If #Russia takes power from #Ukraine, #TeamOneFist will respond!
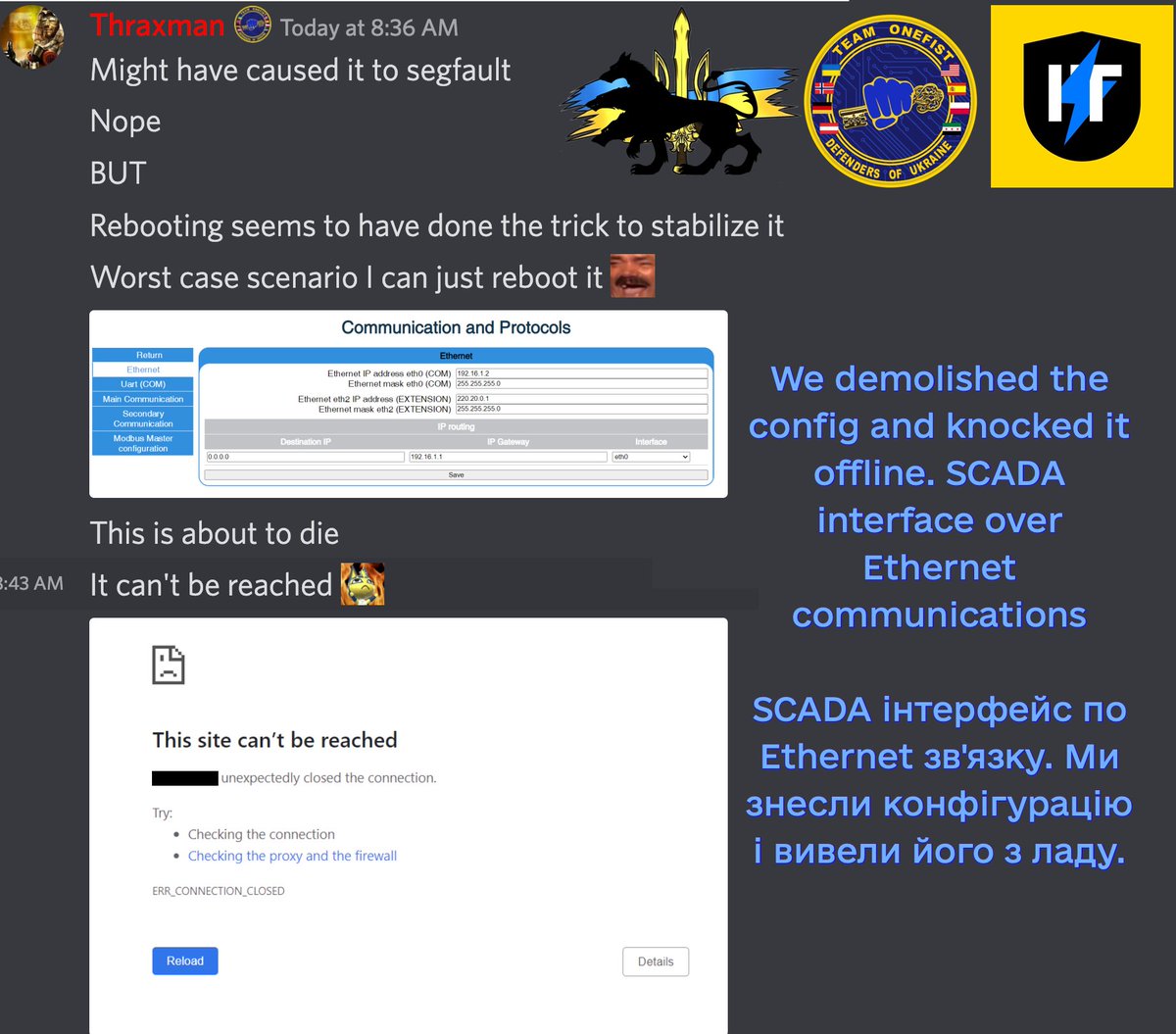
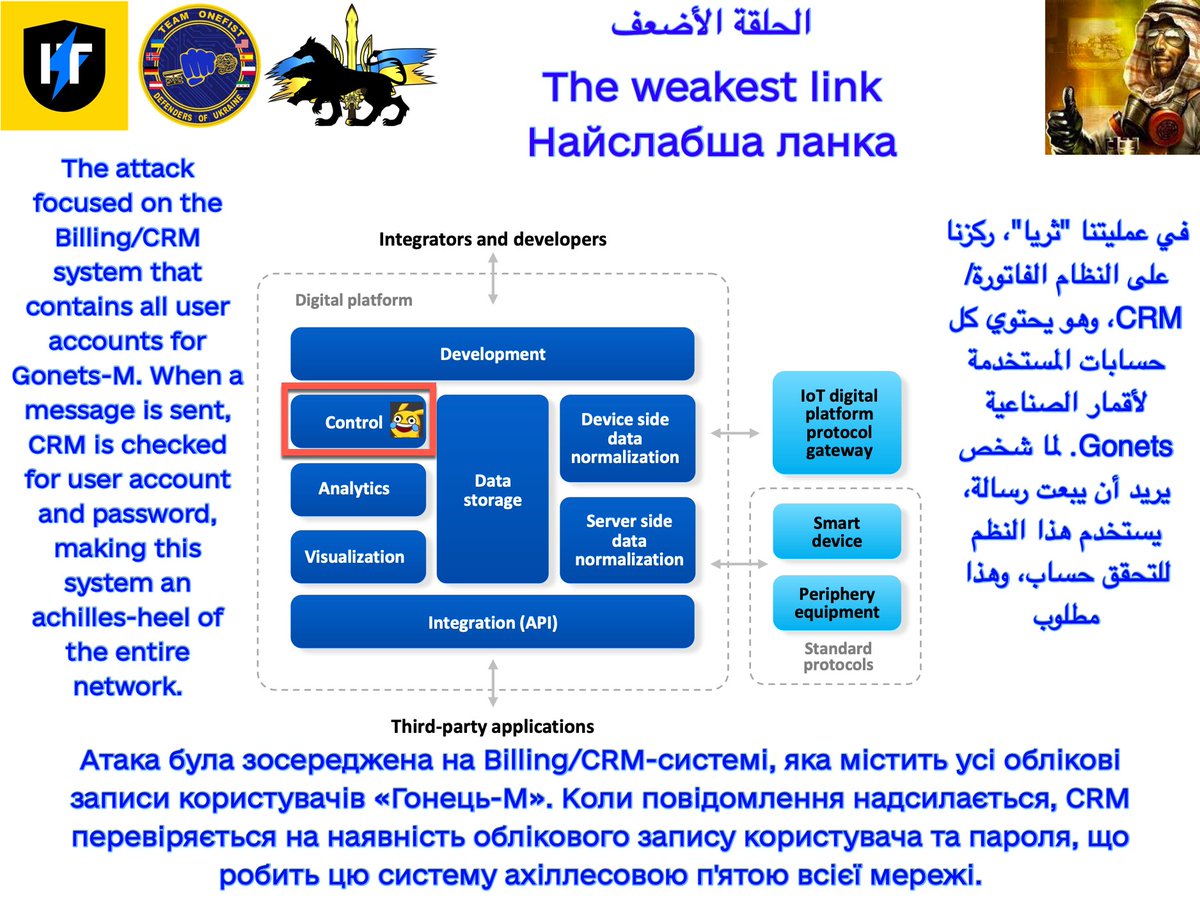
Op.Gradient: a #cyber strike against a #hydroelectric plant's construction site. Their sensor #SCADA network and #GNSS base station were successfully penetrated, which monitored ground/foundation stability. 1/4



Op.Gradient: a #cyber strike against a #hydroelectric plant's construction site. Their sensor #SCADA network and #GNSS base station were successfully penetrated, which monitored ground/foundation stability. 1/4




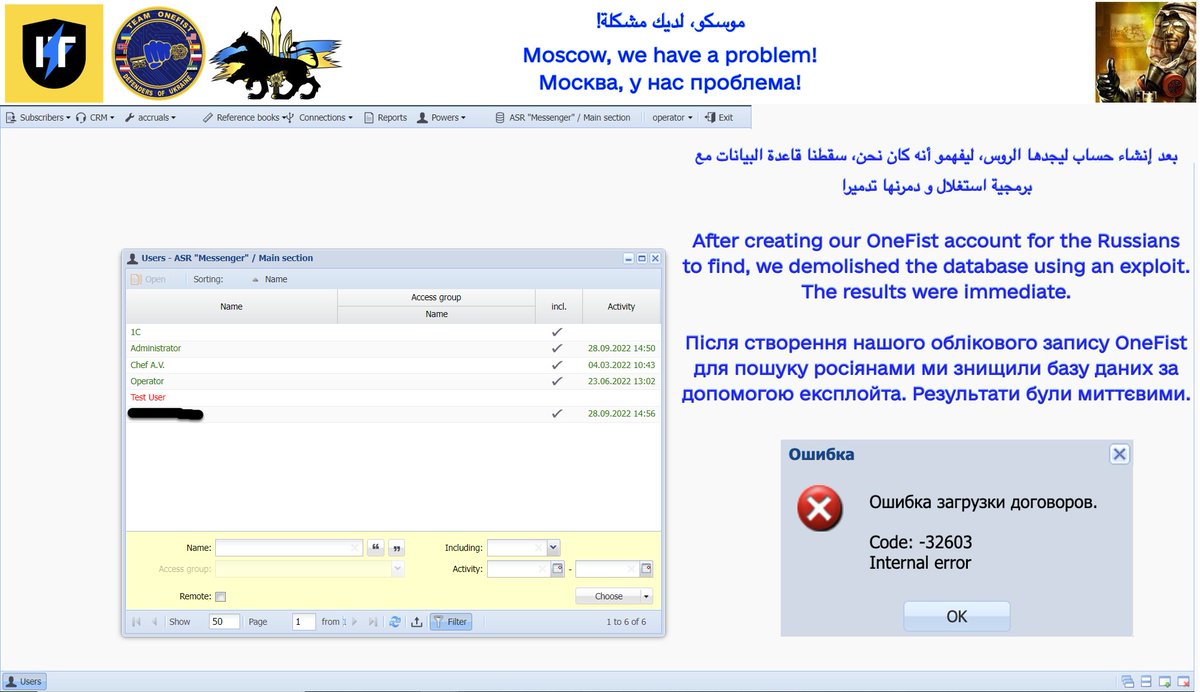
Over the course of a week, I gradually introduced circular error into the GNSS readings, reducing it's accuracy to disrupt their work. At the end of it, both the sensor network and the base station were demolished, to prevent them from fixing the damage caused. 2/4 







(3/4)
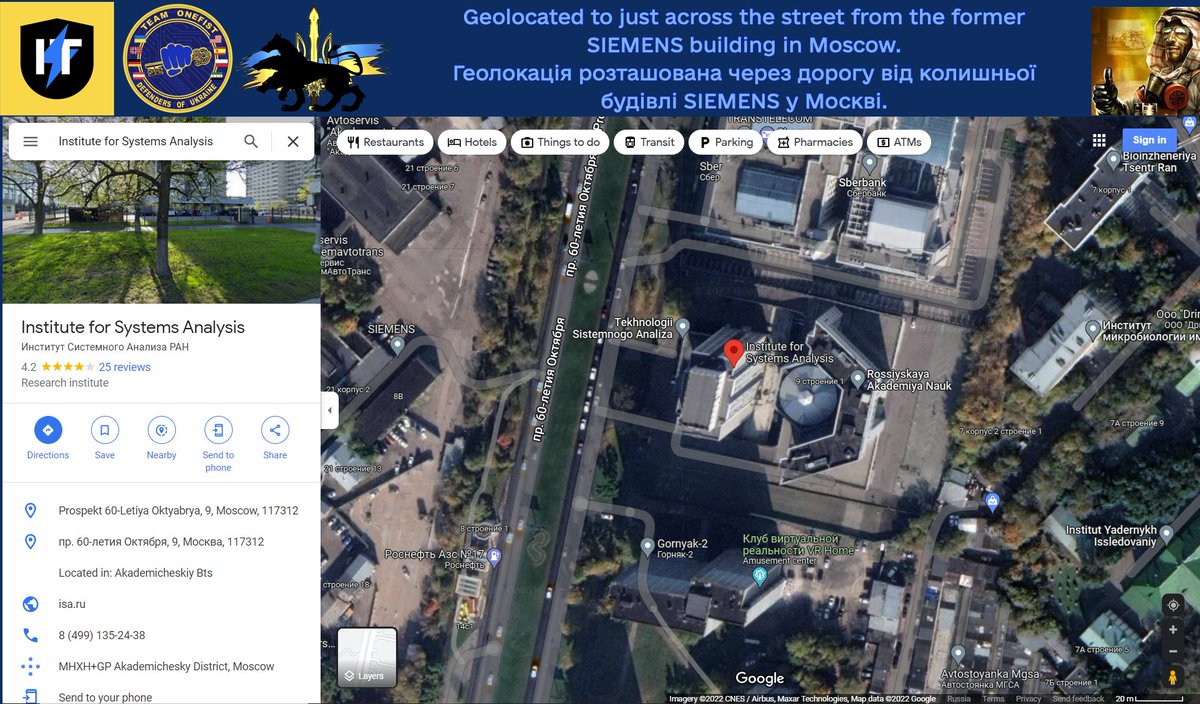
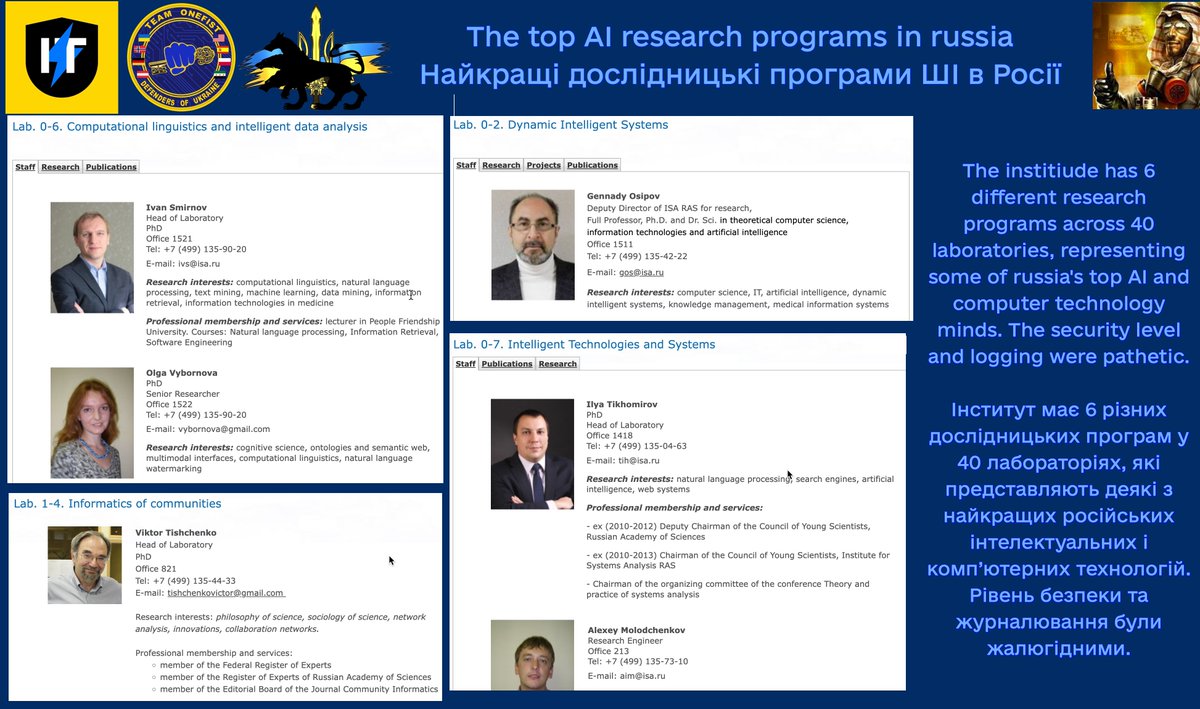
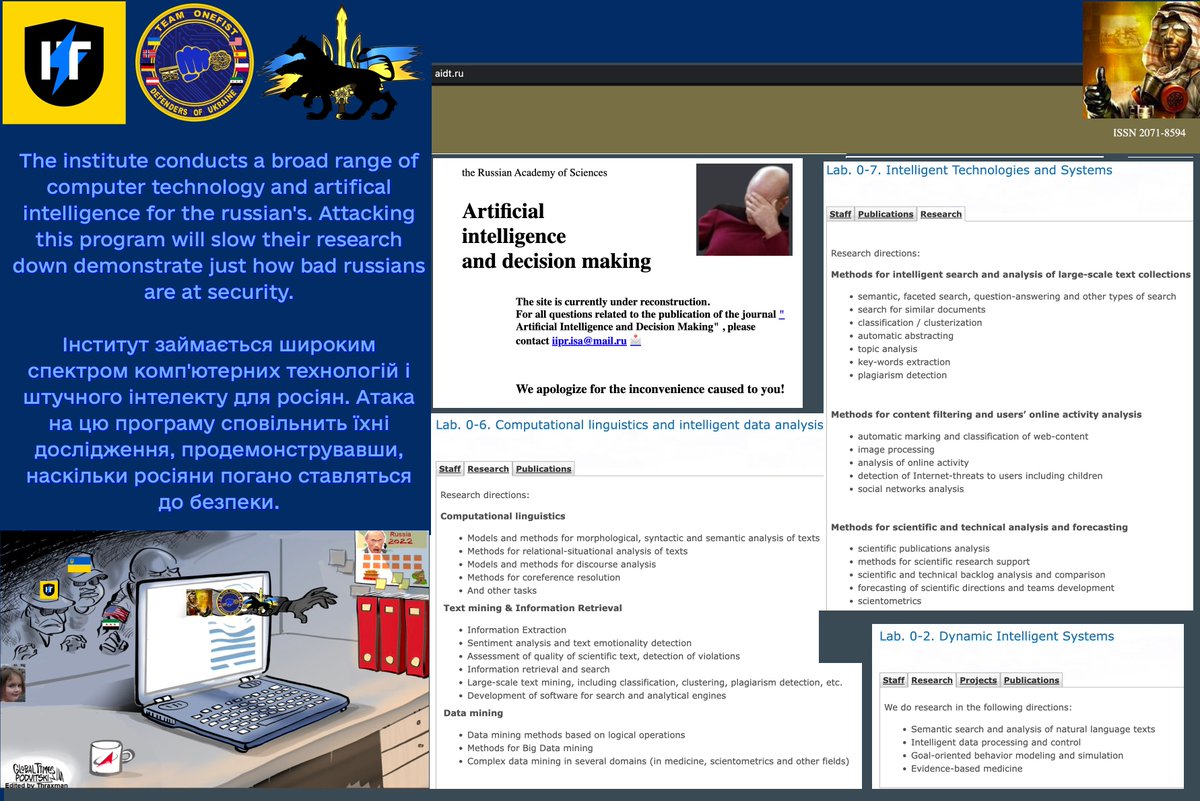
By the way, this site has been flooded from erosion in the past. This network is vital for RusHydro to ensure that construction is safe, and is following the approved plan. All with Western made @LeicaGeosystems and @MoxaInc devices. Hopefully, this will happen again:
By the way, this site has been flooded from erosion in the past. This network is vital for RusHydro to ensure that construction is safe, and is following the approved plan. All with Western made @LeicaGeosystems and @MoxaInc devices. Hopefully, this will happen again:

Unlike the #Russians, our attacks do not harm people. #UkraineWillWin and until then, no Russian #grid nor device is safe from us. #SlavaUkraini! 🇺🇦☢️👊4/4
#UkraineWar #cybersecurity #infosec #cyberwarfare
(Special thanks to @SpoogemanGhost for introducing my backstory earlier✊)

#UkraineWar #cybersecurity #infosec #cyberwarfare
(Special thanks to @SpoogemanGhost for introducing my backstory earlier✊)

• • •
Missing some Tweet in this thread? You can try to
force a refresh