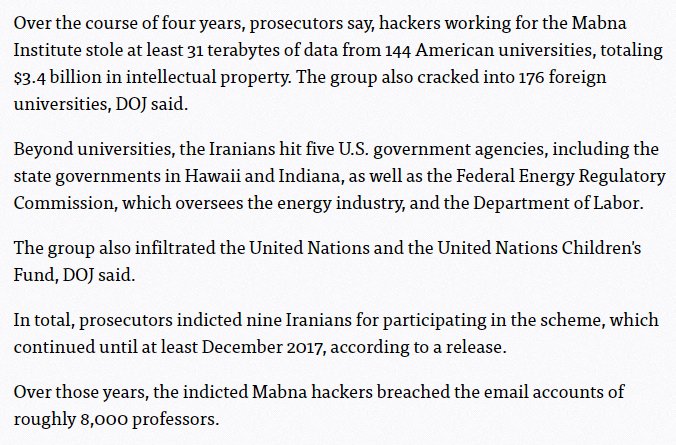
Hackers stole >31.5 terabytes of data from 144 U.S. universities, 176 foreign universities, the UN, and five US govt agencies.
DAG Rosenstein announcing now: justice.gov/live

No dollar figure for the IP stolen from foreign universities.
Rosenstein: “This administration is in its second year, and we are doing quite a lot. … You don’t see the attacks that have been deterred.”
U.S. busts 'massive' Iranian hacking scheme: politico.com/story/2018/03/…
They'd link to a purported article on the same topic.
The idea was to make professors think they'd accidentally logged out of their email, so they'd enter their credentials.

Here are general descriptions of the American company victims.

Sometimes they set up auto forwarding so new emails would also go to accounts they controlled.