Blockchain in Society: Applications, Economics, Law, and Ethics.
Schedule and livestream here: simons.berkeley.edu/workshops/sche…
AFAIU, it is a technical definition of privacy that formalizes the legal requirements of GDPR. (Asks the question—when could an adversary "signal out" a single person/row from a database?)
arxiv.org/abs/1904.06009
-Differential privacy (DP) and k-anonymity are defined mathematically. Contextual Integrity and Robot Lawyers are defined with formal logic.
-Nissim tried to create a math def of FERPA. It ended up ~= DP.
But, surprisingly, k-anon does not conform with PSO! (Why? Maths that I didn't understand.)
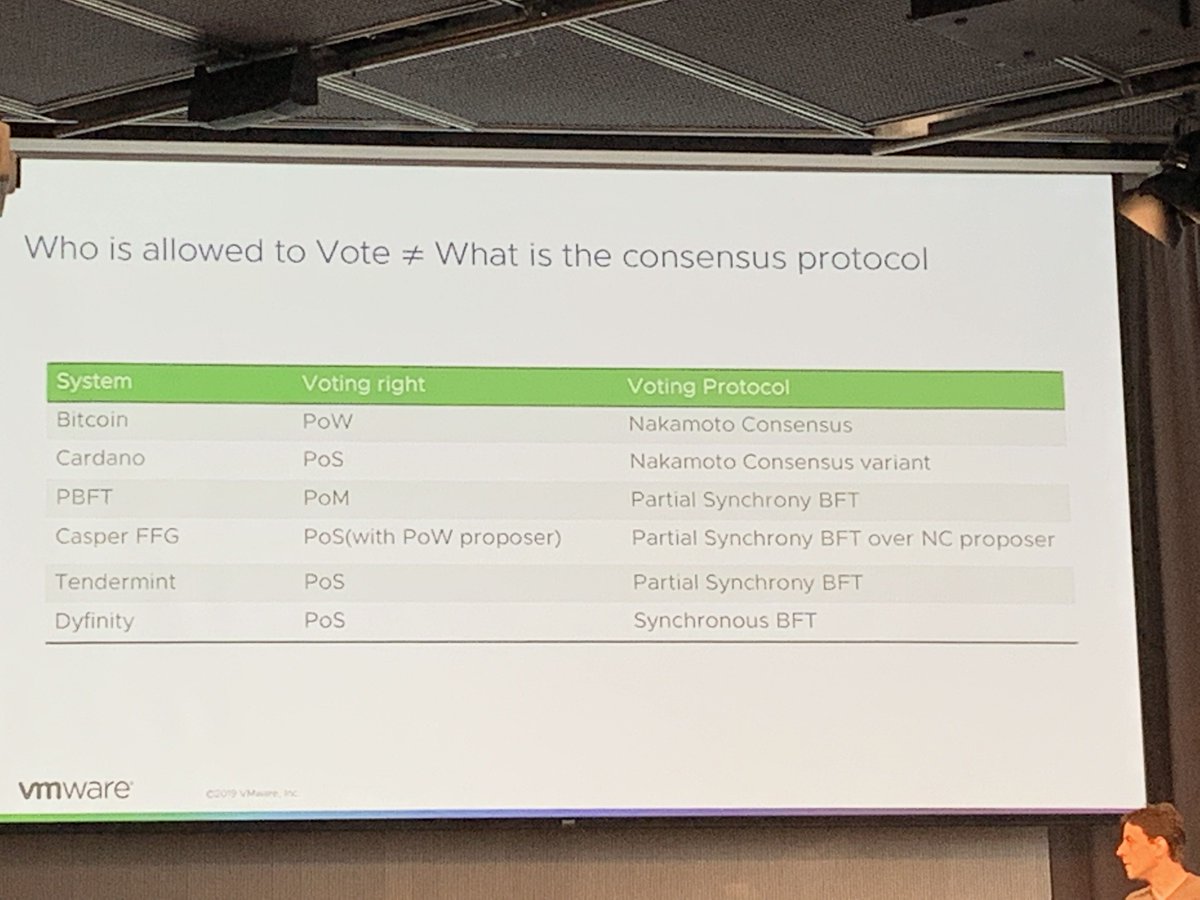
First, Prim explains on-chain vs. off-chain governance.
- On-chain is enforcement BY the infrastructure. Enforcement of rules.
- Off-chain is enforcement OF the infrastructure. Creation of rules.
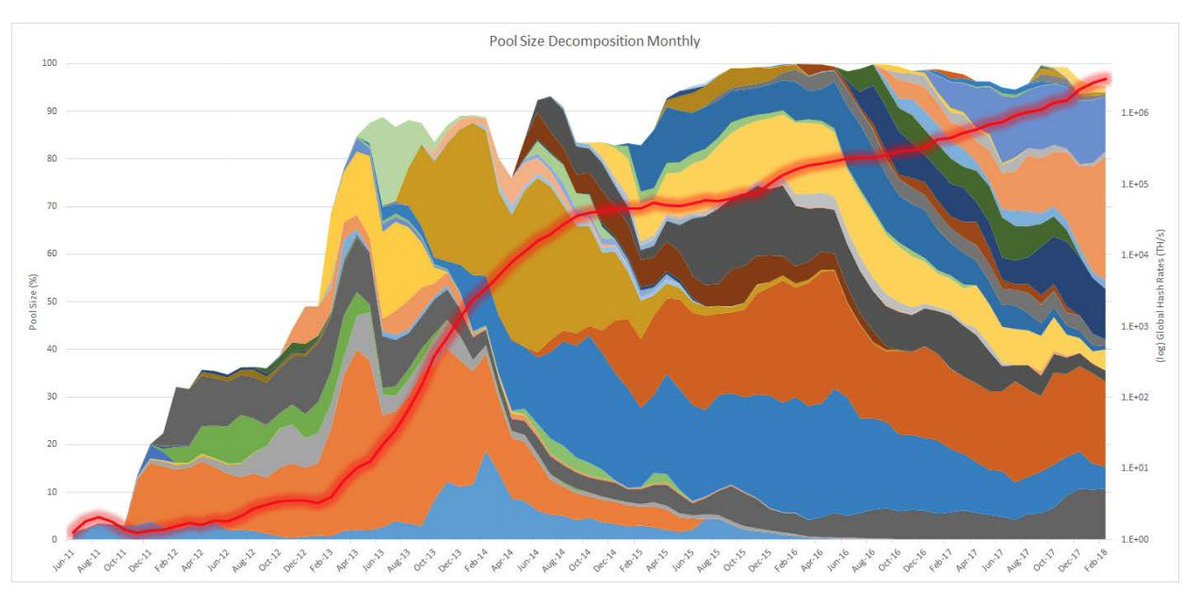
But I do love this graph (that shows how mining pools have increased as a % of total hash rate).
nber.org/papers/w25592.…
See @riabhutoria's: medium.com/circle-researc…
4 ways:
- Naive Replay
- Delegated Accountability
- Trusted Execution Environments (SGX, etc.)
- ZKPs
Each has tradeoff space around privacy, scalability, trust, and attack vectors.
Right now, 99% of computational integrity is done with Naive Replay or Delegated Accountability. But Eli is (obviously) excited by using more ZKPs.
To add a 5th option for CI: fraud-proofs (e.g. @Truebitprotocol @offchainlabs).
With these, the trust is in "economics". (The game theoretical equilibrium of the incentives.)
1. He listens to the question/comment
2. Then reflects it. "If I understand correctly, you're saying..."
3. *Then* responds.
Almost no one does #2. But it's crucial!
Traditionally, we've had "delegated accountability": use a trusted third party to verify the system.
With blockchains, we have "inclusive accountability": *anyone* can verify the system.
But this sacrifices privacy and scalability.
(The best of both worlds!)
tl;dr: claiming that blockchain doesn't have intermediaries is wrong. Miners are intermediaries.
e.g. The crypto world has a strong norm of:
"Crypto devs != fiduciaries"
and
"Crypto miners != intermediaries"
(Angela has pushed back on both.)
-Only miners add new tx, and can change time/order
-Can front run (@phildaian's Flash Boys 2.0)
-Censor (Zcash pool @f2pool_official wasn't adding shielded tx b/c they didn't add that code)
-Rewind (@cz_binance's casual proposal)
- How miners incentives change w/ L2 (see @paddypisa's homepages.cs.ncl.ac.uk/patrick.mccorr…)
- Also see @_prestwich's overview here: blog.keep.network/miners-arent-y…
- FinCEN doesn't think they're a money transmitter
- NY Bitlicense didn't categorize miners as such
And with miners *as* intermediaries:
- OFAC blacklisted Bitcoin addresses
- Should ISPs count as intermediaries? (Answer seems to be that they would get in trouble for OFAC addresses.)
- From FinCEN POV, does "adding tx" count as "accepting and transmitting" $$?
How differentiate intermediaries?
- Intermittent intermediaries. (Miners can only censor tx *some* of the time.)
- Multiple intermediaries. (Miners as part of governance process to determine forks.)
- Types (mining pools vs. cloud etc.)
- To achieve outcomes, when should we trust game theoretical incentives vs. regulation?
- @avivz78 Should miners be regulated as critical infrastructure? (From cybersecurity POV.)
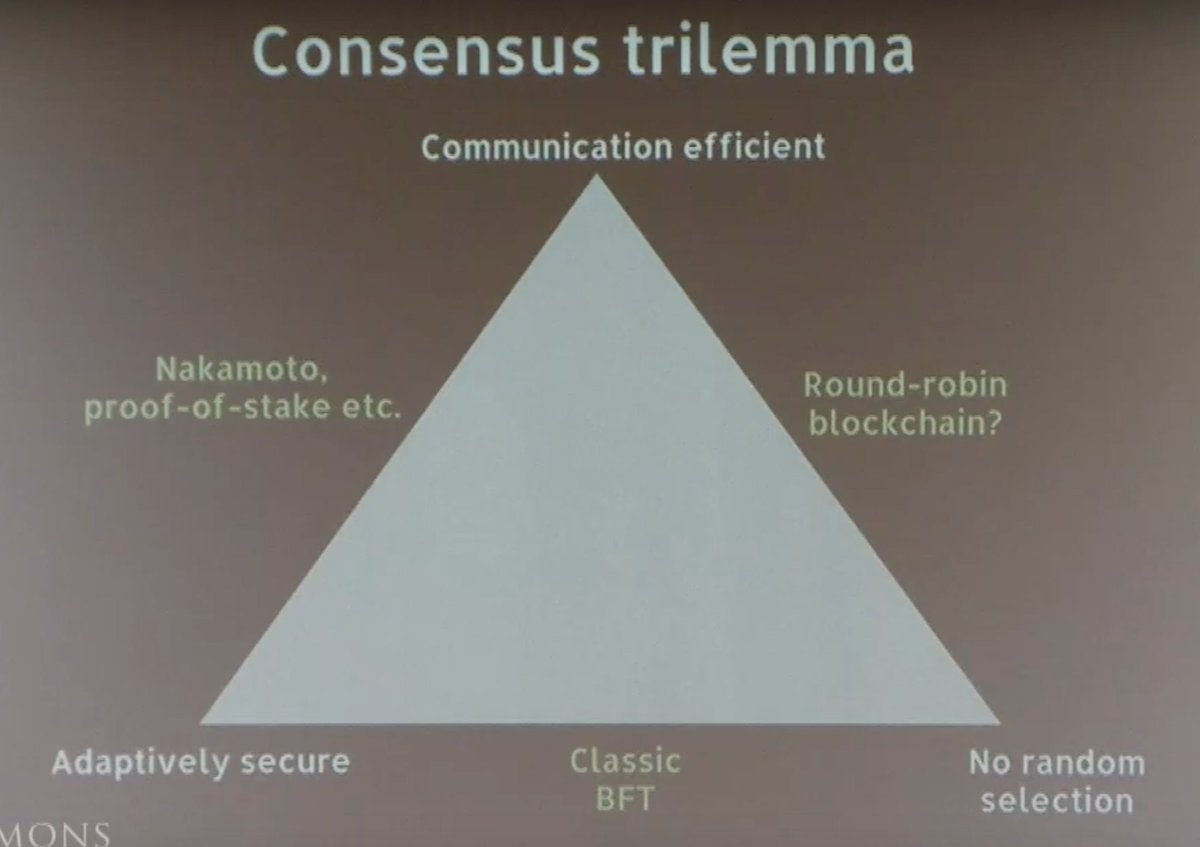
First up, this interesting (non-formal) consensus trilemma. I've never seen this before. It's a pretty way to conceptualize classic BFT vs. Round-Robin vs. PoW/PoS.
- Natural. (How hot is it?) Issue is different sensors.
- Trusted 3rd-party. (Random.org) Issue is trust. Just a company.
-Viewable physical randomness. (Pulling lottery balls.) But can be attacked. (Lead balls.)
-Financial data. In US, lotteries were illegal until 1950. So organized crime did it. They used NSYE digits for randomness. (But can be attacked by messing w/ markets.)
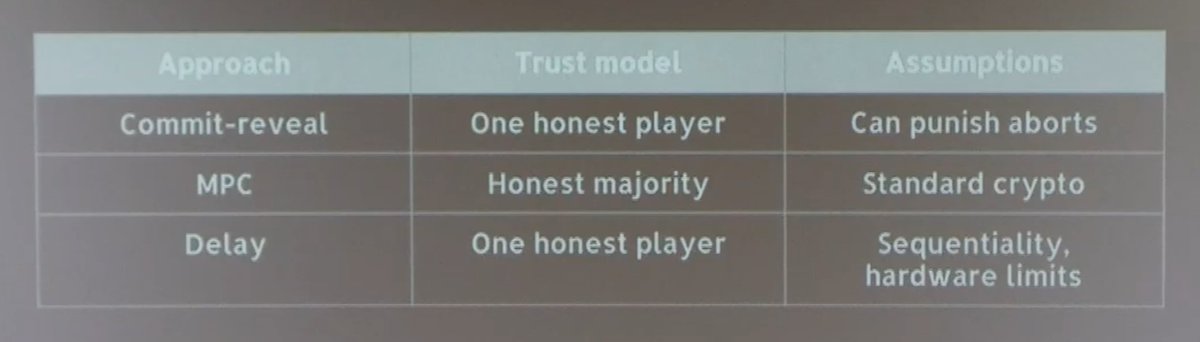
a) You can take away V to get DF (just repeated hashing).
b) But if you want V, you can naively just SNARK the DF. (But super expensive.)
How do V better?
-Still snarky: eprint.iacr.org/2018/601.pdf
-Variants on repeated squaring, which is log(n) efficient to V by binary searching. eprint.iacr.org/2018/623.pdf eprint.iacr.org/2018/627.pdf
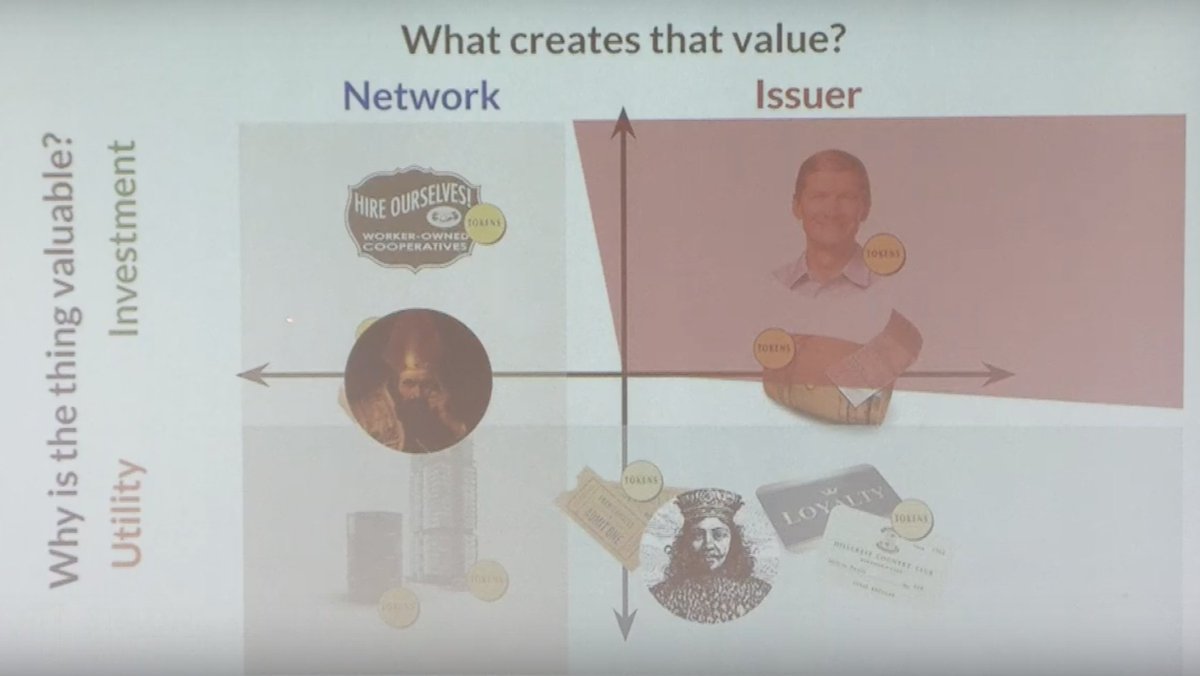
- Regulation is NECESSARY if asset is bought for investment, not utility. (¬ bottom row)
- Regulation is JUST if we can find a "least cost avoider". A single issuer not a huge network. (¬ left column)