vice.com/en_us/article/…
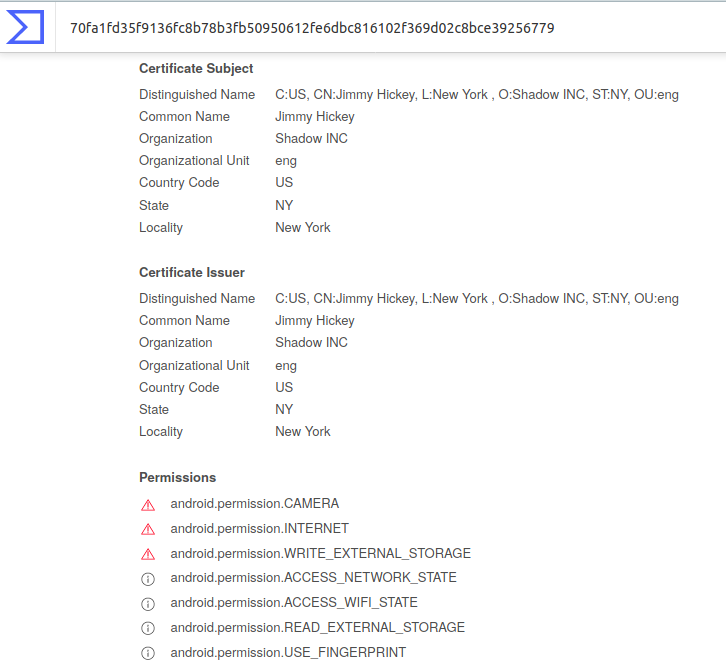
Is this a hardcoded API key/ID? 8/ https://9794bb51044e4aa298d7ce3332dbcea8@sentry.io/179249

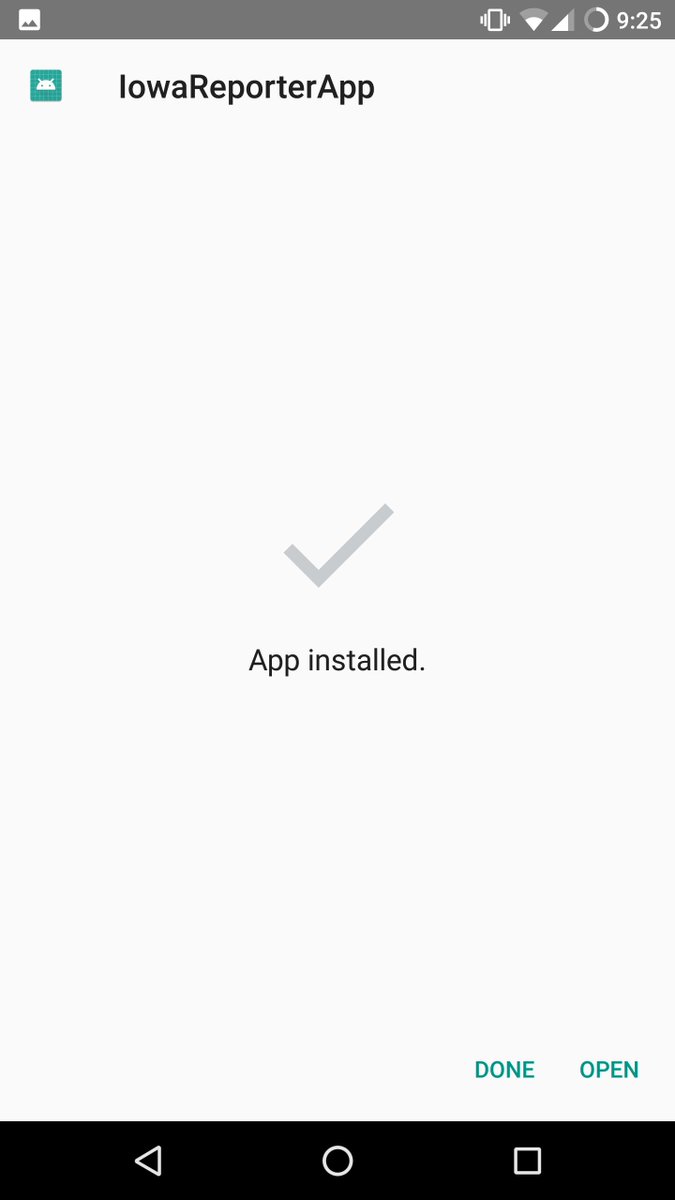
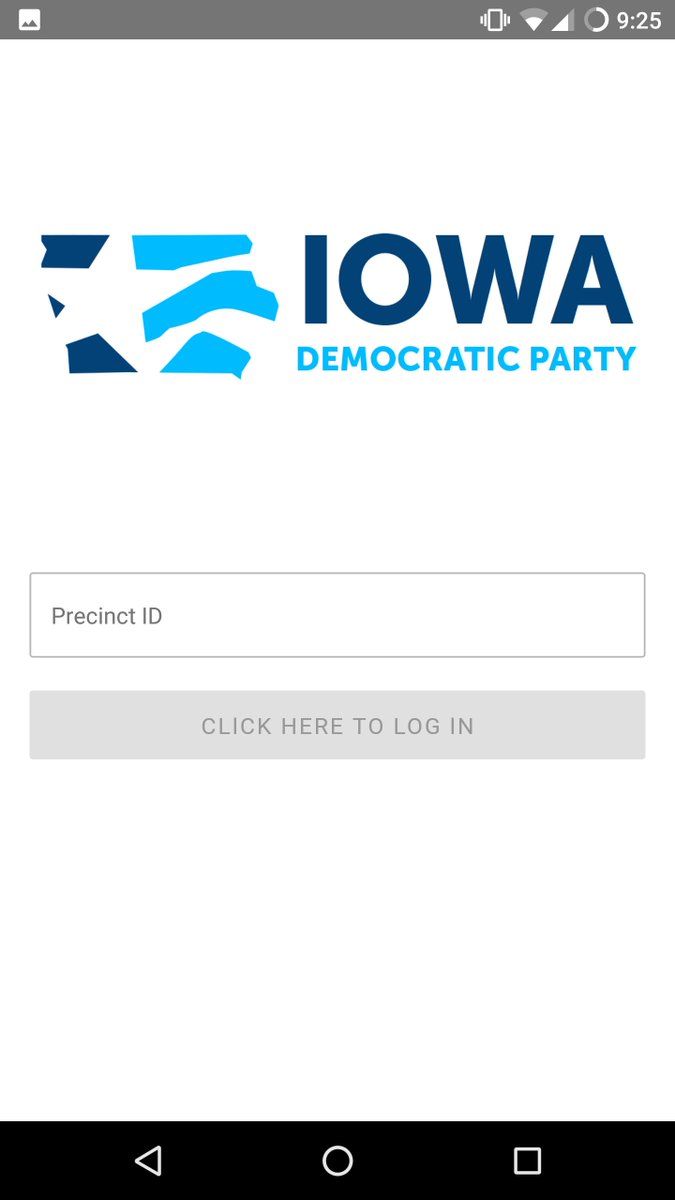
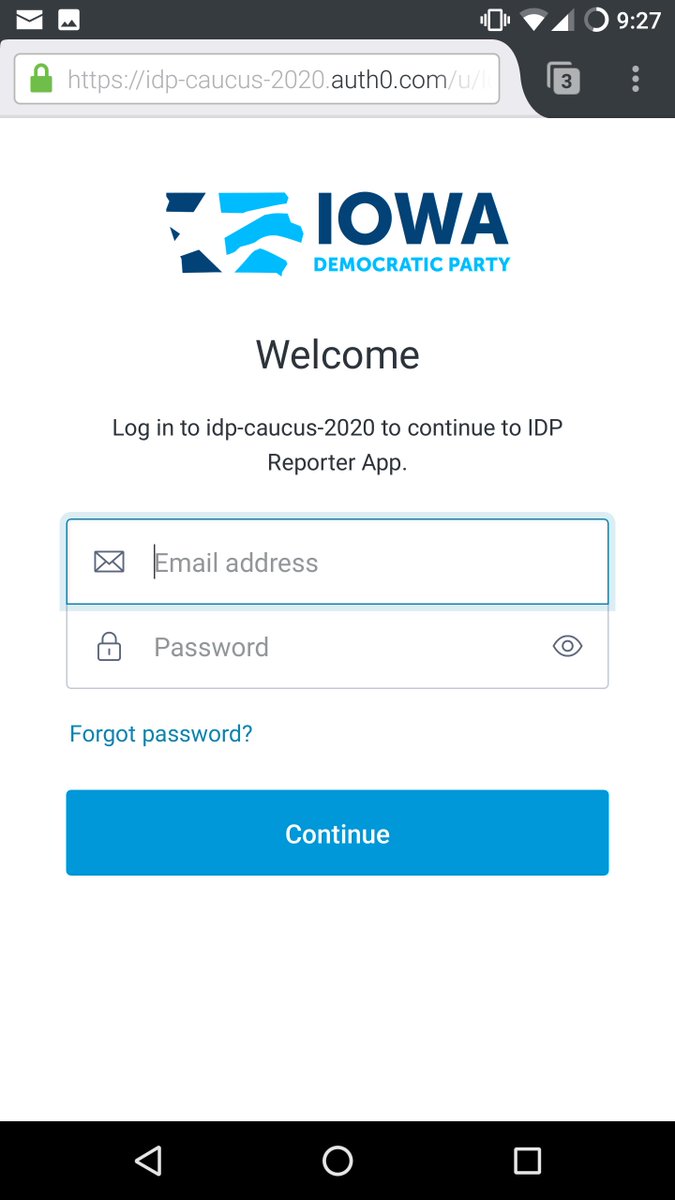
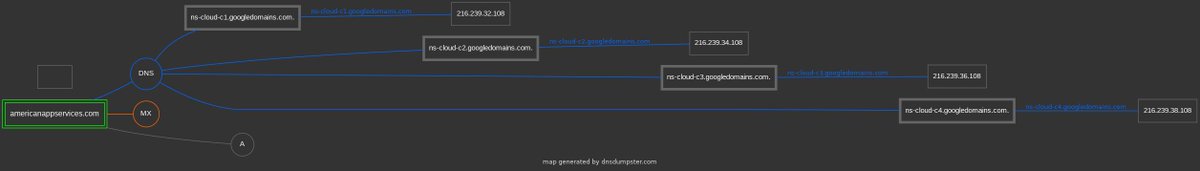
Not sure what this server does yet, but it's on the Google cloud (IDP is Iowa Democratic Party): idp-api.americanappservices.com
This is a Google server with hooks in the app as well:
clients3.google.com 12/
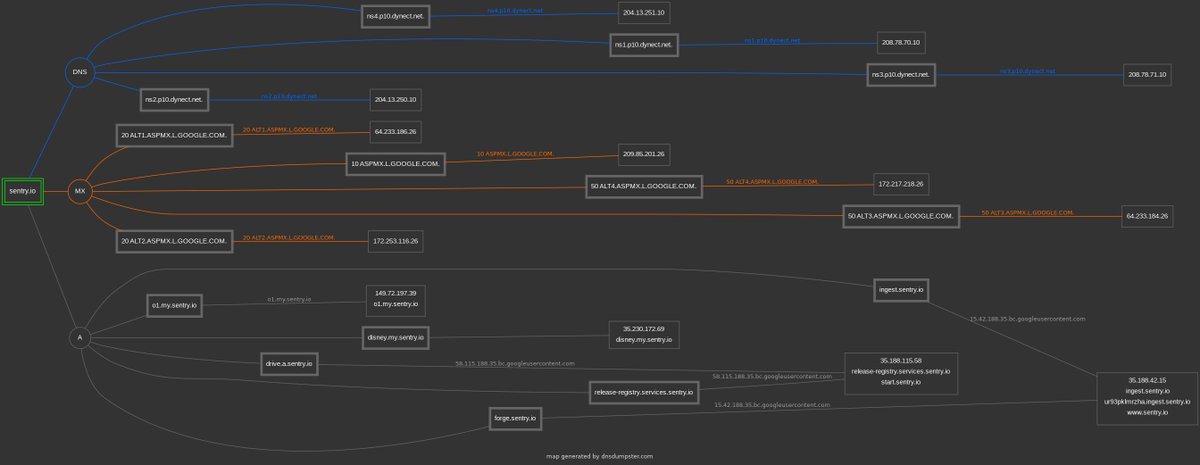
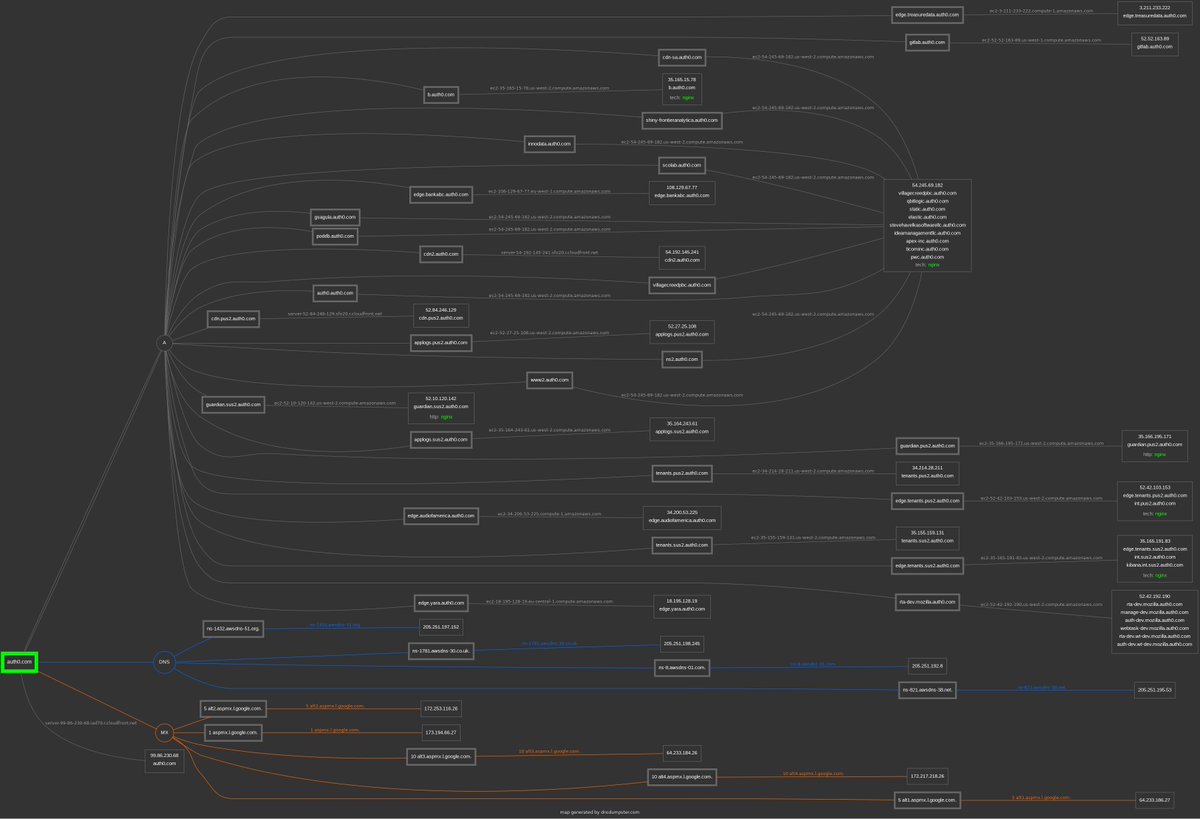
...but seriously, most apps are, esp. under this kind of spotlight. not an excuse and doubly-disturbing given the fact that it supposedly had an independent security audit (or two?) #IowaCaucasDisaster












