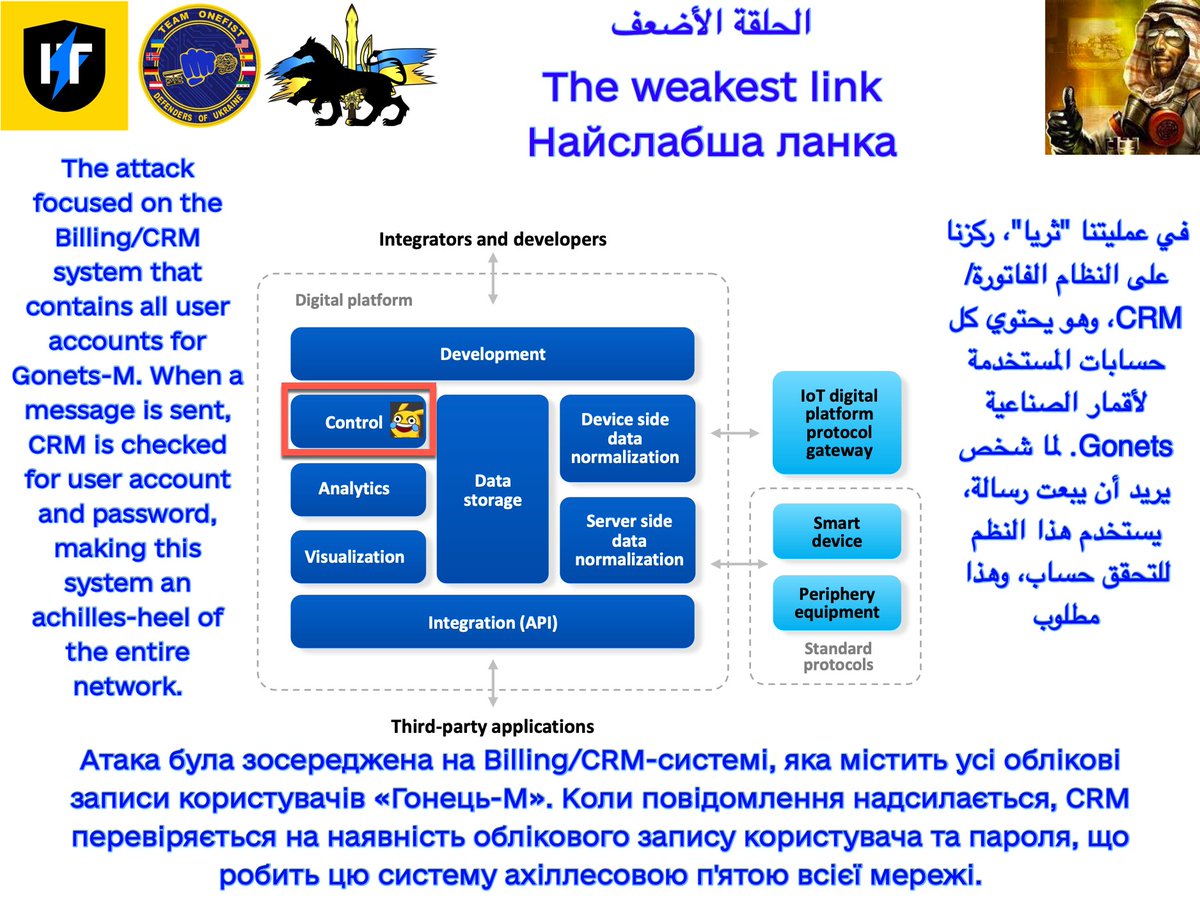
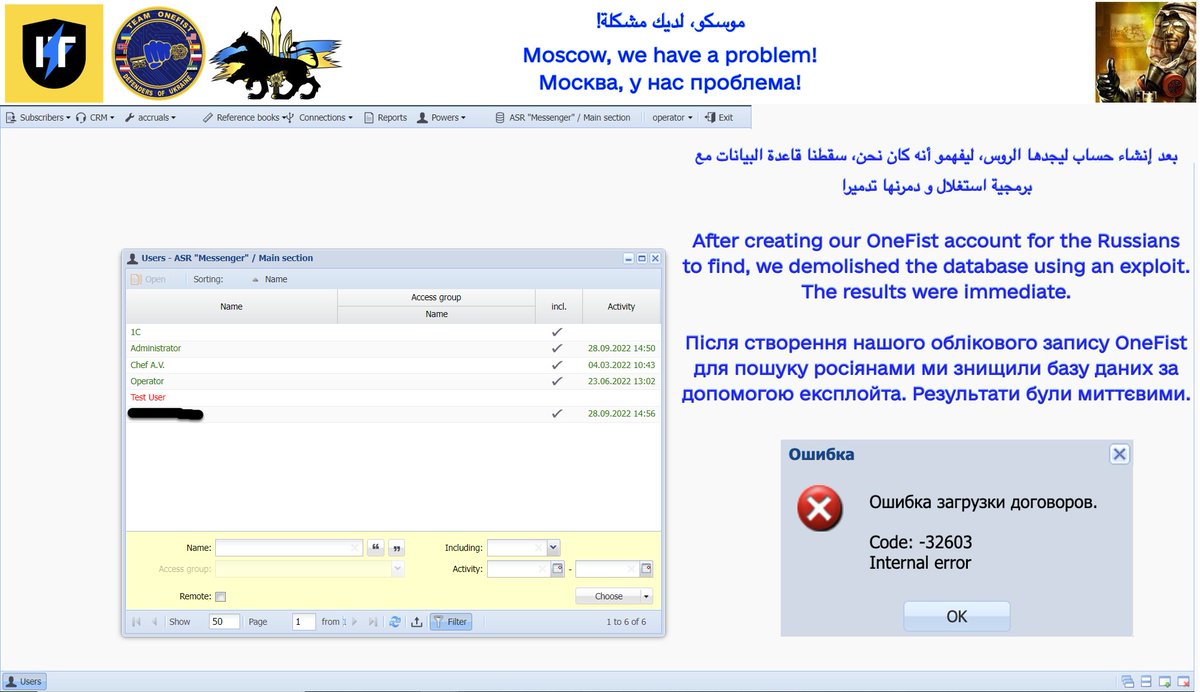
A very special present from #TeamOneFist: Op.Switchblade, one of our largest #DataCenter attacks yet!
We hunted down every #networking #switch we could find in #Russia and tested them for vulns. From these, we conducted a #cyber strike against 55 strategically valuable devices 1/



We hunted down every #networking #switch we could find in #Russia and tested them for vulns. From these, we conducted a #cyber strike against 55 strategically valuable devices 1/




We penetrated devices both large and small; many of them were at the heart of #ISP DCs like Rostelecom or Kuban-Telecom, but many also belonged to individual businesses. All had high utilization rates, uptime, and were rich in features: these were all core infrastructure 2/ 







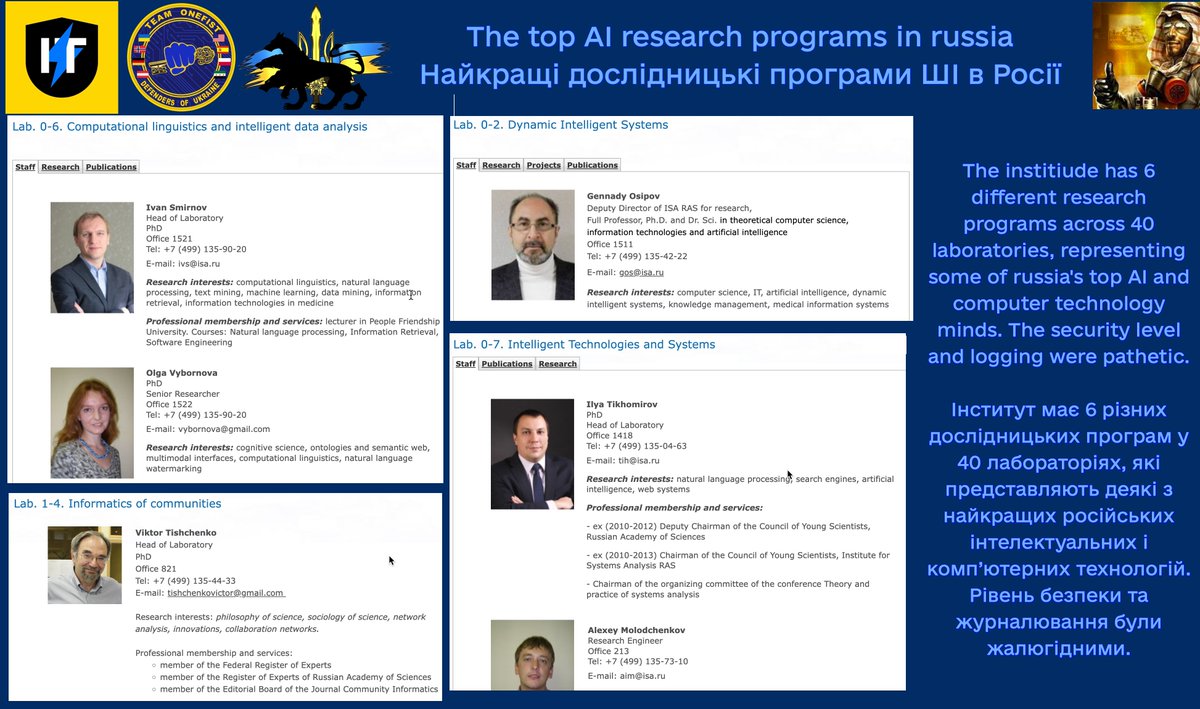
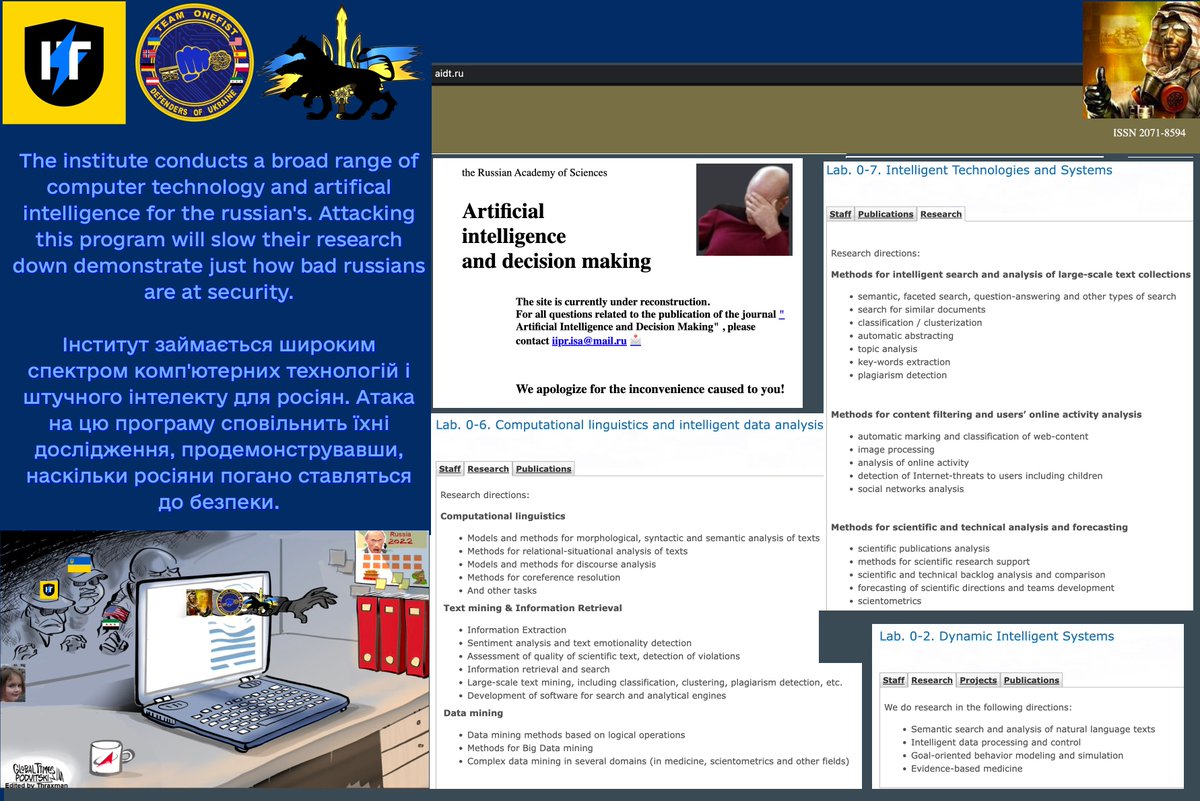
These included #Russian, #Chinese, and #Western boxes like #Cisco and #HP!
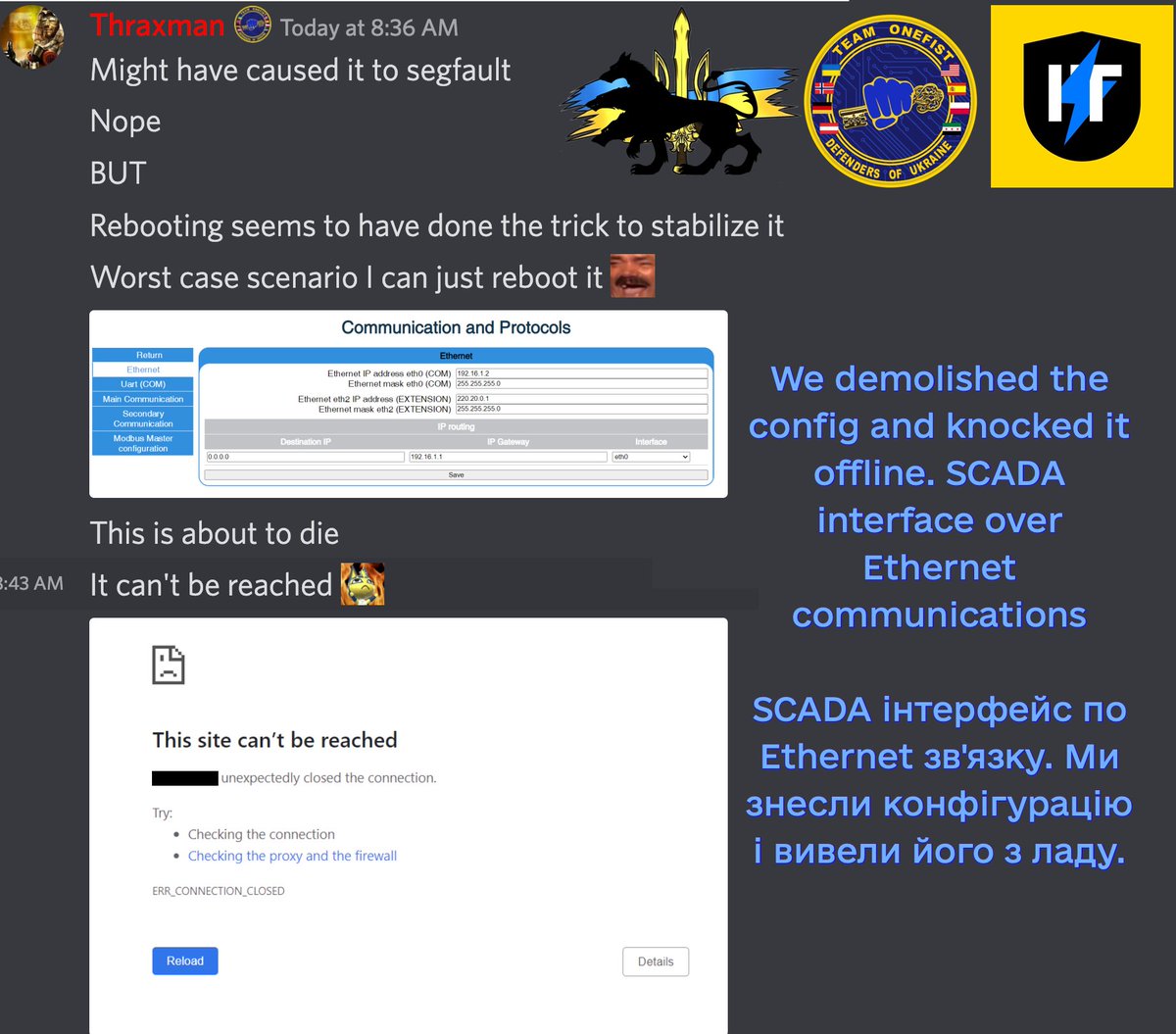
We swiftly demolished them, before any of the sysadmins could react or notice us. After the initial strike, we kept reattacking if they were recovered (>8 times!). No uninterrupted service for them! 3/



We swiftly demolished them, before any of the sysadmins could react or notice us. After the initial strike, we kept reattacking if they were recovered (>8 times!). No uninterrupted service for them! 3/




Another op, another victory for #Ukraine. The most interesting targets we hit are:
-SPZhT (#railway #logistics)
-SK Vostok (Tyumen #power company)
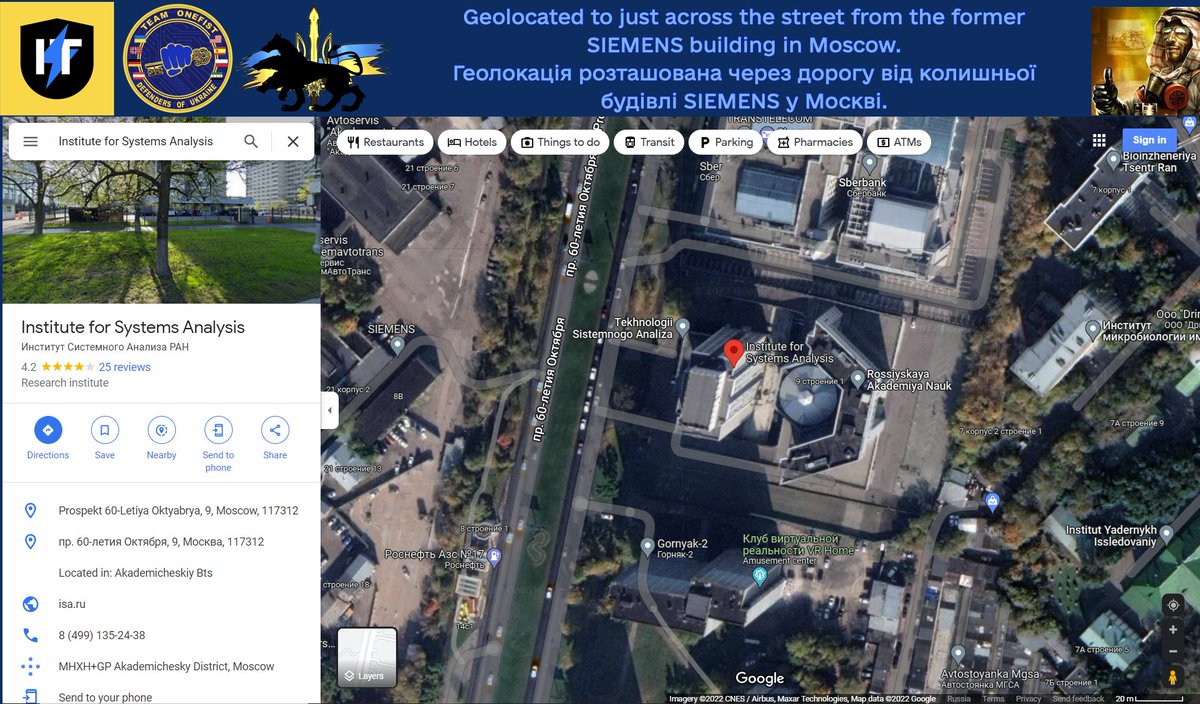
-Rostelecom DC in #Moscow
-An entire business comms network in #Sochi
#SlavaUkraini! #UkraineWillWin 🇺🇦☢️👊
#cybersecurity #infosec



-SPZhT (#railway #logistics)
-SK Vostok (Tyumen #power company)
-Rostelecom DC in #Moscow
-An entire business comms network in #Sochi
#SlavaUkraini! #UkraineWillWin 🇺🇦☢️👊
#cybersecurity #infosec




• • •
Missing some Tweet in this thread? You can try to
force a refresh