Suspected source: Russian intelligence.
@DFRLab has been investigating. Top takeaways here.
medium.com/dfrlab/top-tak…
The full report on #SecondaryInfektion is online here: digitalsherlocks.org/ourwork
When we dug into it, we realised the assets on FB were the tip of the iceberg.
newsroom.fb.com/news/2019/05/m…
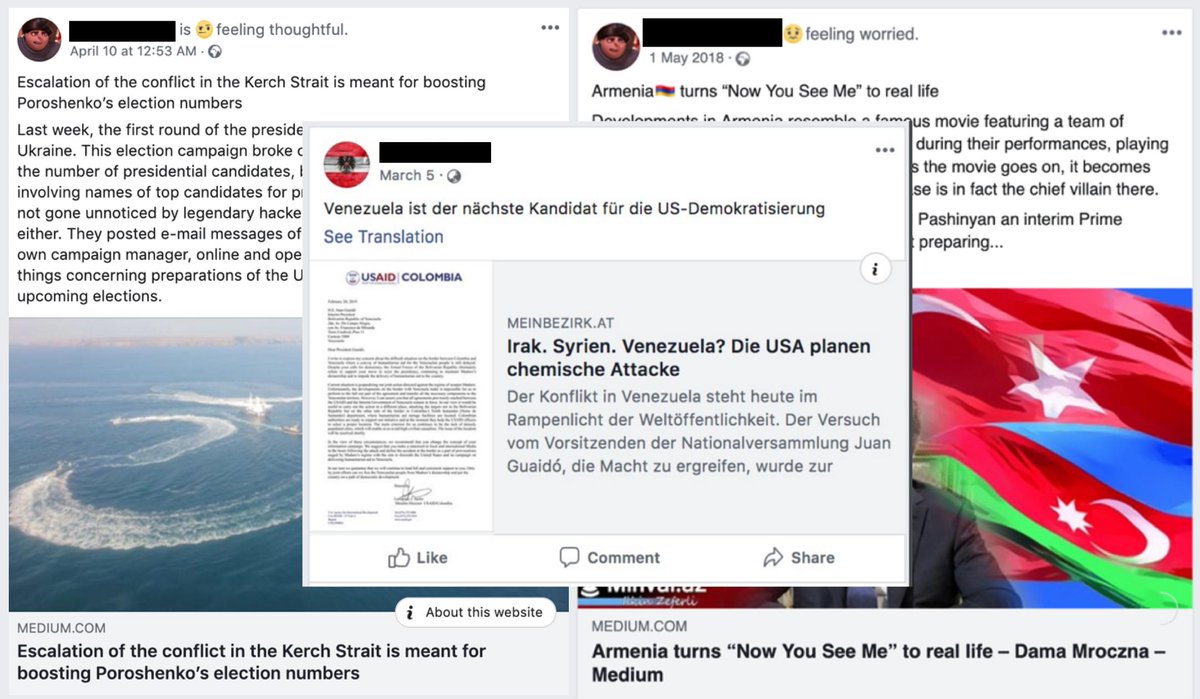
The content the operation posted there often focused on Russian geopolitical concerns.
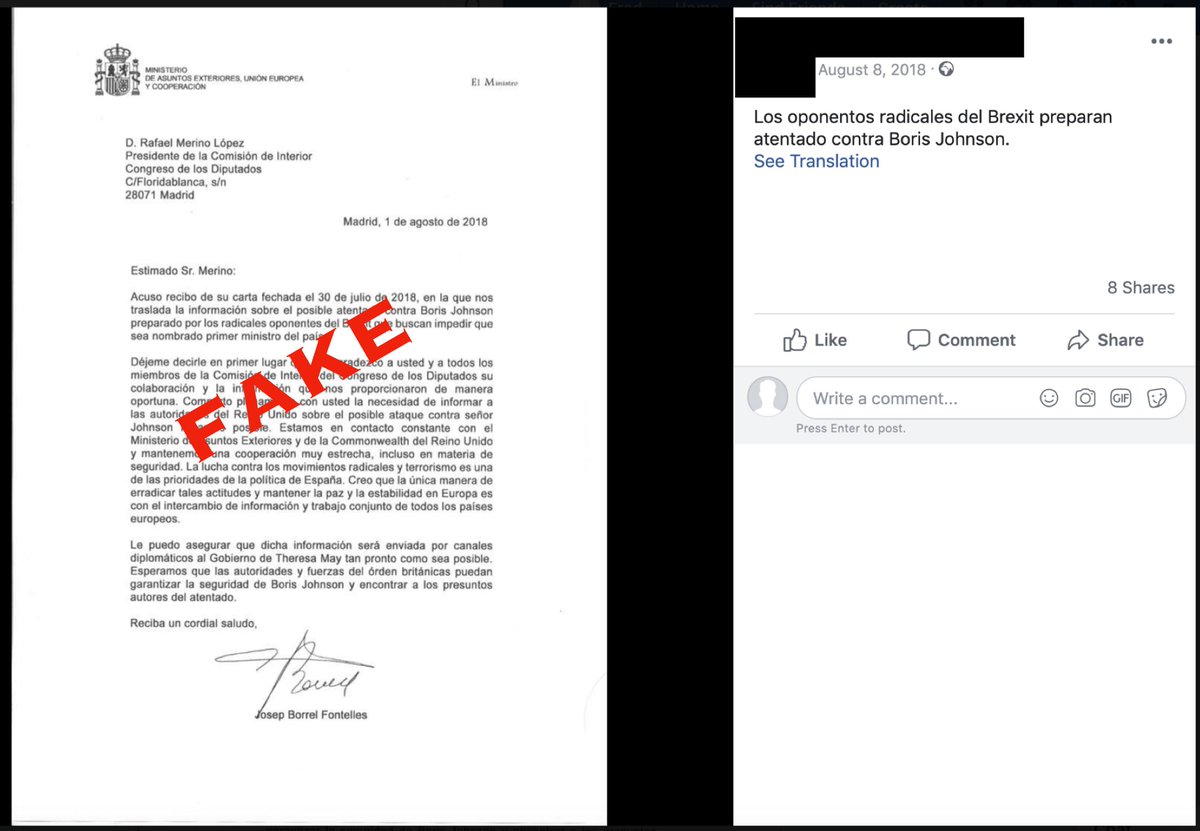
@DFRLab checked with the EC. The letter's a fake.

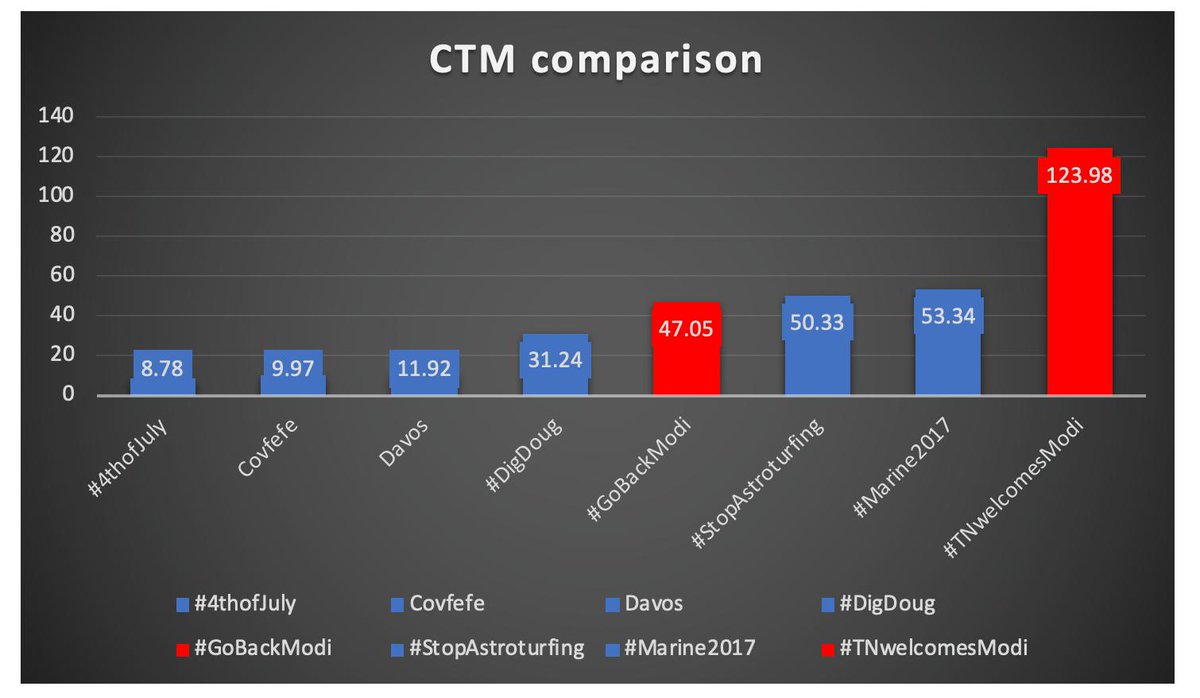
#SecondaryInfektion prioritised security over clicks. Great way of staying hidden, but I've never seen so little bang for so much buck.
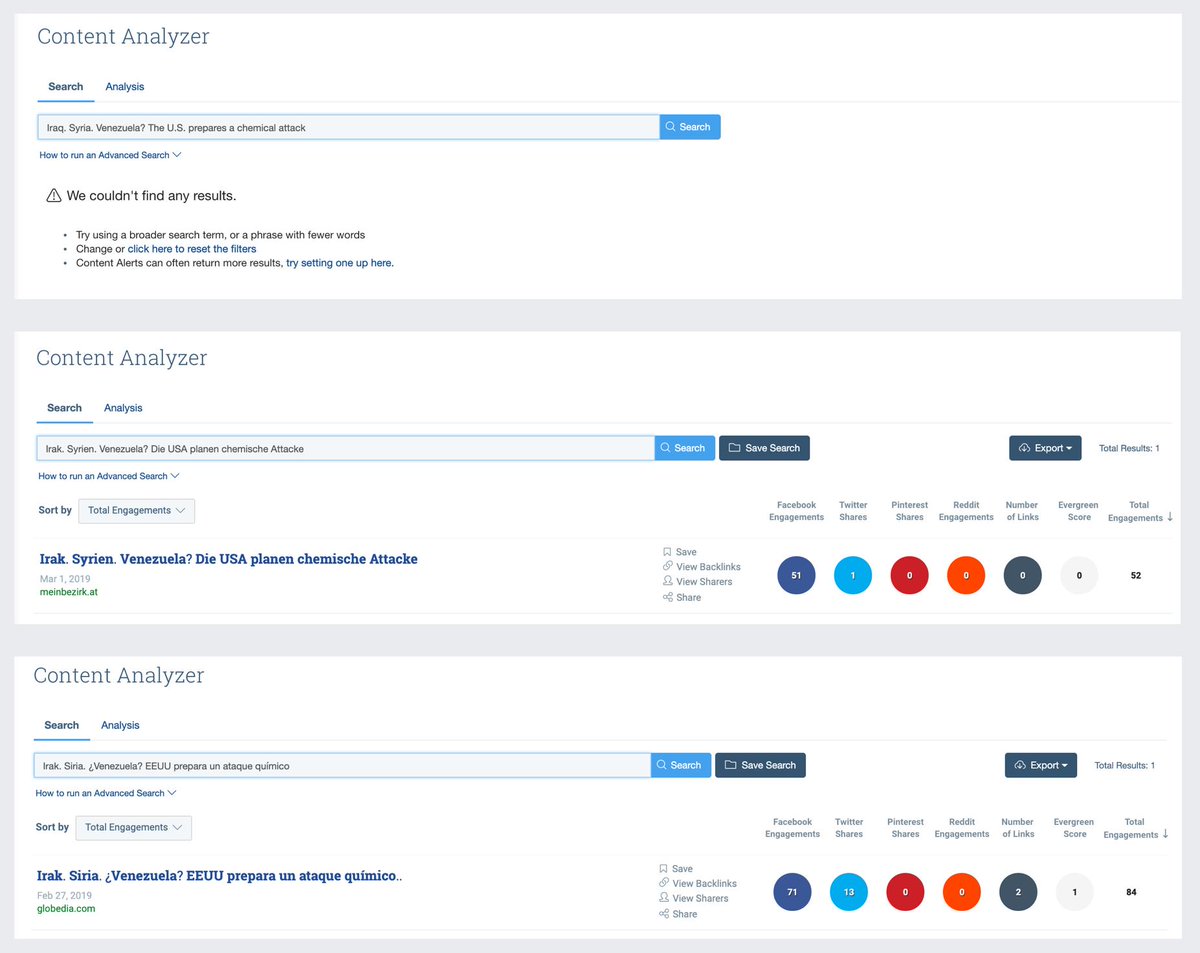
Precise attribution is not possible, but this looks like an intelligence op.
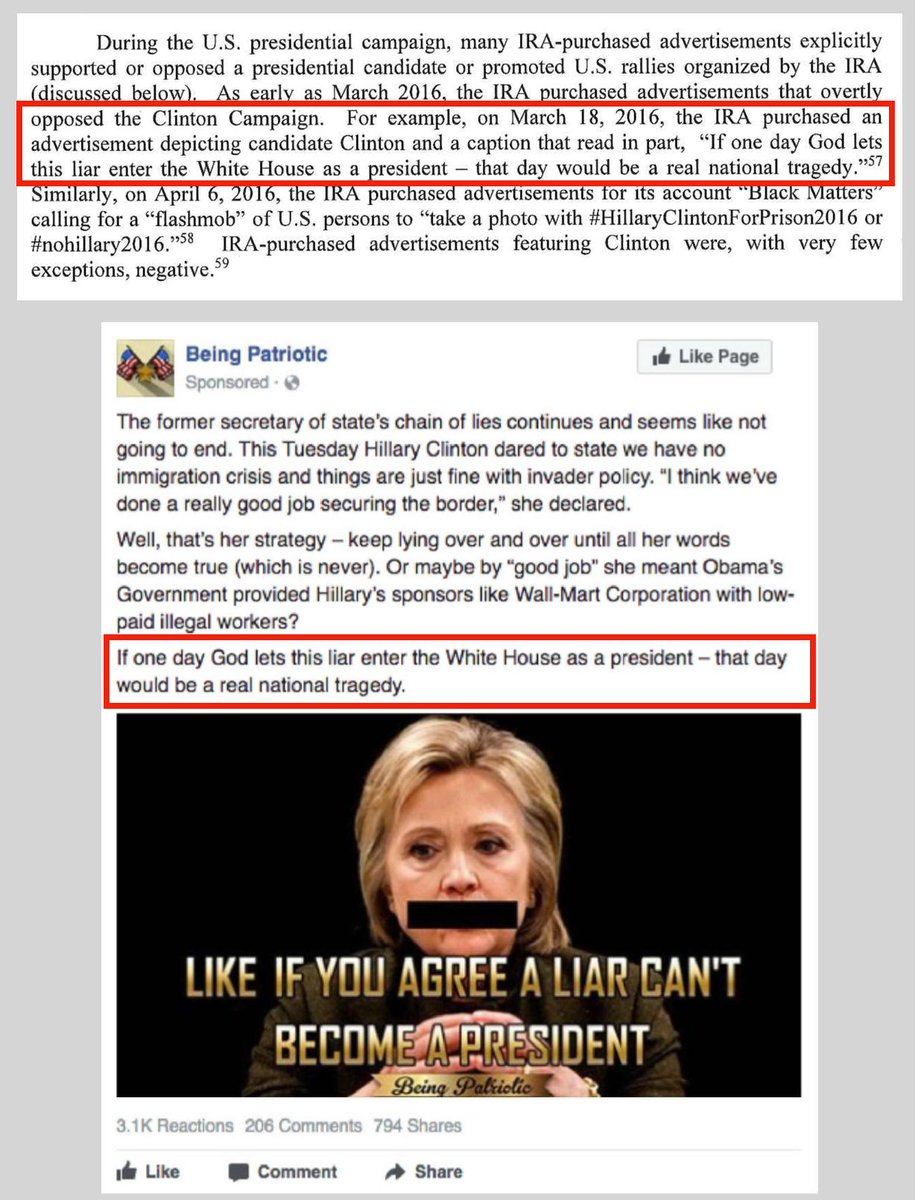
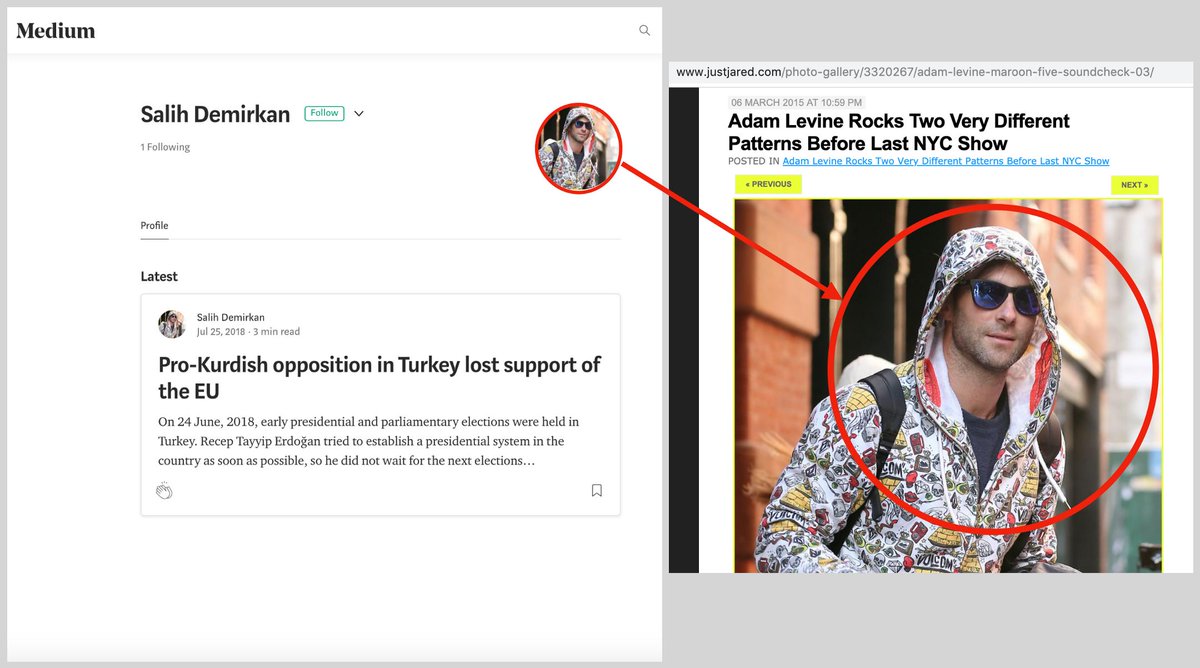
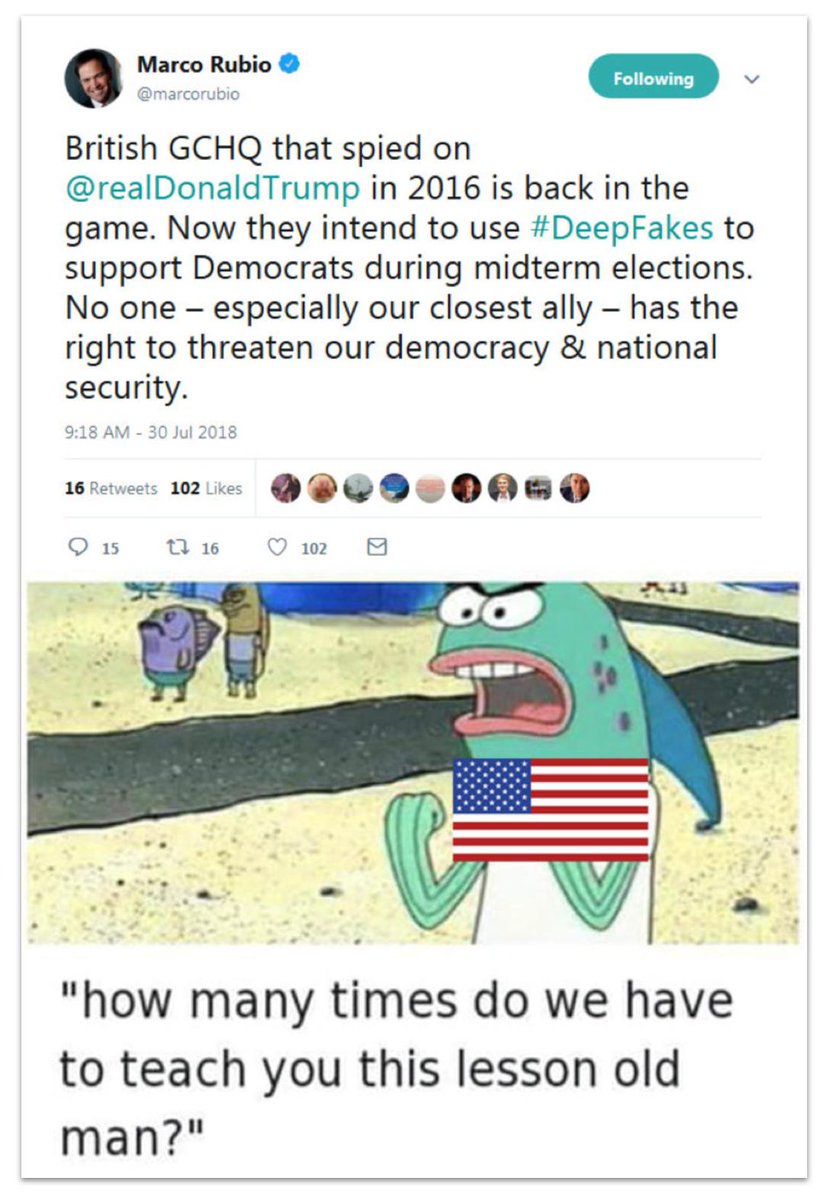
This fake tweet attributed to @marcorubio was one of theirs. It started off as a meme posted by a burner account.
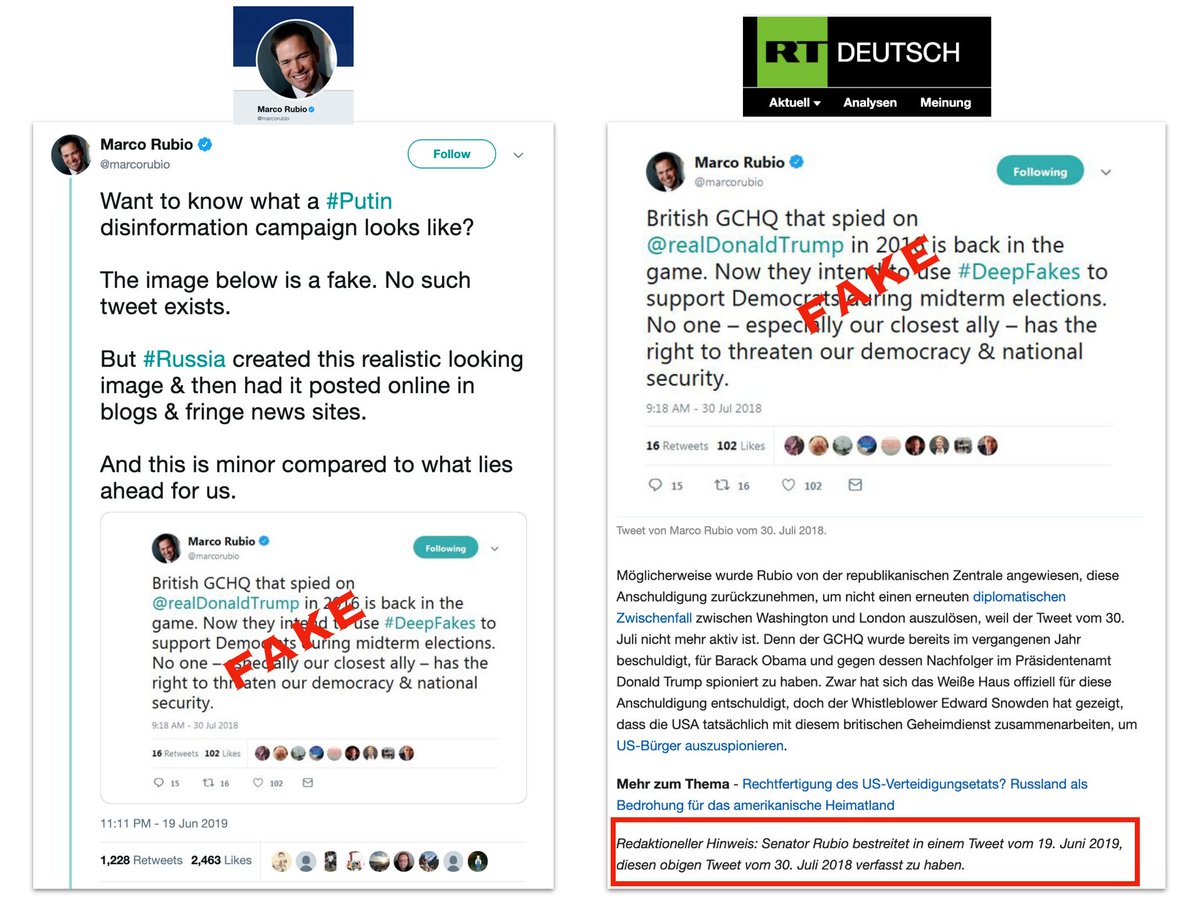
Based on our research, @MarcoRubio tweeted to expose the fake. RT added that he "disputed" the original, but didn't correct.
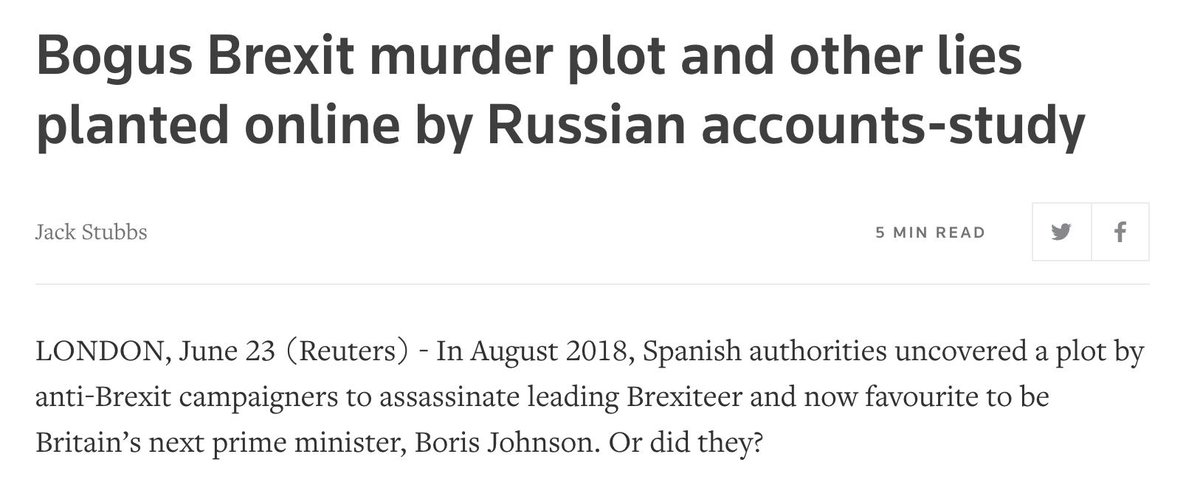
It started with a letter in Spanish, claiming that extremist Remainers were plotting to assassinate... @BorisJohnson.
The letter claimed to be from the Spanish foreign minister, but couldn't even spell his name (it's "Borrell", not "Borell").
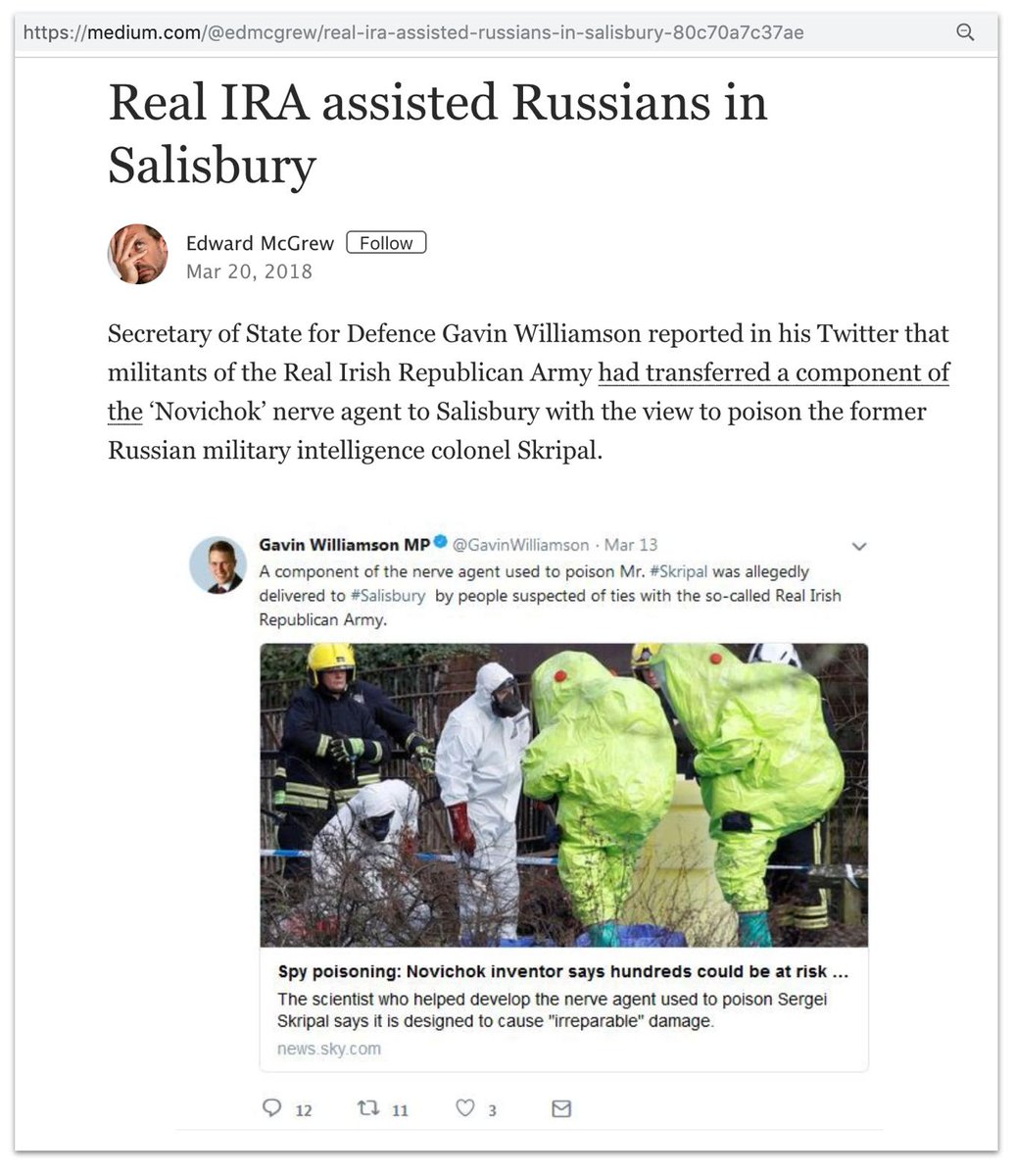
This one used a tweet attributed to @GavinWilliamson implicating the Real IRA in the Salisbury poisoning.
Posted by a burner account on Medium, again. All the indications are that the "tweet" was a fake.
I'd love to know if the operators were House fans. Open sources, sadly, don't go that far.
This time, a burner account even posted the story on a forum in Pakistan.
Created, posted, dropped, all the same day.
reuters.com/article/russia…
Good hunting.
// Thread ends.