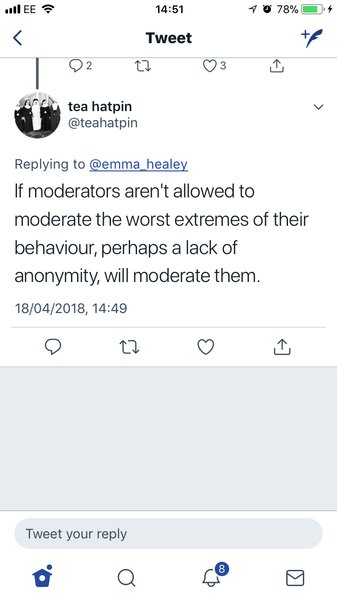
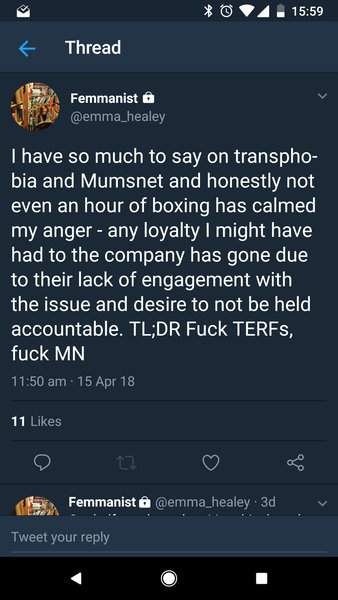
·Be used to initiated hacking attempts.
·Identify where someone works (if visiting from there, for example)
·Cross-reference with other sites to find where else people post.
·Contain real names.
·Contain company names
·Cross-reference with other sites or used to hack