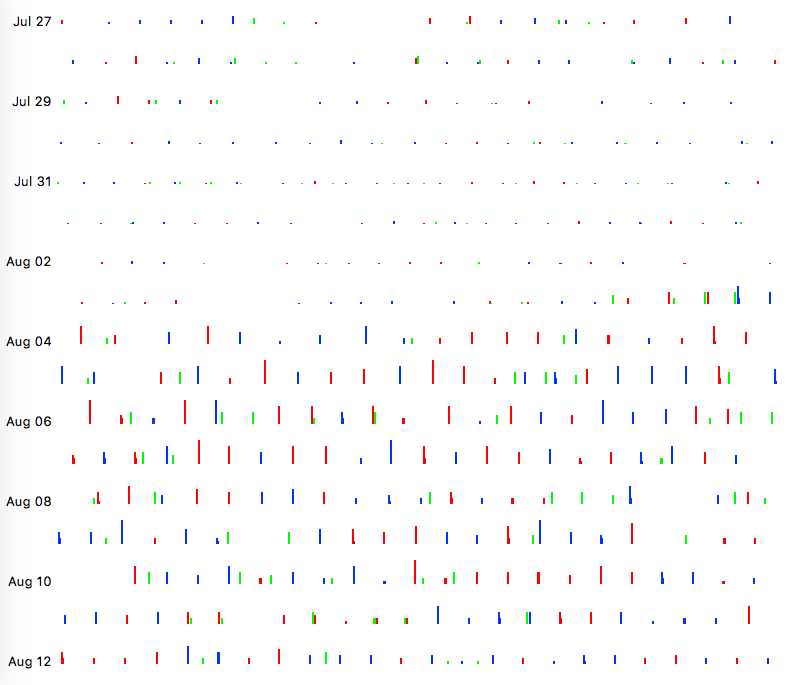
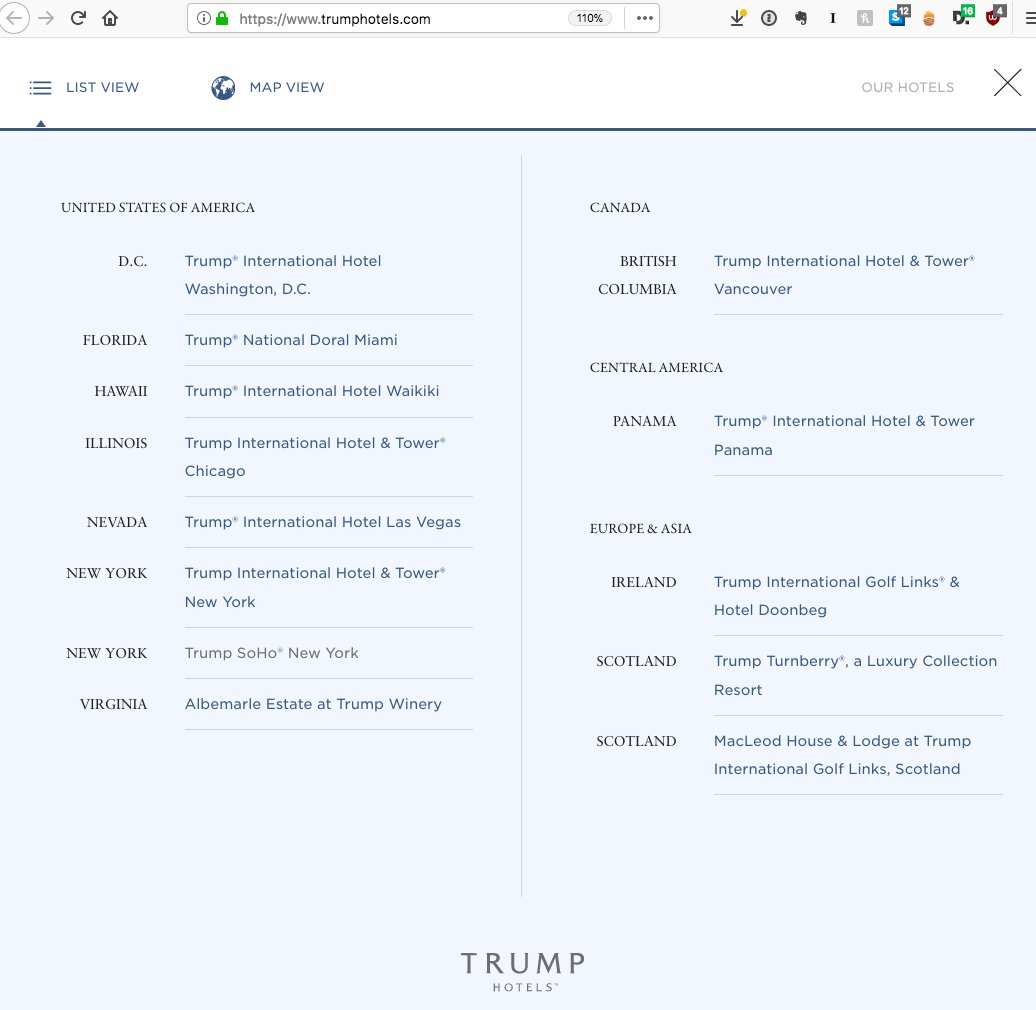
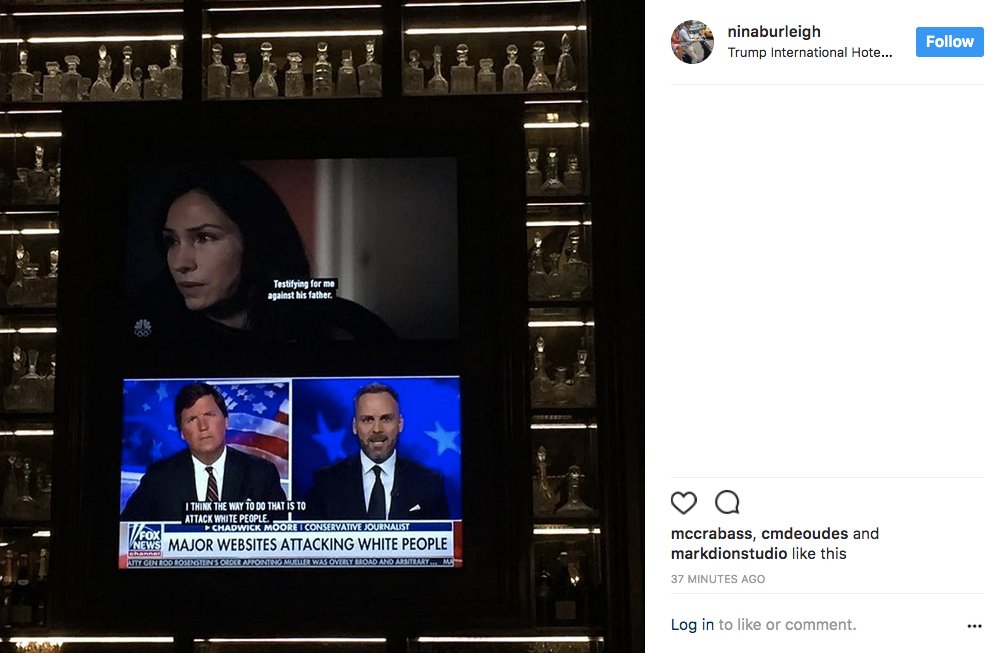
Each row is one day, sliced into two minute slots, and each bar is the number of lookups in that slot.
Claims that these are misconfigured systems going over old mail data are clearly not correct. Some new event has coordinated activity.
A "Domain Name Service" (DNS) lookup finds information about host names. The most common example would be "What is the address of example.com"?