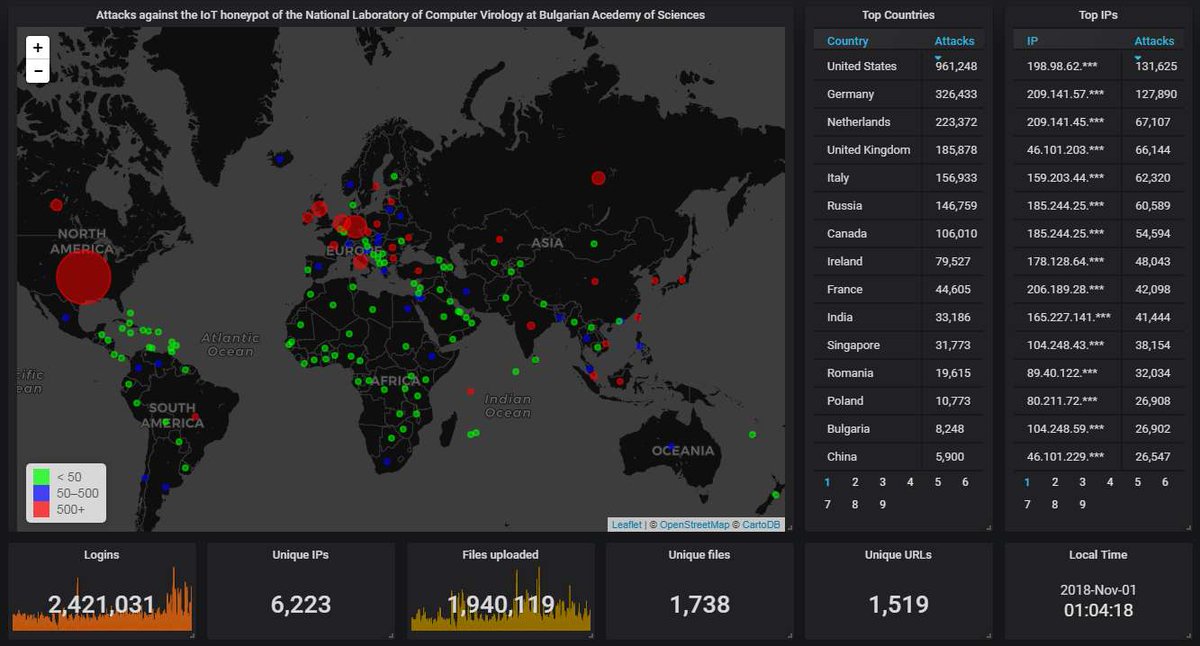
Suddenly, all their visitors are forced to mine crypto currencies in their browsers, which tends to be a tad annoying for them.
Sysadmin doesn't give us full access to their system because "security". We're given access only to the webroot folder.
Somebody has installed a web shell. Whoever could enter through that web shell has wider access to the system than is given to us for investigating it.
He goes ballistic too. "Hey, I just design web sites! I know how to use this software, so I have this software installed. It's not my job to fix security problems in it!"
The issue is that someone has probably compromised the bulk of their passwords (many but not all) and might still have God knows what installed on their system.
"If you run the bad guy's program on your computer, that's no longer your computer."
End of story.