Who is he? Since October 2018, he has been known as the "mastermind" of the #Khashoggi murder.
He is one of #MBS's top aides and has been described as the Saudi crown prince's enforcer and chief propagandist.

They send death threats. They wage disinformation campaigns.
washingtonpost.com/world/saudi-el…
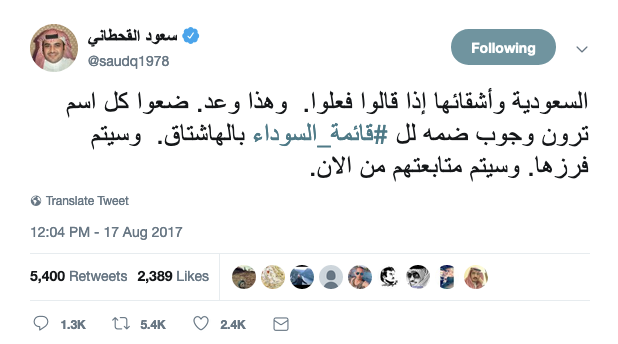
In August 2017, he launched a hashtag that translates to #the_black_list in English — it threatened dissidents that they would be "followed" if tagged.
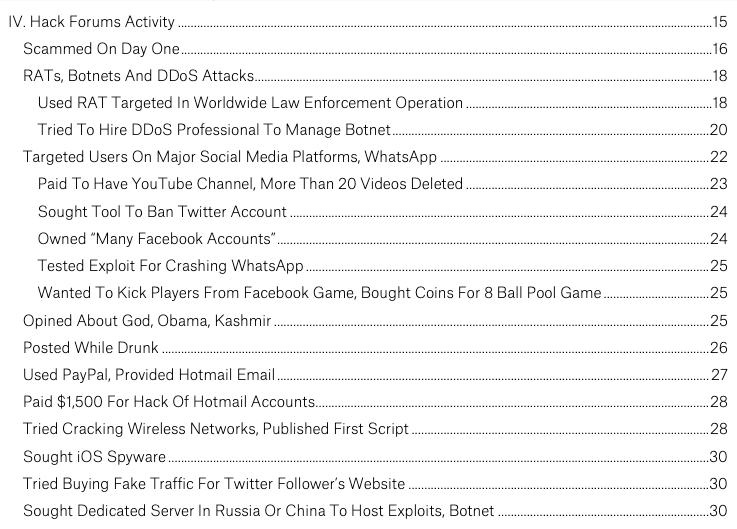
They tied email addresses from someone purporting to be al-Qahtani found in leaked emails from Italian spyware firm Hacking Team to profiles on sites like @HackForumsNet.

We did it by using information leakage on Twitter and Google's password recovery pages.
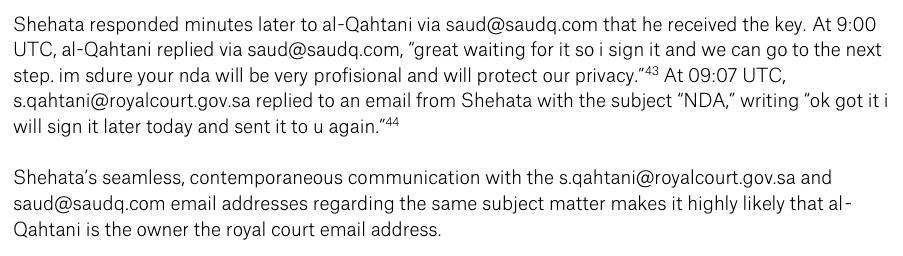
+966 55 548 9750 and saud@saudq.com are both linked to @saudq1978's verified Twitter account.

His s.qahtani@royalcourt.gov.sa account was trickier.
We couldn't confirm it using information leakage. We relied on a telling exchange with a Hacking Team employee.
How much could we find on this guy online? A lot.
@al_b33lz3bub read all 441 posts by al-Qahtani on Hack Forums under his handle nokia2mon2. Here's what we found.
And in 2010. And in 2015.
He was also hacked in 2015, and someone used his account to defraud users of Bitcoin.
He got his account back & recommended everyone turn on #2FA.
Reminder: This is a top intel official.
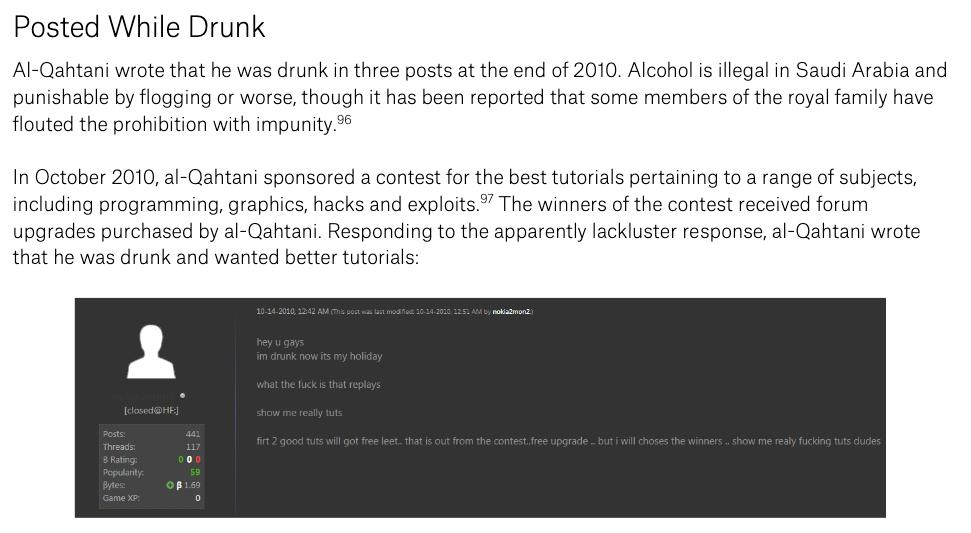
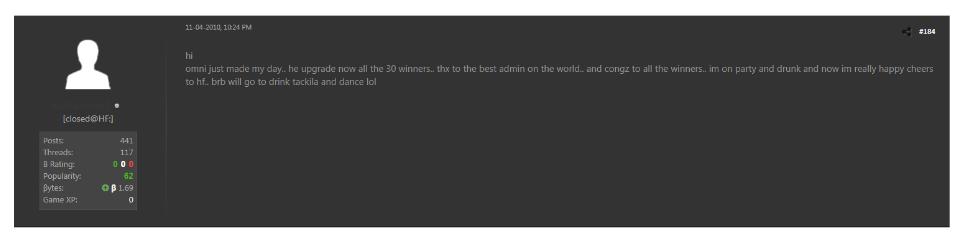
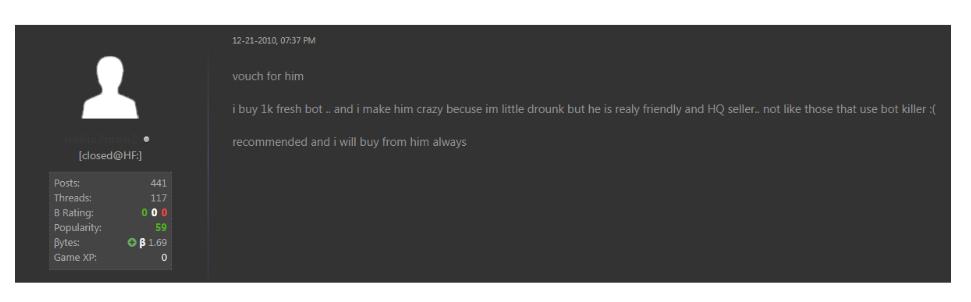
#SaudiArabia has a well-known prohibition against drinking alcohol, of course.
But maybe, just maybe, the rules aren't applied equally?!🤔
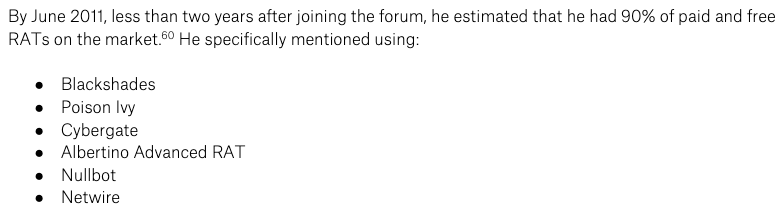
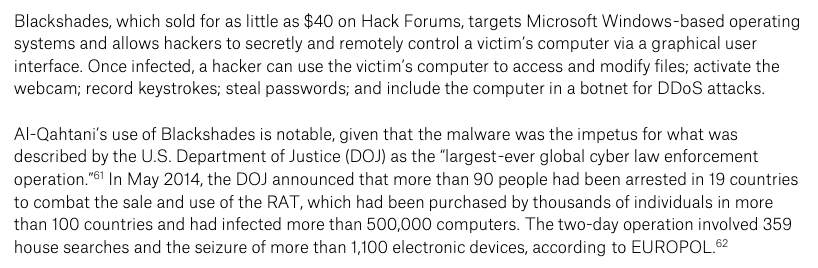
Well, he bought and used as much remote hacking malware (RATs) as he could, including Blackshades, which was the subject of an unprecedented global law enforcement operation.
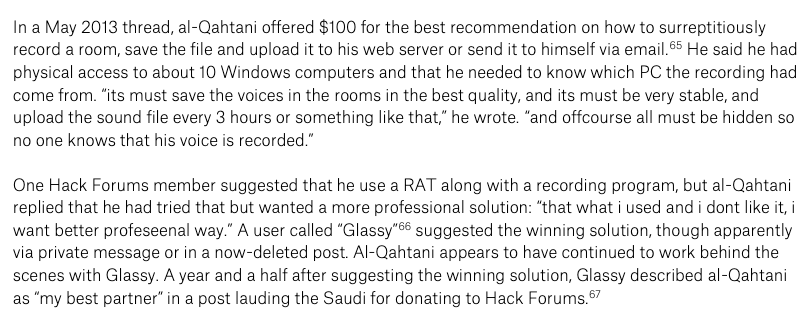
He again lacked the technical knowhow, so he tried hiring flaky server admins or used DDoS for hire services.
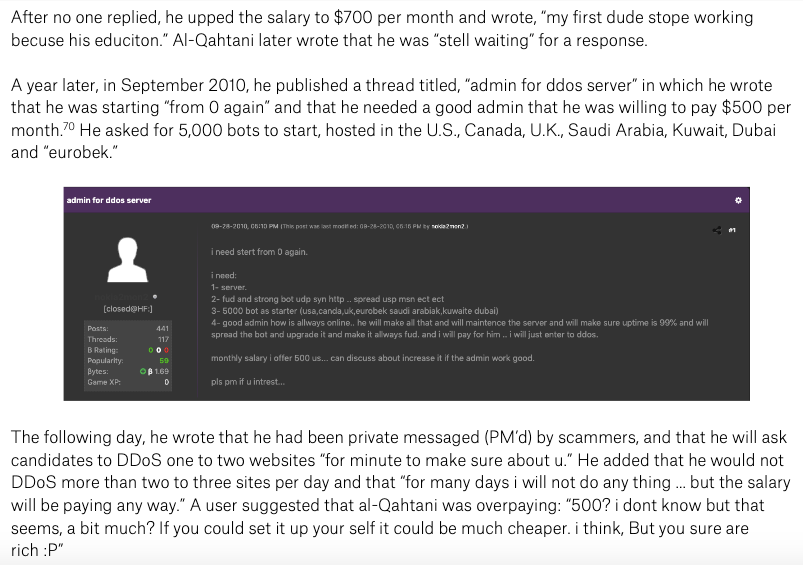
He paid for the deletion of a YouTube channel & said a Hack Forums user had deleted 20 videos for him. He sought a tool to ban Twitter profiles
The Lord of the Flies also had an insatiable appetite for MOAR BOTS.

The most disturbing finding was al-Qahtani's network of domains, some of which were used for hosting malware and launching DDoS attacks.
We encourage readers to build off these findings in your own investigations.
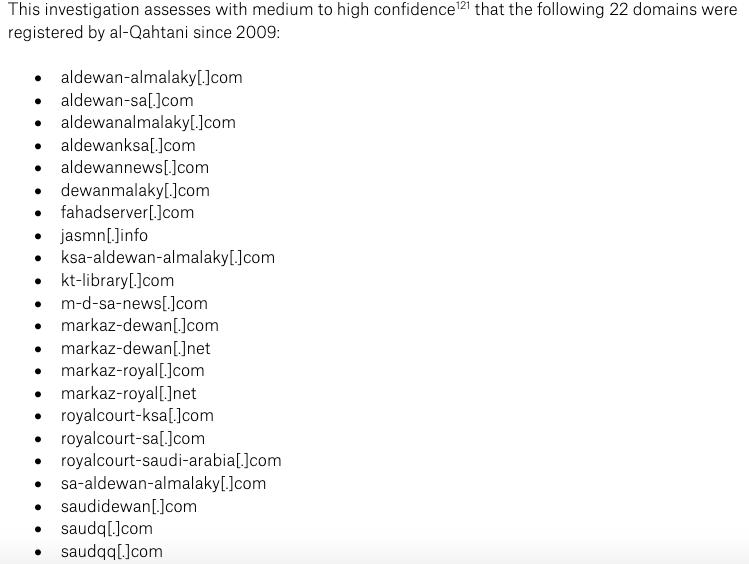
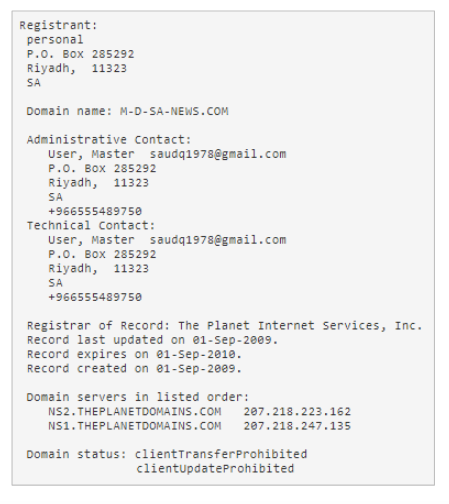
Suffice to say, nothing good.
In the meantime, please read the report.
Victims like #Khashoggi are owed the truth.
bellingcat.com/news/mena/2019…
In fact, if @guardian's reporting is correct, he's still very much active.
The UN's @AgnesCallamard wants him investigated. We agree.