This is the document which is being proffered to protect the facts & details of _YOUR_ online #Porn viewing. Let's read it together!
What could possibly go wrong?
ageverificationregulator.com/assets/bbfc-ag…

"this is the foundation of the non-statutory, voluntary age-verification certification scheme (the Scheme)"
"Only age-verification providers that meet the requirements of the Standard…will receive certification"
What happens to the ones that don't?


In case I miss it, let me know if they've got this covered?
Bit of a difference, there.
How is that ethical of them? Do they want to put people in harm's way?
Don't get me wrong - this is the laudable ISO27001 & BSI approach towards security, but what they _actually_ ought to be doing is the PCI/DSS approach towards security.
Explanation coming up:

This is what's being proposed. It's not enough.
Such is the PCI/DSS approach: "the Internet is an information security earthquake zone"
This takes time, and the @BBFC have not _got_ time, so they have attempted to bodge it:
«We can't build an earthquake-proof information security spec in time, so we'll let people build whatever they want, require them to document it fully, and then we'll go shake the buildings every so often to see if anything bad happens?…»

I AM SURE THERE ARE SOME SITES WHICH WILL PUT THEIR HANDS UP FOR IT, BUT WHY BOTHER?
WHAT'S THE WIN?
player.fm/series/in-my-m…
In truth, they're window-dressing.

That's bullshit.
Will it? Fuck me, no. It punts everything technical to vague obligations upon the #AgeVerification provider:




1/ the scheme is voluntary
2/ the scheme will be a hassle
3/ the scheme confers no customer benefit other than some kind of kitemark, which barely any customers will care about.
Ergo: the scheme is a fig-leaf for something

- if they ARE NOT certified, they are roasted in the press / by regulators as presumably being slapdash/haphazard with process; this leads to "pressure to certify." Sounds good, yes? No…

AND THEN WHAT? TO WHAT END? WOULD CRAYON BE SUFFICIENT, OR DO WE NEED VISIO? WHO NEEDS THEM? HOW FAST?

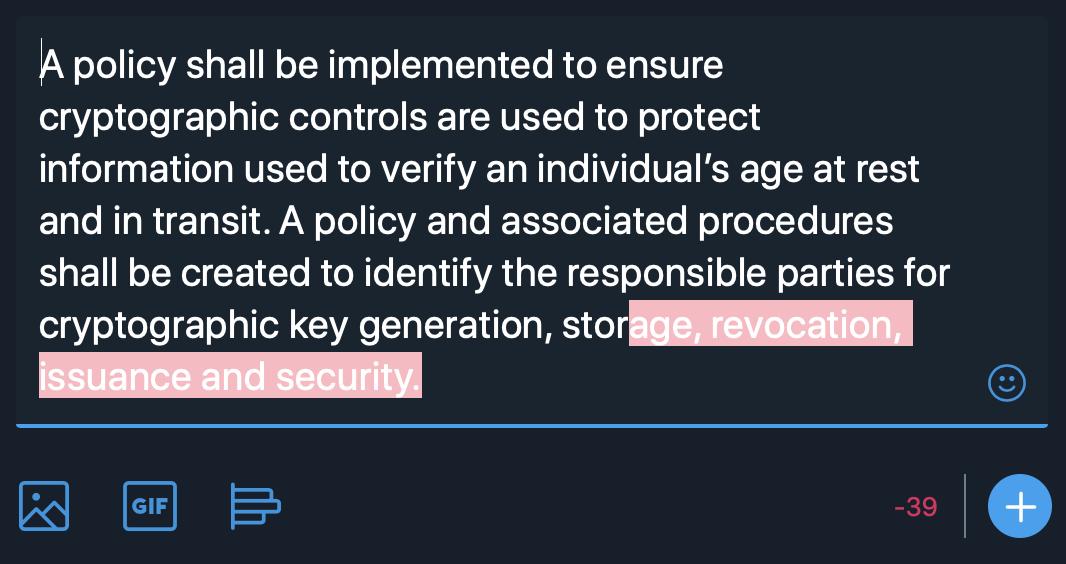
"Data protection by design shall be implemented within all relevant business processes."
— THAT SENTENCE FRAGMENT DOES NOT ACTUALLY MEAN ANYTHING

…ok, so how will the "fraud prevention and detection" stuff work? I believe this LITERALLY negates the point of AV.
There are no standard pseudonymisation techniques; where deployed, pseudonymisation must be tuned to the information available in each environment.

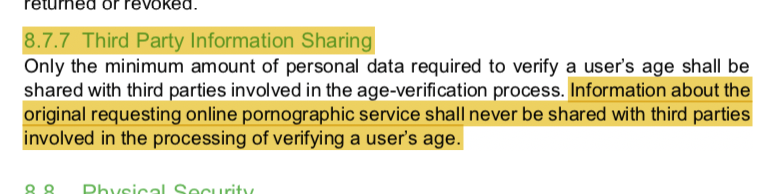
"Age-verification providers shall only share the result of an age-verification check (pass or fail) with the requesting website."
But should say:
"…shall only share, AND SHARE ONLY the result of an age-verification check…with the requesting website."


That means… session-ids / tracking cookies!
Otherwise the user experience will be far, far too painful.

This is where… I get… disappointed.

#noWords
Architecture? Implementation language? EBCDIC?
(see also en.wikipedia.org/wiki/The_Tao_o…)
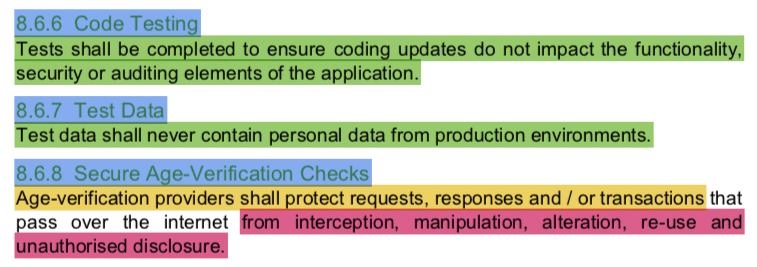
"Secure programming guides from industry recognised sources shall be utilised for each coding language in use and applied to any information system implementation efforts."
Utilised and applied how? And to what extent? With what exceptions?
"Age-verification providers shall protect requests, responses and / or transactions that pass over the internet from interception, manipulation, alteration, re-use and unauthorised disclosure."
Disclosure? Like in a public ledger?
medium.com/@alecmuffett/h…
- open and read the manual
- find every instance of being told "do not do [x]"
- do [x] and as many variants of [x] as you can possibly think of
There's a lot of it, implicit in this document.
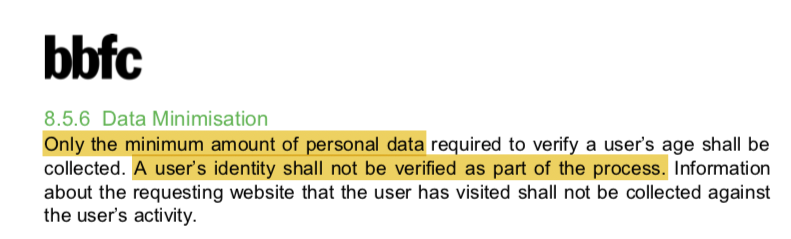
"A user’s identity shall not be verified as part of the process." - what does "verified" entail, here?
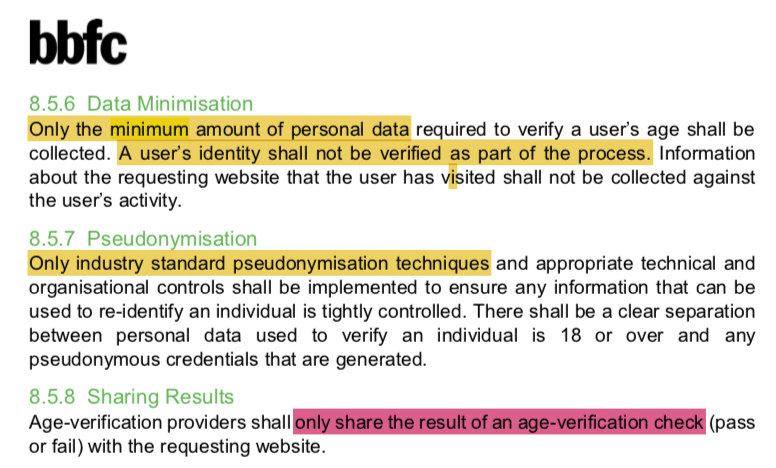
"Only industry standard pseudonymisation techniques…shall be implemented" - but will they be an effective choice for the specific deployment?
This document's approach to data protection is fundamentally flawed.

Or, at least, it would be smart if it weren't voluntary.

( just in case you haven't worked this out, yet )
§8.7.4 "[AV] providers and third parties who can impact, or who are responsible for maintaining, security and privacy controls shall clearly document each party’s responsibility in implementing and maintaining the relevant controls of this Standard."
And then what?

Please define "destroyed"?
Will (eg:) Mindgeek be a third party unto itself? They own a complete AV-to-Content pipeline…

This is the #PenetrationTesting spec; and…
"Penetration testing of [THING] shall be tested by a suitably qualified individual at least annually or after a significant change."
EVERY 👏 FUCKING 👏 TIME

If turnips were watches, I'd wear one by my side.
If "if's" and "and's" were pots and pans,
There'd be no work for tinkers' hands.
en.wikipedia.org/wiki/If_wishes…
we would all be secure. 🤦♂️
No GIF on this one.
No graphic.
No link.
This is too terrible; but there's more:
How long are "non-critical risks" given to be fixed, then?
It's better than #PAS1296, but it's still not fit for purpose.

>Roles and responsibilities associated with information security, data protection and operational activities shall be clearly defined and documented by zombies.
This is a good technique for identifying some of the weaknesses.