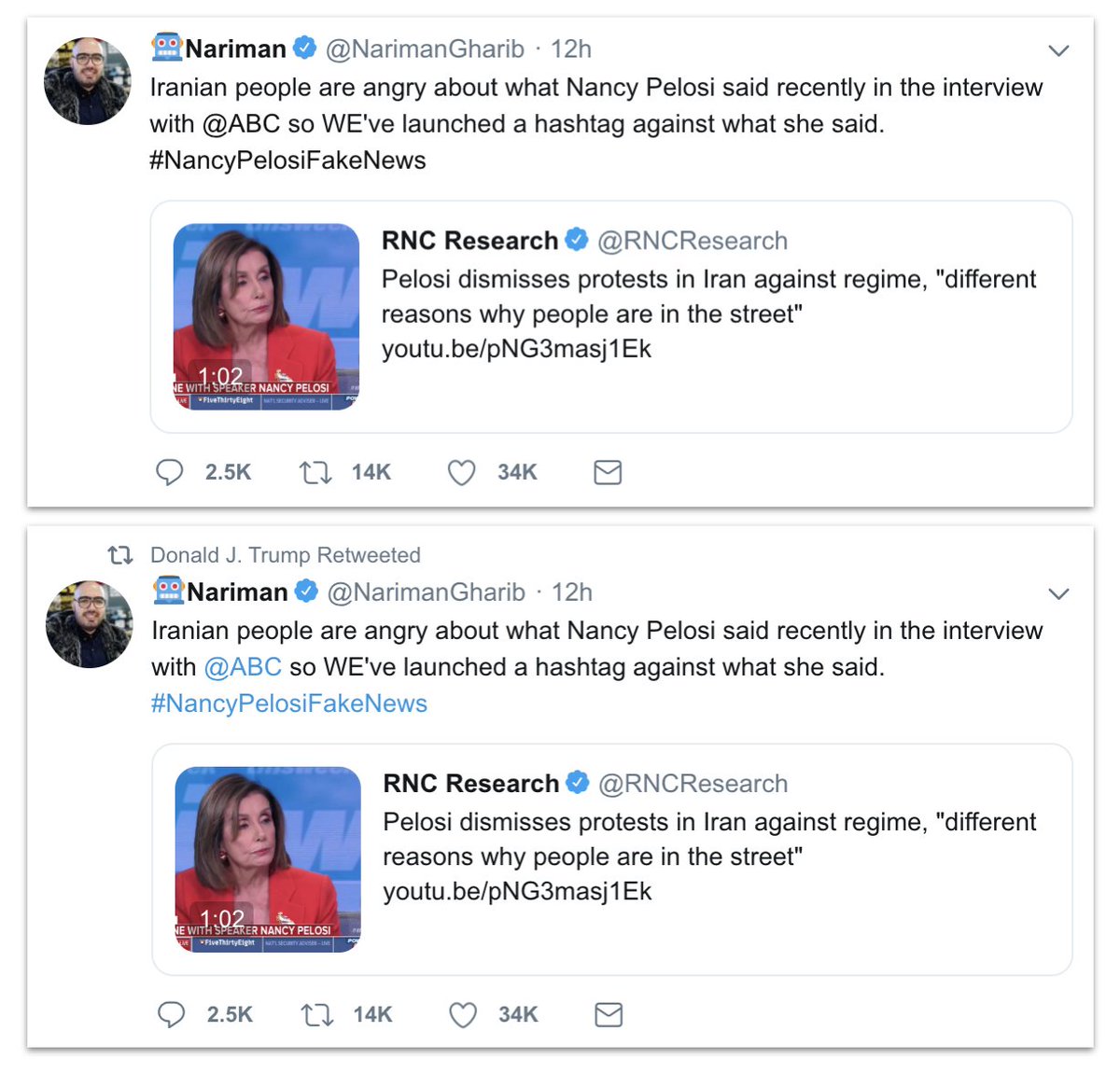
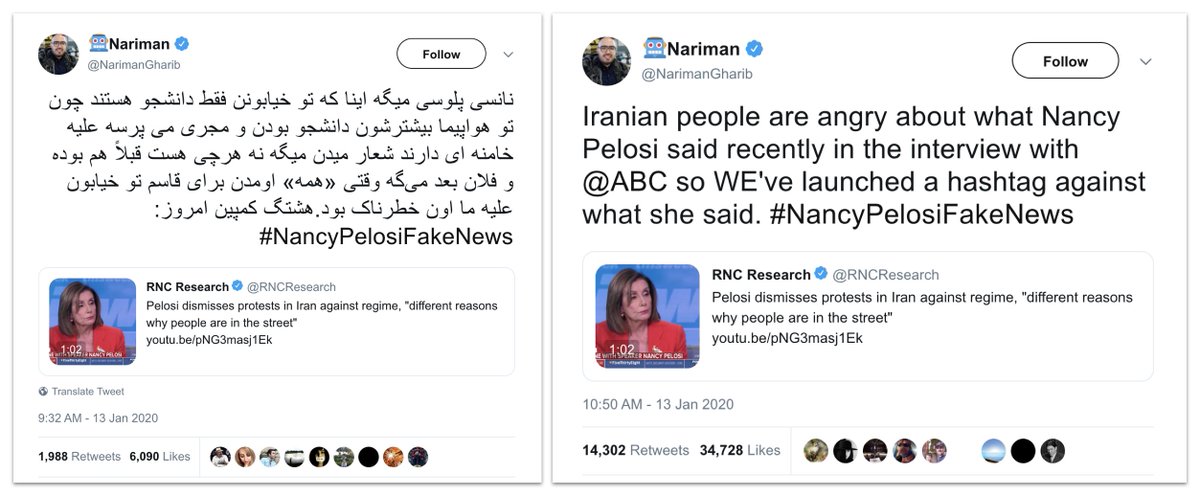
- Russia: military intel targeting Ukraine and neighbourhood;
- Iran: 11 assets targeting US;
- Myanmar: telecoms providers targeting competitors.
@Graphika_NYC report on the Russian op to follow.
about.fb.com/news/2020/02/r…
Blogs were the backbone of this operation. It also used direct messages to target individuals, and pose as citizen journalists.
Not the first time we've seen such things, but they're an under-appreciated threat.
graphika.com/reports/from-r…
Interestingly, there was quite a focus on the Crimean Tatars. And they couldn't resist a dig at @bellingcat and @EliotHiggins, too.
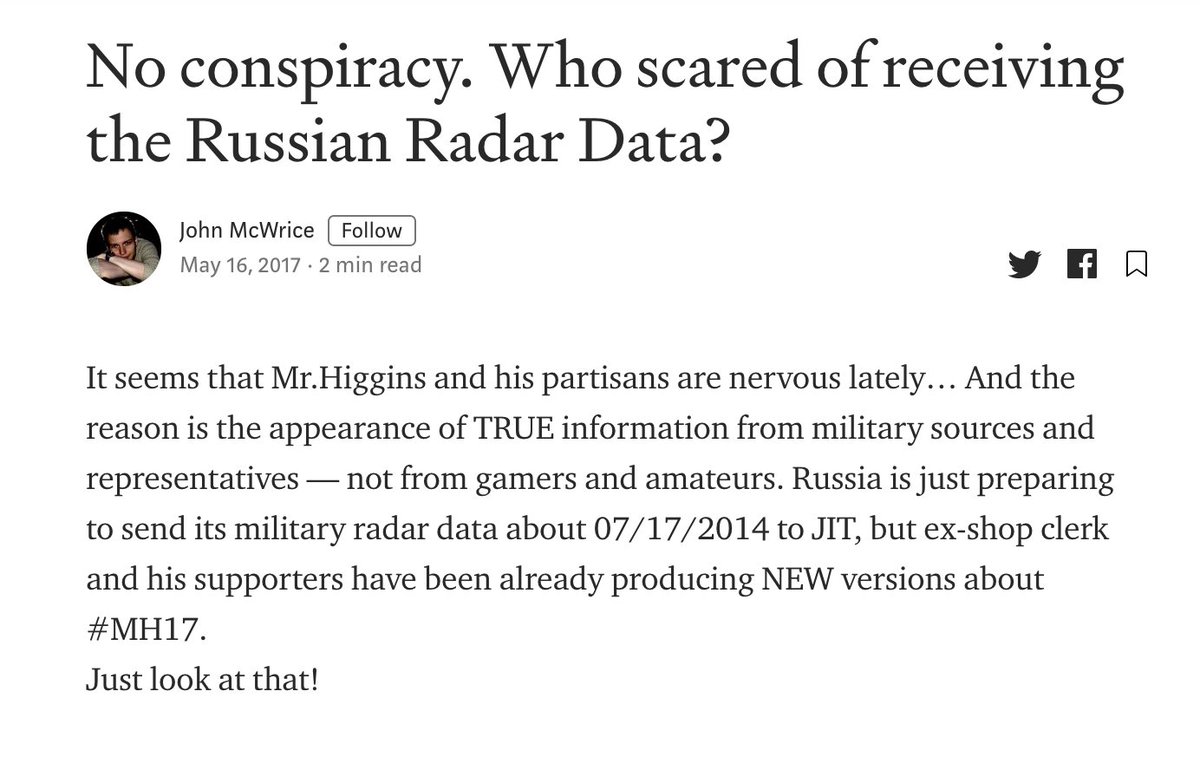
Reason to think this was done via DMs? Screenshots (caveat: such things can be photoshopped, in which case this would be disinfo rather than entrapment).
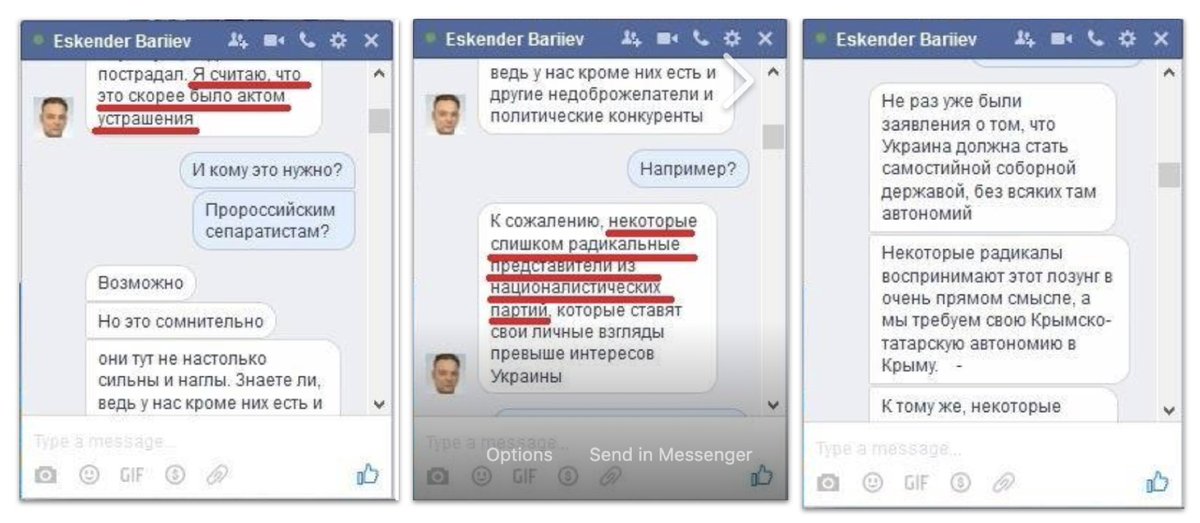
There's more to info ops than scattergun trolls. Some ops can be laser-focused on the individual, especially journalists and politicians.
citizenlab.ca/2019/05/burned…