB.
Soon: MES 131MB
Optimal: hex0 357 bytes.
#CESSummit2019








