zdnet.com/article/chines…
They also filtered texts based on particular phone numbers and particular device identifiers.

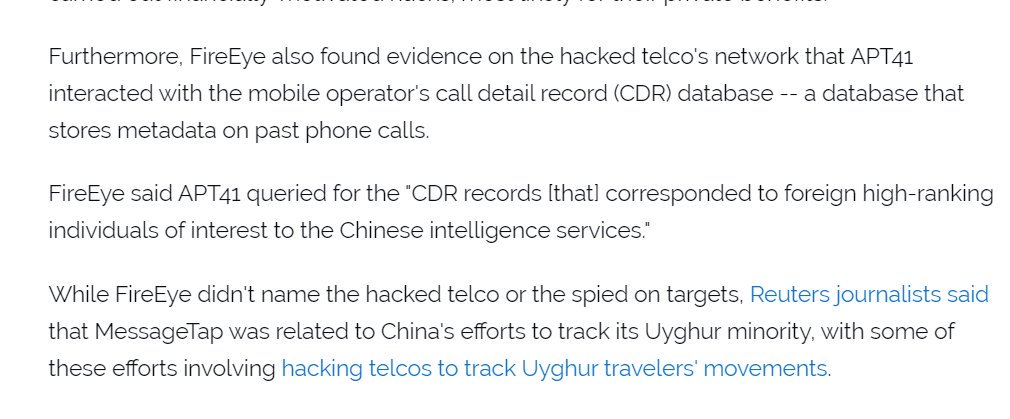
The spyware is also related to #China's spying/tracking of Uyghurs.
cybereason.com/blog/operation…
zdnet.com/article/these-…
thenextweb.com/security/2019/…