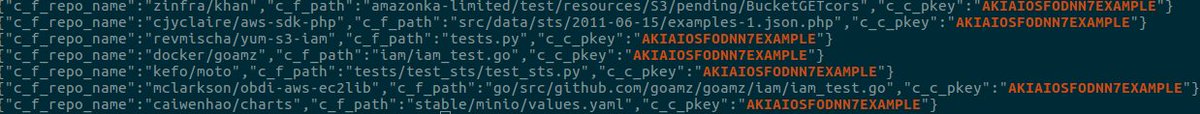
people.eecs.berkeley.edu/~rohanpadhye/f…
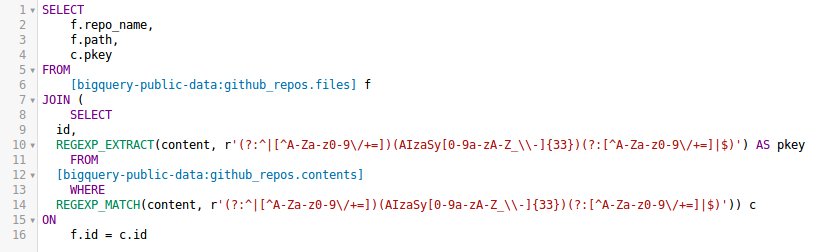
Github can adopt filters during Push time that prevent adding code that matches against known filters. Like, when the user pushes the code, it should run that against known filters. If it does not matches, then only should it succed.
They can use several tools that are available like git-secrets, gitrob, truffleHog etc. Pre-commit hooks are also an interesting choice. github.com/awslabs/git-se… github.com/anshumanbh/git…
All these can prevent such accidental commits.