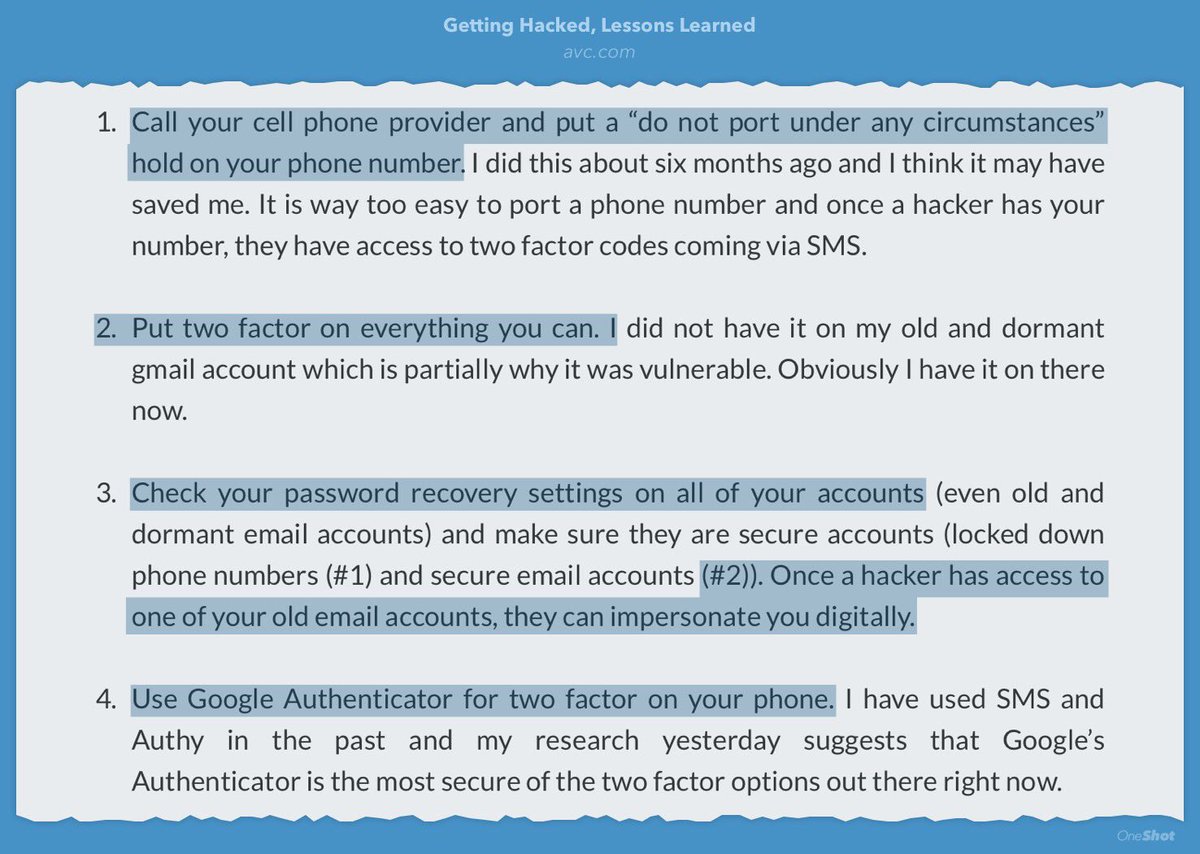
avc.com/2017/06/gettin…
"Russian malware communicates by leaving comments in Britney Spears's Instagram account"
boingboing.net/2017/06/07/wat…
Hacking wind turbine farms!
wired.com/story/wind-tur…

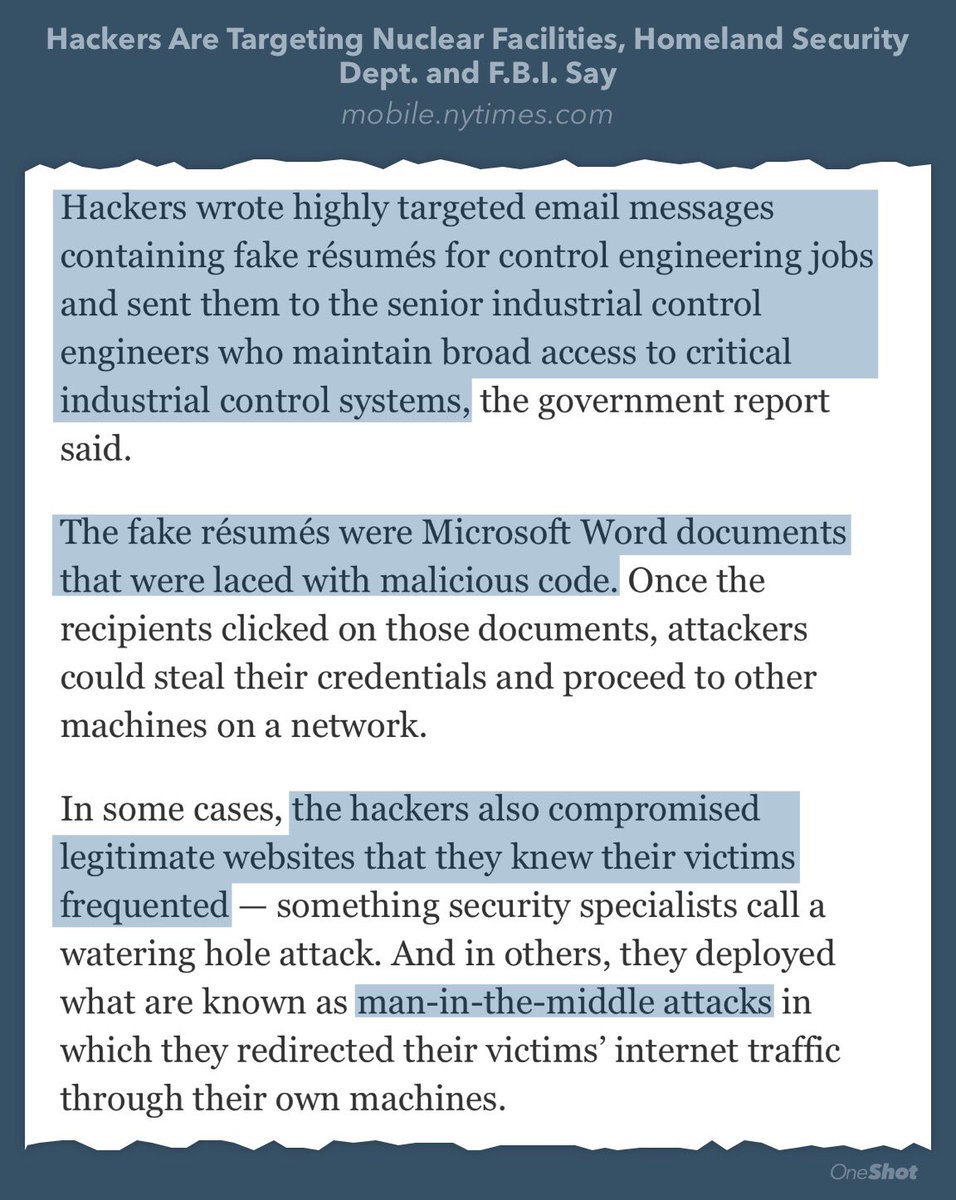
Hackers targeting nuclear facilities!
mobile.nytimes.com/2017/07/06/tec…
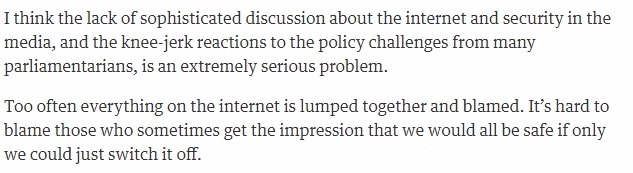
theguardian.com/commentisfree/…
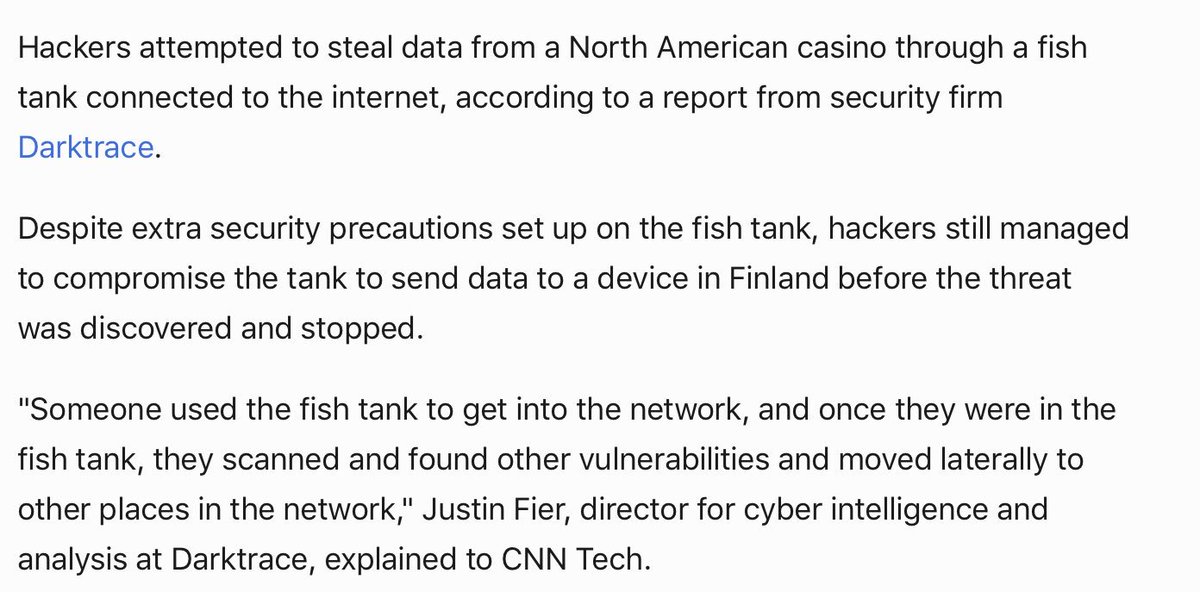
"A smart fish tank left a casino vulnerable to hackers"
cnnmon.ie/2u9JZfG
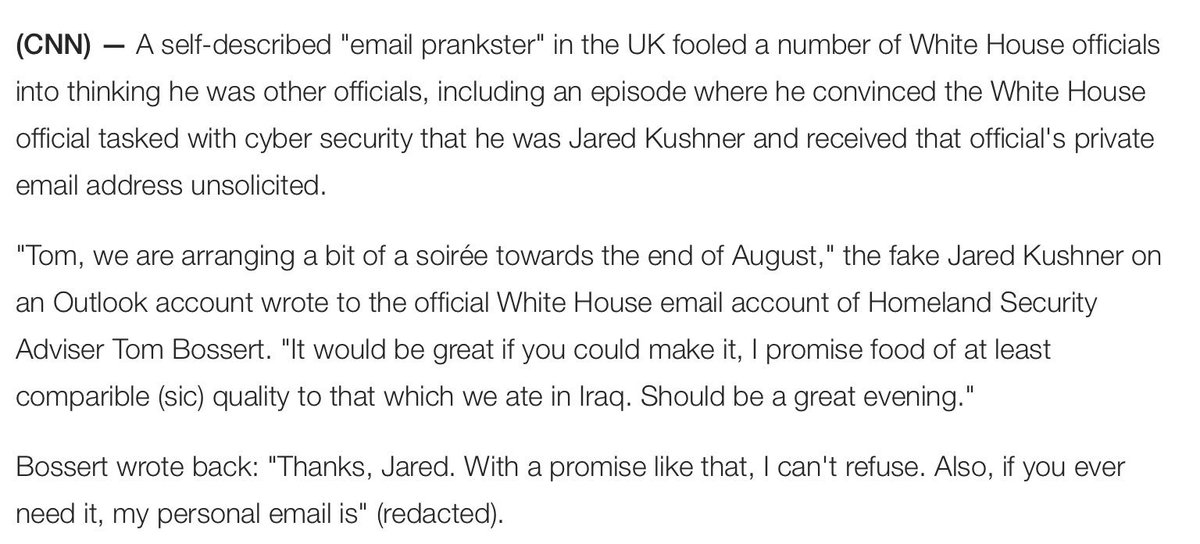
theregister.co.uk/2017/07/29/us_…

Connected turbines & ransomware.
ft.com/content/81c010…

amp.cnn.com/cnn/2017/07/31…
STEP 2: Game Google results!
Malware. Encoded in DNA. That infects the computer running a gene-sequencer 😳
wired.com/story/malware-…

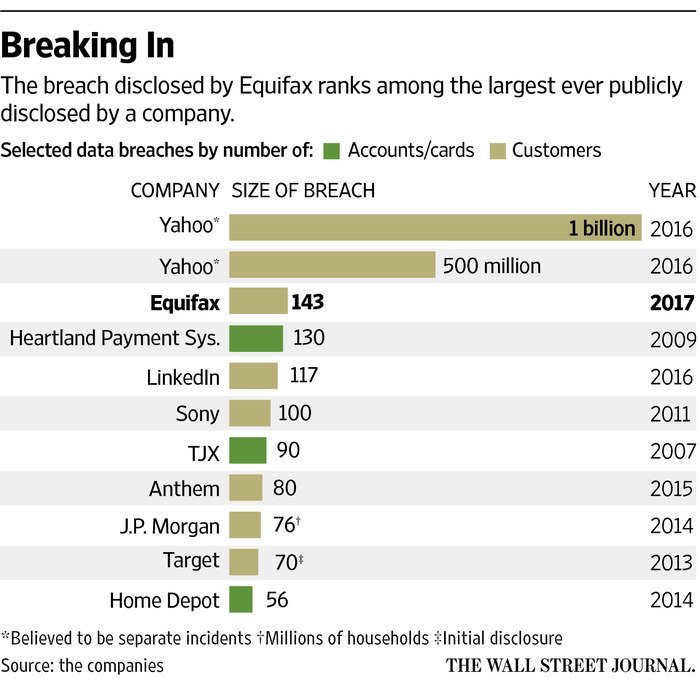
nytimes.com/2017/08/21/bus…
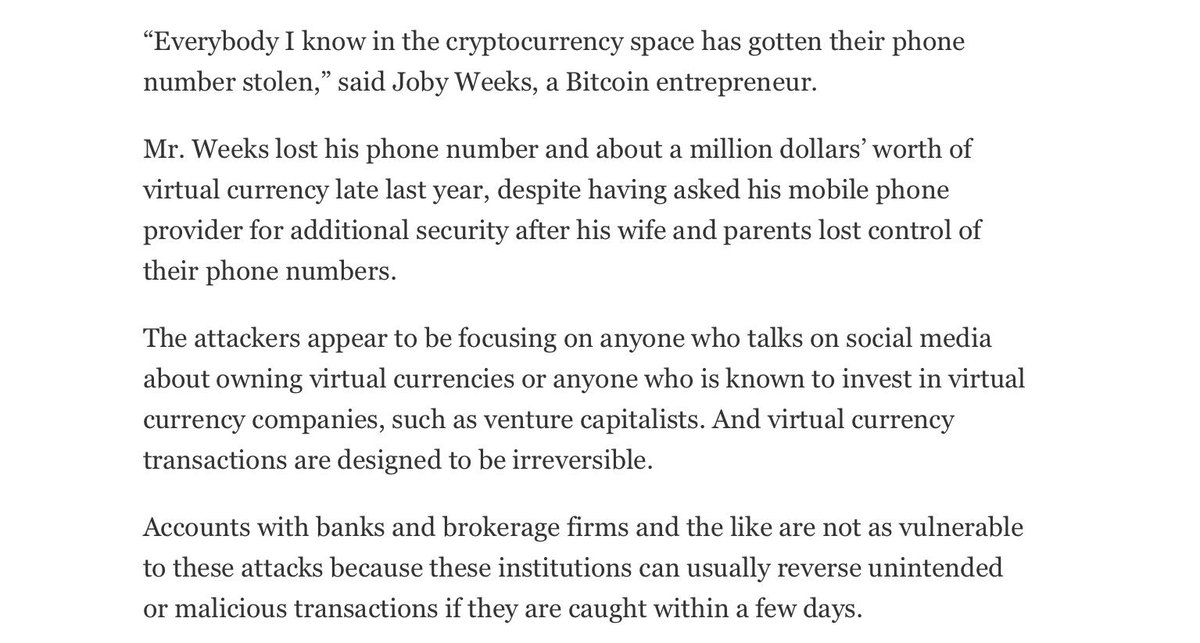
nbcnews.com/tech/security/…


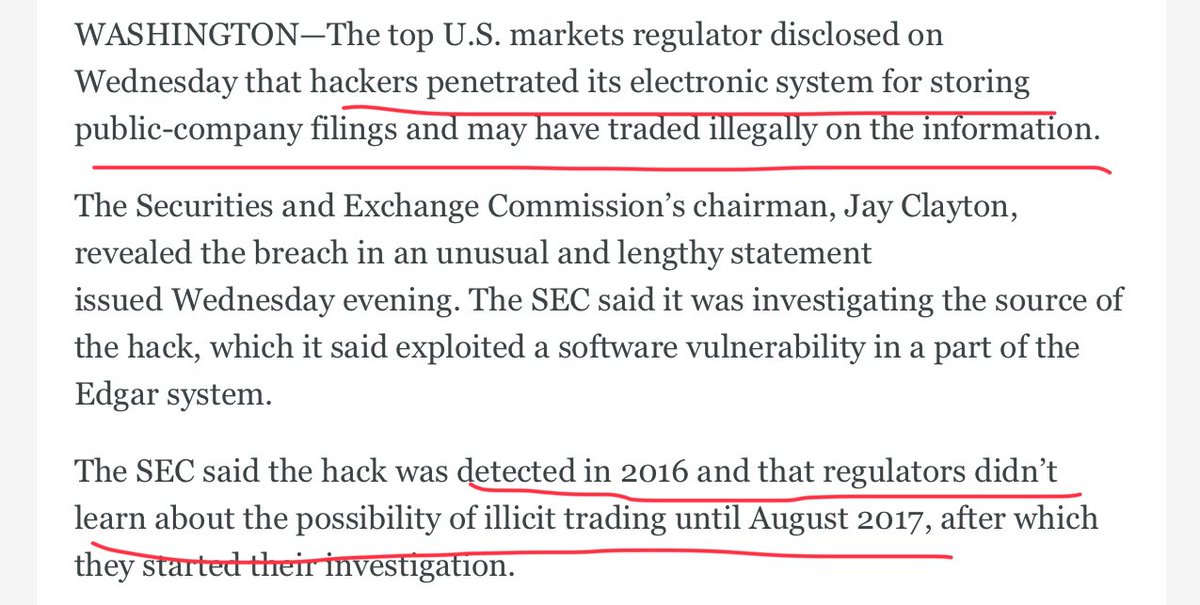
SEC now.
wsj.com/articles/sec-d…
"... start treating data safety with the same seriousness we apply to airplane and automobile safety"
wsj.com/articles/shoul…
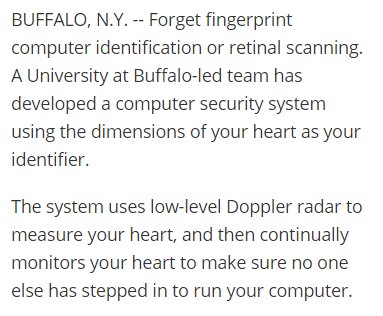
"Getting a heart transplant"
"Why???"
"Some hacker cloned my heart!" 🤦♂️
eurekalert.org/pub_releases/2…
"NotPetya ransomware cost Merck > $310 million"
cyberscoop.com/notpetya-ranso…
wsj.com/articles/surve…
bloomberg.com/news/articles/…

And humans clueless in the middle!
blogs.wsj.com/cio/2017/11/15…
Act 0: Everything becomes a "thing"
Act 1: Starts leaking data.
Ask not if a leaked data point is useful to a bad actor. Ask how.
Ask not if a bad actor will act on a leaked data point. Ask how.
Ask not of the intent. Ask of the outcome. And fix. And iterate. And fix...
🙏🙏🙏
"Cybersecurity Today Is Treated Like Accounting Before Enron"
nytimes.com/2018/01/08/opi…