#TeamOneFist has confirmed - there are no smart comp scientists in #Russia!
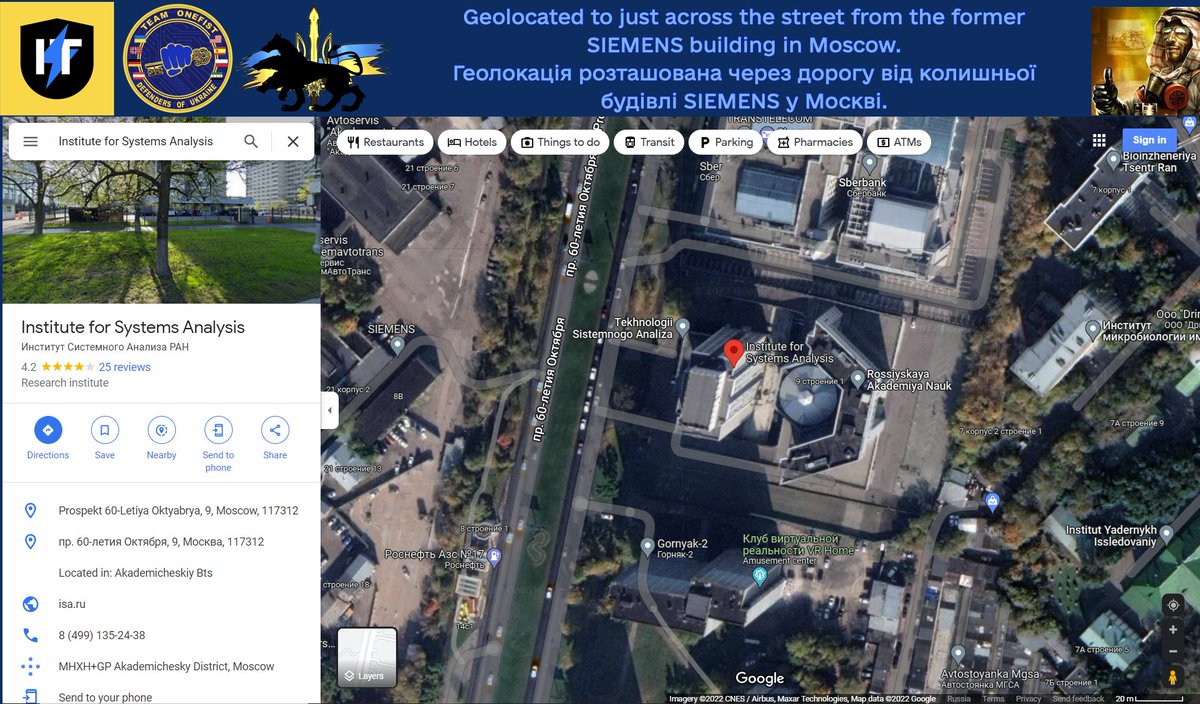
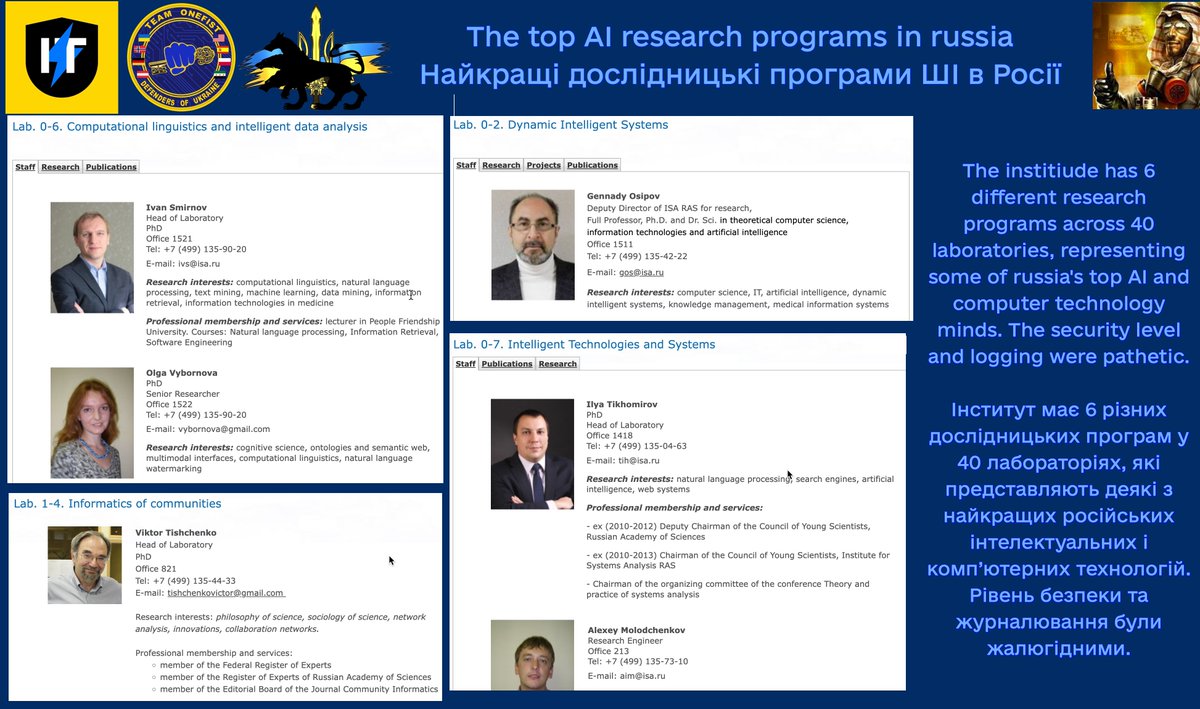
Last night, we conducted a strategic #cyber strike against a top #AI/#compsci institute (ISA RAN), under the Russian Academy of Sciences. Even the president of Russia is a customer of their research. 1/



Last night, we conducted a strategic #cyber strike against a top #AI/#compsci institute (ISA RAN), under the Russian Academy of Sciences. Even the president of Russia is a customer of their research. 1/

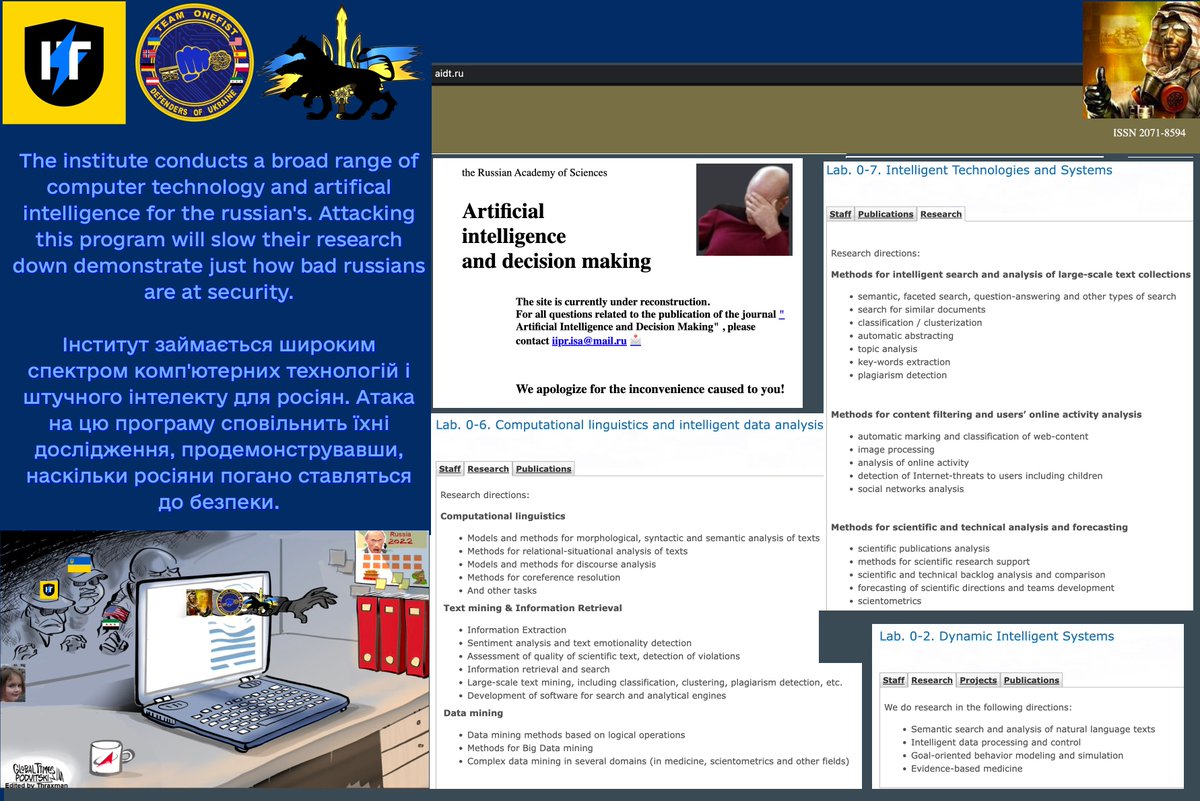
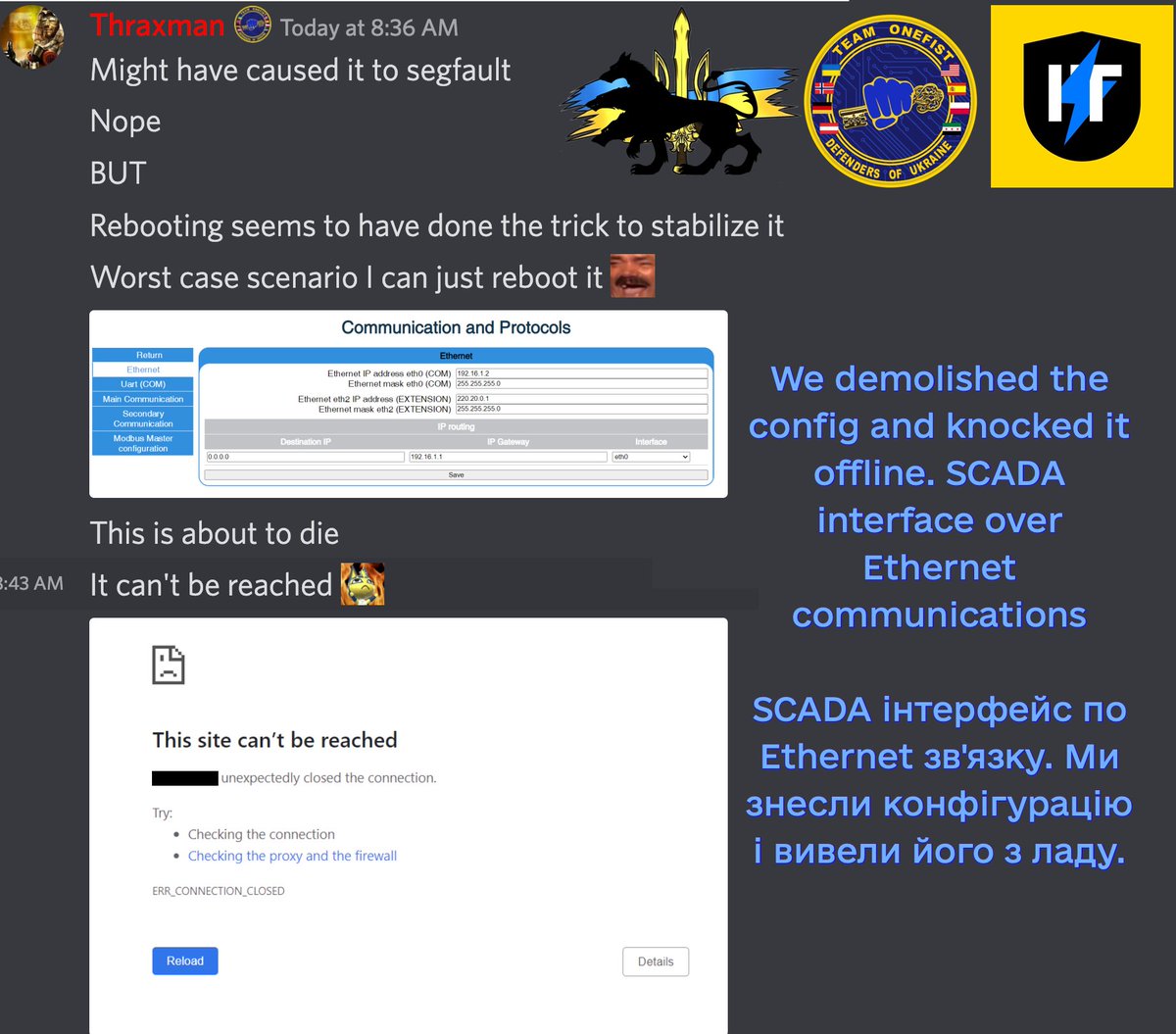
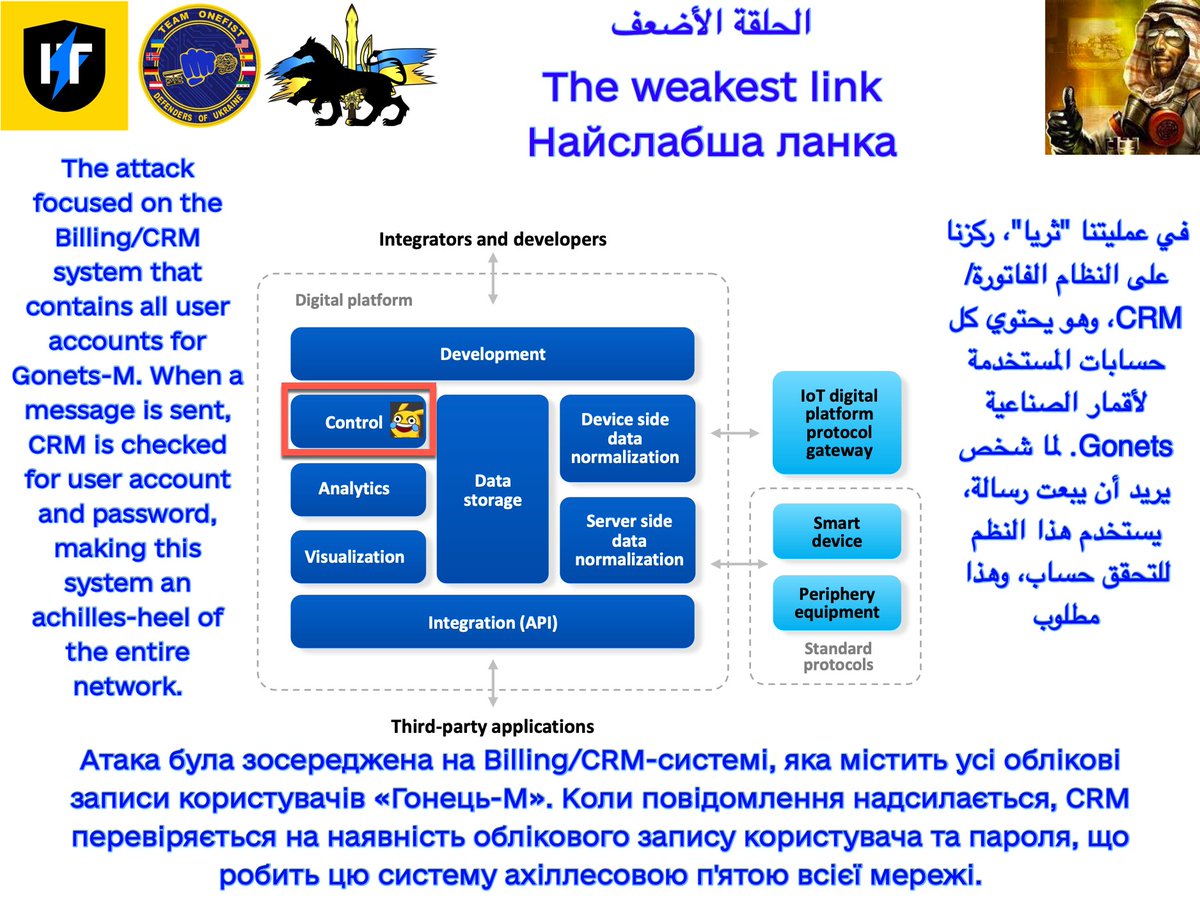
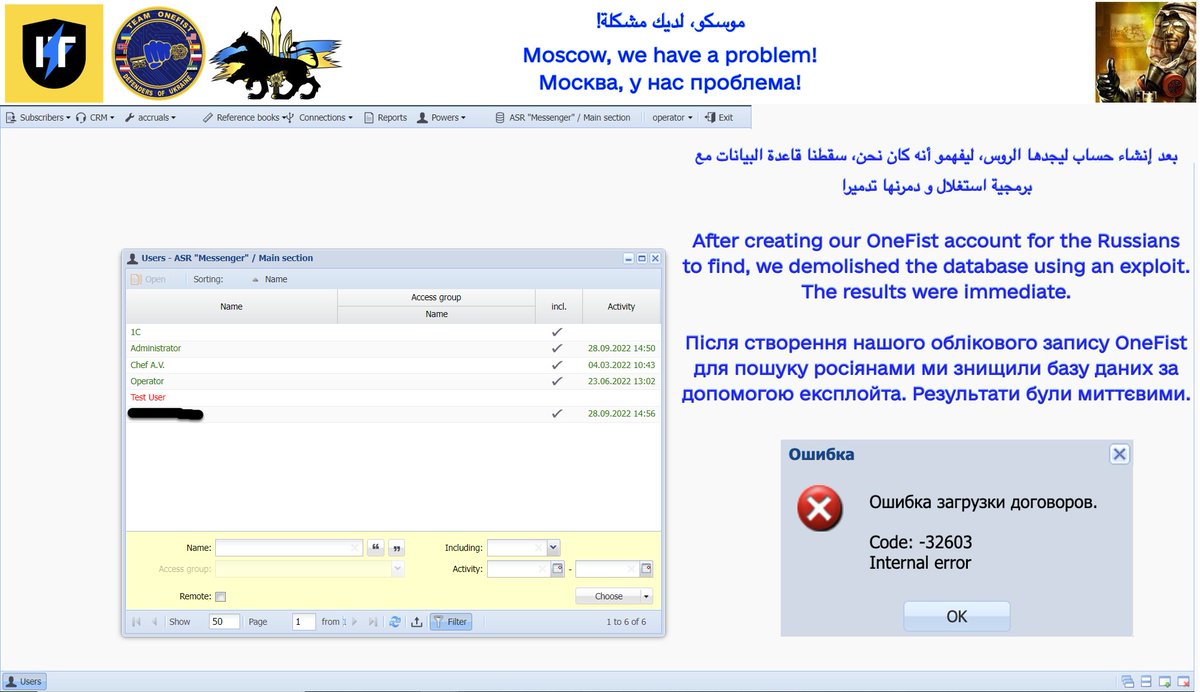
I penetrated this #Cisco switch, which we found to control their entire network: 9 research servers & 100+ devices. All without any #cybersecurity measures! Madness. Bricked it, demolishing their entire research environment; we also gave them a small "gift" from us. 2/ 







They were so arrogant, that they didn't even bother to protect their network. So we gave this famous government institute a perfect reminder, to humble themselves! Опомнись #Россия, за всё ты в ответе!
#SlavaUkraini! #UkraineWillWin, there is no doubt 🇺🇦☢️👊
#Ukraine️ #infosec

#SlavaUkraini! #UkraineWillWin, there is no doubt 🇺🇦☢️👊
#Ukraine️ #infosec


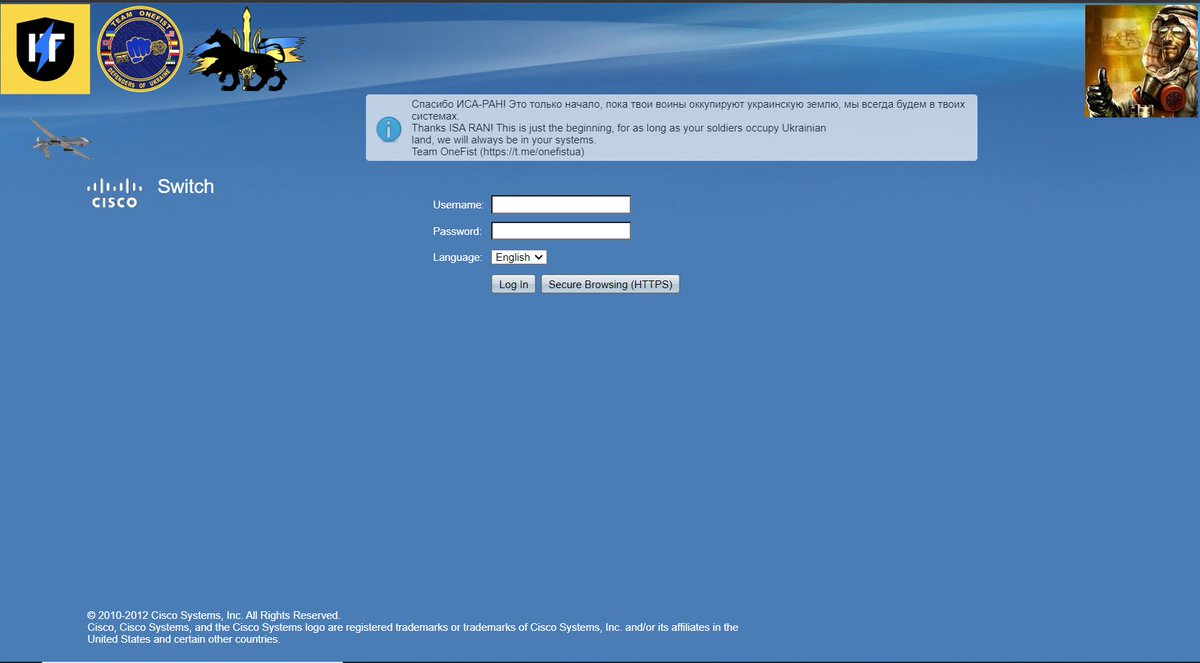
Remember this #Cisco switch? ISA-RAN brought their data center back after a few days, along with the #TeamOneFist message...and a way for me to get back inside.
Well, they were warned about what would happen😁🇺🇦☢️👊
#SlavaUkraini! #Ukraine #UkraineRussiaWar️ #cybersercurity

Well, they were warned about what would happen😁🇺🇦☢️👊
#SlavaUkraini! #Ukraine #UkraineRussiaWar️ #cybersercurity

• • •
Missing some Tweet in this thread? You can try to
force a refresh