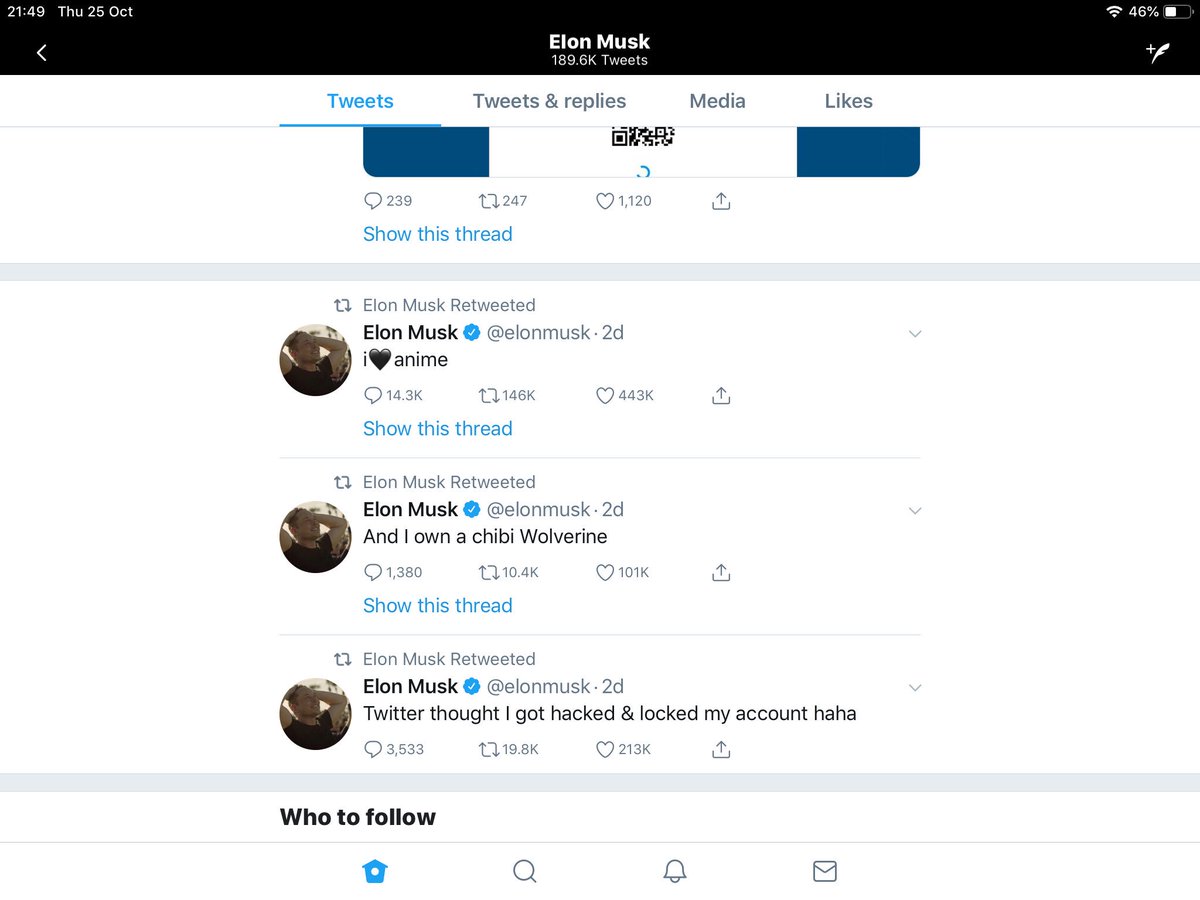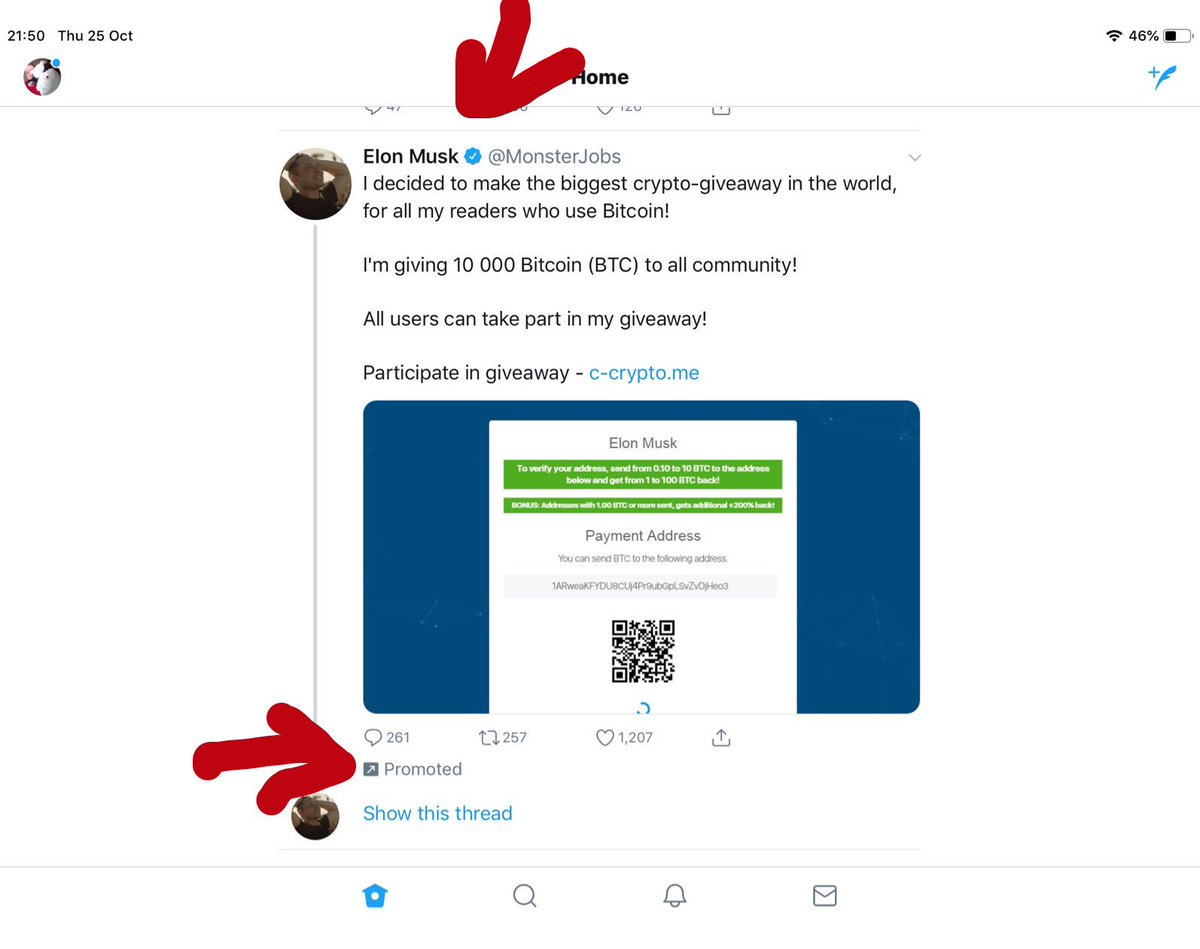
And, yes, these are all real tweets.



Firstly, you hack or phish the login credentials for some credible accounts. You’ll need to hack one account to host the scam tweet (@MonsterJobs in this case) and some other good accounts to lend the scam credibility (see above).
#phishing
#scam #onlinesafety
#security #onlinesecurity
This is, however, another example of why companies need proper 24 hour social media monitoring and disaster recovery training. The reputational damage can be immense.
#gemdbs2018