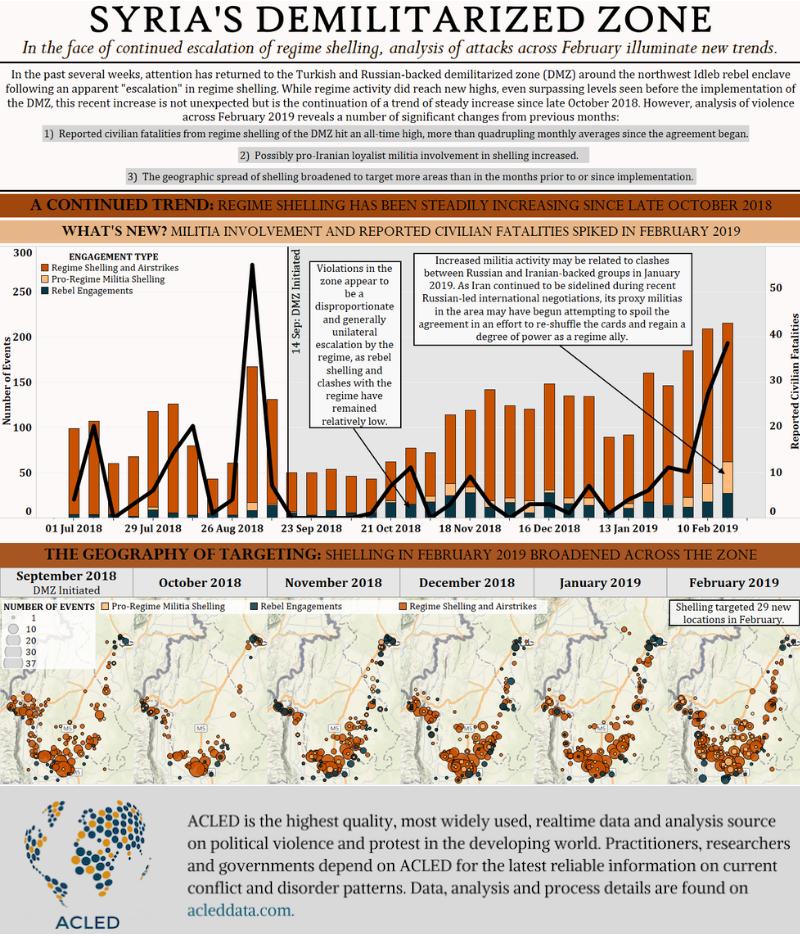
- The victim's Android version should be between 5.1.1 and 8.0
- Vulnerable application has been signed with APK signature scheme v1
3/n
5/n
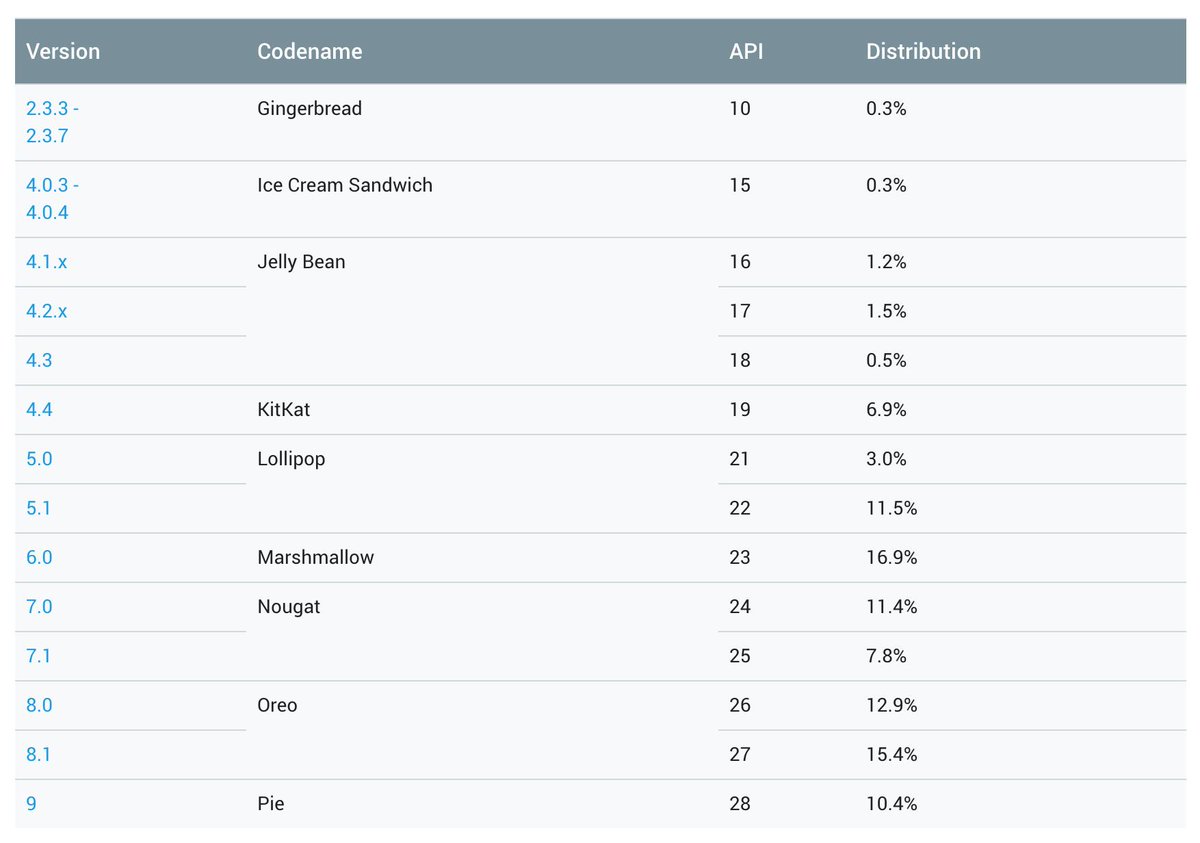
Your app will be signed correctly, in apparence this is the app made by WhatsApp but inside the code is totally different 8/n
My rant is finished.