A good friend asked me what I thought about it and I admitted I hadn't bothered to read up on it.
One of the things we did with @savagesec was that we wrote up advisories for our customers. A lot of them had to do with these 'named' vulns.
🚩named vulnerability
🚩logo (animated, even!)
🚩dark, ominous video
🚩lacking key, important details
🚩lead gen form to download paper
In addition to the common denominators above, they all had some stuff in common. They claimed HUGE impact, when the impact was actually much smaller because of circumstances.
"Simjacker Can Track Phones Just by Sending a Text"
"SimJacker attack allows hacking any phone with just an SMS"
Both headlines are wrong.
As with most of my other advisories, my opinions here are based on primary sources and my own testing.
Also like many baseband vulns, obscurity is not a substitute for security.
It definitely appears to be a legit, 1990s-era no-authentication style issue.
portal.3gpp.org/desktopmodules…
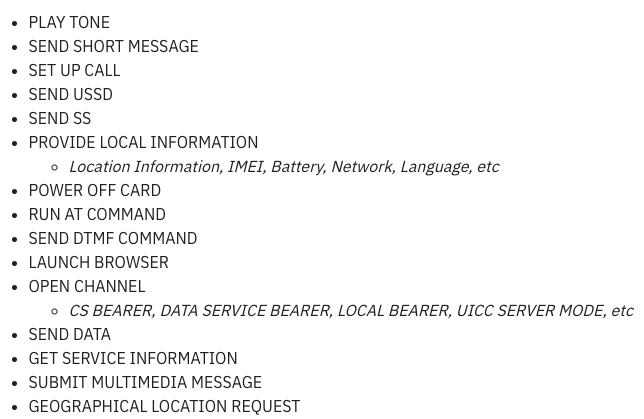
Attack1: Location Tracking
Attack2: Call Fraud
Attack3: Browser Hacking
We'll take a quick look at each.
This nets you a Cell-ID. What's a Cell-ID? From what I can tell, it's the ID of the Cell tower you're connected to.
Takes a leap to get from "tracking phones" to "nearest cell". Overstated claim.
They can get the IMEI though, which is not good.
You can PREP a call to be dialed, but still need the user to tap "Call". What's scary about making a call? The idea is that the attacker could con you into calling an expensive international number.
Social engineering is required to complete this one.
As with the "Call Fraud" scenario, the attacker can tell the phone to open a URL in a browser, but the rest of the attack relies on client-side attacks or social engineering.
Not a lot of meat on this bone.
They don't give any suggestions on how any of this might be accomplished.
I don't know of any good way to determine this, besides contacting them all one-by-one as Joe did.
logossolvo.com/wireless-telec…
The coordinates are almost exactly 1km from my actual location - a 6 minute drive from my house, according to Google Maps.













