nytimes.com/2020/02/13/us/…
This found serious issues, but they're just some of the many problems with @Voatz. 1/
Their fear is well justified. In October, Voatz reported a student at U of Michigan to authorities for analyzing their app: 2/
magazine.cointelegraph.com/2020/02/07/saf…
blog.voatz.com/?p=1209

But instead of extending any benefit of the doubt, Voatz reported the student and changed their scope text: 5/
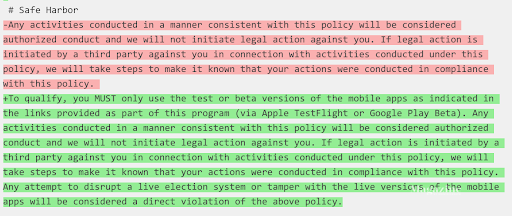
Even given a scope, people will still accidentally tread outside the lines. Election officials and voting companies need to work collaboratively with researchers to be successful. 6/
cyber.dhs.gov/bod/20-01/
It's a genuinely great directive, and accurately captures modern norms in vuln disclosure. 7/
This is right, and what we should be bringing to election systems. 8/
Given how they handled the U of M student, how they responded to the MIT research today, their discomfort with basic transparency, and their reliance on security-through-obscurity -- Voatz should not be trusted to run US elections.
internetpolicy.mit.edu/faq-on-the-sec…
Just to be clear: that is super wrong.
blog.voatz.com/?p=1243
I'm also quoted, noting that Voatz' public bounty doesn't allow the public to research their back-end server the way Voatz claims:
cnn.com/2020/02/14/pol…
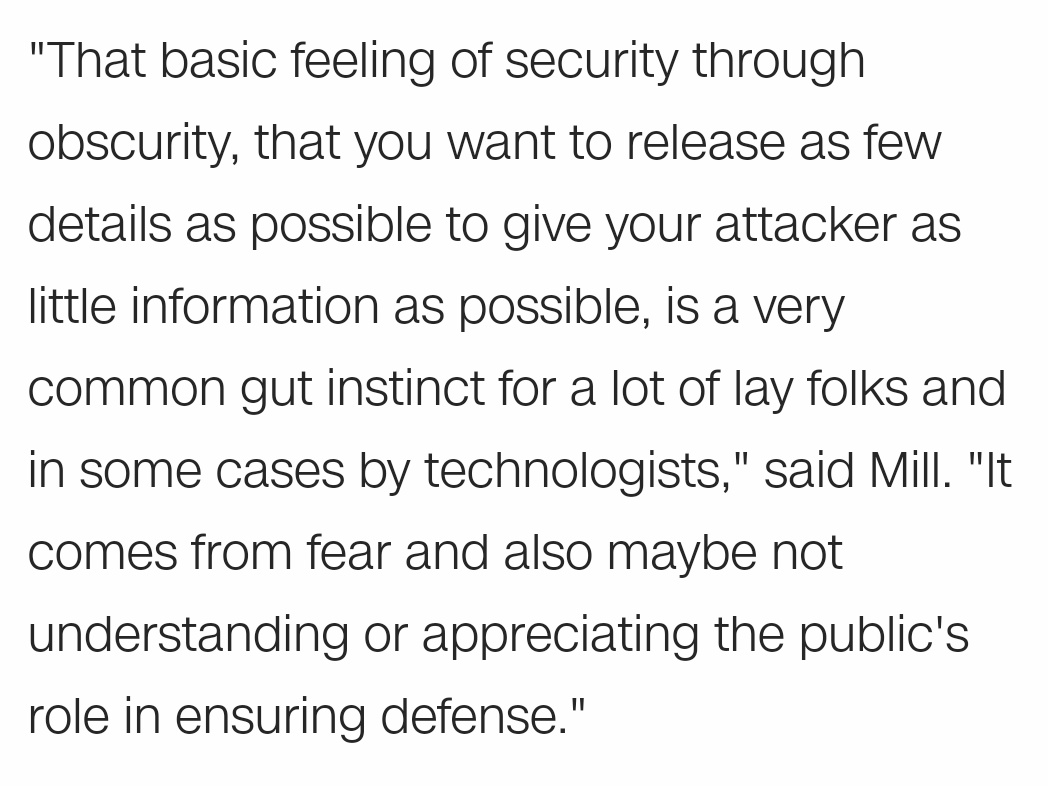
"Security through obscurity" can be tempting, but real security means not being afraid to let the public verify your work.
cnn.com/2020/02/14/pol…

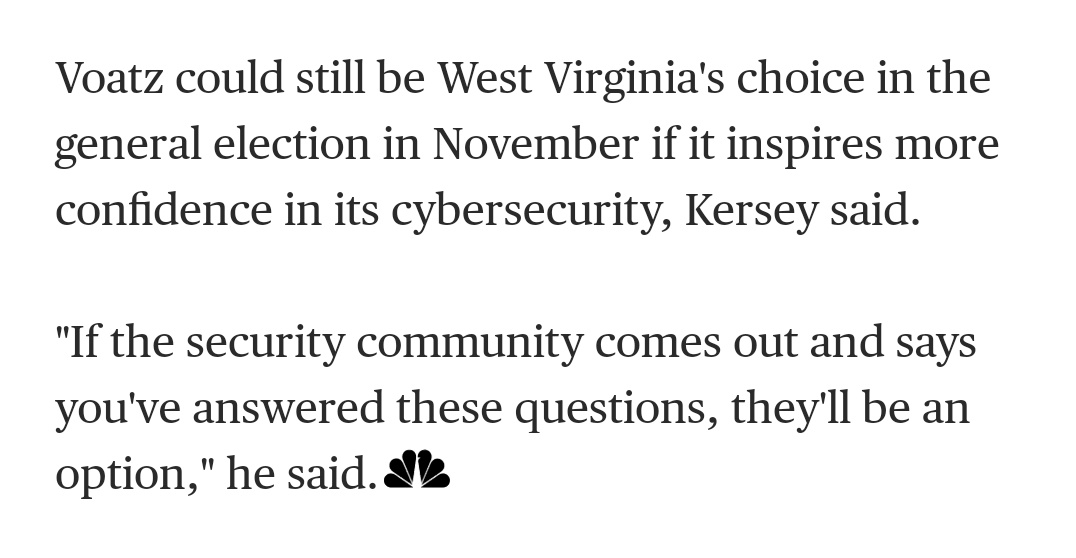
They'll use Democracy Live instead, where ballots can be marked on- or offline, then printed and mailed:
nbcnews.com/news/amp/ncna1…
Two weeks ago, Voatz responded to valid security issues by inaccurately dismissing their impact, and publicly accusing the researchers of wanting to deliberately disrupt elections.
blog.voatz.com/?p=1209

But instead of offering an olive branch, they hand-wave at being "critical infrastructure" to falsely imply they have no discretion in reporting researchers who examine their live systems:
hackerone.com/voatz/policy_v…
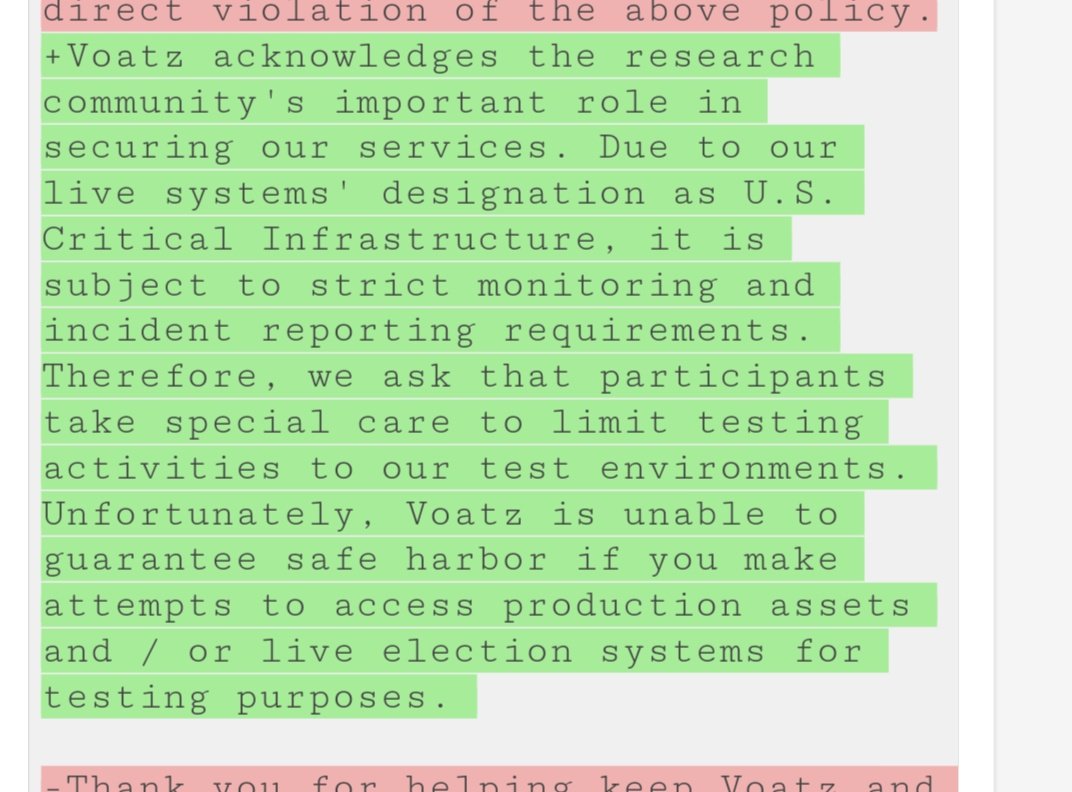
In the meantime, if you find a bug in Voatz' systems, I encourage you to report it right to CISA, since reporting it to Voatz directly is unsafe.
There's no public indication of why, but it's good that it's closed. Given how Voatz treated security researchers, H1 was hosting a space that was unsafe for the public to engage with.