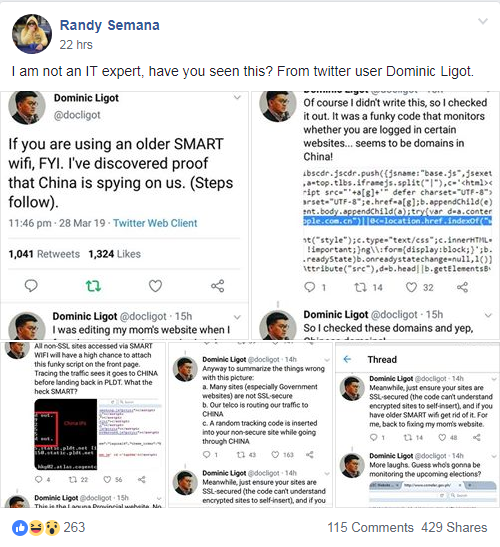
a. Many sites (especially Government websites) are not SSL-secure
b. Our telco is routing our traffic to CHINA
c. A random tracking code is inserted into your non-secure site while going through CHINA
superuser.com/questions/1411…
Any network/device on SSL sites - negative.
For non-SSL sites:
Globe, Nexlogic, Converge - negative.
Using Smart on non-SSL sites:
Oppo A37F, Oppo CPH1801, Xiaomi Double Mi - positive.
LG Stylus 2 - negative.
Will test more devices as I encounter them.
Using Globe on non-SSL sites:
Oppo A37F, Oppo CPH1801, Xiaomi Double Mi - negative.
LG Stylus 2 - negative.
So Globe seems to be negative on these devices. Only the China phones are positive on Smart.
- 10.xx.xx.xx IP addresses aren't China. They are internal to some network (presumably Smart/Sun)
- The code is inserted from these servers
- The code is only inserted if the site is non-SSL
- This seems to only happen using China-phones using Smart/Sun sims.
- The websites we tested (DICT, COMELEC, PNP, NAVY, LAGUNA, MALACANANG) - were all NON-SSL secured
Why is a weird code getting inserted on non-SSL websites from the network?
Why does it only happen on (some) Smart wifi using certain (China) phones?
Why are our many gov websites non-SSL?
- I've been advised by some colleagues from the industry that the telco concerned has taken down the offending server/s
- At least one government website (Laguna) has installed SSL encryption
- Am still testing using my Smart SIM but it is currently down
news.abs-cbn.com/news/03/29/19/…
- Yes it's already established. But the fact is these IPs are part of the route of the traffic. The endpoint is public. I have packet capture and traceroute to prove this.
- That was the first thing we checked. So we tested on multiple laptops. The script is not attached at client side, it is attached at server side - along the way of the traffic. Malware on laptop was also tested. Negative.
- I admitted that I am not a Cybersecurity professional but I have collectively 20+ years in data analytics, data warehousing, networks data centers and web development apart from having a stint in Surveillance and Fraud for a major bank.
- I have been coding since I was 6, and fluent in at least 5 dev languages (although I only use 3 nowadays). I also write Python and Javascript for a living. I teach coding actually - although I'm always open to learn.
Try harder IT Wannabees. Sayang yung sipag ko dito.
reddit.com/r/Philippines/…
- If you are using the network+device mentioned, your traffic goes to the said offending server
- If you are surfing a non-SSL site, the server is able to read and insert the offending script into the site
- The script loads once the site loads
- The script gathers high-level information about what you are doing - time surfed and the site you are viewing and sends this back to the offending server
- The script terminates only if you are on the 2 China websites mentioned
- No info seems to be directly sent to the Chinese websites, the script just monitors if you are there
- No other changes are made to the user's system. So there's seems to be no "infection" to your device worry about.
- Data is still being gathered from you and sent back. So if you are browsing non-SSL be very careful about data you transmit. Avoid non-SSL sites if possible
gmanetwork.com/news/scitech/t…






















