Let’s break down the steps ! 🧵
#30DaysOfThreads #infosec #security #tech 1/9
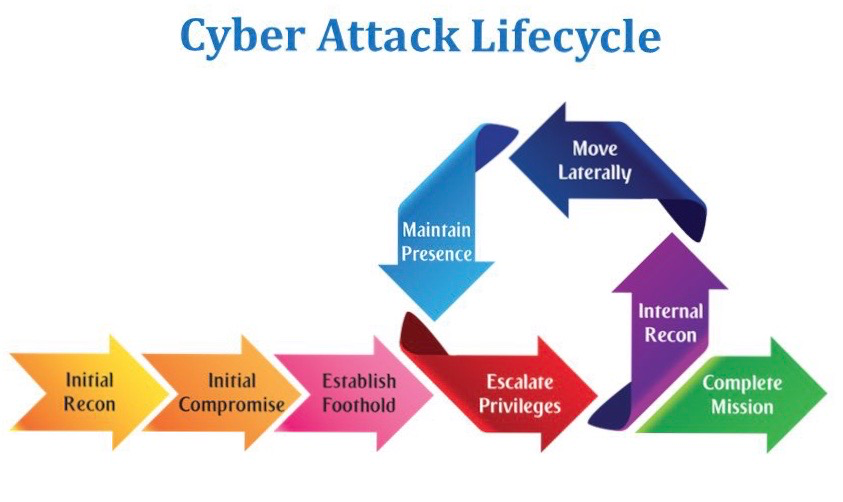
Intruder selects target, researches it, and attempts to identify vulnerabilities in the target network. Some things attackers use and look for:
Whois
Target IP Ranges
Web Properties, Domains & Subdomains
Open Cloud Buckets
Google dorking
Attacker compromises a vulnerable host. This may be a DMZ host or something in a higher security group via email phish. This is the first step into a network and why security people always say:
Don't click email links!
Don't open email attachments!
A compromised system is good, one that you can access is even better. Initial access or a foothold is an attackers first steps in your network. If there are network rules to block various network traffic, the attack may die here.
Attackers often need more privileges on a system to get access to more data and permissions: for this, they need to escalate their privileges often to an Admin.
Where are we internally , what are we looking for, and how can I get there?
Here we apply the OODA loop - a simple strategy to help you find your way forward.
Observe - What do I see
Orient - Where am I
Decision - What do I need to do?
Action - DO
Once they’re in a system, attackers can move laterally to other systems and accounts in order to gain more leverage: whether that’s higher permissions, more data, or greater access to systems.
Being able to return to networks again and again is one of an attackers main goals. They may not find what they’re looking for during in the first compromise and they will want to return.
Mission complete can be any number of things, anything your mind can think up from any spy or heist movie. Real data gets stolen every day. The current “average time to detect a breach” is 197 days.
Stay safe out there!




